A good understanding of active threats is necessary to achieve a good security posture. The following report provides actual trends that emerge from the Internet Background Noise based on the monitoring of two weeks of our Honeypots logs.
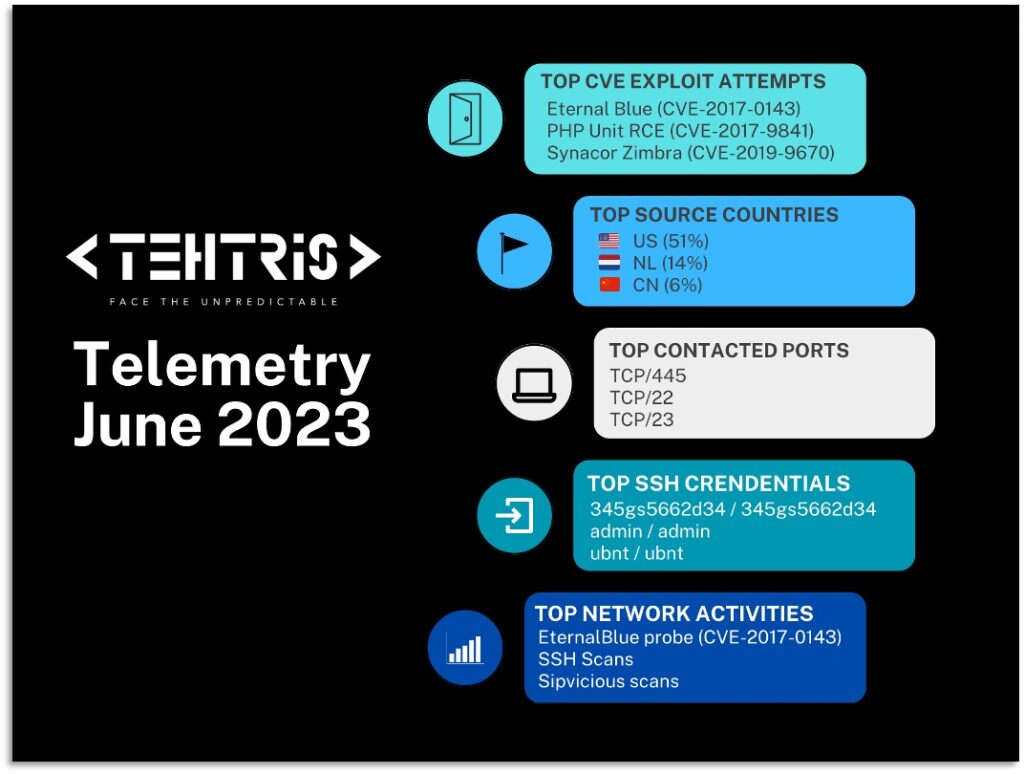
June 2023 Telemetry – overview
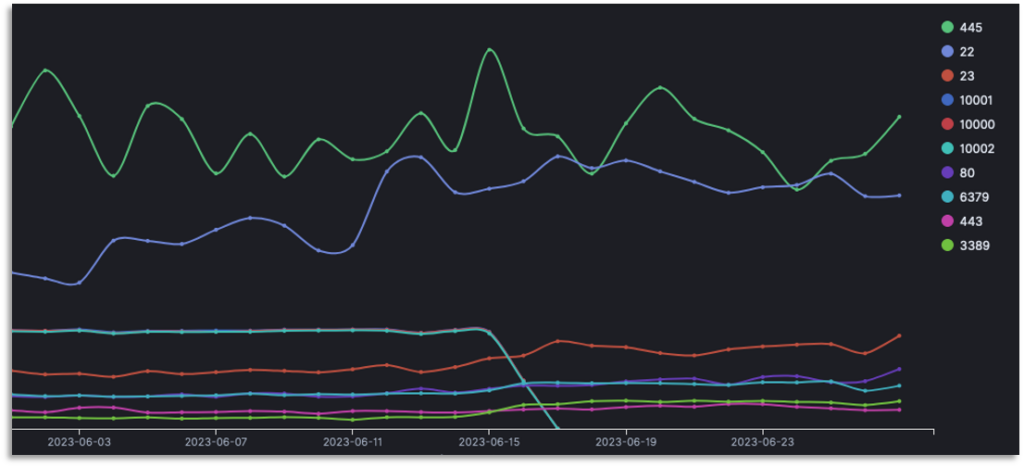
- Focus on a surge of requests on ports 10000, 10001 and 10002
Over the past month, we observed a spike in targeting ports 10000, 10001 and 10002 between the 22nd of May and the 17th of June, with a peak on the 29th May, targeting one of our Southeast Asian honeypots.
