DNS hijacking is the practice of subverting the resolution of Domain Name System requests. The queries are manipulated to redirect users to malicious sites. Since each organization has its own website, and since every employee of an organization is using Internet, DNS hijacking is a significant threat you have to take into consideration when ensuring cybersecurity. TEHTRIS XDR Platform helps you prevent, detect, and remediate these types of attacks.
DNS Hijacking: what is this threat?
How does it work?
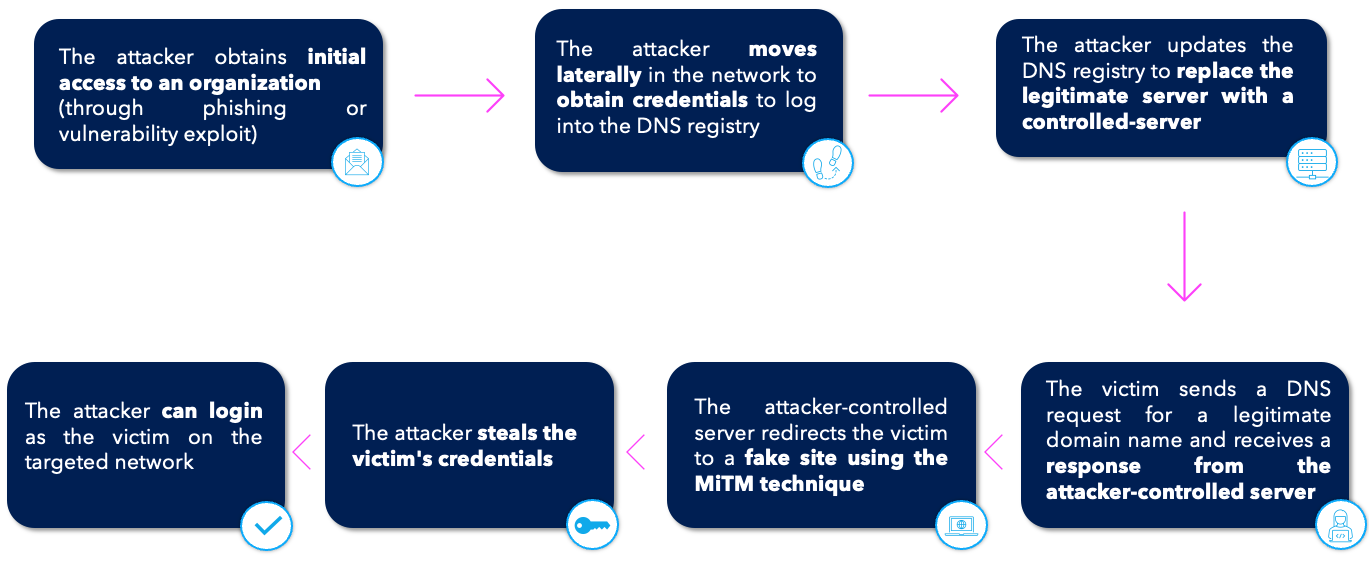
The attacker gains access to the server that controls the organization’s DNS through various means (such as vulnerability exploits or phishing). Then, they modify or falsify the DNS for a certain period of time (usually quite short), which will alter the data the victims will receive from the Internet as well as the DNS name records in order to redirect the victims to servers controlled by the attacker. All this is transparent to the victim who visits the site. The attacker seeks to obtain credentials or exploitable information using the AiTM technique for Adversary-in-The-Middle (T1557 of the MITRE ATT&CK matrix) also known as MiTM (Man-in-The-Middle).
Cyber criminals’ ultimate goal when they target organizations’ DNS is to recover credentials (login/password) without the victims’ knowledge, in order to use them to access sensitive networks and systems.
Example: Sea Turtle
In 2019, the Sea Turtle threat, considered “DNSpionage,” made the news. While the Sea Turtle campaign, terribly effective because it was state-sponsored according to Cisco, was limited to targeting organizations involved in the national security of countries in the Middle East and North Africa, the success of this operation and the risk of other malicious cyber actors replicating this pattern of attacking the DNS system should be of concern.
How to protect your infrastructure from this threat?
