Have you ever heard of “stalkerware“?
It is the contraction of “stalker” and “software”. It is spyware that allows to spy on an individual, an entity, an organization, without his knowledge. Stalkerware is software that anyone can buy. On the market, you can find: FlexiSpy, mSpy, PhoneSpector, …
Everyone is affected, whether they are media personalities, ordinary people or organisations.
These programs are proliferating so much that it is essential to apply a few precautions to protect yourself against threats. A few rules of digital hygiene are necessary to identify and protect yourself from them.

How does it work?
Operation
Spyware can be integrated into free software. Some are remotely controllable and do not require physical access. Another feature is that these programs run in the background and are therefore difficult to detect.
The spy software requires :
- An infection mechanism, such as a virus, via phishing or even via a program that may appear legitimate.
- A collection mechanism. If the spyware is installed on a smartphone, it will retrieve passwords, photos, conversations, geographical location, calls, visited sites, downloaded files, etc.
- A transmission mechanism.
Detection
A device may be suspected of being monitored if it is found to:
- Have problem connecting to secure sites.
- Slowdown in the operation of the device.
- Suddenly turns on and off.
- Notice the emergence of new applications.
- Suffer from a resurgence of advertising.
- Notice that the battery discharges faster than usual.
In addition to these user-detectable clues, a protection tool such as TEHTRIS Mobile Threat Defense can detect the installation of a malicious application, automatically scan mobiles in the background, and verify the access granted to each application. As soon as an application is installed and updated, the TEHTRIS MTD solution analyzes it in the CTI (Cyber Threat Intelligence) database. If the applications are blacklisted in the CTI, the MTD agent will raise an alert, visible on the unified XDR platform and on the compromised mobile.
Use Case: FlexiSpy spyware installation
When FlexiSpy is installed, a digest of the application is automatically scanned in the TEHTRIS CTI, which benefits from antivirus scans containing millions of signatures (on average, 4,000 new viruses are added for mobile platforms every day).
Result of the FlexiSpy analysis in the TEHTRIS CTI:
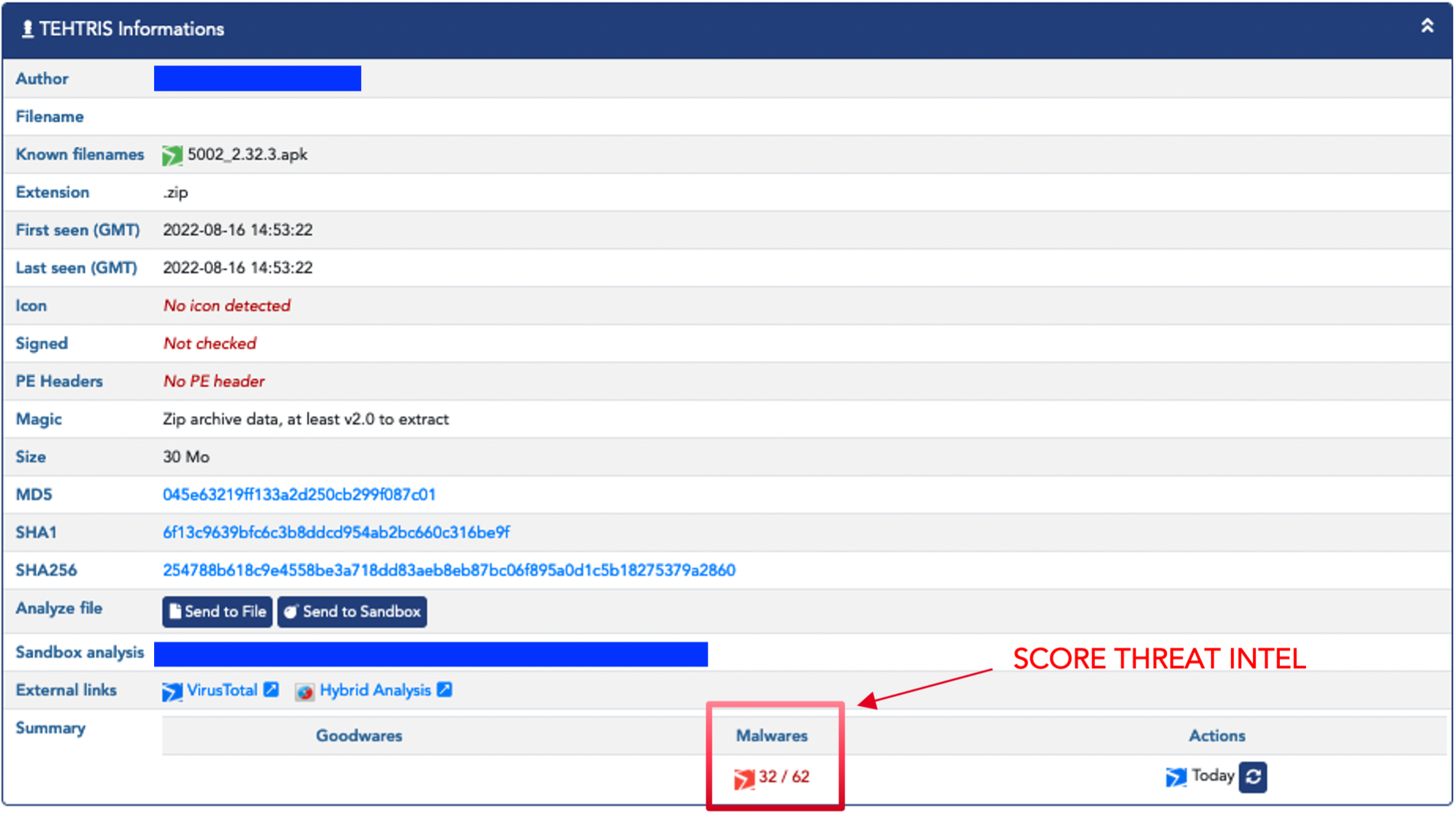
FlexiSpy receives a high virus analysis score because it is unfavorably recognized in antivirus databases, which generates an alert in the TEHTRIS XDR unified console and on the user’s mobile device.
