With the explosion of increasingly fast and complex attacks, defenders must be more resourceful in implementing the countermeasures necessary to fight back, but which ones? One possible answer lies in user behavioral analysis tools.
Endpoint Detection & Response (EDR) and XDR are tools based on artificial intelligence and behavioral analysis.
UBA for “User Behavior Analytics“, which has been around for a few years, should be part of the detection arsenal of cybersecurity teams.
But what is its usefulness? its necessity? and how does it work?
These are the questions we are asking ourselves today and to which we will try to provide answers. We will also see how behavioral analysis can interface effectively with existing tools such as SIEM or XDR technology, and we will give some advice for a better use of this type of tool.

How can UEBA detect security incidents that traditional tools do not see?
Behavioral analysis is not a new technique, especially in cybersecurity. In recent years, it has become clear that the information system is in constant motion, and that users will become one of the most complex “objects” to monitor.
Simply put, behavioral analysis will implement a number of more or less elaborate mechanisms to detect activities that indicate unusual or abnormal behavior in a given environment.
By extension, User Behavior Analytics (UBA) focuses more specifically on user activity, and makes it possible to answer the questions that are most often missing in traditional detection systems: the who, when and where? But we quickly saw the limits of this analysis focused only on the user. Indeed, the contextualization necessary for any good detection in cybersecurity required that we manage to define the what? (The on what? the with what? the from what?)
