“Collective attacks by saturation of service” is now the French expression to talk about DDoS attacks (distributed denial of service attack) that dominate the headlines of cybercrime.
Cybercriminals are expanding their attack techniques, even if DDoS attacks are not new, the news has put them in the spotlight, becoming a growing threat, causing several damages that can be serious:
- risk of business disruption, or even service interruption with financial repercussions and a damaged reputation.
- risk of hiding a more serious and deep attack in the system
… and unlike more powerful cyberattacks such as ransomware, once the attack is over, DDoS leaves no trace on the victim.
This is an opportunity to analyze this type of attack, to understand how it works and to review the trends of this threat.
What is a DDoS attack?
A Distributed Denial of Service (DDoS) attack is a malicious activity carried out by a cybercriminal to disrupt the normal traffic of a server, service or network.
The attacker overwhelms the target with unwanted Internet traffic, resulting in:
- a much slower than normal response to requests
- a malfunction of the requests, of the Web resource
To do this, it will use a security hole or malware to sneakily infect machines in order to take control of them. Each infected device, called a “bot” or “zombie,” becomes capable of participating in DDoS attacks. Armies of bots called “botnets” leverage their numbers to gain power. In addition, these bots typically spoof IP addresses, which anonymizes malicious activity.
These botnets can be purchased through “attack for hire” services. This allows malicious but untrained and inexperienced individuals to easily launch DDoS attacks on their own.
Network resources, such as web servers, can only handle a limited number of requests simultaneously. In addition to the server capacity limit, the channel that connects the server to the Internet also has limited bandwidth.
The network resources are limited in managing the number of requests, they saturate and create a malfunction.
There are 3 types of attacks:
Volumetric attacks
These are the most common attacks. They consist in sending a significant number of requests from a large number of machines to a single infrastructure in order to overload its bandwidth. As a result, the targeted infrastructure will be saturated and unable to process all these seemingly legitimate requests.
In a UDP flood attack, cyber criminals seek to flood the target’s ports with IP packets containing stateless UDP protocol. The targeted infrastructure will request the applications associated with the UDP packets, and if they are not found, will return an “unreachable destination” message to the requester. The infrastructure will no longer be available.
To conduct DNS amplification attacks, the attacker can query:
- authoritative servers for zones with large records.
- recursive servers.[1]
responding to questions from the Internet.
Protocol attacks
This type of denial-of-service targets network communication protocols in order to take advantage of their weaknesses. It consists of exhausting state tables by using all the resources of servers or network equipment such as firewalls.
SYN flood: The TCP protocol allows the connection between a system (client) and a service (server) in three steps: the client first sends a SYN message to the server it is targeting. The server replies with a SYN-ACK message. Then, the client sends an ACK message to definitively open the connection. In a denial-of-service attack, cybercriminals send a large number of SYN requests without completing the other connection steps. Eventually, these partial connections occupy all the ports of the targeted server, so that it cannot receive any new connection requests.
Bounce attack (ICMP-Internet Control Message Protocol): the attacker will rely on the target’s ecosystem of subcontractors or service providers in order to carry out his attack at the network level. The attacker sends a packet to a broadcast network address resulting in an automatic response from each host. The ICMP protocol is used for error messaging and can accompany TCP protocol packets that allow exchanges on a network between application programs and computer terminals. With this method, the number of responses triggered will overwhelm the targeted service.
Attacks at the application layer
The objective is to impact web applications. Some attacks aim to exhaust the processing capabilities of the targeted service. For example, a cyber attacker may seek to reach the limit of the number of simultaneous requests a web server can handle. Other types of application attacks seek to consume all of a server’s computing resources by initiating a large number of TLS (Transport Layer Security) sessions. It is also possible to exploit weaknesses in the design of a web application.
In detail
By the numbers
- DDoS attacks are generally short-lived, with Cloudflare estimating them at around 20 minutes.
They tend to decrease. Attacks lasting five to nine hours remain in second place (3.16% of attacks); while those lasting 10 to 19 hours were in third place (1.60%).[2]
- It’s worth noting that “only 10.5 percent of attacks last between one and six hours, and most last less than 15 minutes.” (source: Imperva DDoS Threat Landscape report)
Nearly 70 % of companies surveyed experience between 20 and 50 DDoS attacks per month.[3]
- The first half of 2022 saw an increase in DDoS activity worldwide.
- In France, there were over 9 million DDoS attacks in 2021.