Alert in response to a malicious APK installation in the
TEHTRIS XDR
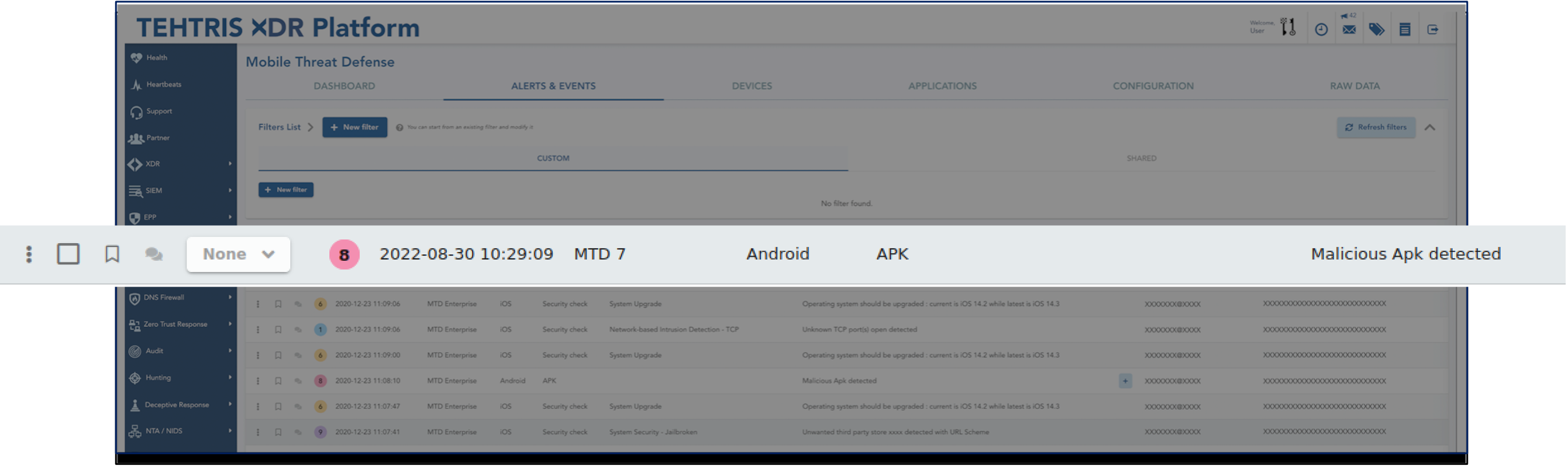
From the XDR console, FlexiSpy can be removed.
In addition, in conjunction with the DNS Firewall module, a request to a domain name blacklisted in the TEHTRIS database will be automatically blocked. Thus, if spyware is installed on a mobile phone and it tries to communicate with its C2 “Command and Control” server to exfiltrate data, the connection will be interrupted.
Good Digital Hygiene
There are several countermeasures and precautions that can be taken to reduce the threat, some of which are listed below:
- Install a minimum of applications and applications certified by trusted publishers.
- Check the access authorizations. Don’t give your password of course.
- Keep your digital tools updated. This is important to benefit from the latest optimal protection.
- Provide for automated analysis.
- Use a good protection tool. There are also tools capable of protecting against intrusions: “Mobile Threat Defense” type applications (see next section), antivirus, antimalware and firewalls.
- Restart your terminal.
- Keep physical control of your device as much as possible. Protect the camera, the microphone, disable the geolocation option…
- Turn off Bluetooth when not in use.
- Be careful with the content of messages. It is important to use end-to-end encrypted messaging.
- Ensure that any tools or equipment connected to the phone are secure (headset, charging system).
- Never connect your terminals to public USB charging stations.
- Avoid public wifi networks.
- Favour secure sites.
- Remove “SyncManager”, “IphoneInternalService”, if these applications are installed on your smartphone.
Go Further with TEHTRIS
At TEHTRIS, our priority is to ensure your safety.
We offer tools dedicated to securing smartphones. TEHTRIS MTD has the ability to identify and detect in real time known or unknown threats.
Our MTD allows:
- analysis of the rights & authorizations of applications
- scheduling regular scans
- detection of brute force attempts
It extends protection to mobile devices running Android, iOS, iPadOS and Chromebook.
TEHTRIS MTD, natively integrated with the TEHTRIS XDR Platform, protects the mobile fleet, allowing to benefit from our latest innovative technologies and to ensure a defense in depth. This solution guarantees optimal security of devices .
For more information more: Discover TEHTRIS MTD.

