In a recent press release, TEHTRIS announced its new partnership with Proofpoint in order to fight against fraudulent emails, and more specifically against “phishing” attacks.
But what exactly is “phishing” and how does it work?
We will try to explain how and why this technique is still a real threat today, and how to defend yourself. And of course we will describe why the TEHTRIS XDR Platform combined with the Proofpoint solution can help. A look at this attack technique that is still as formidable as ever in terms of effectiveness
The well-oiled mechanisms of a phishing attack
To be successful, everything has to look real.
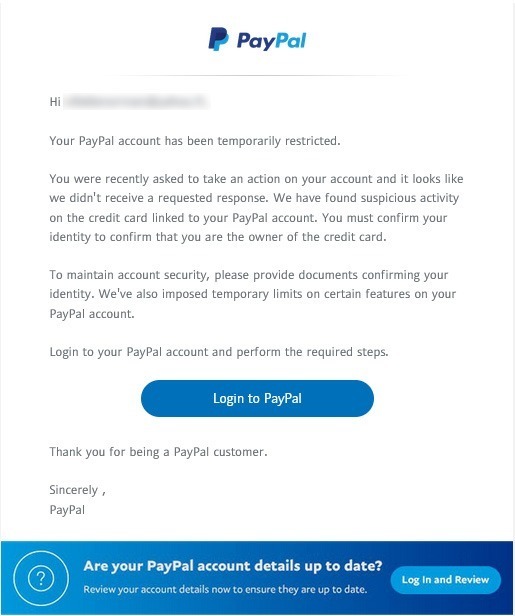
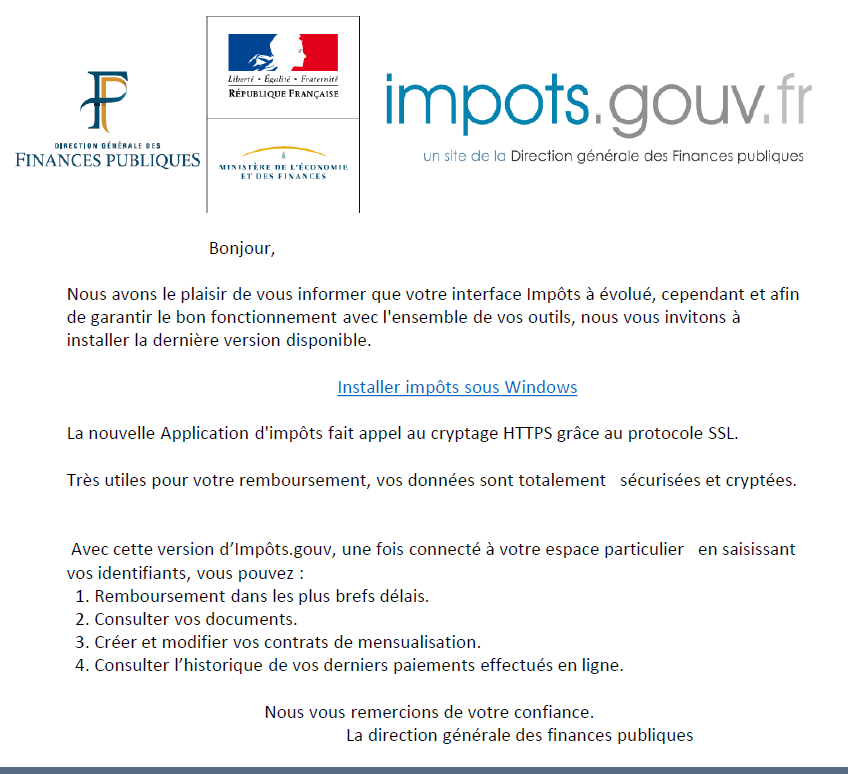
The phishing technique consists in making the victim believe that he is addressing a trusted third party (bank, administration, public organizations…) and that he can, without fear, provide him with the requested information. And of course, this information is usually personal data that will be used by the fraudster to perpetrate an identity theft.
Today, we all receive hundreds of “spam” e-mails announcing that we have won the national lottery or that an old distant cousin is leaving us his entire fortune.
