MITRE ATT&CK EVALUATIONS 2024:
SHIFTING THE LENS
The role of anticipation over post-attack evaluations
For the second consecutive year, TEHTRIS demonstrated its drive to continuously challenge itself and its commitment to reach excellence by participating in the prestigious 2024 MITRE ATT&CK Evaluations: Enterprise – an exclusive assessment, undertaken alongside few leading vendors in cybersecurity.

Strengthening SOC Teams: The power of proactive AI
This year’s evaluation placed a stronger emphasis on post-attack analysis, shifting the focus away from anticipation and detection. TEHTRIS XDR AI PLATFORM demonstrated meaningful resilience by accurately identifying critical detection steps and autonomously neutralizing a complex PROTECTION scenario involving three distinct attack vectors.
This evaluation reaffirmed our philosophy that anticipation of threats with automatic detection and neutralization in real time and without human action, must take priority over post-attack analysis. By empowering security teams with its proprietary AI: CYBERIA, based on Neural Process Automation (NPA), TEHTRIS XDR AI PLATFORM streamlines events to alerts with a primary objective of enhancing overall detection efficiency and eliminating SOC cyber fatigue.
This evaluation validates TEHTRIS innovative approach to detection, response, and supervision strategies.
About the MITRE ATT&CK Evaluations:
The MITRE ATT&CK Evaluations is a globally recognized, independent testing exercise for cybersecurity vendors. This year, it simulated the tactics of notorious threat actors, such as Cl0p and LockBit ransomware groups, alongside behaviours linked to advanced adversaries like those associated with the Democratic People’s Republic of Korea (DPRK). The goal? To assess detection and response capabilities in realistic attack scenarios.
Key Innovation: “TEHTRIS Chokepoint-Centric Methodology”
The TEHTRIS Chokepoint Approach ensures a balanced strategy between comprehensive telemetry and precise detection, minimizing false positives and reducing the chances of missing critical threats. When a detection is triggered via a chokepoint, the TEHTRIS XDR AI PLATFORM enables both automated and manual response actions targeting a predefined list of assets, enhancing operational agility.
By leveraging the TEHTRIS Chokepoint Approach, this round of MITRE ER6 detection and protection scenario showcases the effectiveness of the TEHTRIS XDR AI PLATFORM, achieving
100% relevance
across 12 MITRE ATT&CK® tactics.
The TEHTRIS XDR AI PLATFORM offers role-specific views designed to streamline analyst workflows:
- Targeted Supervision View for frontline analysts, enabling quick and effective threat monitoring.
- Investigation View structured around MITRE tactics, tailored for Level 2 analysts to facilitate deeper analysis.
Both views are powered by TEHTRIS’ proprietary AI, CYBERIA, ensuring analysts can focus exclusively on the most critical and relevant alerts, improving response efficiency and accuracy.
This approach identifies actions requiring either automated or human intervention while aligning investigations with MITRE ATT&CK® tactics. SOC managers benefit from newly launched dashboards that provide actionable insights and improved oversight.
Reflecting MITRE ATTA&CK’s “Summiting the Pyramid” model, TEHTRIS focuses on critical attack stages to minimize noise, maximize intelligence, and enable decisive responses.
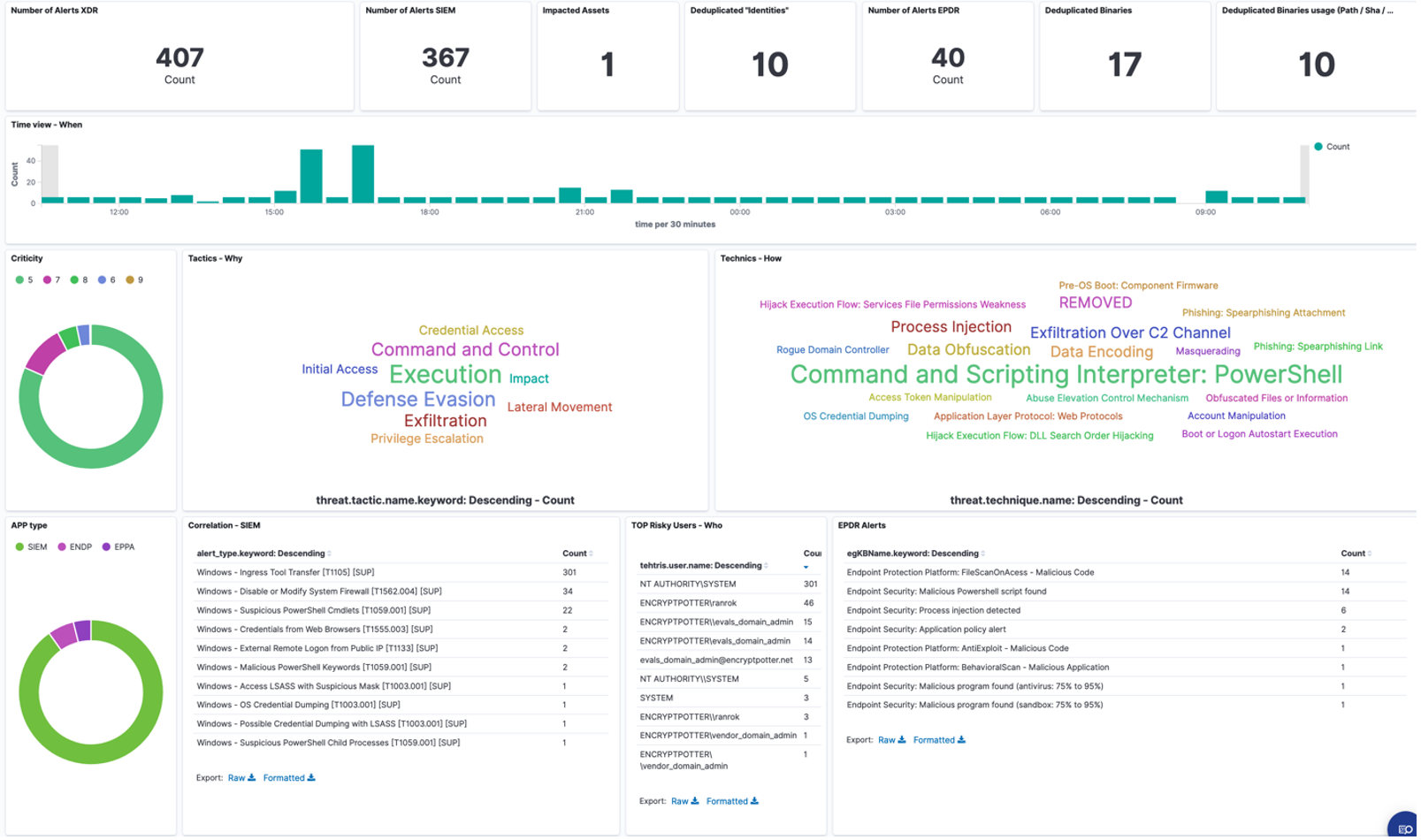
Highlights from the 2024 Evaluation
This year’s evaluation included:
- Scope Adjustments: Initial Access steps were excluded from the evaluated protection scenario.
