When it comes to innovation, cybercriminal gangs are known to be particularly gifted. Some are even close to “genius” as their tools are so elaborate, innovative and ingenious.
But these gangs also know how to evolve their tactics, and recently, their organizational structures.
Some behave like true multinational companies and, as in all such organizations, there is no company today that envisions its business without relying on alliances.
For the past few months, we have been witnessing some very interesting strategic movements within certain groups and we have seen the birth of some real little revolutions in terms of cyber organization.
We knew the “RaaS” model, for “Ransomware As A Service“, we are now discovering the “cartel” and “rsubcontracting network” models.
Cartels in cyber crime.
If we stick to one of the Larousse definitions, a cartel is a “Agreement carried out between professional, union, political, etc., groupings for the purpose of joint action.“
Nothing could be more accurate in defining and describing what we are witnessing today in terms of cybercrime.
Indeed, it was recently discovered that several large groups had decided to pool a number of their assets (intelligence, tactics, offensive tools, extortion platform…) in order to obtain quickly, and in a systematic way, a significant financial benefit.
This association is particularly thought out and elaborate: it is for them to ensure the success of their actions by collaborating intelligently and efficiently. Using the technical capabilities and know-how of each to save time, and guarantee the success of operations.
But this evolution in organization does not stop there.
Some groups have even set up recruitment channels, purchasing centers, etc., reproducing organizations worthy of large companies. So we discover that some have
- an HR department, with recruitment capabilities in the Darkweb
- a finance department that implements operating funds, as well as solidarity funds in case of arrests, seizure of infrastructure, etc.
- a commercial department, which manages the purchase of vulnerabilities or exploits, and sales of rights to use ransomware or tools such as webshell.
The diagram above presents in a simplified way what CTI is, through its three pillars that are tactical, operational and strategic intelligence that allow decision makers to react quickly and well. The strategic part offers a vision of the risk and supports decision making to mitigate it. For each, we link to the output data and the target audience.
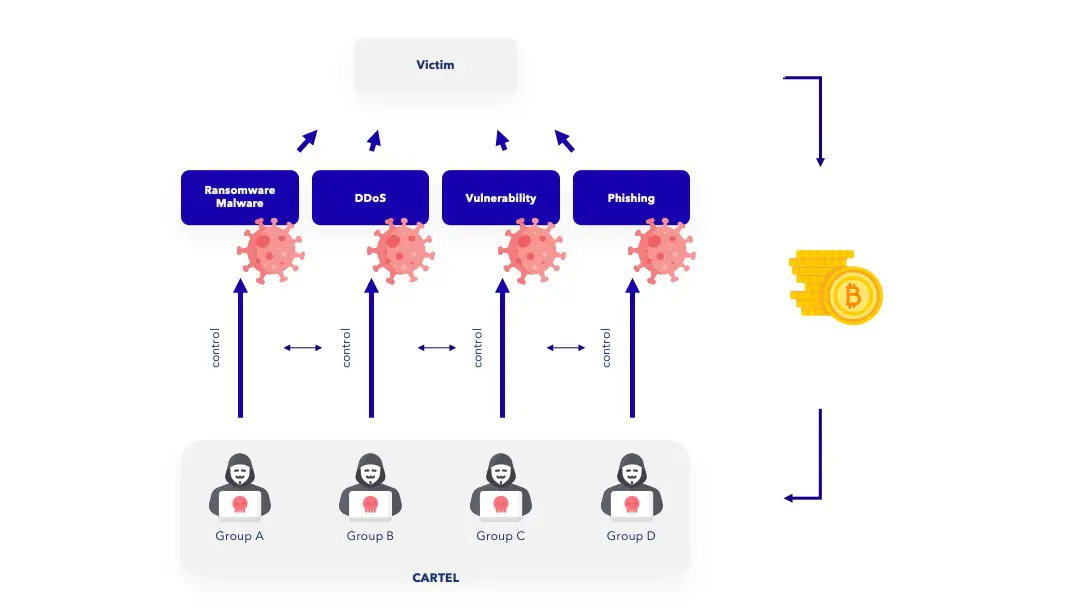
The cartel association of Wizard Spider, Twisted Spider, Viking Spider and LockBit is probably the best known because it is one of the most formidable.
This cartel is perfectly organized and makes every possible profit from this association: Vicking Spider and LockBit use the data stolen by Twisted Spider to perform attacks using very specific and targeted vulnerabilities and exploits. Lockbit and Wizard Spider simultaneously deploy ransomware on victims’ systems to ensure a quick financial return. The Gang of 4 will then pressure each victim, using coercion through triple or quadruple extortion methods.
But we have other examples of cartels, such as the combination of the REvil, Maze and Egregor gangs (the latter two having recently suspended operations), or the trio consisting of Wizard Spider, Ryuk and Conti.