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) was already warning of the threat in January 2019, giving mitigation steps to limit the damage:
- Checking the DNS history
- Changing passwords for DNS accounts
- Adding Multi-Factor authentication to DNS accounts
- Monitoring the Certificate Transparency initiative logs
TEHTRIS XDR Platform: protect your organization from DNS hijacking attacks
TEHTRIS EDR/EPP & TEHTRIS DNS Firewall
TEHTRIS XDR platform will detect and automatically remediate a threat like Sea Turtle through its integrated modules. As mentioned above, a DNS Hijacking attack can start in two ways:
- By one or several compromises of workstations via the exploitation of known vulnerabilities:
TEHTRIS EDR will detect the post-exploitation stage, i.e. when the attacker performs actions such as Lateral Movement (TA0008 of the MITRE ATT&CK matrix) or Credential Dumping (T1003 of the MITRE ATT&CK matrix). In addition, the TEHTRIS EDR has an Audit module, which allows to list all the vulnerabilities on the workstations/servers of the computer park so that the CISO can take appropriate measures to not leave any door open to attackers.
- Via phishing (or even spearphishing)
This will be detected by the EDR if the threat comes from an attachment file. If the victim clicks on a link (to download a payload or a fake authentication page), it is the TEHTRIS DNS Firewall solution that will be able to detect and block the threat by comparing the URL with its database of malicious domains as well as studying it with artificial intelligence to identify domains generated automatically by Domain Generation Algorithm (DGA)[1].
In addition to being able to prevent compromission, if necessary, the “Raw Data” feature of TEHTRIS DNS Firewall is a forensic tool and allows to have a history of the replacement in the client’s DNS responses a posteriori.
TEHTRIS SIEM
TEHTRIS SIEM allows the monitoring of accounts that can modify the company’s DNS. If logs from the CISCO router or DNS server where the DNS is managed are sent to the SIEM, alerts can be triggered if accounts associated with malicious IP addresses (such as Tor nodes) manipulates the DNS.
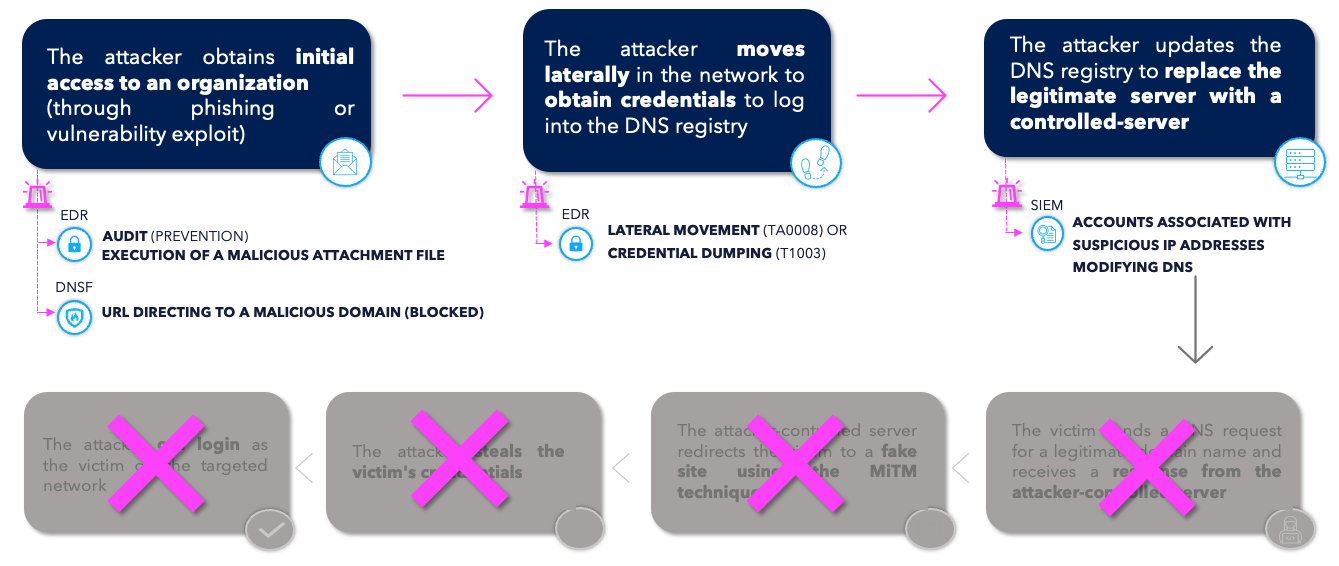
Each step of the attack will be detected by the XDR Platform and will stop it during the early stages.
Conclusion
TEHTRIS tools, unified in the XDR Platform, offer effective ways to better protect organizations by tracking the smallest clues related to this growing threat. The solutions put end-to-end ensure the safety of your IT users by gaining time and efficiency.
TEHTRIS XDR Platform, through its integrated technology, will allow the analyst to have a broad vision on what is happening on its infrastructure in real time, and can also be used as a decisive forensic tool.
[1] Malware uses requests to automatically generated domain names in order to contact their control (C2) servers. They have different characteristics than legitimate domain names.