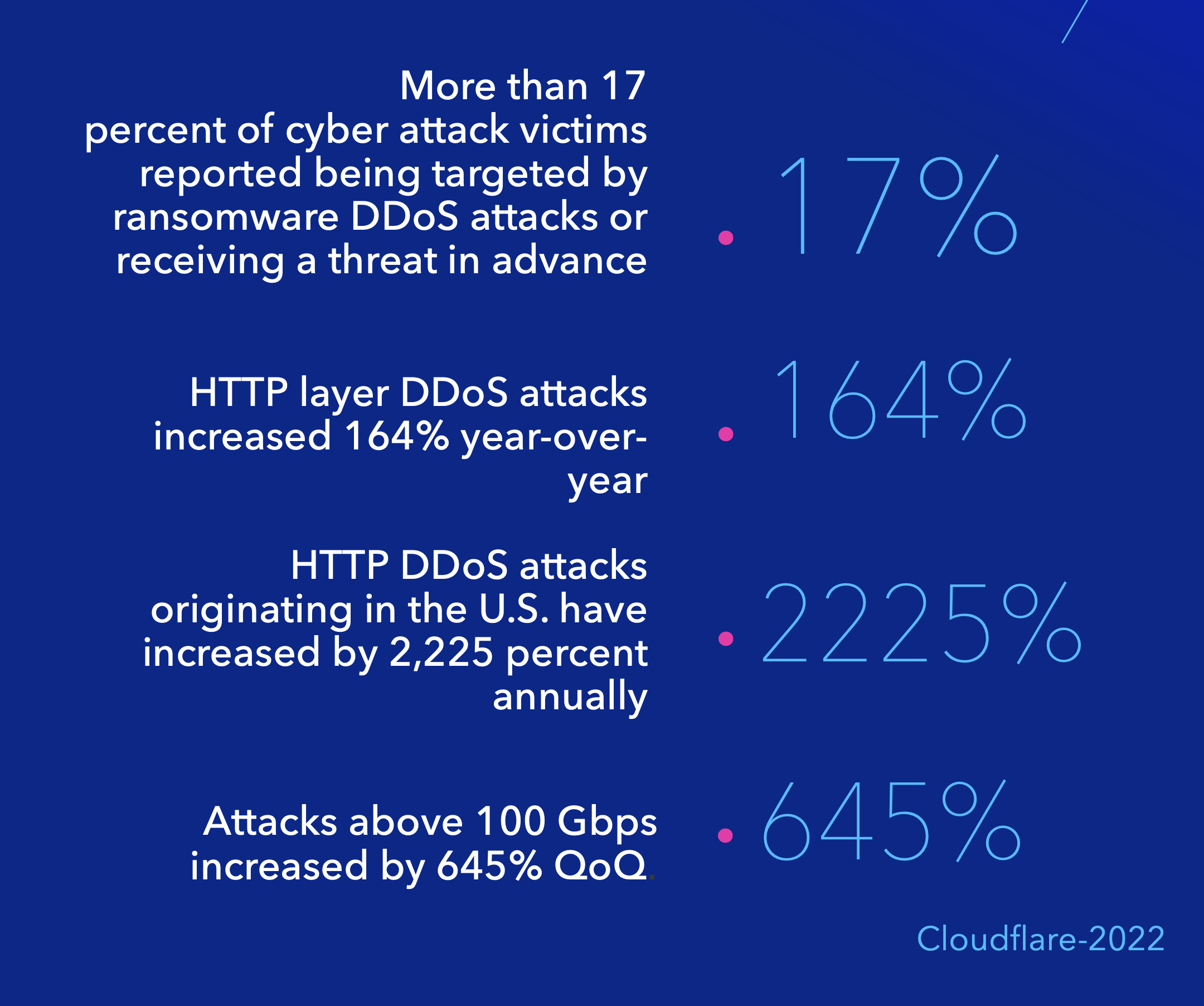
- In terms of targeted industries, it was found that software vendors experienced a 606% increase. Insurance agencies and brokers also with an increase of 257% and the IT sector an increase of over 162%.
- An attack can be costly. According to a Corero survey, the impact can be as much as $50,000 in lost revenue.
Geographical overview
- According to Spamhaus, the country with the most botnets is China, with over 820,000 bots.
India is the second largest country, with just over 800,000 bots, followed by Iran, which has about 400,000.
- Most application layer attacks in 2022 occurred in Japan (+105% vs. 2021)[4] and Taiwan (+200%, vs. 2021). And the most attacked sectors remain the high-tech and telecom companies, followed by the gaming industry.
Another interesting fact to note is that China has replaced the United States as the main source of attack traffic, with an increase of 29%, closely followed by India (61% increase), then the United States and Brazil. Note that Brazil is a growing player in the cyber ecosystem.
- Most network layer attacks in 2022 will take place in the US and Singapore.
They mainly affect the gaming and telecommunications sectors. The source of these attacks comes from Azerbaijan, Tunisia.
The DDoS of all records
Distributed denial of service (DDoS) attacks have reached “unprecedented” levels in the last two years, and are now measured in terabits.
