Cyberattacks affect all endpoints, even mobile ones. They can take different forms and have sometimes disastrous consequences for organizations. In this context, knowing the risks linked to the use of a smartphone, applying good practices, and adopting appropriate security solutions allows to protect oneself efficiently against what is often called “mobile threats” (cyber threats).

What are the risks related to mobile security?
The dangers to which one is exposed via cell phone are numerous and each user must be made aware of them. Here are the main risks:
Theft of personal data
This risk is still underestimated, but the figures speak for themselves. According to Gemalto’s Breach level index, 65 data thefts took place every second in 2020. This is the case for T-Mobile, for example, which was the victim of an attack that affected more than 100 million of its customers in 2021. The information recovered was contact information, social security numbers, driver’s licenses, and electronic device identification numbers (IMEI).
With stolen data, the attacker can easily obtain money, either directly or indirectly. He can use personal data to take out a loan or obtain a credit card in the victim’s name. With a card number, he can make online transactions. He can also sell this information to companies that will use it for advertising purposes or offer it to the highest bidder on the Dark Web.
Data theft can thus have a major impact on the individual, but also on the organization. The latter can see its productivity and its positioning strongly degraded.
Damage to reputation
An attack, whatever it is, can strongly damage the company’s image. Indeed, customers who see their data sold or exposed on commercial sites necessarily lose confidence.
Many structures are affected. In May 2019, a sophisticated cyber attack exploited the messaging system of the WhatsApp video calling application. This attack sent malware to users’ mobile devices. Although WhatsApp reacted quickly, the damage was done and trust in the app dropped.
Blackmail or “breachstortion”
The public image of an organization is also at stake in the case of blackmail. After stealing confidential data, cybercriminals apply pressure by threatening to expose it if a ransom is not paid. They do not necessarily provide proof because they rely on fear. The message they send is usually short and urgent.
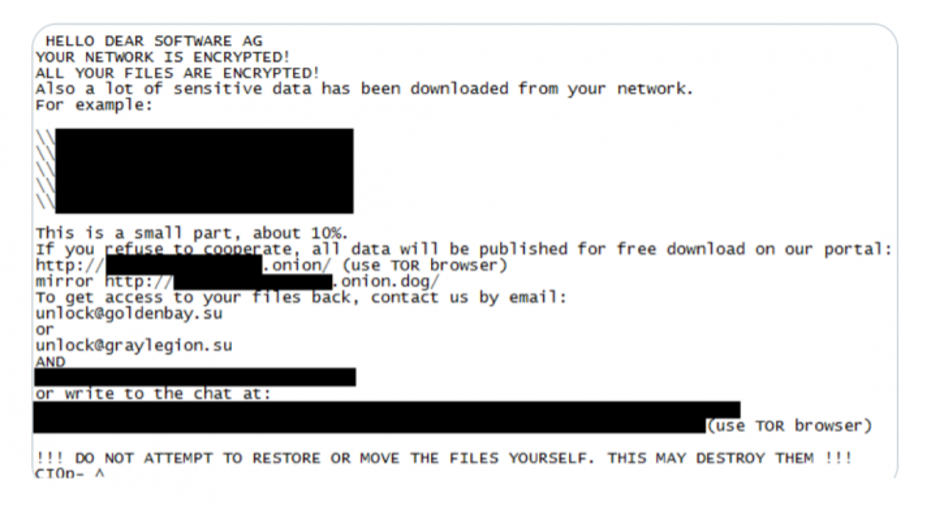
Cyber espionage
Direct financial gain is not the only purpose of cybercriminals. Espionage is another. Both private companies and public administrations can be affected. The primary objective is to obtain highly sensitive information, or information classified as “secret defense”, in complete invisibility, to reuse it. In the industrial sector, for example, a company’s know-how can be disclosed to the competition.
The Pegasus attack, which was widely reported in the media, allowed 50,000 telephone numbers and 17 media outlets to be spied on. This type of cyberthreat is even more dangerous because it is difficult to detect using traditional tools.
The risks linked to attacks on cell phones should therefore be taken as seriously as those encountered on computers. To minimize them and protect yourself from the danger, several solutions exist.
Good security practices to apply on cell phones
Strong security requires a combination of several measures. The following best practices can easily be used as a first barrier of protection:
- Implement end-to-end data encryption to protect all communications
- Adopt multi factor authentication
- Keep the phone’s operating system up to date to avoid vulnerabilities and loopholes
- Be vigilant when downloading an application and make sure it is reliable (some applications are attractive because they are free, but they may contain malicious code)
- Avoid public networks, even if they are convenient, because they are not very secure or not at all
These few measures are within everyone’s reach and contribute to the security of mobile devices. However, they must be completed by the implementation of a security solution dedicated to this type of terminal.
TEHTRIS MTD, the security solution against “mobile threats”
Among the existing cyber security solutions, we find antivirus software. They detect known virus signatures and block them. However, in a context where cyber threats are multiplying, they are not enough. A 360° approach, including behavioral analysis to detect unknown threats as well, will be truly effective. TEHTRIS MTD (Mobile Threat Defense) technology fits perfectly into this approach.
TEHTRIS MTD is managed from a centralized cloud-based console, which provides a global view of the mobile fleet to the security team. The solution provides quick access to key elements, such as alerts raised by the application and their criticality level, the IP address of the device concerned, the number of malware applications present on the devices or the latest security patch for each device. The agent deployed in the mobile devices can discover vulnerabilities at the local configuration level and even anticipate the threat.
This technology enabled early detection of the Pegasus software that made the news.
In the case of Pegasus, hackers used multiple domain names to mask their attacks and place malicious operations. Every time a corporate phone protected by TEHTRIS MTD, looks for a domain, every time a program is installed, the action is traced. When a program is installed that is not authorized by Apple, for example, a security alert is raised. The console screen of the TEHTRIS XDR Platform can then be used to find all the phones that have been compromised. In some cases, when the domains are unknown or suspicious or malicious, we can even have DNS protection, which will cut off the request, protecting the phone upstream.
When a threat is detected, the security teams are immediately informed, thanks to the notifications in the MTD application:
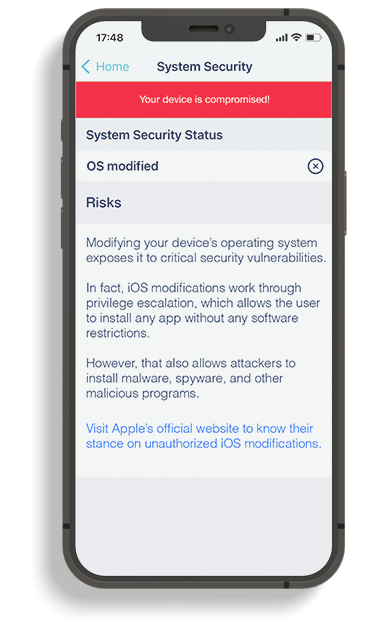
In addition, TEHTRIS MTD monitors for things that other EMM/MDM solutions typically miss by being able to identify weak signals.
As illustrated, effectively protecting mobile devices (smartphones, tablets) involves implementing preventive measures on two fronts: the device itself and the technology that manages that same device.
With constant vigilance, risk mitigation and effective tools, organizations will be able to effectively combat the traps set by hackers on smartphones.

