A good understanding of active threats is necessary to achieve a good security posture. The following report provides actual trends that emerge from the Internet Background Noise. The following data is based on the monitoring of two weeks of our Honeypots logs.
European honeypots: SSH connection attempts with credentials

Italy registered the most connection attempts (18%), Spain ranks second (10%) and Lithuania third (9%).
The most common logins that were used for authentication were:
- root
- 345gs5662d34
- admin
- user
And the most common passwords:
- 3245gs5662d34
- 345gs5662d34
- 123456
- admin
Most exploited CVEs
TEHTRIS NTA monitors exploit attempts on our honeypots. Here are the CVE that are the most used by threat actors to opportunistically get initial access on vulnerable devices connected to the Internet all over the world:
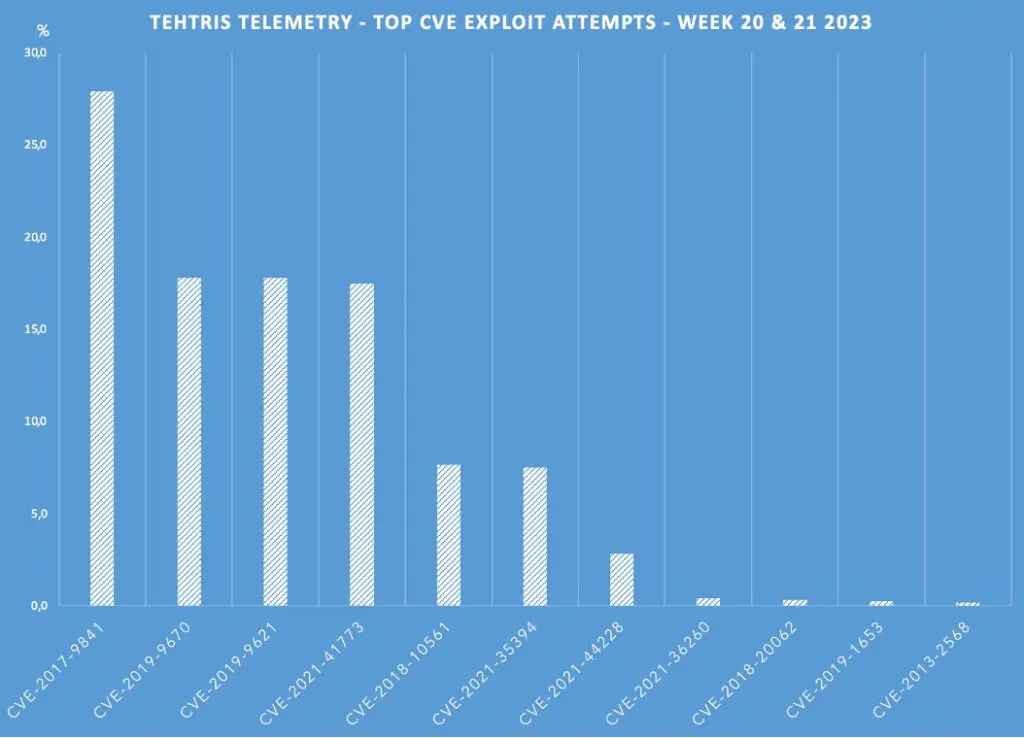
As depicted on the chart, the top 5 CVEs exploited by malicious actors are :
- CVE-2017-9841 (CVSS3.1 9.8) in PHP Unit which allows remote attackers to execute arbitrary PHP code (28%)
- CVE-2019-9670 (CVSS3.0 9.8) in Synacor Zimbra Collaboration Suite which has a XML External Entity injection (XXE) vulnerability (18%)
- CVE-2019-9621 (CVSS3.0 7.5) , also in Synacor Zimbra Collaboration Suite (18%), which is not mentioned in CISA’s known vulnerabilities catalog.
- CVE-2021-41173 (CVSS3.1 5.7) in Go Ethereum protocol (18%) leading to crashing
- CVE-2018-10561 CVSS3.0 9.8) in Dasan GPON home routers allowing to bypass authentication (7,5%)
This is a reminder – if it was ever needed – that old vulnerabilities are still actively exploited by threat actors to gain initial access. Vulnerabilities as old as 2013 – such as a command injection vulnerability in Zavio IP Cameras discovered in 2013 (CVE-2013-2568) – are still in their arsenal of tools. The CISA’s catalog does not mention this CVE although our investigation shows that it has been used to target European servers. You should make sure that all your devices are up to date.
European honeypots : constant EternalBlue exploit attempts
Want to learn more on this subject?
More insights on this research issued from the alerts on our worldwide honeypots network.
Subscribe to our bi-monthly threat intelligence newsletter
Where do most attacks come from ?
Want to learn more on this subject?
More insights on this research issued from the alerts on our worldwide honeypots network.
Subscribe to our bi-monthly threat intelligence newsletter
Information remain TEHTRIS sole property and reproduction is forbidden
TEHTRIS is and remains sole property rights owner of the information provided herein. Any copy, modification, derivative work, associated document, as well as every intellectual property right, is and must remain TEHTRIS’ sole and exclusive property. TEHTRIS authorizes the user to access for read use only. Except as expressly provided above, nothing contained herein will be construed as conferring any license or right under any TEHTRIS’ copyright.
No warranty and liability
TEHTRIS will not be held liable for any use, improper or incorrect use of the information described and/or contained herein and assume no responsibility for anyone’s use of the information. Although every effort has been made to provide complete and accurate information, TEHTRIS makes no warranty, expressed or implied regarding accuracy, adequacy, completeness, legality, reliability, or usefulness of any information provided herein. This disclaimer applies to both isolated and aggregated uses of the information.