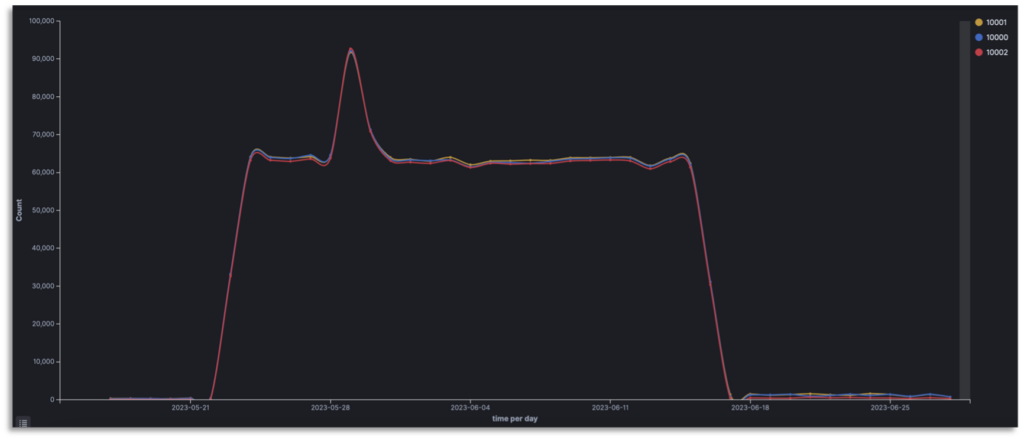
| Protocol | Port | % |
| TCP | 10000 | 33.435% |
| TCP | 10001 | 33.316% |
| TCP | 10002 | 32.971% |
| UDP | 10001 | 0.268% |
| UDP | 10000 | 0.01% |
6,625 unique IP addresses targeted our honeypots on those ports. We noticed a specific behavior for 495 of them, which sent as much as 95,000 requests to the same Southeast Asian honeypot.
Top 10 most exploited CVEs – June 2023
In June, an overwhelming majority of exploit attempts (99%) were EternalBlue exploits. Eternalblue aside, here are the top 10 most exploited CVEs by threat actors to gain initial access:
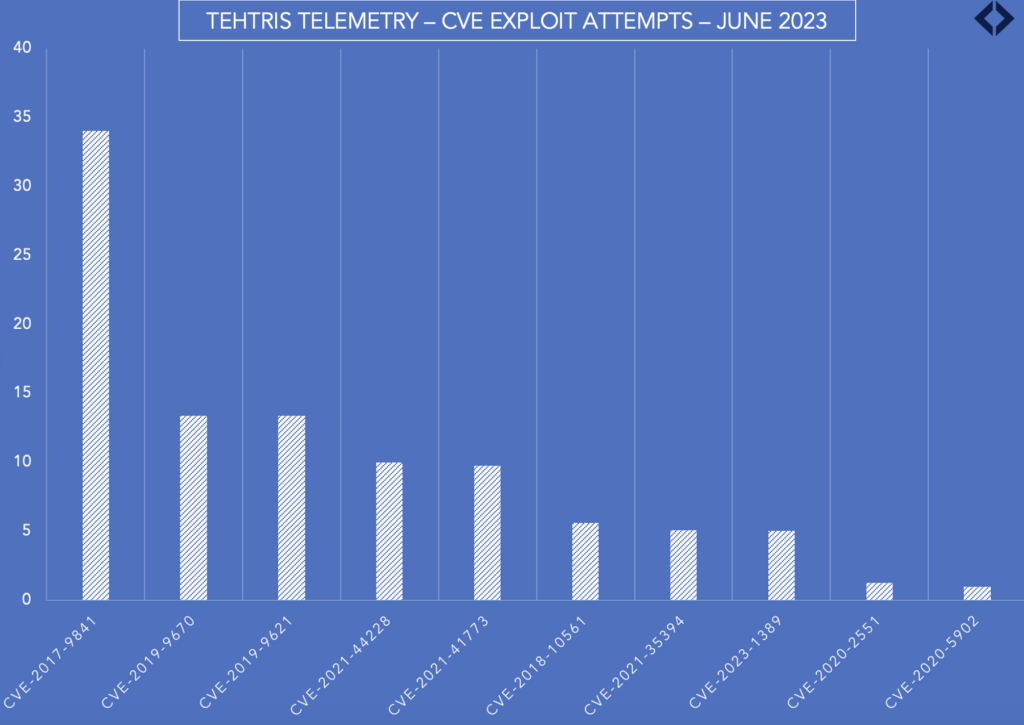
More information:
- CVE-2017-9841 (CVSS3.1 9.8) in PHP Unit which allows remote attackers to execute arbitrary PHP code
- CVE-2019-9670 (CVSS3.0 9.8) in Synacor Zimbra Collaboration Suite which has a XML External Entity injection (XXE) vulnerability
- CVE-2019-9621 (CVSS3.0 7.5), also in Synacor Zimbra Collaboration Suite, which is not mentioned in CISA’s known exploited vulnerabilities catalog.
