Unreleased RaaS analysis- CashRansomware
Introduction Our experts managed to intercept a pre‑release sample of a new Ransomware‑as‑a‑Service (RaaS) variant called... Read more
- Updated on

Introduction Our experts managed to intercept a pre‑release sample of a new Ransomware‑as‑a‑Service (RaaS) variant called... Read more
- Updated on

RustyStealerDropper Use case A reminder: what are malware droppers?How do they stay in your systems?Deobfuscating a... Read more

MedusaLocker is extremely active malware at the time of writing, including in France. It first appeared... Read more

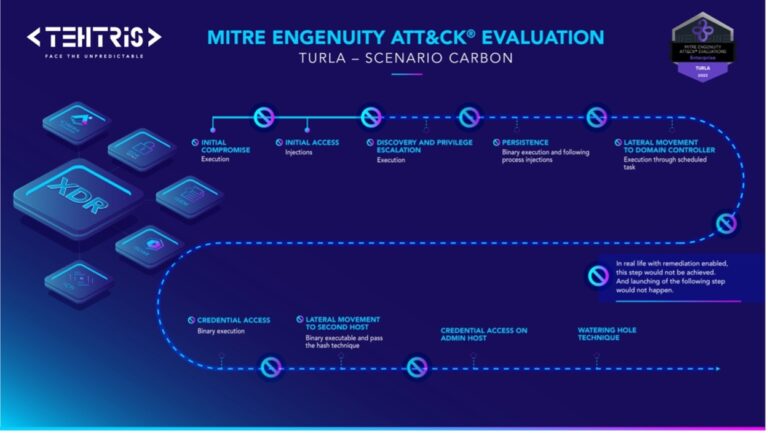
For the first time, TEHTRIS participated in the 2023 MITRE Engenuity ATT&CK® Evaluations: Enterprise. Using TEHTRIS... Read more
"30% of CISOs of CAC 40 companies are already convinced of the risks posed by foreign... Read more

One of the main concerns for 2023 is the risk of data leaks from civilian devices... Read more

"Collective attacks by saturation of service" is now the French expression to talk about DDoS attacks... Read more

The geopolitical news and the Russian-Ukrainian conflict have highlighted the threat and impact of disinformation. Of... Read more

After Black Friday, Cyber Monday, Christmas shopping is just around the corner, so here's a little... Read more
