TEHTRIS understands that there is strength in numbers and has chosen to join the Cyber Threat Alliance, alongside other experts in the field, to bring the power of the TEHTRIS XDR Platform and to share its unique, high value-added markers in order to contribute to a safer digital world.
What is Cyber Threat Intelligence?
CTI is an activity that aims to provide as much intelligence as possible about the cyber threat, both from a technical and tactical or operational perspective.
If we use Gartner’s definition “Threat intelligence capabilities can make your digital business more resilient. Security and risk managers will need to evaluate the capabilities and features of IT offerings and match them to the needs of their security programs based on the use cases described in this research.”*

Threat intelligence allows :
- A better protection of the company’s information systems and sensitive data.
- A better understanding of the threat and a better anticipation of attacks.
- A better reaction and decision making capacity.
The diagram above presents in a simplified way what CTI is, through its three pillars which are the tactical, operational and strategic intelligence which allow the decision makers to react quickly and well. The strategic part offers a vision of the risk and supports decision making to mitigate it. For each, we make the link with the output data and the target audience.
How does Threat Intelligence work?
TEHTRIS CTI has a transversal impact thanks to its native integration with the TEHTRIS XDR Platform. Indeed, the different bricks of the XDR Platform, such as TEHTRIS EDR, MTD, etc. can interrogate the CTI in order to qualify a potentially malicious element, and thus to remedy it if necessary. Our various modules will help feed our intelligence team. This vision, as close as possible to the strain, as close as possible to the endpoint and therefore to the user, is what sets us apart. It allows us to obtain exclusive data, and thus to anticipate new signatures. In September 2021, TEHTRIS CTI contained 200 Million qualified entries (a figure that has been steadily increasing since its creation in 2013).
TEHTRIS CTI is the result of a unique processing of millions of indicators collected close to the field and which are systematically analyzed, enriched and correlated to provide TEHTRIS clients and all the actors of the CTA program with an unprecedented analysis, hunting and investigation capacity.
The interest of the CTI
The professionalization of ransomware groups, the maturity of attackers, and their new organizational capacity (cartel formation, RaaS, etc.) justify the importance of joining forces to better anticipate, prevent and neutralize threats.
If we were to summarize the panorama of the most feared threat today, it could be presented as follows
- Ransomware attacks
- Supply chain attacks
- Denial of service attacks
Even if the most important threat in volume today is still the denial of service attack, which is the easiest to implement for novice attackers or by unscrupulous competitors, it is obvious that ransomware attacks are of particular concern. It is estimated, for example, that there will be an average of 4,000 ransomware attacks per day in the US in 2020! The total number of attacks in 2020 exceeds 300 million…
However, one of the emerging threats of the last 12 months is undoubtedly the one targeting software supply chains.
Everyone still remembers the attacks against SolarWinds and Kaseya, which impacted more than 20,000 large companies and administrations worldwide, including very sensitive entities such as certain critical government services.
The side effects of these two attacks are still causing collateral damage.
Today, it is clear that both attacks were orchestrated and carried out by extremely powerful, organized and wealthy groups, and therefore undoubtedly sponsored by states. And while attacks by APT groups remain among the most complicated to detect, some traces (such as TTPs or malware used) could have alerted cyber analysts and put them on alert.
The importance of CTI is therefore no longer in question. And the obviousness of mutualization is no longer in question. If all the players who knew the latest TTPs of these hostile groups had shared them, it might have been easier to react in time.
“However, one of the emerging threats of the past 12 months, without question, is the one targeting software supply chains.”
What is the Cyber Threat Alliance?
Cyber Threat Alliance defines itself as “a nonprofit organization that strives to improve the cybersecurity of our global digital ecosystem by enabling the sharing of high-quality, near-real-time cyber threat information among businesses and organizations in the cybersecurity field.”
The basic premise of the CTA is this:

The primary objective of the CTA is to give each member access to quality cyber intelligence via a shared platform maintained by the consortium.
This platform automates the collection and contextualization of information on threats.
Thus, intelligence that was previously abstract or unknown to some, becomes concrete, contextualized and immediately exploitable: we speak of activatable cyber intelligence, improving analysis, detection and deployment of response strategies for protection equipment.
More globally, this initiative allows to qualitatively harmonize usable cyber intelligence, to extend its use practices to the largest number of people, and thus to reinforce the capabilities to fight against cybercrime.
As J. Michael Daniel-President & CEO Cyber Threat Alliance states.
“Regardless of size, regardless of capability, no organization has complete visibility into the Internet or cyberspace. Different companies and organizations have different perspectives, information sources and monitoring methodologies. Yet threat analysis and mitigation benefits from as broad and diverse an information base as possible. Therefore, sharing threat intelligence is a critical component of effective cybersecurity. It’s the only way to get the visibility you need and deliver effective products and services to customers.”
Cyber Threat Alliance Program Success Stories
ORG Impact Awards
This organization fuels the missions of organizations around the world whose goal is to have a positive impact on the communities they serve.
CTA was named a finalist in the “Promoting a Safer Internet” category.
Whose goal is “to improve the safety and security of the digital ecosystem through sharing and collaborating on threat intelligence.”
