Our selection of alerts on honeypots: report 20 – November 2023
The following report consists of TEHTRIS observations on our worldwide honeypots network to provide you with... Read more

The following report consists of TEHTRIS observations on our worldwide honeypots network to provide you with... Read more

The following report consists of TEHTRIS observations on our worldwide honeypots network to provide you with... Read more

TEHTRIS AI R&D team has developed from scratch an Artificial Intelligence based module called Cyberia eGuardian.... Read more

The following report consists of TEHTRIS observations on our honeypots to provide you with information on... Read more

For the first time, TEHTRIS participated in the 2023 MITRE Engenuity ATT&CK® Evaluations: Enterprise. Using TEHTRIS... Read more
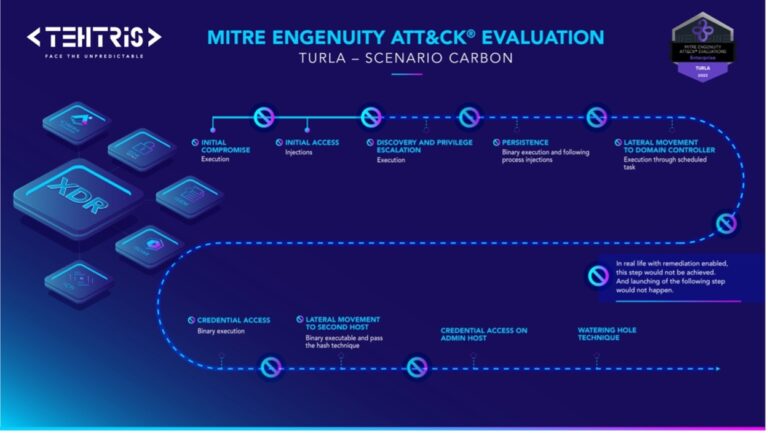
This use case is a summary of the Blitz WarGames, which was organized during the TEHTRIS... Read more

TEHTRIS believes in creating cyber threat intelligence based on empiric observations of what is happening in... Read more

A malware powered by Artificial Intelligence is now capable to adapt itself to the targeted infrastructure,... Read more
After a summer break, we are back with observations on our honeypots to provide you with... Read more

Only 17% of SMBs (1) rate their cybersecurity capabilities as ‘effective’ or ‘somewhat effective’. And a... Read more

If you are a SMB owner trying to strengthen your cybersecurity quickly but, most importantly, efficiently,... Read more

RustyStealerDropper Use case A reminder: what are malware droppers?How do they stay in your systems?Deobfuscating a... Read more