- CVE-2021-44228 (CVSS3 10) in Apache Log4j2 which contains a vulnerability allowing for remote code execution
- CVE-2021-41173 (CVSS3.1 5.7) in Go Ethereum protocol leading to crashing
- CVE-2018-10561 (CVSS3.0 9.8) in Dasan GPON home routers allowing to bypass authentication
- CVE-2021-35394 (CVSS3 9.8) in Realtek Jungle SDK which can allow remote code execution
- CVE-2023-1389 (CVSS3 8.8) in TP-Link Archer containing a command injection vulnerability allowing for remote code execution
- CVE-2020-2551 (CVSS3 9.8), which is not mentioned in CISA’s known exploited vulnerabilities catalog and affects some versions Oracle WebLogic Server products allowing successful attackers to takeover Oracle WebLogic Server
- CVE-2020-5902 (CVSS3 9.8) in F5 BIG-IP Traffic Management User Interface which contains a remote code execution vulnerability in undisclosed pages
This illustrates just how old vulnerabilities and newer ones are included in threat actors’ arsenals to find and exploit vulnerable devices exposed over the Internet. TP-Link Archer’s vulnerability was disclosed in March 2023 and cybersecurity researchers have noted that it was quickly used by DDoS-as-a-Service botnet named Condi as well as being added to the Mirai botnet’s arsenal. TEHTRIS monitored a spike in June on our previous report.
Mozi botnet : update
To follow-up on Mozi botnet since our previous post, we keep observing constant attempts to spread the Mozi botnet, with a little decrease around the 15th of June.
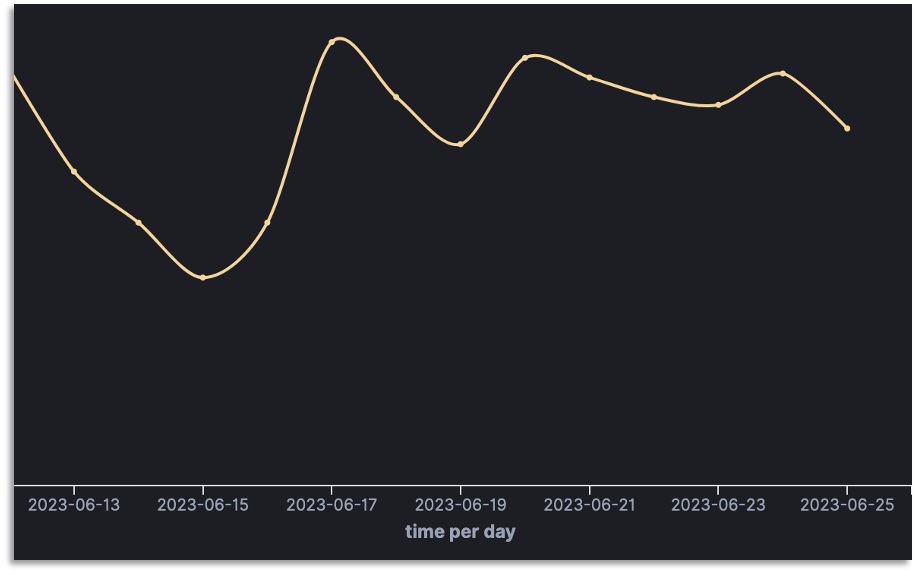
436 unique IP addresses attempted to exploit a Netgear vulnerability and a MVPower DVR Shell vulnerability allonwing remote command injection to download a file called Mozi.m from 180 different URLs.
