For the first time, TEHTRIS participated in the 2023 MITRE Engenuity ATT&CK® Evaluations: Enterprise. Using TEHTRIS XDR and EDR Optimus, we successfully demonstrated our robust threat detection capabilities at critical points in the cyberattack kill chain, which, combined with the remediation capabilities of the EDR and SOAR modules, would have immediately neutralized threats without the need for human intervention.
What is MITRE Engenuity ATT&CK Evaluations: Enterprise?
About MITRE Engenuity ATT&CK® Evaluations: Enterprise
MITRE Engenuity ATT&CK Evaluations: Enterprise is an independent, international exercice for cybersecurity vendors. This year, it was simulating the modus operandi of the infamous Turla threat actor, to highlight detection capabilities.
MITRE Engenuity ATT&CK® Evaluations is built on the backbone of MITRE’s objective insight and conflict-free perspective. Cybersecurity providers turn to the ATT&CK Evaluations program to improve their offerings and to provide defenders with insights into their product’s capabilities and performance. Evaluations enable defenders to make better informed decisions on how to leverage the products that secure their networks.
Rules of the Evaluations
For this evaluation, given the rules set by MITRE Engenuity, TEHTRIS used only a part of its defensive arsenal, i.e. only the EDR and SIEM modules of the TEHTRIS XDR platform were deployed in the simulated attack environment.
The attack emulation was realised in a laboratory environment without performing TEHTRIS Cyberia Artificial Intelligence training, without TEHTRIS EPP and without TEHTRIS network components (NTA/Honeypot), and third-party integrated products enabled in customer production environments – thus our protective shield was therefore not complete.
For example, our neural network could not be trained with normal activities before the tests. The network traffic analysis and the deceptive response solutions could not be deployed, meaning that we had not the full power of the XDR during this MITRE testing session.
Moreover, it should be mentioned that remediation actions were strictly forbidden in order to allow the emulated attack to proceed to its end without any kill allowed for our solution.
Also, MITRE Engenuity does not rank or rate vendors that take part in their evaluations. MITRE Engenuity ATT&CK Evaluations are not competitive analyses, because there is no “one-size-fits-all” solution for our end-users’ environments.
Have you heard about Turla before ?
Active since at least the early 2000s, Turla is a sophisticated Russian based threat group that has infected victims in over 45 countries.
The group is known to target government agencies, diplomatic missions, military groups, as well as research and media organizations. Turla adopts novel and sophisticated techniques to maintain operational security, including the use of a distinctive command-and-control network in concert with their repertoire of using open source and in-house tools.
Turla is known for their targeted intrusions and innovative stealth. After establishing a foothold and conducting victim enumeration, Turla persists with a minimal footprint through in-memory or kernel implants. Turla executes highly targeted campaigns aimed at exfiltrating sensitive information from Linux and Windows infrastructure.
What happened ? Emulated Attacks spotted at every critical stage by TEHTRIS
Carbon scenario follows Turla’s multi-phase approach to implant a watering hole for persistence on a victim’s network as a way to compromise more victims of interest.
Turla gains initial access through a spearphishing email, a fake software installer is downloaded onto the victim machine and execution of the EPIC payload takes place.
Once persistence and C2 communications are established, a domain controller is discovered, and CARBON-DLL is ingress into victim network.
Further lateral movement takes the attackers to a Linux Apache server, PENQUIN is copied to the server and used to install a watering hole.
