The following report consists of TEHTRIS observations on our worldwide honeypots network to provide you with information on what is going on the Internet. This actionable cyber threat intelligence is based on observations from a real and uncontrolled environment. Keeping track of trends and keeping an eye on what is actively scanned by threat actors in a reconnaissance phase allows to adjust the cybersecurity posture..
Check out our previous report here.
Minecraft RCE vulnerability targeting Nintendo devices
Minecraft is the best-selling video game in history, with over 238 million copies sold and nearly 140 million monthly active players on multiple devices, including Nintento ones. Of note, Minecraft allows its players to host private servers on port TCP/25565, assigned by the IANA (Internet Assigned Numbers Authority) itself, to be able to play with others.
Unfortunately, fame comes with a price and players are often facing security breaches. Recently, at the end of July 2023, a remote code execution (RCE) vulnerability has been disclosed by Minecraft community as the flaw, named BleedingPipe, has been exploited in the wild. It affects clients and servers running popular Minecraft mods. A threat actor scanned all Minecraft servers on the IPv4 address space to mass-exploit vulnerable servers. A likely malicious payload was then deployed onto all affected servers.
When it comes to our honeypots, in September, we monitored more exploit attempts coming from threat actors using Nintendo fingerprint on port TCP/25565, with a spike on the 3rd of October.
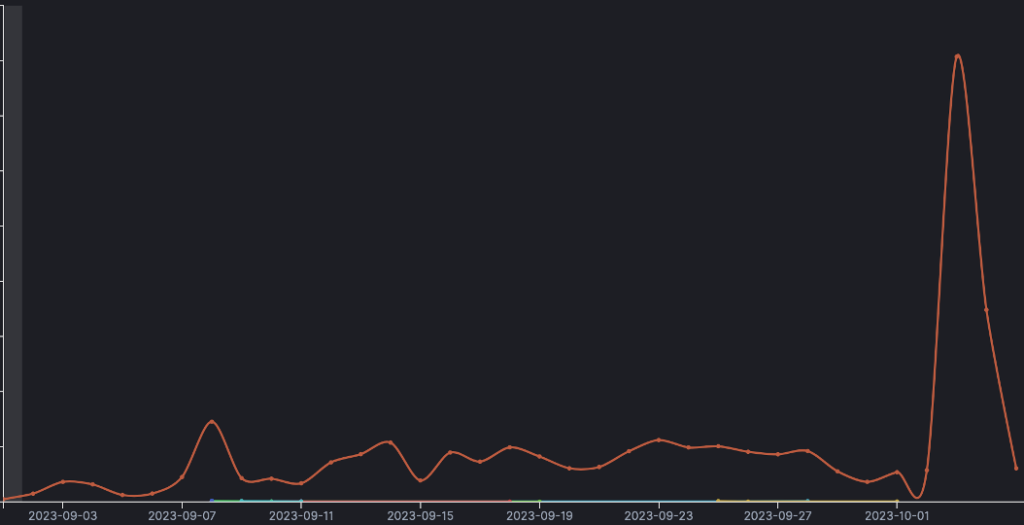
We assess threats actors are impersonating Nintendo devices to find out out other devices which port TCP/25565 is open. It might be their way to spread among multiple players around the planet. The goal is not clear, but we assess it could be the way of creating a massive Nintendo Minecraft botnet.
We recorded only 8 unique IP addresses targeting our worldwide honeypots network with this particular manner:
IoC – known from VirusTotal community
164.68.124[.]86– AS 51167 (Contabo GmbH) 🇩🇪
84.54.51[.]212 – AS 202685 (Aggros Operations Ltd.) 🇳🇱
51.15.34[.]47 – AS 12876 (Scaleway S.a.s.) 🇫🇷
51.15.62[.]117 – AS 12876 (Scaleway S.a.s.) 🇫🇷
51.15.101[.]63 – AS 12876 (Scaleway S.a.s.) 🇫🇷
88.99.33[.]115- AS 24940 (Hetzner Online GmbH) 🇩🇪
IoC – not known from VirusTotal community
37.27.7[.]148 – AS 24940 (Hetzner Online GmbH) 🇫🇮
45.55.133[.]153 – AS 14061 (DIGITALOCEAN-ASN) 🇺🇸
Aside from this specific port, two of these threat actors (identified as malicious by VirusTotal community) using Nintendo fingerprints also reach out to hundreds of other ports in addition top port TCP/25565. Here is the top 10 of port/protocol contacted:
| Protocol | Port |
| TCP | 25576 |
| TCP | 25582 |
| TCP | 25573 |
| TCP | 10006 |
| TCP | 25585 |
| TCP | 25569 |
| TCP | 25567 |
| TCP | 10230 |
| TCP | 25590 |
| TCP | 25577 |
IoC – known from VirusTotal community:
164.68.124[.]86 – AS 51167 (Contabo GmbH) 🇩🇪
51.15.34[.]47 – AS 12876 (Scaleway S.a.s.) 🇫🇷
Most of Nintendo devices have several ports/protocols enabled to function correctly. As it is known from threat actors, they might be trying to enroll Nintendo IoT to create a botnet. But, it also could be the result of IP spoofing.
