In October 2022, a TEHTRIS customer was protected from the threat known as Purple Fox thanks to the TEHTRIS XDR Platform and its TEHTRIS EDR and EPP modules. Let’s have a look at the ever-evolving exploit kit since its discovery four years ago and how TEHTRIS’ tools work against the threat.
Get to know the threat: Purple Fox
An old threat still relevant
The Purple Fox threat was discovered in 2018, and this recent attack highlights the importance for CISOs to consider older threats that are still very much relevant. Indeed, since 2018, Purple Fox has continually reinvented itself to increase its capabilities and renew the vulnerabilities it exploits. In March 2022, TrendMicro published an analysis of Purple Fox’s new capabilities. It was then observed in the summer of 2022, in particular by Japanese analysts.
Purple Fox is an exploit kit that exploits, among other things, a known Internet Explorer vulnerability (CVE-2021-26411 – CVSS3:7,5) to distribute other malware on the systems it infects via PowerShell execution. Since 2021, it has primarily delivered the DirtyMoe malware, a computer worm with cryptocurrency mining capabilities. The Internet Explorer vulnerability exploited by Purple Fox has since been patched. Therefore, updated versions are not at risk.
Attack scheme
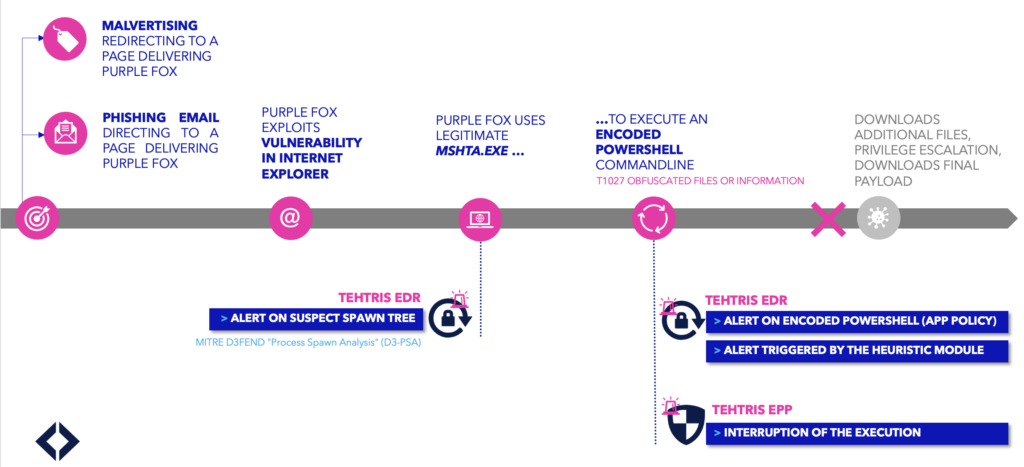
By clicking on a malicious URL contained in a phishing email, or by a redirection via a fraudulent advertisement (malvertising), the victim will go to a page containing Purple Fox, which will exploit the Internet Explorer vulnerability to download itself on the victim’s device.
Once on the machine, an encoded Powershell.exe is executed by mshta.exe (a legitimate Windows component). Encoding the PowerShell is an obfuscation technique to avoid detection.
Purple Fox checks the permissions granted on the machine and downloads additional files, including a MSI installation package (Microsoft System Installer), and seeks escalation of privilege. The payload (e.g. DirtyMoe) is then installed via the MSI installation package.
Protect your IT system thanks to the TEHTRIS XDR Platform: detection & remediation by TEHTRIS EDR and EPP
TEHTRIS’ customer was automatically protected from this threat through the detection and remediation capabilities of EDR and EPP, which are integrated and interact inside the TEHTRIS XDR Platform.
Thus, the analyst was alerted by the EDR based on 3 criteria:
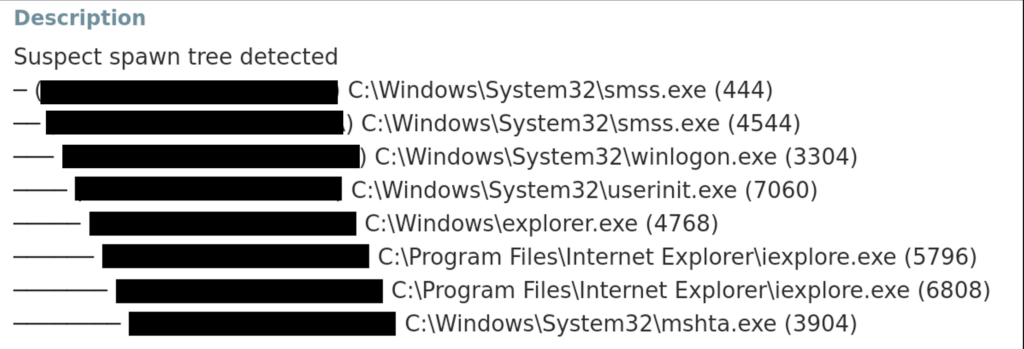
The EDR raised an alert on the spawn tree:
The child processes of programs such as web browsers (in our case, Internet Explorer) or Microsoft Office are monitored for suspicious activities that attackers might use.
This detection corresponds to the MITRE D3FEND “Process Spawn Analysis” (D3-PSA) which consists in “analyzing spawn arguments or attributes of a process to detect processes that are unauthorized”.
The EDR raises an alert and, depending on the remediation setting, may stop the process from running.

The EDR’s heuristics module also raises an alert about the suspicious characteristics of this execution.

Among the suspicious features are PowerShell arguments, corresponding to the MITRE T1059.001 “Command and Scripting Interpreter: Powershell” attack sub-technique, whereby attackers can abuse PowerShell commands for execution. PowerShell is a powerful command line interface included in Windows. Using PowerShell can enable many actions, such as environment discovery on the machine and code execution.
Alert from an Application Policy configured to report encoded PowerShells
The executed binary is mshta.exe, a legitimate Windows component. However, the fact that it contains an encoded PowerShell is a suspicious feature. Indeed, encoding the PowerShell is an obfuscation technique to avoid detection (tactic T1027 Obfuscated files or information of tactic TA0005 Defense Evasion of the MITRE ATT&CK matrix). An Application Policy had been configured beforehand by the analyst to monitor and alert on this kind of event.

In Purple Fox, mshta.exe is used to execute PowerShell commands that aim at obtaining an privilege escalation (TA0004 Privilege Escalation technique from the MITRE ATT&CK matrix), download additional files and deliver the final payload. In this case, the final payload is unknown since the attack was not successful because the process was killed by the EPP before the execution of Purple Fox.
Kill the threat with EPP

EPP allows for a signature-based program kill. Advanced features complement the local antivirus protection by fighting vulnerability exploits of intrusion vectors (such as web browser vulnerabilities).
Here, it is the Behavioral Application module that detected the Purple Fox threat and raised an alert on the console. This alert, associated with a severe criticality threshold, triggered an automatic remediation action by the EPP which interrupted the execution of the binary.
All the module alerts are visible from the Alerts & Events tab of the XDR or specifically from the tab of each dedicated module. It is also possible to predefine a SOAR playbook to send alerts to specific email addresses, by phone or via the MTD application installed on the company’s mobile devices to be informed in real time wherever you are.
Synergy of modules inside the TEHTRIS XDR Platform
Conclusion
As part of the TEHTRIS XDR Platform, the EPP and EDR modules are complementary to ensure the security of the organization’s workstations and servers and protect the information system from known and unknown threats. The unified XDR console allows to manage the alerts raised by these two solutions to gain time and efficiency: leverage technology to decrease Mean-Time-To-Detect and Mean-Time-To-Respond!

