In an Industrial Control System environment, let’s imagine the standard maintenance procedure in which files need to be transferred inside an industrial site. For security reasons, automated systems are not connected to the internet to avoid security risks. And some maintenance operations need to be done by external contractors, who may not have access to the network. This situation generally leads to the usage of USB storage devices that are connected by third party companies. And it is common that the third party’s employee has to work in several industrial sites a day… using the same USB device.
What the employee did not anticipate at the third industrial site of his working day is that an autorun is executed and a ransomware spreads on the machine as he plugged his USB device. The antivirus solution installed on the machine instantly scans it, but it turns out that the malware escapes detection of the latest version of the antivirus solution. Then, the ransomware spreads laterally across the industrial network and encrypts crucial data.
If the company was protected by TEHTRIS XDR Platform, here is how your IT security team would be informed in real-time of the threat, and how the different stages of the attack would be automatically stopped.
Initial access
The starting point of this attack is a replication through removable media (T1091 on MITRE ATT&CK framework).
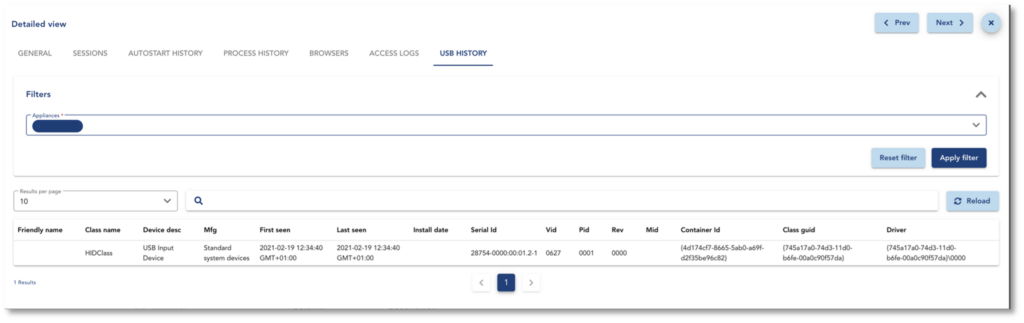
USB Monitoring module of TEHTRIS EDR detects every new USB device inserted on a computer. This raises alerts on inserting a new USB flash drive:

The module allows to remotely disable suspicious USB devices.
USB Monitoring module keeps a list of any USB devices that have been plugged to the computer – which is also useful for the investigation phase to trace back to the source of the attack.
Defense evasion
To evade detection, the malicious binary tries to disable security tools such as the antivirus protection, TEHTRIS EDR… This action is immediately prevented and triggers an alert based on TEHTRIS CTI (Cyber Threat Intelligence), which is natively integrated into the XDR platform and benefits all technologies – all binaries launched on an endpoint are automatically analyzed by TEHTRIS Antivirus powered by CyberIA, as well as in TEHTRIS’ sandboxes, to detect and stop the execution of malicious files. It is also possible to setup a configuration to monitor defense evasion technique (known as T1562.001).
Lateral movement
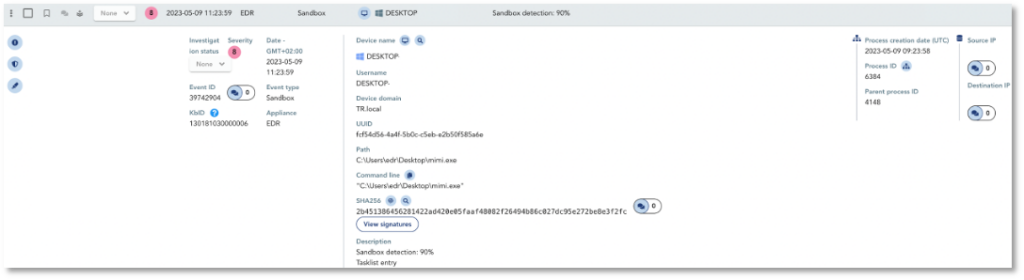
To obtain domain admin privilege stored in the victim’s memory due to misconfiguration, the threat actor performs credentials dumping using Mimikatz.
