We consult it at least several times a day, and have a strong bond with it. It is a daily assistant that has become essential, and some people can feel lost without it. You will have guessed it, it is the smartphone.
The cell phone, so precious for the user, is also precious for cybercriminals since it is a real mine of information: bank accounts, e-mails, passwords or even photos are directly accessible. It can also store professional documents, more or less confidential. Nicknamed “mini-computer”, the cell phone is as exposed as a PC. If phone owners often forget this, hackers have not waited to adapt their cyber attacks to mobile devices.

A real danger in our hands
Looking at the numbers, we understand the appetite of hackers for data stored on smartphones:
– according to We are Social’s Digital 2020 report, there were 5.19 billion mobile users in the world in January 2020, or 67% of the population
– also according to this source, the average Internet user spends 6 hours and 43 minutes online each day
– according to GlobalWebIndex, this same user spends more than half (50.1%) of his time surfing the Internet via his mobile device
We can only observe that the pool is enormous. The choice of smartphone (iPhone, Android, Windows Phone) does not prevent the danger, because each device on the market has vulnerabilities. The same is true for the targets of these cyber attacks: individuals and organizations are targeted without distinction. According to Check Point, 97% of the companies have suffered a mobile malware attack in 2020.
The danger is real and omnipresent. It is even exacerbated by the fact that, generally, users are more wary on computers than on mobiles. Yet, cyberattacks are just as common there.
Cyberattacks that target users on cell phones
Hackers target computers and mobiles with the same interest. They have the same techniques to defraud (phishing, exploiting vulnerabilities, spyware…) and create cyberattacks to affect smartphone users as well.
Smishing
We frequently hear about phishing. There is a mobile version called smishing (SMS phishing). The principle is the same, i.e., to obtain personal information, but this time the cybercriminal uses fake SMS messages. He pretends to be a publicly known company, a bank or an administration to trick the recipient into clicking on a link. The practice used is that of social engineering.
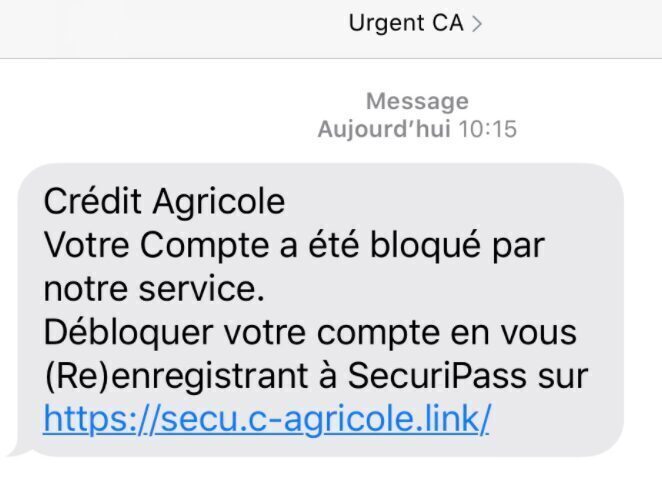
SIM Swapping
There are security holes, such as zero-day, on computers, and similarly, there are on cell phones. Attackers fall prey to them and create new fraudulent techniques.
This is the case of SIM Swapping, of which the co-founder of Twitter, Jack Dorsey, has been a victim. The principle is as follows: the criminal impersonates the victim and contacts his cell phone operator. He pretends to have lost or had his smartphone stolen. Thanks to the portability, he asks to transfer his number to a phone with a different SIM card. Calls and SMS being redirected, the hacker is free to ask for temporary connection codes by SMS to organizations and service companies.
Attacks via malicious applications
Malicious applications are another scourge on mobiles. They take many forms and use different techniques.
One of the best known is the Trojan, which is used 95% of the time. It consists of luring the owner of the phone to deposit a backdoor, an operating flaw or rootkits (stealth malware), to then spy discreetly, delete or modify data. This is the case of Android.Bankbot, which in 2015 posed as an official online banking application. 100,000 users of the affected bank reported a loss, amounting to over 2 billion rubles in total.
A malicious application can also contain spyware, which allows to retrieve a maximum amount of information. This is the case with Strandhogg 2.0. which can pretend to be a legitimate application and allows the hacker to take control of all applications on an Android. Another well-known example is Pegasus, an application that installs invisibly for the user. It offers many possibilities to the cyber attacker: listening to calls made and received, reading Signal or WhatsApp messages, retrieving the device’s content (photos, emails, contacts, SMS…). In addition, this malicious application can remotely activate the phone’s microphone or extract very precise GPS coordinates, encrypted files, and messages.
Injection attacks
The technique of an injection attack consists of entering an SQL query in an input field in order to communicate directly with the server. The attacker can then access the entire database, modify the contents and compromise the security of the device as a whole.
Discovered in 2017, Dvmap was the first code injection malware for Android. Its mission was to infect devices by bypassing Google Play Store security systems. While this technique is still in its infancy, it shows that the ingenuity of cybercriminals has no limits.
This list is not exhaustive and there are many ways to access data on a smartphone. With the help of different cyber attacks, hackers can read SMS messages, listen to conversations, unlock a SIM card and access our location and contacts.
Being aware that the danger is the same on a normal workstation as on a smartphone is an essential first step. However, it must be completed by complementary steps, such as adopting an effective security solution for mobiles. TEHTRIS brings you this solution through its MTD technology.
We have therefore built this article around two main axes. The first one gathers the threats and the risks linked to the use of smartphones, let’s see in a second one the solutions to bring.
[1] Erwan Sojae – Digital 2020 report – global digital overview – January 2020 https://wearesocial.com/fr/blog/2020/01/digital-report-2020/
[2] Check Point Software Mobile Security Report 2021

