As a CISO working in the healthcare industry, optimizing the cybersecurity of your information system (IS) can be a real challenge. Healthcare industry facilities are known to have the most complicated IS of all industries.
A recent report of the French institution La Cour des Comptes, for example, showed that the Parisian hospital’s infrastructure used over 1000 applications daily, dispatched on over 40 sites. The same report states that health facilities use, on average, between 80 and 500 applications daily, on several sites.
Additionally, the health sector has been increasingly targeted following the Covid-19 pandemic which made it even more vulnerable to cyberattacks as citizens had to extensively resort to online services, thus expanding the surface of attack.
This article explores the cybersecurity challenges of the healthcare industry, an industry where the stakes are exceptionally high: ranging from risks on patients’ lives and severe operational disruptions to substantial financial losses, that persist long after an attack.
I. A particularly complex cybersecurity
Cybersecurity matters are uniquely difficult to handle for actors of the healthcare industry. A recent report from the highest French auditing institution notes profound weaknesses in the cybersecurity of healthcare facilities (both public and private) that keeps worsening. Several key factors are mentioned, and this trend is observed worldwide.
1) Highly complex infrastructures
Healthcare facilities have uniquely complex information systems. They need to include countless different sources, tools, actors and processes, making them difficult to create, manage and scale. But most, importantly, it makes them challenging to secure and particularly vulnerable to cyberattacks.
In its staggering report, the highest French auditing institution gives the example of the IS of an University Hospital, limited to its laboratory:
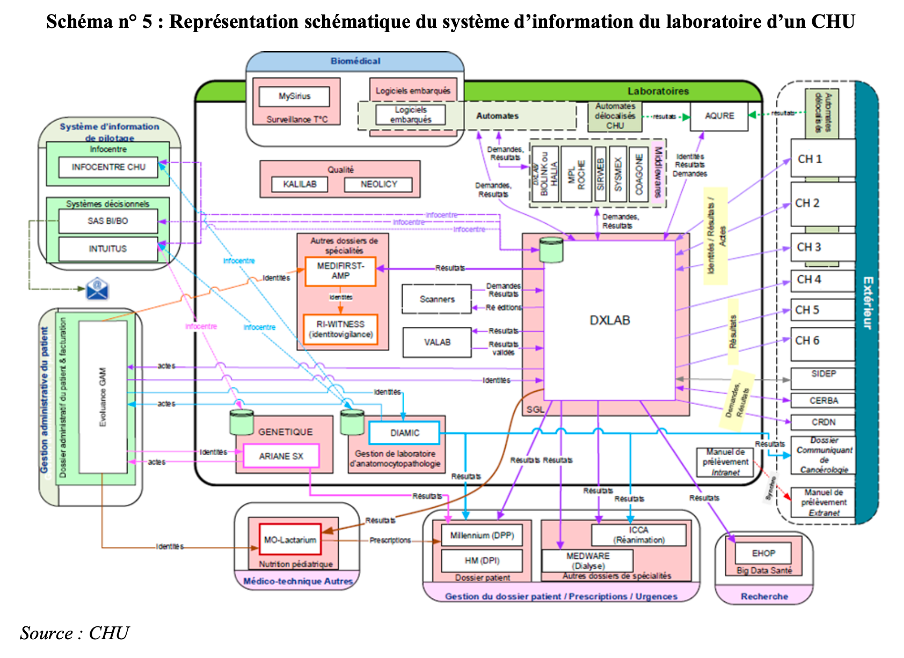
In addition to an already challenging internal structure, healthcare facilities have had to quickly incorporate new external components, that added to their complexity:
- External labs, partners and service providers that created a shift from an exclusive internal use to apps and programs that aren’t solely hosted in the facility anymore
- The use of cloud and SaaS programs that significantly extended the attack surface and that need their own, specific, protection processes
- Remote consults for patients and staff exacerbated this tendency even more
- The ever-growing use of IoT devices, only increases the vulnerabilities of an already complex infrastructure
For a more detailed analysis of the complexity of health facilities’ information systems, refer to the report of the French auditing institution.
2) Budgetary constraints
A primary contributor to cybersecurity vulnerabilities in the healthcare sector are budgetary constraints. This “chronic underinvestment”, as the highest French auditing institution calls it, significantly weakens the sector’s ability to defend itself.
However, cost-effective security solutions tailored to the unique needs of the healthcare industry do exist, as we will explore later in this article.