The UBA was then transformed into UEBA (User and Entity Behavior Analytics), concretely defined in 2015 by Gartner[1]. UEBA focuses on user and application behavior. The latter are represented by the E, for “Entity”. The “E” therefore refers to very specific assets, such as the Cloud, the Endpoint, the network…
UEBA has the same capabilities as the UBA, but in addition to analyzing user activity, the engine analyzes the activity of these entities that can have an impact on the user’s behavior and vice versa.
To operate, UEBA is able to work on a multitude of data that can come from a multitude of sources such as SIEMs, EPP-type solutions, NTAs, system logs and, obviously, EDRs.
The power of a UEBA engine lies in learning behavioral patterns. In general, UEBA uses Machine Learning, and sometimes Deep Learning, algorithms to create a behavioral map of each monitored object and thus define a complete reference matrix in which each new entry will be evaluated against previous ones.
What are the detected behaviors?
This can include the use of unusual terminals or commands, connections at unusual times, fast typing sequences, data exfiltration attempts, access to certain system files, changes in privileges on certain user accounts, abnormal geographical connections…
Obviously, more complex scenarios can be implemented to cover more specific risks related to particular populations in the company, to specific functions, or to very critical applications.
Here is an example of a specific case of detection stage:
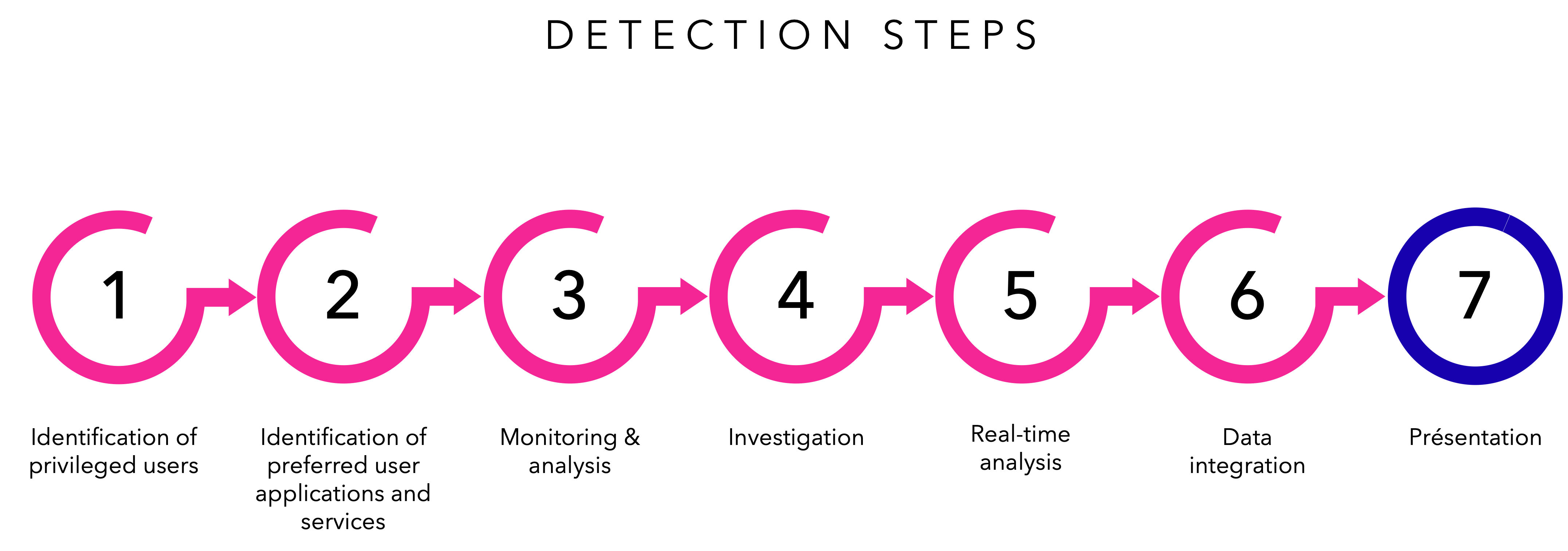
You can see below how the behavioral analysis works in a more global way:
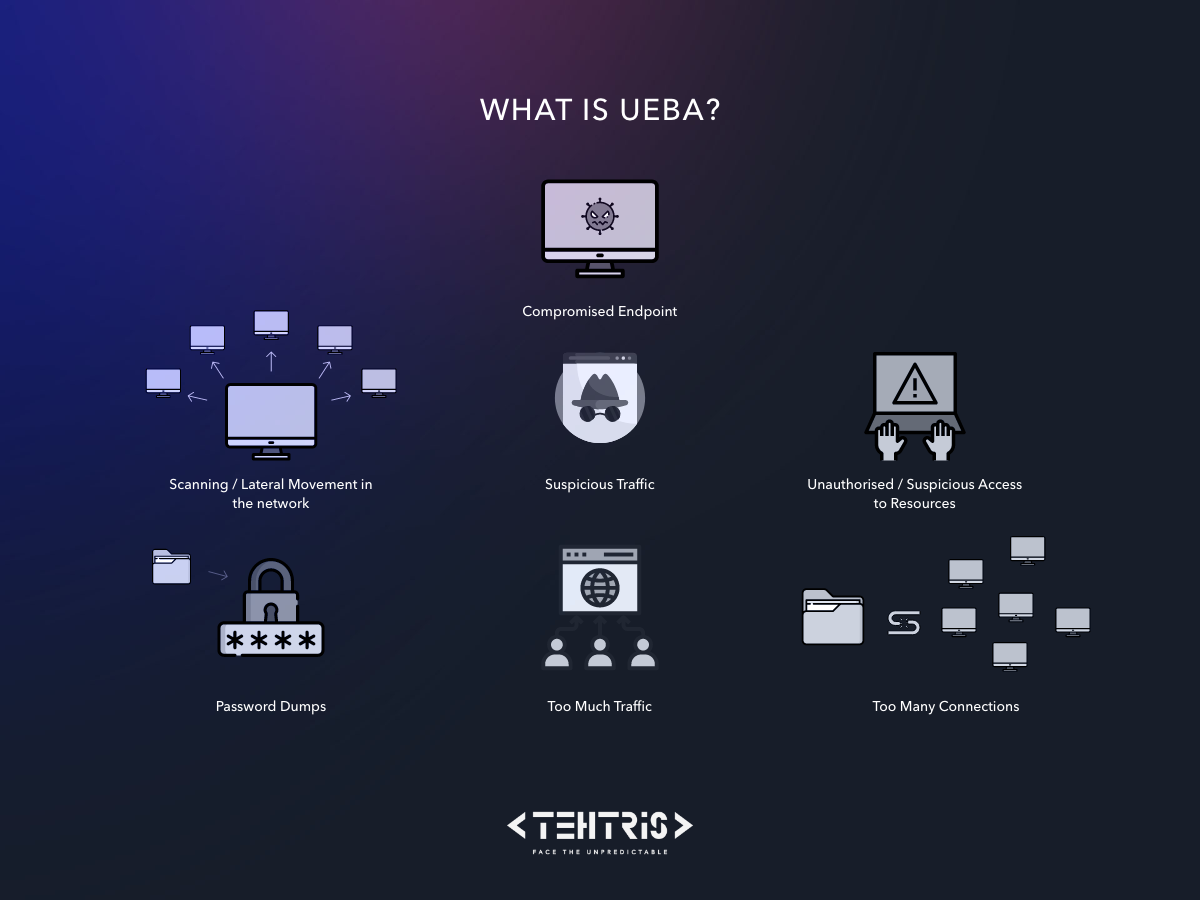
Behavioral analysis has an anticipatory action because it will allow to identify as soon as possible a possible threat. As we can see from the diagram above, it can concern a doubtful traffic, as well as too many connections, etc.