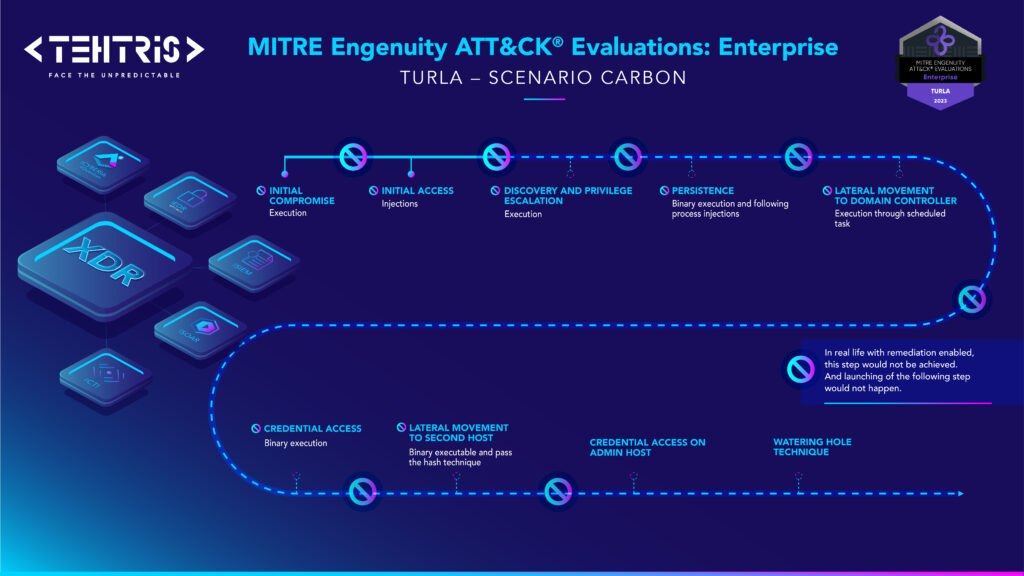
This kill chain timeline highlighs and illustrates the strenghs and capabilities of TEHTRIS solutions regarding the evaluation. In brief, TEHTRIS is particularly proud of detecting critical attack stages as soon as they are executed.
This gives us the assurance that, with remediation activated, the attack would be neutralised instantly and without human intervention thanks to the TEHTRIS XDR platform.
Decoding our results : how TEHTRIS keeps you safe !
The key benefits of using TEHTRIS
Let’s have a look at the key benefits of using TEHTRIS regarding the results:
- Spot key criticals alerts to detect and prioritize in the incident view of the TEHTRIS XDR platform, with minimal verbosity
- Enable advanced threat hunting & forensic analysis from the Alerts & Events or TEHTRIS SIEM Raw Data view, or from the Threat Intelligence Platform of TEHTRIS CTI thanks to Extensive Telemetry.
- Automate Response capabilities without human intervention to stop the attack at an early stage with automatic EDR and SOAR remediation actions and integrated playbooks
- Understand technics thanks to MITRE Technique inclusion within TEHTRIS XDR platform, giving user access to internationally well-known cyber standard.
Being able to detect and remediate to the essential steps of an attack path is undoubtly an important goal of a security solution. But which are the key steps that actually hinders an attacker to go any further ?
Well, as the evaluation shows, TEHTRIS is proud of being able to detect AND to stop the major executions for each and every single step of the attack path as illustrated. It is also important to notice that the very first execution of the attack path was triggered on the evaluation that took place.
In real life that’s exactly the kind of protection customers need : a remediation without any human interaction at the very beginning of an attack path, which hinders the attack to go any further.
SOC analysts and Incident Response teams need filtered and prioritised alerts, they cannot not every single action. For forensic, we keep logs and telemetry, with advanced analysis tools and high-speed search capability.
Our product philosophy is to focus the analyst on most critical and priority alerts, and not to flood him on what is really happening and need its attention. This vision contributes to gain time, accelerate the MTTR (Mean Time To Respond) and reduce alerts fatigue.
Even if we imagine an attacker’s skill that let him an entire step of an attack path beyond our detection features (which we haven’t encountered yet), our results clearly demonstrate that our solution detect and remediate on each and every next step of the attack path.
Another interesting analysis of our’s concerns the insane race to the absolute perfect score of 100% of actions where detected with the precise MITRE Technique. Let’s make a step aside and consider the complex subject of vulnerability management. It also has been a insane race for years, as the cybersecurity standards and best practices required to patch all vulnerable software in every IT system.
