A good understanding of active threats is necessary to achieve a good security posture. The following report provides actual trends that emerge from the Internet Background Noise based on the monitoring of two weeks of our Honeypots logs.
Check out our previous report here.
CVE-2023-27350 PaperCut exploit attempt
On the 2nd of July, one of our German honeypot captured the IP 198.23.251[.]118 hosted by AS 36352 (AS-COLOCROSSING) in the US. This IP address is scarcely known from public databases identifying malicious IP addresses.
This threat actor attempted to exploit CVE-2023-27350 (CVSSv3: 9.8) which is a critical vulnerability on PaperCut MF/NG servers. It turns out to be a Remote Code Execution (RCE) allowing an unauthenticated attacker to execute arbitrary code on the server. This CVE is publicly known since the beginning of May.
The threat actor targeted our German honeypot on port 80/TCP.
HTTP request analyzed by NTA:
GET /app?service=page/SetupCompleted HTTP/1.1 Host: x.xx.xxx.x User-Agent: Mozilla/5.0 (Windows NT 5.1) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/35.0.3319.102 Safari/537.36 Connection: close Accept-Encoding: gzipTEHTRIS recommends applying the latest patch. Check out the editor’s page for more details .
CVE-2017-7577 exploit attempts
This past couple of weeks, every European honeypots has been hit on port 80/TCP by the following IP address : 193.32.162[.]190 – hosted by AS 47890 (Unmanaged Ltd) in Romania.
Our honeypots were equally targeted as the graphic shows below:
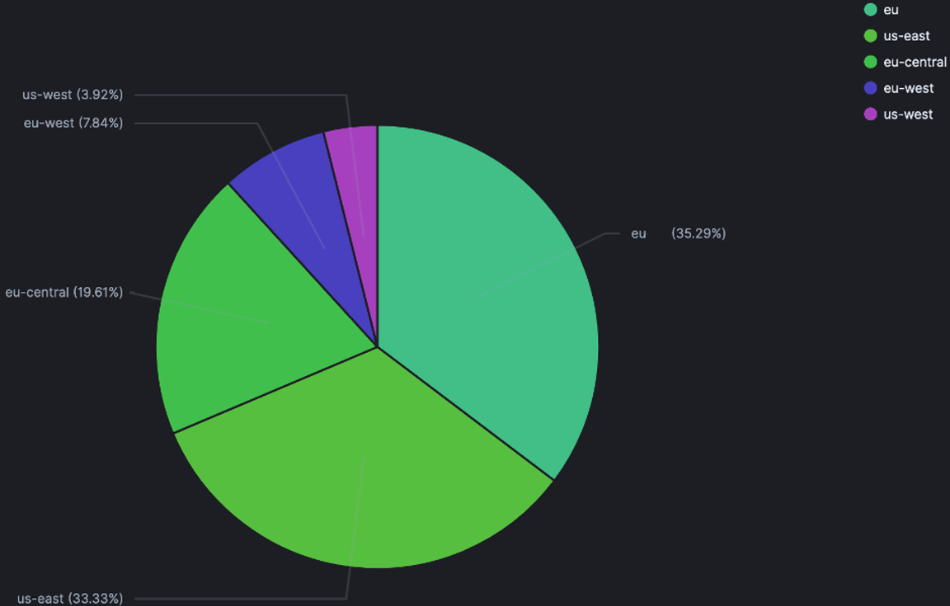
The threat actor was trying to exploit CVE-2017-7577 (CVSSv3: 9.8), a directory traversal vulnerability which affects Xiongmai/HiSilicon DVR and allows the reading of arbitrary files thanks to a GET ../ HTTP request. It is possible to use it for requesting user details for example. Of note, this CVE is not mentioned in CISA’s known exploited vulnerabilities catalog.
HTTP request analyzed by NTA:
GET /../../mnt/mtd/Config/Account1 HTTP/1.1 Host: x.xxx.xx.x User-Agent: Mozilla/5.0 zgrab/0.x Accept: */* Accept-Encoding: gzipWe monitored an increase in exploit attempts of this 6-years old CVE, at the end of June and the beginning of July.