3) Legacy structures
The combination of an already complex IS and insufficient investment often forces healthcare facilities to rely on their legacy structures. These structures present major cybersecurity risks, including:
- Outdated encryption protocols,
- Unpatched security vulnerabilities,
- Weak authentication mechanisms.
Legacy structures can be full of vulnerabilities that can easily be exploited by threat actors and leaves them exposed to advanced cyberthreats.
Additionally, as mentioned earlier, the information system of healthcare facilities keeps expanding. Integrating new tools and services with outdated infrastructure further compounds security risks, making it imperative to modernize legacy systems.
II. A rise of attacks against healthcare facilities
The complexity of healthcare facilities’ IS and their use of legacy equipment create considerable vulnerabilities in their cybersecurity that other industries do not face to the same extent.
Simultaneously, CISO’s tasks are made even more challenging through an unprecedented intensification of cyberattacks against healthcare facilities, with data breaches being the main consequence.
1) Ransomware attacks
Ransomware attacks are globally rising, and the healthcare industry has been particularly affected. In its most recent threat landscape analysis of the healthcare sector, the European Union Agency for Cybersecurity (ENISA) noted that in 43% of ransomware attacks, breach or theft of data was confirmed.
The Washington Post recently published an article noting that, if ransomware attacks are on the rise in the healthcare industry, it is because they are fairly effective and lucrative for threat actors. When targeted, many healthcare institutions opt to pay the ransom, inadvertently reinforcing a cycle of attacks. However, even when a ransom is paid, healthcare facilities recover, on average, only 64.8% of their encrypted data.
2) Phishing attacks
According to the ENISA, phishing accounted for 8% of incidents reported under the NIS directive in 2021 and 26% in 2022 (2). This growth persist, as human errors remain the biggest liability in cybersecurity and phishing attacks are still on the rise globally. Healthcare workers are the most likely to fall for fraudulent e-mails, after employees of the transportation and automotive industries.
As numerous experts note, healthcare facilities are fast-paced environments which facilitates social engineering attacks. When handling emergencies, with a pressure to get things done, mistakes can easily be made and that is why phishing attacks can be so effective in this industry. Regular security awareness training and phishing simulation exercises remain essential to mitigating these risks.
3) DDoS attacks
DDoS attacks, which are currently on the rise worldwide, are prevalent in the healthcare sector. The ENISA notes that DDoS attacks have be growing in 2023 and are mainly perpetuated by pro-Russian hackers, targeting European hospitals and health authorities. This largely increased the number of DDoS attacks in the healthcare industry (by 9%), while DDoS attacks for other motives aren’t on the rise in the healthcare sector.
4) Supply chain attacks
Finally, supply chain attacks are a major risk for the healthcare industry. By exploiting the vulnerabilities of third-party vendors, threat actors can easily access healthcare facilities. This is why this type of attacks are on the rise, according to the American Hospital Association (6).
In most cases, they lead to data leakage or theft for the supplier or the healthcare facility directly. The main causes for the breaches are usually poor cybersecurity practices or strategies, resulting in vulnerabilities, on the third-party vendor’s side (2).
Most experts agree that supply chain attacks, especially those linked to cloud services, will keep growing and heavily impact the healthcare industry.
III. Practical solutions to strengthen your cybersecurity
Cybersecurity in the healthcare sector might be one of the most challenging to manage. Given the need to balance patient care continuity, financial stability, and complex IS infrastructures, robust security measures are essential.
The best way to reach this goal is through constant and effective monitoring of the IS.
At TEHTRIS, we have combined our EDR with our own AI, CYBERIA. By leveraging CYBERIA, our EDR takes the monitoring to the next level for a robust, proactive, cybersecurity. Simultaneously, our AI hyperautomates responses to attacks, for real-time neutralization without human interaction.
A strong employee training on risks and vulnerabilities is still a must to prevent human behavior, but, even on this part, our EDR can help by detecting any unusual behavior.
Given the prevalence of legacy systems and the constantly growing attack surface due to the added IoT devices, a Honeypot / Deceptive Response solution is an add-on you should be considering.
By deploying it on your network, you can secure areas beyond the reach of traditional cybersecurity solutions. This additional layer of security is essential to your cybersecurity strategy and will keep you ahead of threat actors.
The Deceptive Response solution will divert them from your critical assets and helps you to spot threats before they even happen.