All these mails are usually placed directly in the “junk mail” folder by systems that have learned to detect them: spelling mistakes, email addresses coming from a country known to be hostile, formatting errors, wrong email headers, etc…
However, some of these phishing emails end up in our inbox, and many (too many) people are fooled by their particularly well done content, both from a technical and visual point of view.
These are usually well-prepared campaigns, and the victims are chosen.
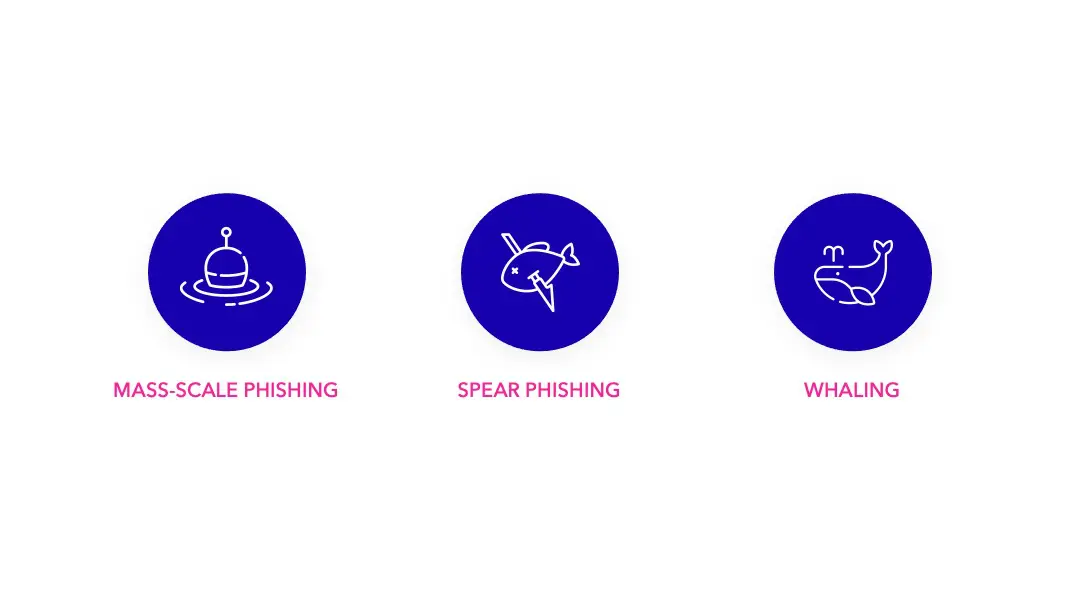
The attackers will work on their campaign, and carry out a real “screening” work. The screening of their targets will go through a multitude of steps: use of social networks to identify individual characteristics, theft of data collected by certain websites (cookies are gold mines for attackers), infiltration into the chat rooms of “customer support” to retrieve user bases, etc…
And for some campaigns, the attackers’ work goes even further. They try to get in touch with the targets to create a link and gain their trust. This is called spear-phishing and not phishing.
Finally, there is a last technique, which is called “Whaling“. This is a very advanced form of spear phishing that targets very important people in an organization. Whaling is a very prepared, complex but generally very effective attack.
Some figures
Numerous reports in 2020 show the impact of phishing on businesses (*/**)
A recent report from the FBI and the Internet Crime Complaint Center (IC3) supports these statistics. They received a record number of complaints from U.S. citizens in 2020. More than 241,342 victims came forward, not including all those who do not. According to Proofpoint in its seventh annual “State of the Phish” report, one out of every two companies in France and Germany is a victim of a successful phishing attack.
While phishing remains inexpensive for criminals to implement, it is for victims.
BEC (Business Email Compromise) attacks, which combine the 3 methods described above, cost U.S. businesses over $1.8 billion in 2020.
