A good understanding of active threats is necessary to achieve a good security posture. The following report provides actual trends that emerge from the Internet Background Noise. The following data is based on the monitoring of two weeks of our Honeypots logs.
SSH bruteforce attempts with variants of Password or Welcome
Several reports on most used passwords all over the world, such as one by SafetyDetectives or by Specop, show that a general trend regarding passwords is the use of password or welcome (and variations). And threat actors do know that.
Observations on SSH connection attempts on TEHTRIS honeypots over the past couple of weeks allow to confirm that “password” and “welcome” (and their variations) are indeed relentlessly tested by threat actors: over 17,000 times coming from around 6,304 IP addresses.
Below are the top 50 logins tested with either “password” or “welcome”:
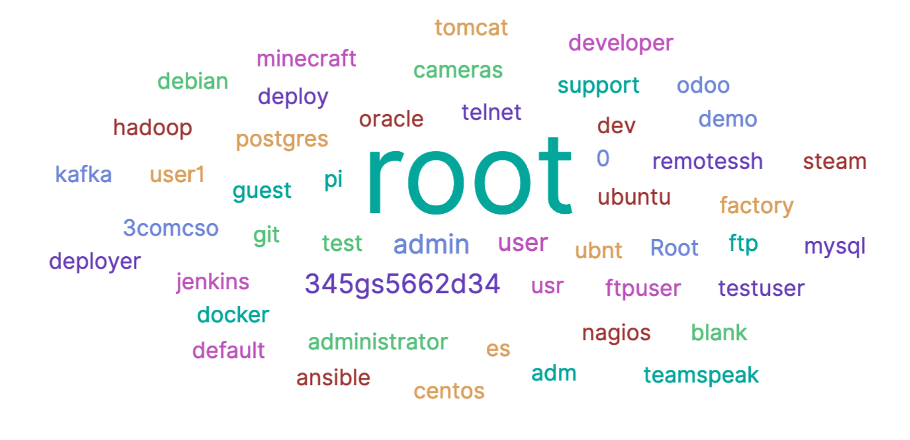
The top 10 IP addresses responsible of those SSH credential attempts are the following:
| IP address | AS | Country |
| 195.3.147[.]52 | 41390 (RN Data SIA) | LV |
| 193.105.134[.]95 | 42237 (w1n ltd) | SE |
| 61.177.173[.]16 | 4134 (Chinanet) | CN |
| 167.71.141[.]138 | 14061 (DIGITALOCEAN-ASN) | GB |
| 147.135.137[.]204 | 16276 (OVH SAS) | FR |
| 61.177.172[.]143 | 4134 (Chinanet) | CN |
| 51.83.70[.]228 | 16276 (OVH SAS) | FR |
| 61.177.172[.]147 | 4134 (Chinanet) | CN |
| 218.92.0[.]204 | 4134 (Chinanet) | CN |
| 106.12.122[.]62 | 38365 (Beijing Baidu Netcom Science and Technology Co., Ltd.) | CN |
Let’s have a closer look at what credentials threat actors bruteforce by regions:
Across all regions, 345gs5662d34 / 345gs5662d34, as well as admin / admin and root / root are in the top 5 of credentials most used by attackers. Everywhere, these three logins are tested with different types of classic passwords:
- 0
- 1234
- 123456
- admin1234
- password
- admin
Among the slight differences in different regions’ top 10 credentials that are most used by attackers are the following:
- The login user makes it in the top 10 in Canada
- pi / pi is seen in the US, South America and South Pacific Asia
- ubunt / ubunt ranks in the top 10 of Western Europe, North America, South Pacific Asia and South America
- factory / factory, 3comcso / RIP000 (which are the default credentials of 3Com SUPERSTACK II router) and cameras / cameras are only in the top 10 of Western Europe
To be on the safe side, you should follow ENISA’s recommendations regarding passwords: change default passwords and do not reuse passwords for multiple accounts, use complex passwords (more than 8 characters with alphanumeric and special characters). It is also recommended to use Multi-factor Authentication (MFA) to strengthen account security – a password alone is not enough.
Top commandlines when an attacker enters a system
After bruteforcing SSH credentials, the top two commandlines conducted one after the other by threat actors when entering the system are the following :
cd ~; chattr -ia .ssh; lockr -ia .sshFirst, the attacker uses those Linux utilities to unlock access to the .ssh file.