The Kaseya Case
September 2, 2021, Kaseya falls victim to a blockchain cyberattack. The ransomware attack was identified as a REvil ransomware attack
CTA members were able to share information and analysis about this incident via the Early Sharing program. They highlighted the zero-day attack against MSPs using the VSA product and the attack on the service supply chain that leverages the VSA platform. The CTA collected threat reports, blog posts, protection tips and proposed mitigation measures.
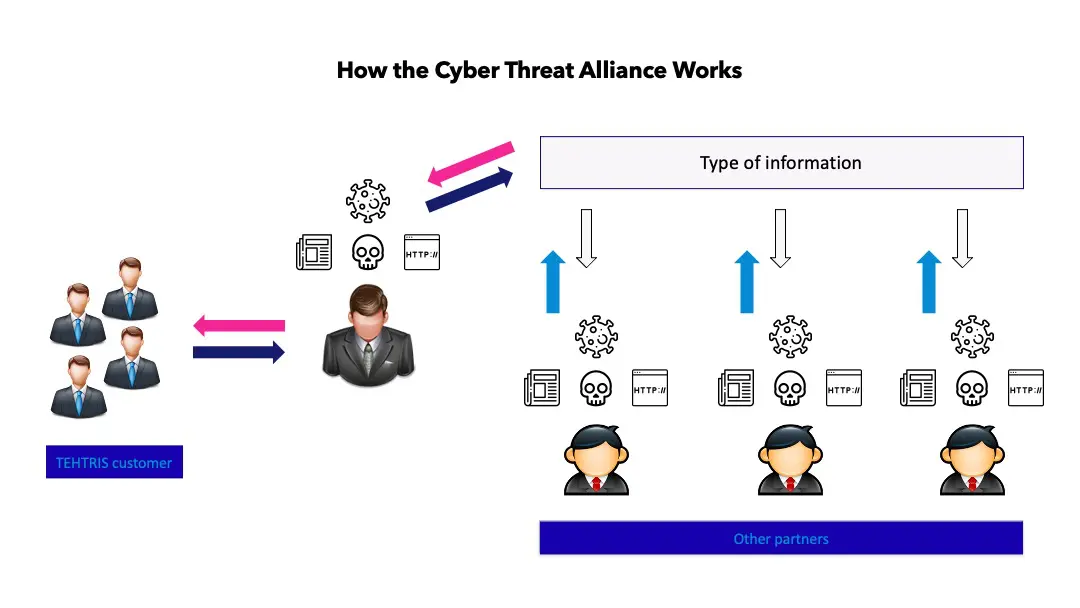
TEHTRIS and CTA Alliance
TEHTRIS, which has long understood the importance of integrating context into its detection, has decided to share it with other specialists in the field in order to improve, once again, the detection and anticipation capabilities of each.
The company is therefore offering the alliance a part of its cyber intelligence collected by its unique and innovative technology, the XDR solution. It provides an extremely precise vision of the threat, because we are as close as possible to the endpoint and the user, the preferred targets of attackers.
In return, TEHTRIS CTI can benefit from the cyber-intelligence produced by other professionals from other sectors, and can therefore share it with all its customers. This is a real added value that the Bordeaux-based company will be able to bring to its partners and customers.
This project is totally in line with the company’s sharing values, as it allows to:
- Improve the quality of our cyber defensive arsenal, for a better service and a better protection of the end-users (because improvement of the knowledge of TEHTRIS CTI); by having a better knowledge and understanding of the environment of the cyber threats, by reinforcing our knowledge on the exploitable information; but also by continuing our work of improvement of our tools and service, in particular, the automation and the reduction of the time of detection and response, by ensuring the safety, the availability, the integrity of the IS. This real-time sharing of information between partners from the same or different backgrounds will allow us to provide a high quality service.
The latest attacks show the need to have ever more robust solutions, as is our XDR. TEHTRIS’ position is based on the implementation of resilient solutions for the protection of systems.
- Participate in a more global strategy to promote and improve cybersecurity worldwide. All members are contributors, which is a core principle of the alliance.
- Through its sovereignty, TEHTRIS knows how to find the appropriate course of action to share intelligence that contributes to strengthening cyber defense.
TEHTRIS develops synergies between actors from different sectors of activity, from different geographical areas, and thus strengthens the integration of European countries in the global economic fabric, and promotes a rise in competence in the cyber ecosystem. Europe has reached maturity in cyber and intends to make its voice heard, and to stand out, by proving its ability to react to a threat, by making its contribution within the framework, among others, of the CTA program.
Conclusion
By this union, we put at the service of the CTA our skills, our expertise, and our determination to work together with other partners to fight against cybercrime. On the other hand, we participate in the highlighting of Europe’s involvement in the construction of a Cyber Intelligence strategy. We are demonstrating our place as a digital power; we must now count on this alliance as a major player in the strategy to fight cybercrime.
*Market Guide for Security Threat Intelligence Products and Services
Published 20 May 2020
By Craig Lawson, Brad LaPorte, John Collins, Mitchell Schneider, Ruggero Contu