As we found out online and on the Nintendo consumer manuals, for accessing Wi-Fi through consoles, players have to enable traffic incoming from specific ports/protocols.
Here is an example for Nintendo DS :
“The Nintendo DS requires unrestricted access to several sites across various ports andprotocols to function correctly. These addresses and ports vary according to game, and may change in the future without notice. Many software firewalls restrict outbound access. Only if your firewall blocks outbound traffic do you need to enable this traffic:
- TCP: Allow traffic to all destinations on ports: 28910, 29900, 29901, 29920, 80, and 443
- UDP: Allow all traffic to all destinations. (Necessary for peer-to-peer connections and game play).”
Our honeypots hosted in Europe were by far the most targeted by this campaign, before the ones located in Asia Singapore and Japan.
Focus on a Colombian threat actor
This Colombian IP address 190.1.203[.]180 hosted by AS 10299 EMPRESAS MUNICIPALES DE CALI E.I.C.E E.S.P. have been targeting our honeypots since August. It is flaged as malicious by VirusTotal community mainly for SSH bruteforce attempts.
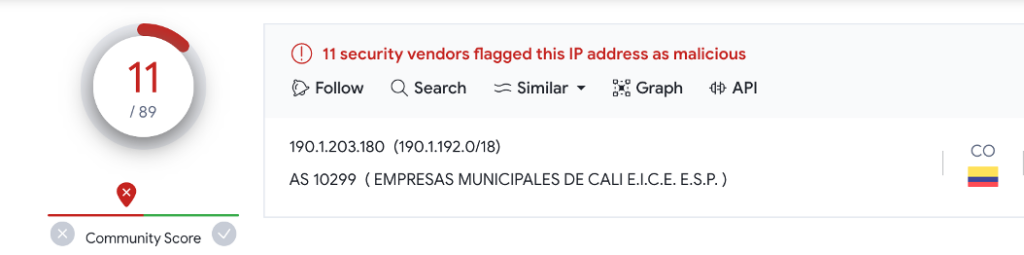
Betwen the 22nd and the 29th of August, our honeypots recorded almost 400 hits, mostly on Monday 28th.
Half of hits targeted SSH services on port TCP/22. The following honeypots were targeded: one in Thailand, 4 in Europe (France, Germany, Czech Republic and Finland) and 2 in Singapore.
This threat actor tested a wide range of credentials possibilities. Most of them remain by default login and password.