One of the most notorious successful cartel attacks was undoubtedly the one on Solarwinds, which was revealed in late 2020. The SilverFish group, obviously very close to the FSB and SVR (Russian intelligence services), is suspected to be behind this attack. But this group itself would be made up of other groups, such as the terrible Russian gang EvilCorp.
But when the “Cartel ” mode is impossible, we witness an equally effective and formidable operation, that of outsourcing.
Subcontracting programs
It’s all about cybercriminal groups finding the most efficient way to achieve their goal: to succeed in their attack, whether it’s motivated by money or the data they covet.
The watchword is and remains efficiency.
This means moving fast, and raising the bar for success.
Not all groups may have all the skills required to carry out a sophisticated attack, so some groups choose to use the skills of other cybercriminals to achieve their goals.
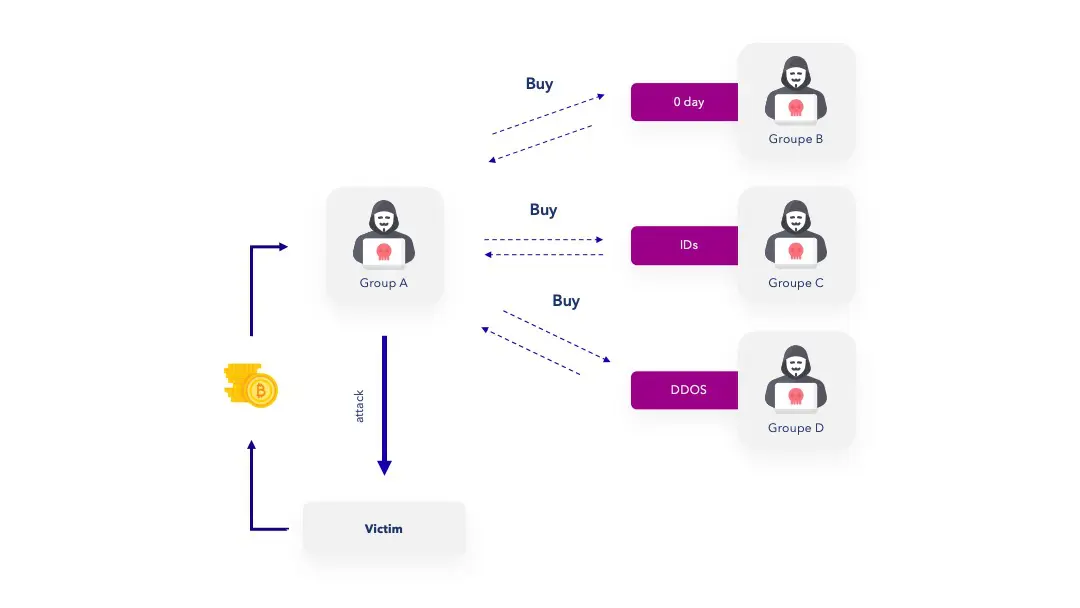
For example, it is known that discovering an entry point into an information system is a complex and time-consuming task. It takes work to discover vulnerabilities, and the ability to exploit them.
A gang will therefore buy the services of other groups or individuals, and exploit the purchased discoveries for its own purposes. Its purchases will soon have paid for themselves. But it will also be able to resell the purchased exploits to other groups in order to make a little more money.
A recent and quite prominent example is that of a known actor in the cybercriminal world, named “Integra“, who deposited nearly 27 Bitcoins (more than $1 million) on a Darkweb forum in order to buy 0-day exploits: RCE (remote code execution)-LPE( local private escalation) from other forum members.
This kind of offers on underground forums are starting to multiply, which is not really a good omen since it means that attacks will now be more and more lightning fast.
The long reconnaissance phases, which could be detected by the intelligence capabilities of cyber defense teams, are no longer systematically a sign of an upcoming attack.