All this information will allow us to communicate additional information and thus provide a response to mitigate the risk. UEBA is not a defense mechanism, but a monitoring process.
What is the link between UEBA, SIEM or EDR?
Some EDRs do not have a contextual notion, and this limits their performance. This lack of visibility then becomes an obstacle to the automation and processing of alerts. TEHTRIS EDR includes an integrated tactical SIEM and behavioral analysis mechanisms that provide context in the detection phase. By complementing the EDR with behavioral analysis in a SIEM, the detection capabilities are multiplied.
UEBA is now integrated with XDR technologies.
As a reminder, SIEMs collect and aggregate data from security tools and IT systems, analyze them and provide real-time alerts to analysts. the behavioral analysis brick is more and more added to SIEMs. This allows for better detection, by bringing this human dimension that was previously hidden. The addition of UEBA to the SIEM allows a total vision of the use of data in a hybrid environment (at the user and device level).
UEBA is a technology opportunity that allows defenders to focus on their business. Some checks are now done in a hyper-automated way. Behavioral analysis will eliminate false positives by helping analysts determine what to look for, answering the question: what is normal and what is not? To do this, the UEBA engine will collect information about the expected behavior of both users and machines and create repositories via the SIEM that will then determine whether or not the unusual behavior constitutes a real threat. UEBA will combine machine learning and rules to create typical profiles.
UEBA is a reliable response when combined with technologies that provide context, such as EDR, NTA…Here is a diagram representing the optimal detection system:
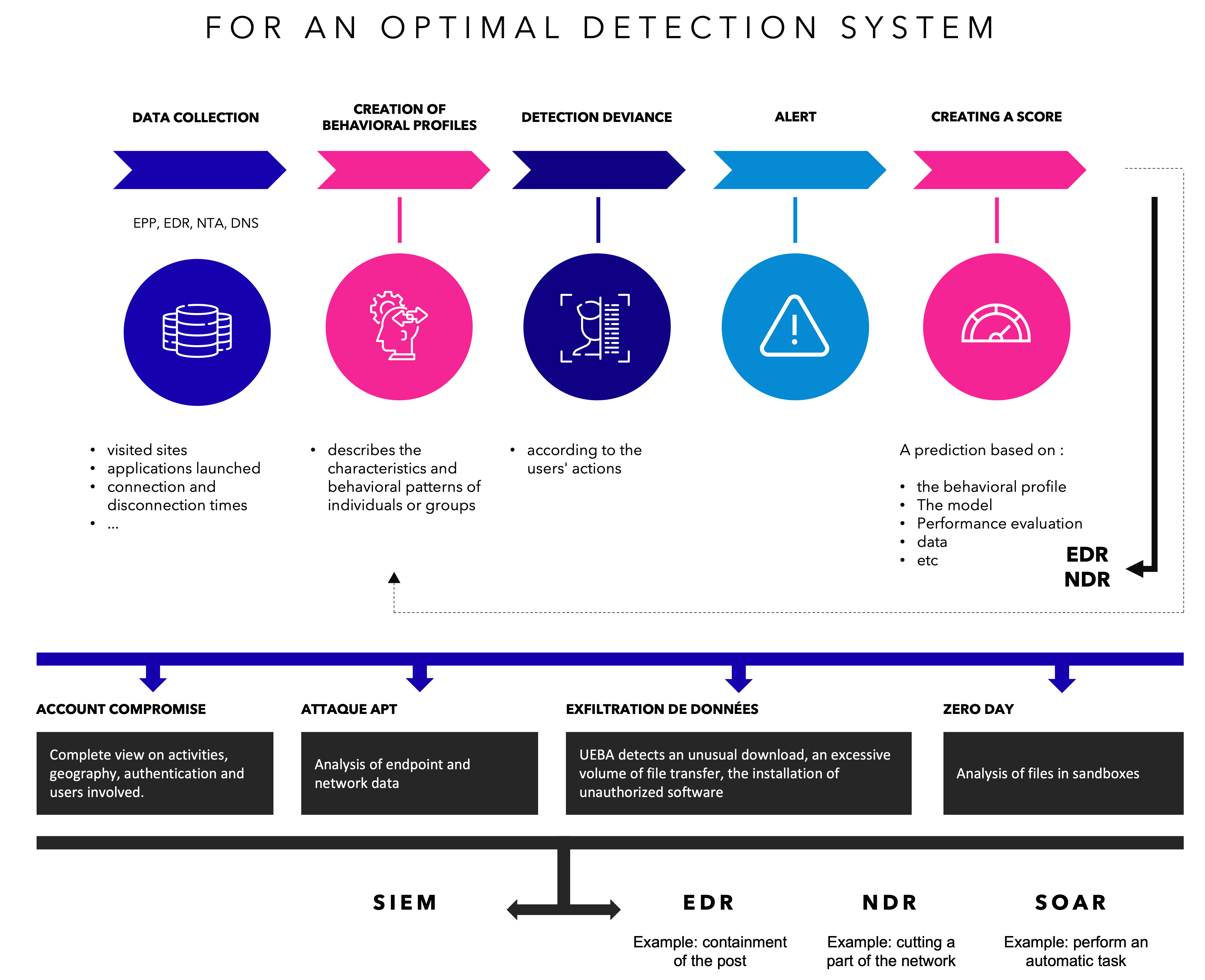