- Broader Threat Scenarios: Expanded to include macOS threats, benign activity testing false-positive rates, and attacks across Windows and Linux environments.
- Focus on Ransomware: Detailed analysis of attack methods in Cl0p, LockBit, and DPRK-inspired campaigns.
Telemetry and configuration:
This year protection scenario focused on post-compromised environments
As per the MITRE ATT&CK Rules of Engagement (ROE), generic and general blocking of services – such as block Powershell, block all flow from internet… – was not authorized during the evaluation.
To adhere to these guidelines, TEHTRIS had to make specific adjustments to its TEHTRIS XDR AI PLATFORM configuration and authorized a specific behavior. A temporary authorization was granted for remote RDP access, allowing a privileged account to connect from a non-management network to an Internet-exposed Windows Domain Controller.
This adjustment – which would not occur in a real production environment – was necessary to allow the MITRE ATT&CK Evaluations Enterprise to move forward with the evaluation scenario.
In a real-world environment, TEHTRIS XDR AI PLATFORM’s configuration would have immediately stopped such a threat. These adjustments highlight the flexibility and precision of our solution when operating under controlled evaluation parameters.
While attack telemetry was not evaluated this year, it remains integral to production environments, enabling SOAR playbooks, automated responses, and forensic analysis. TEHTRIS demonstrated its ability to detect and halt malicious activity at critical stages, validating its chokepoint strategy.
Results that matter: Stopping attacks BEFORE they escalate
While many view 100% detection coverage as the ultimate achievement, TEHTRIS adopts a broader perspective.
At TEHTRIS, however, we prioritize what truly matters: equipping SOC teams and Managed Security Service Providers (MSSPs) with solutions that enable real-time automatic detection and neutralization of threats. By anticipating risks and preventing breaches before they escalate, our approach ensures operational efficiency while minimizing unnecessary noise and alert fatigue.
TEHTRIS XDR AI PLATFORM excels at detecting and neutralizing threats. In real-world conditions, our technology would have stopped attackers straight from the start.
This evaluation reaffirmed our commitment to providing practical, operational tools that deliver immediate value—helping cybersecurity professionals focus on prevention and protection, rather than post-attack analysis.
By optimizing configurations across these stages, we ensure our technology anticipates and halts attacks at critical points.
FORRESTER underlines, “MITRE ATT&CK Evaluations Are Not A Ranking, Which Is Why They’re Valuable” cautioning that excessive focus on comprehensive detection can generate unnecessary noise, false positives, and overwhelming alert volumes, many of which may not be actionable, ultimately burdening security teams.
Looking Ahead: Raising the role of Configuration specialists
TEHTRIS’ participation in 2024 MITRE ATT&CK Evaluations reaffirms our commitment to equip cybersecurity teams with practical, operational tools that deliver immediate and meaningful value. By prioritizing proactive prevention and streamlined management, we empower professionals to focus on safeguarding their systems and anticipating threats, rather than merely reacting to incidents after the fact.
As cybersecurity challenges grow more complex, the role of Configuration Specialists is becoming increasingly vital. These experts are pivotal in optimizing and managing security tool configurations, ensuring that solutions operate at peak efficiency. By minimizing misconfigurations and enhancing the effectiveness of penetration testing and threat detection, they strengthen an organization’s overall security posture.
To address this emerging need, the concept of Configuration-as-a-Service (CaaS) is gaining traction. This model centralizes and simplifies configuration management, allowing SOC analysts to concentrate on their core mission, preventing breaches and maintaining operational efficiency. By adopting such forward-thinking practices, organizations can achieve greater agility, reduce operational risk, and enhance the resilience of their security operations.
As the cybersecurity landscape continues to evolve, the integration of Configuration Specialists and streamlined management practices will be indispensable to build robust, modern security strategies. TEHTRIS remains dedicated to leading this evolution, providing the tools and insights that enable organizations to stay ahead of emerging threats.
Learn more about the MITRE ATT&CK Evaluations here: https://attackevals.mitre-engenuity.org/