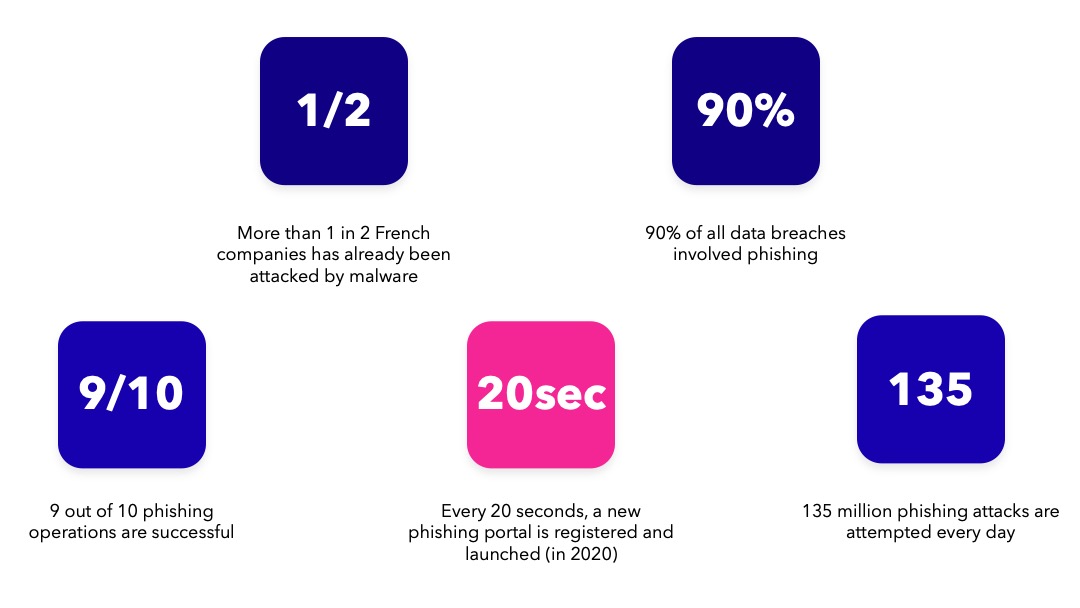
All of these figures are dizzying, but prove that in 2021, the threat is still very real and costly for companies. Not to mention the tightening of national laws that can cost hundreds of millions of dollars in penalties for personal data loss.
But whatever happens, whatever the target or objective, and whatever the technique used, the attacker will always exploit the same flaw: human weakness.
Whatever happens, whatever the target or objective, and whatever the technique used, the attacker will always exploit the same flaw: human weakness.
Why does “the fish” (still) see the bait and not the hook?
One of the strengths of cybercriminal groups is their organization and mastery of all the techniques necessary to achieve their goals.
As we know, gangs know exactly what they want, and they know how to get it.
Organization is key, but they also understand that they must master the art of war.
Technological warfare of course, but also psychological warfare. Being able to master the psychological weaknesses of the individuals they target, knowing how to manipulate human beings to perfection is one of the keys to their success.
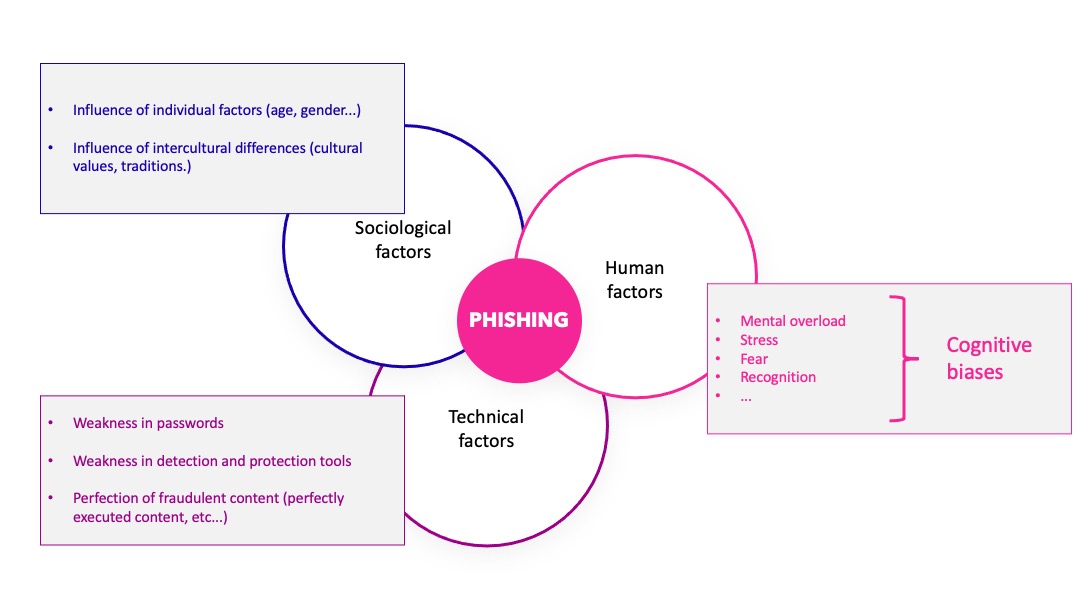
Phishing, spear-phishing and whaling derive their effectiveness from the fact that they rely on weakness.
