Haven’t you ever quickly typed your favorite website on your computer, or with your supersonic fingers on your smartphone and then hit a key?
“wikipedia” becomes “wikipedai” if? You are human, you made a typo. Sometimes the link leads nowhere and sometimes it leads to a site that looks just like the right one, you have been a victim of typosquatting.
The phenomenon is not recent, but it still works. Why does it work? What is this simple yet effective technique?
Typosquatting vs Cybersquatting, what is the difference?
Typosquatting technique
Typosquatting is a form of social engineering attack. This technique consists in imitating a legitimate site. It is also called URL hijacking or domain spoofing. The cybercriminal buys a domain name similar to a legitimate site.
In concrete terms, this can be:
- a spelling very close to the official site
- an inversion of two characters
- homoglyphs
- hijacked domain extensions
- addition of a dash
- …
Example: “amazone.com” vs “amazon.com” (Amazon has bought the domain names Amazone.com so this case is redirected to the right site)
The objective for the hacker is to get traffic, clicks, visits thanks to the notoriety of the targeted site. The victim lacks vigilance does not systematically observe the domain name, and is trapped. They find themselves on a fraudulent Web site, almost identical, with a similar graphic charter, same design, same layout. All the criminals must do is retrieve the personal information.
Cybersquatting technique
The cybersquatting technique consists of using the name of the brand, buying a domain name corresponding to a brand. By reselling the domain name, the person can obtain a financial gain. In this case, the registered domain is similar to the trademark. This technique can be considered a form of unfair competition. It is therefore in the interest of the brand in question to purchase the various domain names that could be used.
Example: ” levis.com ” vs ” levis.fr “.
A typical case in France is that of the car glasses repair company Carglass.
Who hasn’t seen the Carglass commercial, which clearly states at the end of the spot to type the right address? “To be sure to arrive at our place, do not just type Carglass but Carglass DOT F R” For cause? The company refused the game of paid referencing imposed by the search engines. Their policy is to familiarize Internet users with the address of the site, to type the address correctly to avoid any risk of phishing.
If the address is misspelled, the link can lead to a humorous or satirical site, or to “related search” pages.
Typosquatting is often used to get the identifiers of the visitors of a site, via surveys, or a promotional offer, or a patch offer.
Attacks on the rise
Variant of typosquatting
This seemingly harmless technique is usually the start of phishing, malware transfer… The number of characteristic registrations of typosquatting or cybersquatting is constantly increasing.
The use of the most common domain names such as “.com” and “.net” is gradually decreasing. On the other hand, the use of the “.om” domain name is on the rise and domain name sales are constantly increasing.
According to a study conducted by a consulting firm High-Tech Bridge:
“The average lifespan of a fraudulent site is 1,181 days, or over 3 years. Cybersquatting sites have a life expectancy of 431 days.”
Recently a new form of typosquatting has been detected. This time the technique is not aimed at the average user but at the developer installing Python packages from the PyPI (Python Package Index) repository. The bad code was hiding in the repository. A package represents next-generation software supply chain attacks that rely on typosquatting.
In March 2022, it was the turn of Microsoft Azure developers to be targeted through malicious npm packages. Typosquatting was used to try to trick developers into downloading malicious files.
The list of malicious packages can be found here: https://jfrog.com/blog/large-scale-npm-attack-targets-azure-developers-with-malicious-packages/
Another example that we have already mentioned in a previous article: NFT, the new cybercrime paradise, concerns the attacks targeting NFT platforms that are constantly increasing.
Cybercriminals use domain names that impersonate these platforms, as was the case with Rarible.com. This leads to victims downloading malicious software.
Typosquatting can affect companies but also public services. The ANSSI (French National Agency for Information Systems Security) has identified the purchase of fake domain names resembling those of French institutionsAnother well-known example in the cyber world is John Zuccarini, who has been using this technique since 2001. He found about fifteen variants around the theme cartoonnetwork.com and 41 around the name of the singer Britney Spears. He was caught by the justice and sentenced to 30 months in prison and 164,000 dollars in fines.