- November 2021, Microsoft was able to stop a DDoS attack at 3.47 Tbps
- A variant of the Mirai botnet launched a 2.5 Tbps (terabytes per second) attack, the target was a Minecraft server named Wynncraft. This was a volumetric attack.
- In January 2022, North Korea suffered a DDoS attack that lasted about six hours.
- Another version of the Fodcha DDoS botnet also appeared. The botnet now uses encryption to establish communication with the C2 server. When it was created in April 2022, it had 100 victims per day, now it has reached 1000. It has also attacked a cloud service provider (1 Tbit/s).
- Before Google, it was the company Cloudflare that in June 2022 stopped a DDoS attack of 26 million requests with just over 5000 machines.
- On June 27, 2022, a Chinese company specialized in telecommunications was the target of a DDoS attack that would have lasted 4 hours and reached a peak of 3.9 million requests per second.
Trend
The geopolitical situation in the world, the pandemic, and the evolution of the attack surface have created multiple possibilities of aggression of which DDoS is a part.
Why such a trend?
The geopolitics involved
DDoS attacks are also a means of expression to show political support or opposition. The Russo-Ukrainian war is an example.
Indeed, patriotic hacktivism has exploded with the tensions between pro-Russians and pro-Ukrainians.
Russian online media companies were the most targeted industries in Russia in the first quarter of 2022. In Russian and Ukrainian cyberspace, the most targeted industries were online media and broadcast media. [5]
- A pro-Russian group: NoName057, has even created a participatory project called “DDOSIA” that pays volunteers (13,000 members on their Telegram channel today) to launch DDOS attacks against the nation’s enemies. In return, the volunteers leave with a bonus ranging from $300 to $1250.
- In July 2022, Killnet launched several DDoS attacks on infrastructure targets, airports, Lithuanian government websites.
- On August 16, 2022, 7.25 million bots targeted the website of Ukrainian nuclear power plant operator Energoatom for three hours.
Each defends their nation with denial of service attacks, with the goal of inflicting havoc on their targets, causing economic or social disruption.
Following the tensions between China and Taiwan, there has been an increase in this type of attack.
The Web is the new battlefield and a power play.
The race to compete
There is also an increasingly fierce competition, all means are good to weaken the competitor, recover market share, or achieve reputation.
Solana, which hosts many DeFi projects (Decentralized Finance, or “DeFi”, is a digital financial infrastructure), went down for the fourth time in twelve months as a result of multiple DDoS attacks in December 2021. These outages hurt its image as the site attempted to position itself against Ethereum. [6]
Cybersecurity researchers are also seeing more and more cases of former employees using this method to get back at their former employers.
The emergence of new cybercriminals
The emergence of ransomware attacks is not to be ignored and they have a name: RDDoS, DDoS extortion attacks. The goal of an RDDoS is to financially extort the victim by taking their website offline. The addition of extortion is the new thing.
Attackers use these attacks a lot to divert the attention of security teams to conduct more stealthy and sophisticated attacks that are difficult to attribute.
More about Cyber Gangs: Cyber Gangs, the mafias of the future?
But very surprisingly, the attackers themselves fall victim to them. On August 20, 2022, LockBit was knocked out by an attack of 1000 servers and 400 requests per second for each malicious domain.
A week later, ALPHV was the victim, and since then other ransomware gangs have been affected.
Who are behind these attacks? Rival gangs? Intelligence services? The attribution is not clear. However, on the offensive, this type of attack could become a means of protection and give defense teams valuable time to investigate.
Solution
Faced with these figures, and the resurgence of this type of attack, it is necessary to adopt a defense in depth approach, which requires different tools.
The mission of TEHTRIS is to help to face this type of attacks.
A DDoS attack can also be a diversion to keep cyber defense teams busy. This gives the cybercriminals more time to launch a more complex, in-depth attack on the system, while defenders are busy restoring the impacted service. This is where TEHTRIS tools will show their full potential. Our solutions will neutralize the threat automatically and immediately without the need for human action. The unified XDR console provides a single view of everything that is happening on the IT asset. A post-mortem forensic analysis will also ensure that nothing abnormal happened on the IT estate during the period of the distributed denial of service attack.
- DDoS on the application layer vs. EDR/EPP
Since these attacks target vulnerabilities present on the victim infrastructure, the EDR tool’s Audit module will verify that there are no vulnerable versions of software installed. In the same way, the EPP with its Anti-exploit module will prevent any exploitation of vulnerabilities on the machines protected by TEHTRIS.
[1] DNS server that explores the alternate servers of the primary server when the latter is unreachable.
[2]Kasperky
[3] Spamhaus-2022
[4] Cloudflare DDoS Threat Report 2022 Q3
[5] Cloudflare DDoS Threat Report 2022 Q3
[6] https://journalducoin.com/solana/le-reseau-solana-sol-neutralise-quelques-heures-soupcon-dattaque-ddos/