The UEBA integrated with a solution like XDR technology will add an additional layer of detection, facing internal and external threats. It brings added value in terms of protection of movements on the endpoint, on the user, on the local network traffic.
The XDR platform allows to centralize and consolidate the data collected by the different sensors and probes deployed in an information system.
According to the Verizon 2020 Data Breach Report, more than 25% of breaches took months or longer to be discovered.
It is now understood that we should no longer focus solely on monitoring the technical foundation. It is now necessary to add the monitoring of the user and his ecosystem, which can potentially be a source of threat.
Early detection, reduced response time, these are the first benefits of UEBA technology. Anticipate the threat, and thus reduce the risk.
But to be as effective as possible, UEBA algorithms must be fed with multiple, complete and, above all, reliable data. And this is where TEHTRIS brings all its value. All the components of the TEHTRIS XDR Platform come into play in the collection, but also in the processing, scoring, aggregation, etc… The behavioral analysis engine integrated into our XDR platform is therefore fed in real time with immediately exploitable data.
Equipping yourself with UEBA technology is therefore a real asset in your cyber defense arsenal, but you must keep in mind a few good practices to make it work.
Good practices for the use of UEBA
For a good UEBA optimization, it is important to be as close as possible to the endpoint and the user; this is the case of the TEHTRIS XDR Platform which, due to its technology, is the most efficient and the most advanced on the market. It can map precise behavioral profiles and adapt to each customer context.
UEBA does not replace other security systems but brings a real added value.