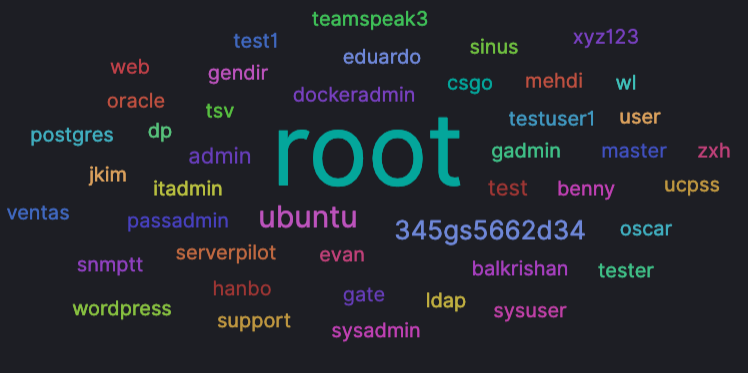
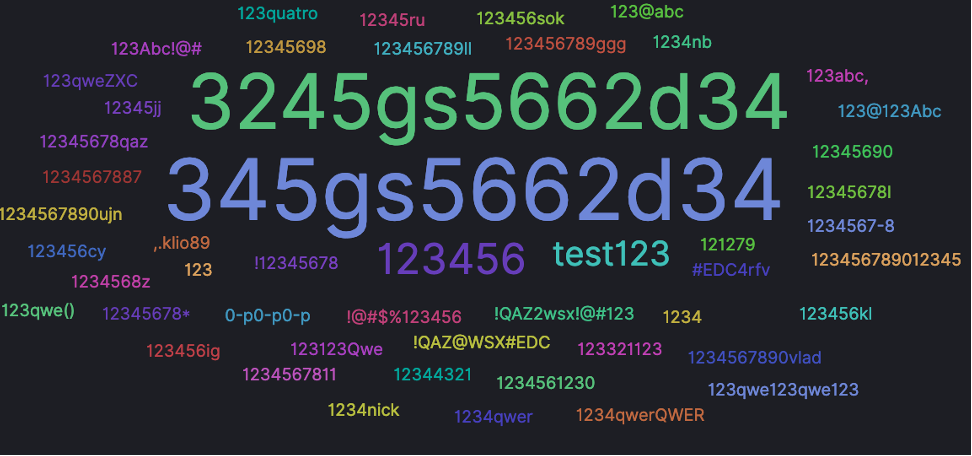
Then, the threat actors came back on our honeypots network on September 18th. The higher hits were recorded on Tuesday 26th of September. In total, over 700 hits were recorded on honeypots hosted in Singapore, Thailand, Indonesia, Japan, and a dozen European countries. This time the threat actors used different combination of credentials with more names – such as parker, joseph or chandra – included in attempted logins compared to their August campaign.


Muieblackcat Scanner
The Bulgarian IP address 5.181.80[.]137, hosted by AS 50360 (Tamatiya EOOD), targeted one of our Indian honeypots with Muieblackcat scanner on TCP/80 which the port used for HTTP web traffic.
TEHTRIS NTA recorded the following packet:
GET /muieblackcat HTTP/1.1 Accept: */* Accept-Language: en-us Accept-Encoding: gzip, deflate Host: 43.205.243.106 Connection: Close
Other honeypots located in Indonesia were targeted by this same IP address with the following urls:
- /muieblackcat
- //phpMyAdmin/scripts/setup.php
- //MyAdmin/scripts/setup.php
- //myadmin/scripts/setup.php
- //phpmyadmin/scripts/setup.php
- //pma/scripts/setup.php
The Muieblackcat Scanner is known since at least 2015, as Fortinet wrote about it in their Threat Encyclopedia. Muieblackcat is a vulnerability scanning product for web servers. The threat actors are using it to collect sensitive information on all web server utilizing PHP applications.
This is an important reminder that old tools (8 years old !) are still included in current threat actors’ arsenals to find and exploit vulnerable devices exposed over the Internet.
A new password massively tried on our SSH honeypots
Want to learn more on this subject?
More insights on this research issued from the alerts on our worldwide honeypots network.
Subscribe to our bi-monthly threat intelligence newsletter
Top 10 most exploited CVE – September 2023
Want to learn more on this subject?
More insights on this research issued from the alerts on our worldwide honeypots network.
Subscribe to our bi-monthly threat intelligence newsletter
Information remain TEHTRIS sole property and reproduction is forbidden
TEHTRIS is and remains sole property rights owner of the information provided herein. Any copy, modification, derivative work, associated document, as well as every intellectual property right, is and must remain TEHTRIS’ sole and exclusive property. TEHTRIS authorizes the user to access for read use only. Except as expressly provided above, nothing contained herein will be construed as conferring any license or right under any TEHTRIS’ copyright.
No warranty and liability
TEHTRIS will not be held liable for any use, improper or incorrect use of the information described and/or contained herein and assume no responsibility for anyone’s use of the information. Although every effort has been made to provide complete and accurate information, TEHTRIS makes no warranty, expressed or implied regarding accuracy, adequacy, completeness, legality, reliability, or usefulness of any information provided herein. This disclaimer applies to both isolated and aggregated uses of the information.