TEHTRIS tools detect the execution and the use of Mimikatz.
First, TEHTRIS CTI Sandbox analyses the binary and displays a high score via TEHTRIS EDR.
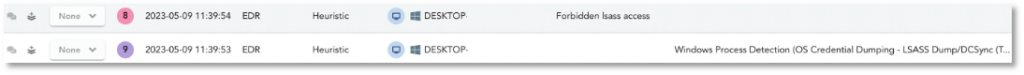
TEHTRIS EDR, thanks to a pre-configured monitoring rule, raises alerts when the very specific command line used in Mimikatz is detected, but also when Local Security Authority Subsystem Service (LSASS) is accessed.
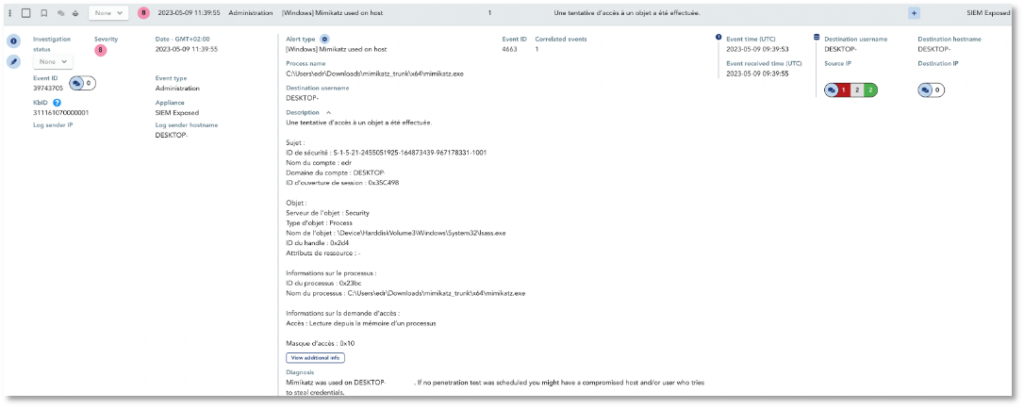
TEHTRIS SIEM detects the credentials dump via Mimikatz and raises the following alert:
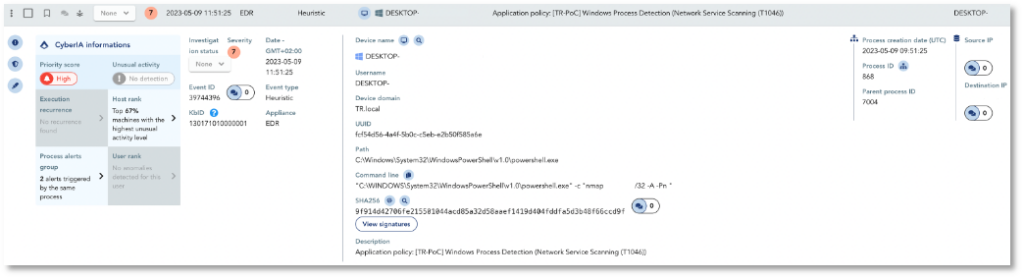
Then, the threat actor performs network discovery (T1046) using nmap to map the potential victims on Windows OS. TEHTRIS EDR raises the following alert thanks to a preconfigured monitoring rule.