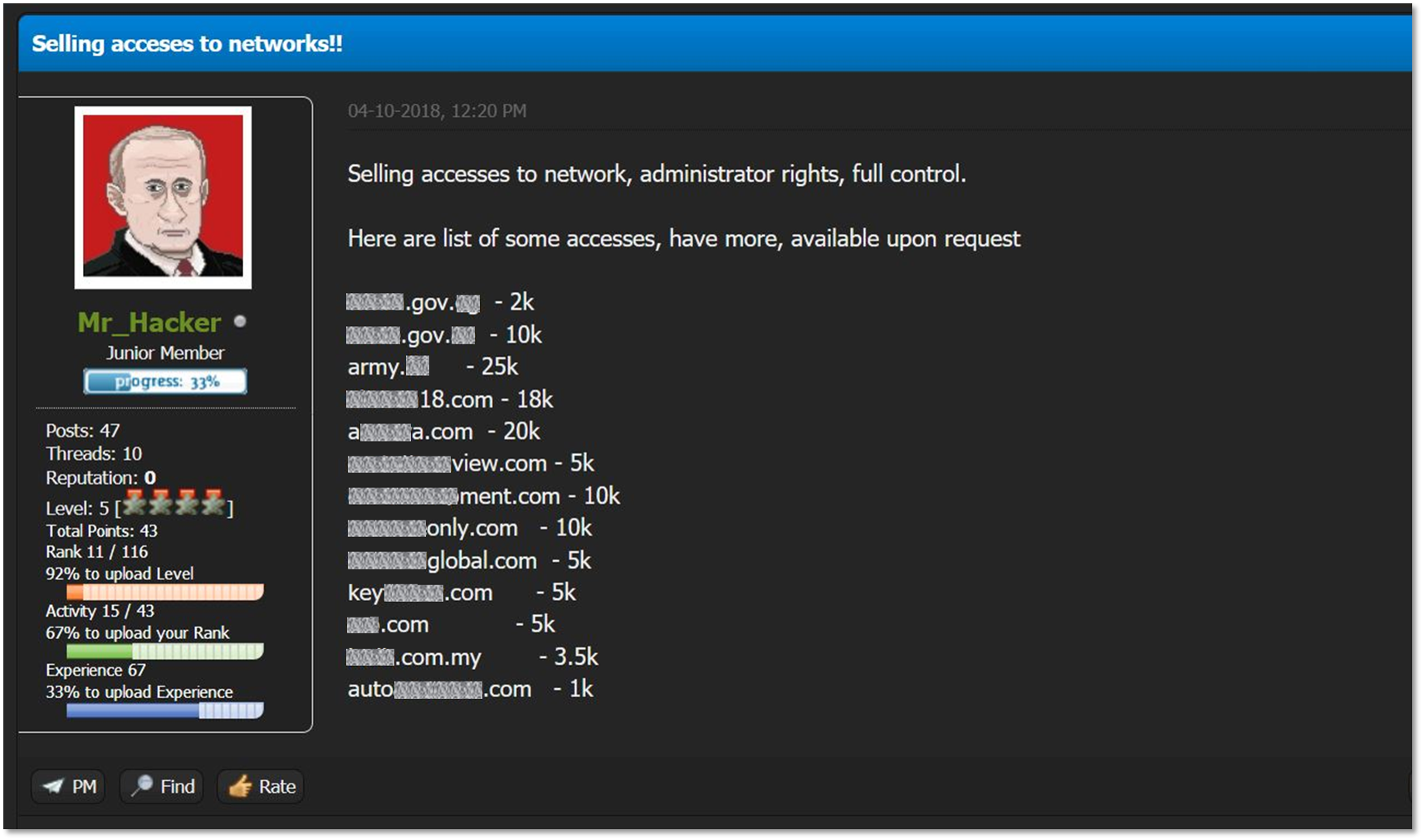
Here’s an example of a gang selling:
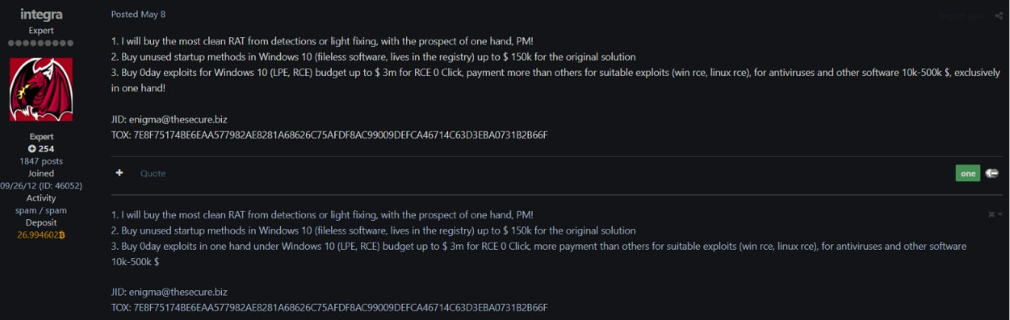
And one that buys:
Conclusion
As we can see with these 2 models, cyber gangs are becoming more and more structured, and these strategic organizational developments allow them to be more and more aggressive and virulent.
We have gone from double extortion, to triple and even quadruple extortion in some cases.
The first extortion involves encrypting all of the victims’ data in order to force them to pay for it.
The second involves stealing the data, and threatening to publish it on the darkweb if a ransom is not paid.
The third is the threat to destabilize the victim’s entire infrastructure using denial-of-service attacks.
And recently, a new threat has been flourishing harassment and blackmail, whereby gangs threaten to publicly communicate that a company has been looted.
The cybercriminal gangs are brilliantly applying the basic principles of what is called “collective intelligence.” More than the addition of intelligences put end to end, collective intelligence allows solutions to emerge, when different individuals each possess specific skills.
It is easy to understand that these organizational evolutions are strategic for both attackers, who find ways to increase their efficiency, and for defenders, who must find new ways to understand and detect the threat.