In order to be effective, it is necessary to
Define use cases
Depending on its detection needs and the associated risk coverage, each operational detection team will focus on the detection of privileged account abuse, compromise, identity theft or fraud. Each situation to be monitored is a specific use case, which unfolds one or more technical scenarios. This is a crucial phase in the implementation of behavioral analysis. The algorithms must “understand” where they are in order to be relevant. And these use cases must not be fixed in time, quite the contrary. They must be scalable, dynamic if necessary, and be able to take into account several organizational systems.
Multiply the types of analysis
The analysis must focus, of course, on privileged or at-risk users, but not only. As we saw earlier, depending on the risk to be covered, several scenarios can be run. And it is strongly recommended to create them all, to cross them and to correlate them.
Define the sources and behaviors on the data
The choice of data to be used is crucial. You must be able to define what you are looking for and where to look for it. For that, it will be imperative to determine the sources of the data, to evaluate the quality, the quantity, the frequency, etc… It is all this work of qualitative and quantitative audit that the TEHTRIS XDR platform does upstream and for you: each of its bricks is involved in the raising of a clean, complete, and reliable information. The UEBA only has to use it through its algorithms to cover the detection use cases. It is imperative to collect data from various data sources, the TEHTRIS XDR Platform has been deployed and can be interfaced with the security solutions of the market, which allows it to have at its disposal a vast perimeter of play, and to process large volumes of activity.
Regular updates
Machine Learning algorithms need to be regularly reviewed, adjusted, and sometimes corrected in order to best fit the data being processed, but also the constant evolution of the information system and the behavior of the company and its users. The case of the health crisis was a flagrant example: the algorithms that were not adapted to the situation no longer saw the environment in the same way and had to make detections that were not. Updating the scenarios, the data collected, and the algorithms is therefore one of the keys to success.
The hyper-automation of the TEHTRIS XDR platform has again this advantage. The relevance of its detection algorithms will enable real-time decisions.
Enrich correlation and contextualization
As we have just seen, it is important to make regular updates, because the context and the news evolve, in the same way the scoring will evolve. This scoring will have an impact on the detection of the threat. Each time there is a deviation in behavior, the system adds to the risk score of a particular user or machine. The more unusual the behavior, the higher the risk score. The aggregation is done automatically, as soon as the score reaches a certain level, the analyst is warned and can act accordingly. Data without this context is much less useful and can lead to false positives.
For more details, see our link dedicated to the TEHTRIS XDR platform: https://tehtris.com/en/products/xdr-extended-detection-response/
Have a holistic approach to cybersecurity
The holistic approach to security is once again the most appropriate. It is necessary to be able to combine behavioral analysis, aided by machine learning, on the one hand, and automation via XDR technology on the other.
An effective and reactive cybersecurity defense strategy that focuses on detecting attacks in real time is important, such an approach alone is insufficient. It is also necessary to invest in a proactive solution, to focus on how an attack may be possible and to automate the neutralization. TEHTRIS works in this direction, and continues its work of innovation, which remains its DNA.
Security is a daily challenge. It becomes imperative for companies to focus on their most important assets. To do so, they must adopt a global vision of their information systems and the related risks. This holistic approach to cybersecurity, based on risk management, requires a very clear definition of detection and anticipation strategies.
This holistic approach is essentially based on the ability to identify and classify the company’s critical data, to define the risks and therefore the scenarios to be implemented to cover them. The adoption and implementation of tools and techniques then becomes the key to a perfect cyber defense posture and this is what TEHTRIS understood perfectly several years ago: to develop a complete and reliable ecosystem capable of collecting, analyzing and correlating all available security information in order to produce contextualized and therefore immediately usable alerts. With the XDR Platform, TEHTRIS is changing the paradigm of cybersecurity, which until now has been limited to a question of infrastructure.
The TEHTRIS XDR Platform takes into account the entirety of the company’s activities, from the perimeter infrastructure of the Legacy domain to the most remote infrastructure such as the cloud and the multitude of its applications.
For more details on our offers, do not hesitate to contact us.
[1] Gartner-Avivah Litan-Market Guide for User and Entity Behavior Analytics Published 22 September 2015