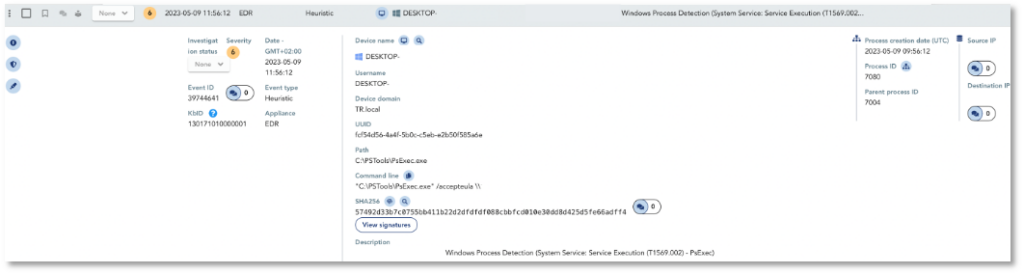
The threat actor executes Psexec to laterally move to other Windows devices (T1021). TEHTRIS EDR raises the following alert thanks to a preconfigured parameter.
Impact: prevent recovery and data encryption
The final steps of the attack consist in deleting shadow copies to prevent recovery (T1490) and then encrypting data (T1486). These very offensive actions are detected by TEHTRIS EDR and CTI and could be automatically prevented with the right settings:
- The command lines to delete shadow copies can be monitored by a configured parameter.
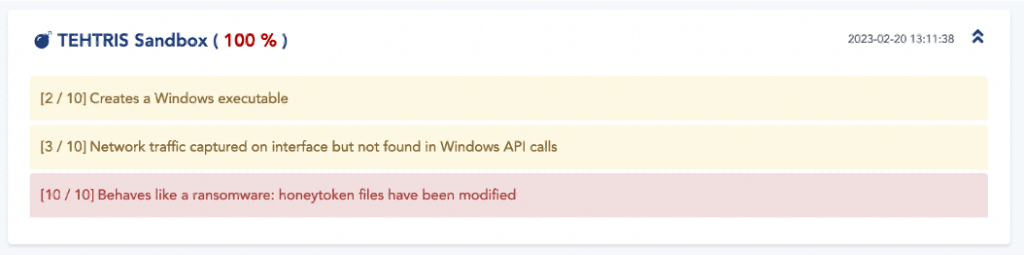
- When the final payload is executed, a dynamic analysis in TEHTRIS’ sandboxes detects the ransomware nature of the binary.
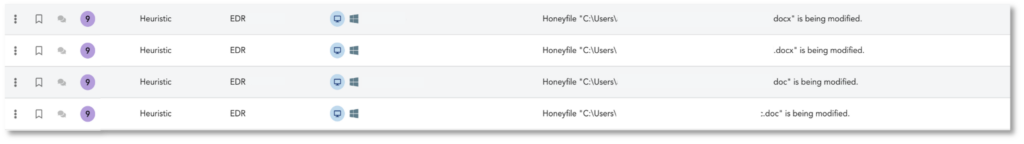
- The encryption of files will reach TEHTRIS’ honeyfiles, which were dropped in critical locations of the system, and doing so, will raise a heuristic alert with very high severity score. In order to respond to the emergency of a ransomware attack, every process linked to that event will be automatically terminated.
Conclusion
TEHTRIS XDR Platform unified cybersecurity tools help the industrial sector to be better protected and better prepared in the event of a cyberattack. Settings are customizable and can be set to alert-only or remediation, depending on the needs of the organization.
Initial access is usually due to human mistakes. But in this case, it is a legitimate industrial need: having third parties in charge of maintenance in industrial environments is very common. It is also a best practice from a cybersecurity perspective that their employees don’t have access to the network and that industrial systems are not connected to the Internet. All of which lead the subcontractors to use removable media.
But the cybersecurity policy handling the specific industrial systems should go further: inserting a USB key on an industrial device without any assurance that the USB drive is clean is not acceptable. The use of a dedicated device – known as a sheep-dip or decontamination station – to ensure that no malware is introduced by a removable media is recommended in this case. It is a good practice that employees and third-party contractors should be aware of. Also, people in charge of industrial systems should always follow subcontractors’ activities when they are on-site to avoid misjudgment of the cyber risks. Raising awareness among collaborators is key in this kind of business. Being assured of the cybersecurity awareness of subcontractors’ employees is just as important.
More information on how to protect strategic data against cyber-espionage here.