cd ~ && rm -rf .ssh && mkdir .ssh && echo “ssh-rsa AAAAB3NzaC1yc2EAAAABJQAAAQEArDp4cun2lhr4KUhBGE7VvAcwdli2a8dbnrTOrbMz1+5O73fcBOx8NVbUT0bUanUV9tJ2/9p7+vD0EpZ3Tz/+0kX34uAx1RV/75GVOmNx+9EuWOnvNoaJe0QXxziIg9eLBHpgLMuakb5+BgTFB+rKJAw9u9FSTDengvS8hX1kNFS4Mjux0hJOK8rvcEmPecjdySYMb66nylAKGwCEE6WEQHmd1mUPgHwGQ0hWCwsQk13yCGPK5w6hYp5zYkFnvlC8hGmd4Ww+u97k6pfTGTUbJk14ujvcD9iUKQTTWYYjIIu5PmUux5bsZ0R4WFwdIe6+i6rBLAsPKgAySVKPRK+oRw== mdrfckr” >> .ssh/authorized_keys && chmod -R go= ~/.ssh && cd ~Then, the attacker tries to delete SSH keys stored on the device. This permits to gain time before blue teams can access the system again to remediate the attackers actions. But it also permits to pull out other malicious actors from the machine. The attacker adds it’s own SSH key associated with username mdrfckr. This precise script had been associated in the past to a variant of the Monero miner Shellbot. We do observe a slight evolution in the threat actors’ TTPs since they now take into account possible file attribute protections and try to bypass them.
This behaviour is common in cryptomining attacks, as was underlined in the Color1337 campaign studied by TEHTRIS.
Surge of ZMAP scans
Monitoring the number of ZMAP scans on our honeypots, we observed a surge around the 23rd of April – as illustrated below.
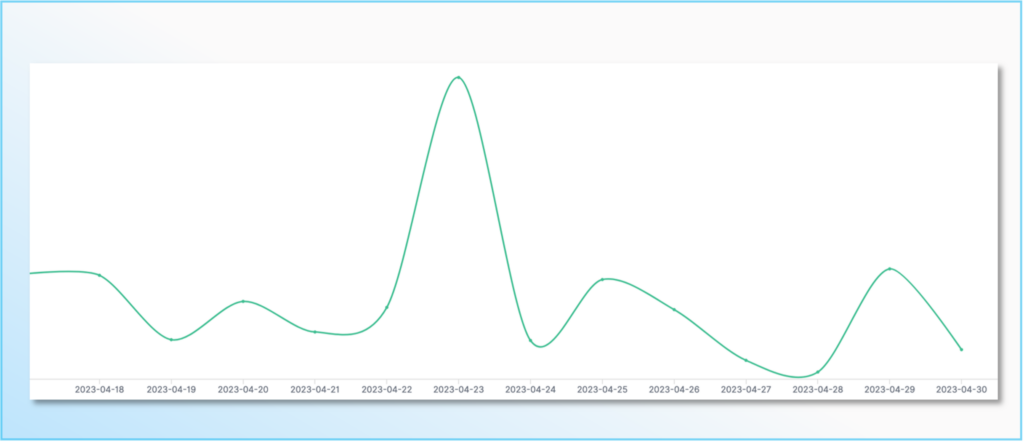
ZMAP is a large-scanning tools that can be used by cyberattackers during the reconnaissance phase to identify victims to conduct further malicious activities. It is not malicious per se – and actually, blue teamers and researchers also resort to these types of tools to identify vulnerabilities.
We observe massively requests on port tcp/80, as well as residual requests on port tcp/445 and tcp/22.
The top 5 IP addresses conducting these scans are known from public databases on malicious activities:
| IP address | AS | Country |
| 66.240.236[.]116 | AS 10439 ( CARINET ) | US |
| 64.227.146[.]243 | AS 14061 ( DIGITALOCEAN-ASN ) | IN |
| 142.93.115[.]5 | AS 14061 ( DIGITALOCEAN-ASN ) | US |
| 170.64.166[.]144 | AS 14061 ( DIGITALOCEAN-ASN ) | AU |
| 159.203.44[.]105 | AS 14061 ( DIGITALOCEAN-ASN ) | CA |
PHPUnit : 2017 vulnerability still exploited
Want to learn more on this subject?
More insights on this research issued from the alerts on our worldwide honeypots network.
Subscribe to our bi-monthly threat intelligence newsletter
Mozi botnet
Want to learn more on this subject?
More insights on this research issued from the alerts on our worldwide honeypots network.
Subscribe to our bi-monthly threat intelligence newsletter
Information remain TEHTRIS sole property and reproduction is forbidden
TEHTRIS is and remains sole property rights owner of the information provided herein. Any copy, modification, derivative work, associated document, as well as every intellectual property right, is and must remain TEHTRIS’ sole and exclusive property. TEHTRIS authorizes the user to access for read use only. Except as expressly provided above, nothing contained herein will be construed as conferring any license or right under any TEHTRIS’ copyright.
No warranty and liability
TEHTRIS will not be held liable for any use, improper or incorrect use of the information described and/or contained herein and assume no responsibility for anyone’s use of the information. Although every effort has been made to provide complete and accurate information, TEHTRIS makes no warranty, expressed or implied regarding accuracy, adequacy, completeness, legality, reliability, or usefulness of any information provided herein. This disclaimer applies to both isolated and aggregated uses of the information.