The weakness of the human being on the one hand… And this is probably the most complex to manage because it involves psychological and social notions that are very difficult to control and channel. Les biais cognitifs sont des perturbateurs de la réflexion qui conduisent la plupart du temps aux mauvais choix.
Social engineering and the attacks that follow exploit weaknesses in human decision-making that are systematically associated with cognitive biases.
Attackers know that when a person is at risk of losing something, such as their data or money, they are very quick to make riskier and more hasty decisions.
And this is due to a cognitive bias associated with what is known as the framing effect. A person’s decision making is shaped by how the question is asked, and by whom it is asked. If the questioner represents an authority (police, bank, boss…), then the victim will respond quickly for fear of being reprimanded.
In a situation of intense stress, or overload of work, a fragile or sensitive person will misjudge a situation, an e-mail, a file and will click.
There are more than 200 biases, so many loopholes, that the attacker can use to achieve his ends.
And on the other hand, the technological weakness that allows attacks to slip through the cracks of a net that is always too permeable.
But then can we fight?
As you can see, phishing attacks are still numerous, and their number is growing. Their efficiency
remains formidable, and their consequences are sometimes devastating.
But it is possible to fight, and to do so, we must be organized on 2 fronts: awareness and protection.
The Hack-it-In conference in which TEHTRIS participates is an example, with the ENSEIRB-MATMECA partnership which offers many conferences on various concepts such as hacking, cyber-espionage, cyber-surveillance, but also offensive and defensive techniques that are in the news.
Here is another action encouraged by the Bordeaux nugget, this time, it is an awareness campaign about the cyber world realized by high school students:
Educating on vigilance is a constant task, and it is up to each of us to teach our family members, colleagues and friends how to detect, read or understand that we are the target of a fraud attempt.
Protection, on the other hand, is a matter for specialists, as it requires a multitude of technological know-how.
This is why TEHTRIS and PROOFPOINT have joined forces. Proofpoint’s Targeted Attack Protection (tap) offers an innovative approach to detecting, analyzing and blocking advanced threats that target the workforce. It also provides unique visibility into these threats and provides intelligence to TEHTRIS to ensure best-in-class multi-layered protection. The TEHTRIS XDR platform improves the productivity of technical teams with unprecedented detection and response capabilities. It unifies its components into a single platform to eliminate network blind spots.
By combining the cutting-edge technologies provided by the TEHTRIS XDR Platform with Proofpoint’s technical capabilities (Email Protection and Targeted Attack Protection), we offer our customers two main advantages:
- A double vision, both on the desktop and on the email content, to ensure powerful filtering and optimal protection.
- Hyper automation to reduce intervention and remediation time.
This technical partnership provides joint customers with the ability to protect their staff and endpoints from today’s threat landscape. It provides additional security benefits and increased visibility.
Conclusion
The fight against cyber-attacks, and in particular against fraudulent e-mails, is a complex but indispensable battle.
As we have seen, phishing and its derivatives are among the most profitable attacks to date, and remain the least detected.
By combining their expertise and solutions, TEHTRIS and Proofpoint now offer the most comprehensive solution for early and automated detection of fraudulent emails in Europe.
This association marks the beginning of a new era in the fight against phishing, which is now known to be one of the most formidable cyberattacks due to its impressive effectiveness.