Luckily, as operational cybersecurity matured, more and more people shouted out to finally make a point : it’s damn hard and most probably impossible to follow the pace and for the vast majority of businesses there’s no way to actually patch every vulnerability published in the world. It eventually give birth to KEV by CISA : Known Exploited Vulnerabilities.
With that a new path of operational cybersecurity was born : business could now step from patch’m all to patch what’s actually used by attackers to begin with. What a relief ! It is now ok, allowed and understandable to do good security without achieving a fully imaginary perfect cybersecurity !
At TEHTRIS, this was one of our main pillars from the beginning 12 years ago : which are the main technical steps attackers actually use most.
And ideally, what are the ones that are used in most (if not all) attack path ?
Ten years later, MITRE Engenuity wrote a paper about these choke points : “A specific technique where many other techniques converge or diverge, and eliminating that specific technique would cause disruption to an adversary”. MITRE Engenuity ATT&CK Evaluations: Enterprise now show we’re right : without having a 100% score of detection, we actually detect and remediate the major execution steps that actually disrupt the adversary’s attack path.
Each entity has its own cybersecurity needs and restrictions. Our philosophy at TEHTRIS is to be modular, adaptable and allow our customers to face the unpredictable, that’s why our tools include a variety of setup possibilities. This evaluation was a test to our default configurations, which we are improving every day to match the most recent threat actors’ TTPs.
TEHTRIS tools have been designed to hyperautomate cybersecurity operations, for enabling an automatic remediation immediately when an critical alert is generated by one of our security solutions.
This evaluation was very profitable as it objectively assesses the strength and weaknesses of our techniques and capabilities. We have taken into account every details to considerably improve our effectiveness.
How to go further with TEHTRIS XDR for optimum cyber coverage?
Artificial Intelligence
Use the full potential of CYBERIA, our in-house artificial intelligence (as the evaluation took place over a short period of time, it was not possible for our AI modules to learn about the environment and behaviour to produce relevant detections).
Network Traffic Analysis and Deceptive Response
Add our network solution bricks to predict attacks and detect weak signals on network activity. From our experience in real life, we clearly see initial reconnaissance that take place in attack paths as they always hit on our honeypots.
During the evaluation thought the attacker directly headed to specific hosts and IP addresses without having the noise of discovering other existing hosts.
XDR Spirit
United we stand! Think about interoperability with TEHTRIS Ecosystem’s trusted partner solutions (Email Protection, IAM, ZNTA, CTI, etc.).
In this use case, Proofpoint’s email protection and security solution would have prevented the phishing attack from the very first stage of Carbon scenario).
Limitations of this document
Disclaimer
The views and opinions expressed in this are those of TEHTRIS and do not necessarily reflect the views or positions of any entities they represent.
Purpose of Testing
The primary aim of an evaluation or test should be to assess a product’s actual ability to handle various threats in a real-world setting.
When vendors are overly focused on optimizing for a specific test, they may overlook other vital aspects of protection, performances, integrations, real-life examples, etc, as the resources dedicated to optimizing for a test could also be used to enhance overall protection, user-friendliness, integration with other tools, etc.
Narrow Focus
If vendors knows that MITRE Engenuity tests specific techniques or tactics, they might allocate a disproportionate amount of resources to these areas, neglecting other threats that are equally if not more important, like real-life everyday attacks.
Misleading Outcomes
A product that is tailored for MITRE evaluations may perform exceptionally well in that specific setting but might not be as effective in the real world against diverse and ever-evolving threats.
False Assurances
Customers who rely solely on MITRE test results or any other test results, might have a false sense of security, thinking a product will provide complete protection in all scenarios, whereas there is always a difference between theory/lab, and the real battlefield.
It’s therefore crucial for companies to keep the broader goal of threat protection in mind and not focus solely on scoring well in evaluations. Similarly, for consumers and businesses selecting security solutions, it’s vital to look beyond test scores and evaluate how a solution will function in their specific environment.