Top 5 IP addresses conducting the attacks attempts:
| IP source | AS | Country |
| 49.143.32[.]6 | 9319 (HCN CHUNGBUK CABLE TV SYSTEMS) | KR |
| 120.86.252[.]247 | 17816 (China Unicom IP network China169 Guangdong province) | CN |
| 1.246.222[.]20 | 9318 (SK Broadband Co Ltd) | KR |
| 1.246.222[.]83 | ||
| 113.69.130[.]1 | 4134 (Chinanet) | CN |
At the time of writing, the Chinanet IP address was unknown from public database listing malicious IP addresses.
Our European honeypots were targeted in the following manner:
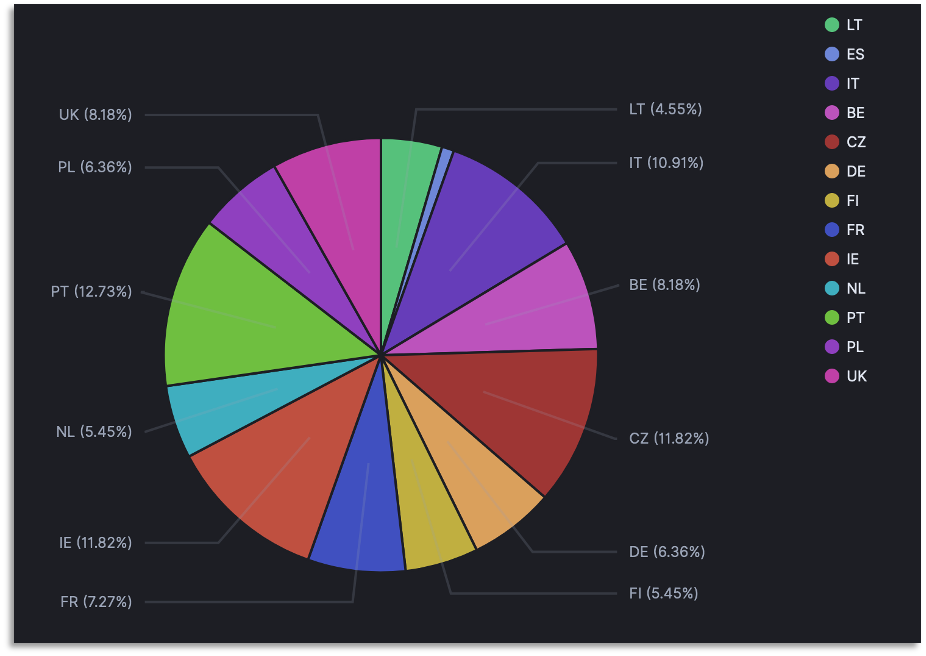
Origin of attacks
Want to learn more on this subject?
More insights on this research issued from the alerts on our worldwide honeypots network.
Subscribe to our bi-monthly threat intelligence newsletter
Romanian IP address targeting IoTs
Want to learn more on this subject?
More insights on this research issued from the alerts on our worldwide honeypots network.
Subscribe to our bi-monthly threat intelligence newsletter
Information remain TEHTRIS sole property and reproduction is forbidden
TEHTRIS is and remains sole property rights owner of the information provided herein. Any copy, modification, derivative work, associated document, as well as every intellectual property right, is and must remain TEHTRIS’ sole and exclusive property. TEHTRIS authorizes the user to access for read use only. Except as expressly provided above, nothing contained herein will be construed as conferring any license or right under any TEHTRIS’ copyright.
No warranty and liability
TEHTRIS will not be held liable for any use, improper or incorrect use of the information described and/or contained herein and assume no responsibility for anyone’s use of the information. Although every effort has been made to provide complete and accurate information, TEHTRIS makes no warranty, expressed or implied regarding accuracy, adequacy, completeness, legality, reliability, or usefulness of any information provided herein. This disclaimer applies to both isolated and aggregated uses of the information.