The Russian group Nobelium (the same group responsible for the attacks on the software/publisher Solarwinds) is reportedly preparing for a typosquatting campaign. According to U.S. researchers, the group “has widely used typosquat domains in SSL certificates and will likely continue to use deceptive techniques, including typosquat redirection, when using Cobalt Strike tools.”
The consequences of such attacks
Typosquatting may seem simple and sometimes harmless, yet it can allow the cyber attacker to:
- retrieve login credentials and other personal data.
- install malicious extensions
- install keyloggers
- redirect the victim to a competitor’s website and thus lose a market
- develop hacktivism
- Damage the image of the website or brand by integrating content whose purpose is to damage the image of the official website.
What solutions to protect yourself?
At the legal level
Trademark law in France is regulated, but there are no specific texts yet, so there is still a legal vacuum. However, in the event of cybersquatting, the company can contact the organization where the disputed domain name is registered directly to have it removed.
Large companies, on the other hand, will go to the civil courts.
To recover a domain name, you must contact:
- For the English-speaking zone: the UDRP. (Uniform Domain-Name Dispute-Resolution Policy). The victim will then have to prove that the hacker has used an illegitimate domain name. The procedure is done online.
- For the FR and .re zone: the dispute resolution procedure is done via the PARL (alternative dispute resolution procedure) it works according to the same principle as the UDRP procedure.
At the technical level
To protect yourself from typosquatting we advise you to:
- mark your favorite sites
- check the spelling of URLs
- check the sender of the email
- make regular backups of your data on external media
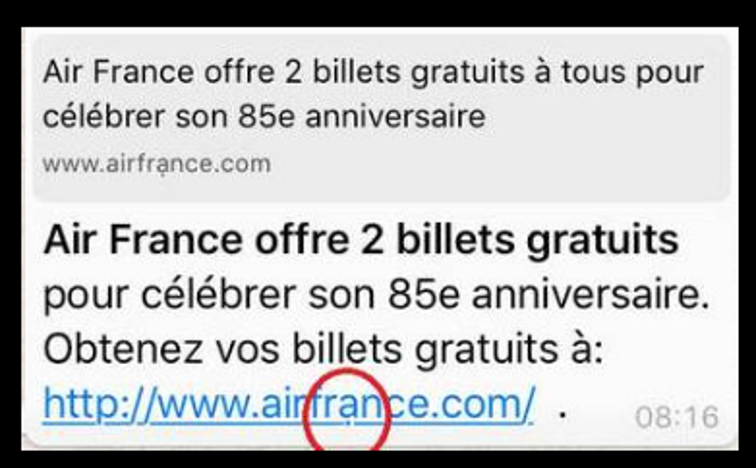
- check the consistency of the text of the e-mail (spelling, syntax, etc.) and to be vigilant with regard to overly generous offers (free airline tickets, etc.)
- update all the computer equipment
- check the traffic figures on the website (Google Analytics for example)
- configure and run the internal server of the domain name system, within a company
- use open-source tools that check if a typosquatting attack has already taken place: example dnstwist
- raise the awareness of staff
In addition to these good practices, we advise you to have security solutions capable of detecting and especially neutralizing in real time all malware. This is what TEHTRIS offers.
TEHTRIS EDR is equipped with numerous detection engines capable of detecting the most dangerous and recent advanced threats. It leverages TEHTRIS CYBERIA’s proprietary artificial intelligence and innovative neural network to detect and anticipate known and unknown threats in real time.
The AI engine uses the power of Deep Learning for continuous improvement in threat detection accuracy.
Through the orchestration of the TEHTRIS SOAR tool, integrated with the TEHTRIS XDR Platform, the TEHTRIS EDR agent responds hyper-automatically, at any time, without human intervention, directly neutralizing unknown cyber threats.
Découvrir la TEHTRIS XDR Plaftorm
Social engineering attacks are often based on the psychological manipulation of individuals and their weaknesses. Typosquatting is a good example of this type of attack. Nobody is infallible. Urgency, stress, inattention… everything is conducive to making a “bad move”.
“The price of freedom is eternal vigilance.”
Thomas Jefferson

