Cybersecurity best practices for Small Medium-sized Businesses (SMBs)
If you are a SMB owner trying to strengthen your cybersecurity quickly but, most importantly, efficiently,... Read more

If you are a SMB owner trying to strengthen your cybersecurity quickly but, most importantly, efficiently,... Read more

RustyStealerDropper Use case A reminder: what are malware droppers?How do they stay in your systems?Deobfuscating a... Read more

TEHTRIS AI R&D team has developed from scratch an Artificial Intelligence based module called Cyberia eGuardian.... Read more

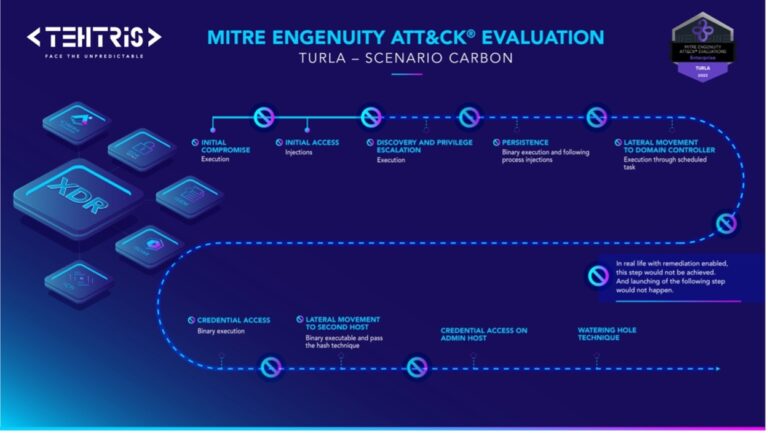
For the first time, TEHTRIS participated in the 2023 MITRE Engenuity ATT&CK® Evaluations: Enterprise. Using TEHTRIS... Read more
A malware powered by Artificial Intelligence is now capable to adapt itself to the targeted infrastructure,... Read more
In an Industrial Control System environment, let’s imagine the standard maintenance procedure in which files need... Read more

We hear about these new technologies every day, but are we really aware of their differences... Read more

As the threat landscape continues to evolve, the needs expressed by companies are changing. Chief Information... Read more

While XDR (eXtended Detection & Response) technology has become the benchmark in the cyber defense arsenal... Read more
