Although not very vocal until the latest attacks, LAPSUS$ has known victims from all over the world.
The group appears to have emerged in 2020, uses the Portuguese language in its communications and is believed to originate from the South American continent. Until now, members have mainly attacked smaller targets.

The particularity of the LAPSUS$ group
The peculiarity of this group, which has been making the headlines in the international press in recent weeks, lies in the fact that it does not seem to be interested in developing ransomware but rather in direct data theft.
The LAPSUS$ group likes to distinguish itself by its originality and does not use the classic communication channel via Dark Web sites, preferring two Telegram channels where it accumulates a total of 33,000 subscribers.
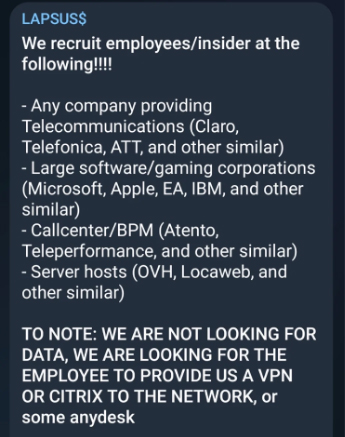
The members of the group do not hesitate to communicate about their recruitment, and have openly announced that they are looking for moles in a series of companies, especially in the field of telecoms or software publishers such as Microsoft, Apple, EA, AT&T… This kind of communication is not very surprising, as the group is suspected of using internal employees to perfect their attacks.
Main attack campaigns
Although the LAPSUS$ group has remained very quiet until now, no one in the cyber world can ignore them.
Their list of victims is starting to grow dangerously long, and they include:
- The Impresa media: LAPSUS$ published a message directly on their website demanding a ransom.
- Brazil’s Ministry of Health, a victim of the group last December had its servers brought to a halt.
- Vodafone
- MercadoLibre, whose 300,000 user data were stolen.
- LG: the group threatens to reveal employee passwords.
- Ubisoft…
Let’s take a closer look at the last 4 attacks.
NVIDIA
NVIDIA is an American company, designer of the GPU (Graphics Processing Unit). These are computer chips located on the graphics card, which aim to optimize the 2D and 3D display.
The American company suffered an attack on February 23, 2022. The group suspected behind this attack is none other than Lapsus$. The latter would have in their possession 1TB of data concerning the projects of the company or its customers, including certificates allowing NVIDIA to sign their binaries. These certificates could also have been used by attackers to sign their malware and appear as legitimate NVIDIA binaries.
Their attack technique seems to be different from the majority of groups as they would rely on internal moles to carry out their misdeeds. In this case, they would have been able to access information systems for over a week via an employee’s VPN.
MICROSOFT
On March 22, 2022, Microsoft confirmed that one of its employees had been compromised by the Lapsus$ group hacking group.
Amount of loot: 37 GB of source code stolen from Microsoft’s Azure DevOps server.
The group has also confirmed the theft via the publication of screenshots shared on Telegram. Among the data, we see a file about Cortana (the group claims to hold 45% of the data), projects related to the search engine Bing (the group claims to hold 90% of the source code)…
Microsoft link: https://www.microsoft.com/security/blog/2022/03/22/dev-0537-criminal-actor-targeting-organizations-for-data-exfiltration-and-destruction/
SAMSUNG
On Monday, March 7, 2022, it was Samsung’s turn to declare that it had suffered a data leak. A part of the source code of the Galaxy devices has been disclosed. The origin of the attack would be due to a flaw found in these same source codes.
Lapsus$ goes further and claims to have 190 GB of confidential data of the electronic giant that currently represents 19% of the volume of smartphones sold in the world.
The impact is colossal since hundreds of millions of users can potentially be affected. Samsung reassures that no personal information of its customers has been compromised.
OKTA
Okta is the specialist in access management and authentication in service mode.
They have 15,000 customers worldwide including Zoom, AWS, Confluence, Splunk, Salesforce and Jira.
The attack on OKTA was announced on March 22, 2022 by Lapsus$ (the attack having been detected in January) which continues to expand its roster. The group reportedly had access to the laptop of an engineer working for a third-party provider for five days (source Mag IT)[1].
For all that, the access management specialist confirms that there was no compromise. Once again Lapsus$ confirmed this attack via a screenshot. From these attacks we can deduce that the LAPSUS$ hacker group is growing in activity and is likely to cause scares in the coming days. These attacks could serve as a springboard for other threats, including supply chain attacks.
Finally, protection measures must be more than ever active and planned in each company, including digital hygiene, usage behaviors and internal business intelligence.
The threat can come from within. The concept of zero trust has never been more aptly named.
Protection solutions
Protection solutions must be activated more than ever in the face of such a formidable enemy.
We can only advise once again to adopt the right attitude in terms of security.
This goes through the famous 5 pillars, which are :
- The implementation of multi-factor authentication
- Securing VPNs
- The securing of the cloud
- Segmenting its assets
- Having healthy, reliable endpoints that are well protected. That’s what TEHTRIS offers with its XDR technology
And finally, to improve awareness of internal attacks, as the threat comes from everywhere. Lapsus$ has chosen the internal route and we have to admit that it works.
Contact us
[1] Valery Marchive. Lapsus$: Okta evokes a “failed attempt” of compromise.2022 & Lapsus$: Okta evokes a “failed attempt” of compromise