RECENT CVE-2023-27997 EXPLOIT FEASIBILITY STUDY
The CVE-2023-27997 (CVSSv3: 9.8) last month, relates to FortiOS and FortiProxy SSL-VPN. Indeed, they contain a heap-based buffer overflow vulnerability which can allow an unauthenticated remote attacker to execute code using specific crafted requests.
According to bishopfox, it is possible to search for Fortinet servers returning the HTTP response header Server: xxx-xxx. This turns out to be a trustworthy fingerprint for devices running FortiOS. Then, it is possible to filter down on those that redirect to /remote/login, which is the path that exposes the SSL VPN interface.
Therefore the URL /remote/login allows the display of the VPN vulnerable interface. Looking for this request gives information to acknowledge the existence for the page in order to exploit it. It is the preliminary step before the exploit CVE-2023-27997 attempt.
On our honeypots, we captured this specific URL these past weeks. The IP address 179.43.142[.]226, which is known from public databases identifying malicious IP, hosted by AS 51852 (Private Layer INC) in Switzerland, targeted our European and North-American honeypots as follow:
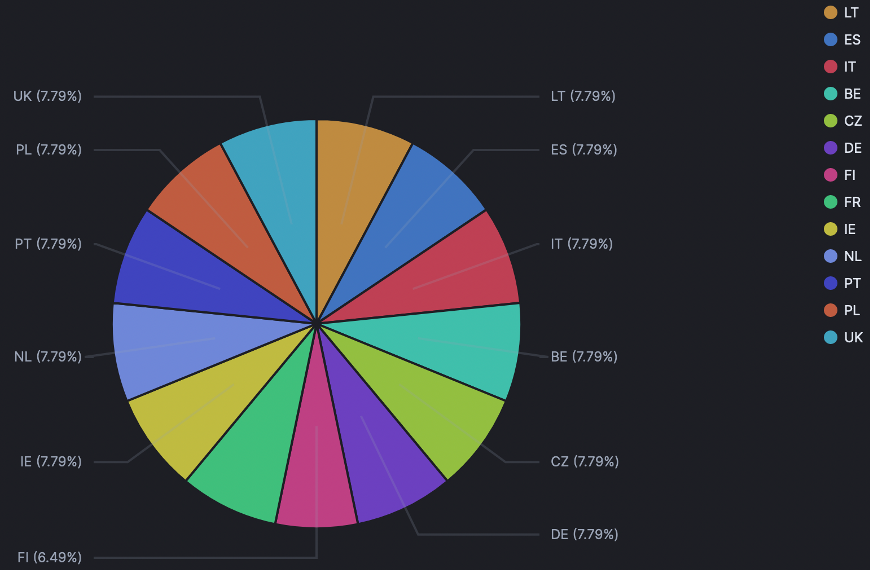
It really started on the 22nd of June and reached a spike on the 24th of June and on the 5th of July. But since the 6th of July, our honeypots stopped being targeted this way.
For the following steps of the exploit, TEHTRIS NTA monitors the URL, known for being vulnerability’s indicators of exploitation, including:
- /remote/hostcheck_validate
- /remote/logincheck
- /remote/info
TEHTRIS recommends applying updates per vendor instructions.
Bruteforce attack on Portuguese honeypot
Want to learn more on this subject?
More insights on this research issued from the alerts on our worldwide honeypots network.
Subscribe to our bi-monthly threat intelligence newsletter
Top ports/protocols targeted by threat actors
Want to learn more on this subject?
More insights on this research issued from the alerts on our worldwide honeypots network.
Subscribe to our bi-monthly threat intelligence newsletter
Information remain TEHTRIS sole property and reproduction is forbidden
TEHTRIS is and remains sole property rights owner of the information provided herein. Any copy, modification, derivative work, associated document, as well as every intellectual property right, is and must remain TEHTRIS’ sole and exclusive property. TEHTRIS authorizes the user to access for read use only. Except as expressly provided above, nothing contained herein will be construed as conferring any license or right under any TEHTRIS’ copyright.
No warranty and liability
TEHTRIS will not be held liable for any use, improper or incorrect use of the information described and/or contained herein and assume no responsibility for anyone’s use of the information. Although every effort has been made to provide complete and accurate information, TEHTRIS makes no warranty, expressed or implied regarding accuracy, adequacy, completeness, legality, reliability, or usefulness of any information provided herein. This disclaimer applies to both isolated and aggregated uses of the information.


