Network Traffic Analysis (NTA), Network Detection and Response (NDR) or Network Analysis and Visibility (NAV) was coined by Gartner.
It is a security solution that intercepts, analyzes and records telemetry of network traffic communication patterns and flow records. To do this, the technology relies on AI via machine learning (ML) and behavioral analysis.
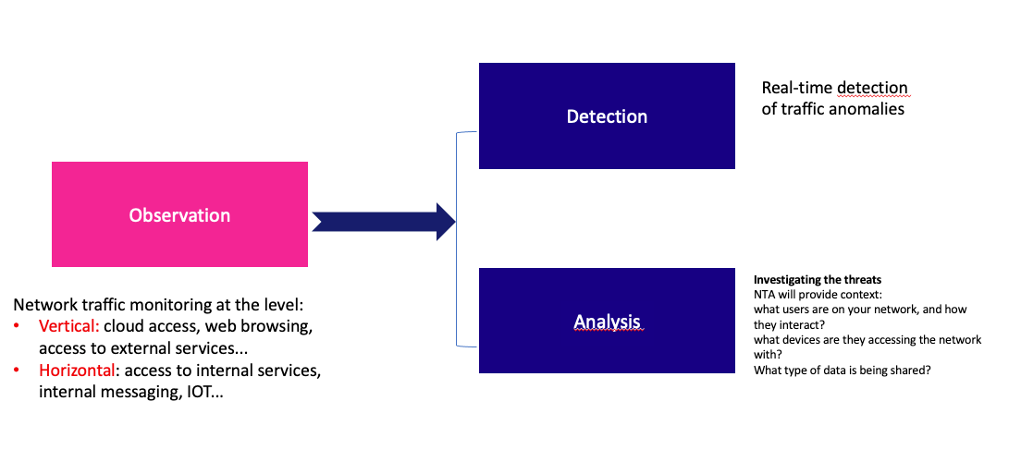
TEHTRIS NTA is a tactical solution for analyzing your network flows in real time, using flow capture, metadata (NetFlow) and passive auditing mechanisms.
The monitoring is total since this technology monitors north-south and east-west traffic.
Advantages of the NTA solution
NTA solutions are powerful tools for any organization, adapting to new attacker methods. They represent the defensive layer that all companies need.
They provide real-time alerts, which is a considerable asset when you know how quickly a threat spreads.
Visibility without blind spot
As we have just seen, NTA technology could monitor a range of communications in real time. This 360° view is a real plus in terms of security.
All entities in a network are observed and analyzed, all types of network communications, including TCP/IP packets, cloud traffic, virtual network, APIs, applications, users, routers, switches, firewalls, IOTs nothing escapes the NTA technology.
If abnormal traffic or irregular network activities are detected, then the alarm is triggered.
This detection can be done within the company, but also for roaming employees.
This solution detects the threat coming from inside (an unsecured port activated by mistake), as well as from outside the network.
Self-learning and advanced detection
NTA solutions evolve in real time and are self-feeding. It is an iterative process.
The network traffic analysis will learn from the behavior of the environment by considering the behavior of the entities, to avoid false positives. Without this analysis of the normal and the ‘abnormal’ there would be too much noise.
To put it simply, the AI will feed itself from the data and the behaviors identified. From this data, it will be able to identify patterns and make predictions without human intervention.
The NTA uses AI and behavioral analysis, it is the combination of these two technologies that represents a real added value in the detection of ransomware, DDOS attacks, …
Thus, the slightest connection to an unusual remote access, connections from a foreign country, the use of restricted protocols, will be immediately detected.
Finally, the automation of the detection process will allow to define rules and to correlate them according to different parameters. This detection based on these new rules will in turn allow to search for the modus operandi of the attackers: the TTPs and to further improve the detection and the understanding of the threat.
Time saving
Technical teams will gain complete visibility in record time.
They will be able to detect anomalies immediately, determine the cause, and implement appropriate measures.
Security teams will focus on removing threats rather than detecting them.
This time savings is invaluable in cybersecurity.
Good practice of the NTA solution implementation
Each company is different, and each solution must be implemented according to the specificities of the organization.
- The first thing to determine is to define and categorize the data sources: servers, workstations, routers, etc. It is also important to know the suppliers, the security policies and the configurations in place within the company.
- The second thing is to choose the right collection method (with or without agent).
- Provide a separate storage space for the collection of information.
-
Beware of false positives, it is important to configure your alerts properly.
- Integrate the NTA solution with other security solutions to optimize response capabilities. TEHRTIS offers DNS Firewall solutions, Deceptive Response decoys, VPN protection with our partner The GreenBow…
- Of course, it is important not to forget to train security teams to these new products. TEHTRIS accompanies each of its customers in the implementation of its solutions. This is also the advantage of proximity and a sovereign solution.
Why choose TEHTRIS?
Here are 4 reasons to choose TEHTRIS:
- All-in-one solution: TEHTRIS NTA offers unique network flow monitoring capabilities with a signature-based NIDS component, a network forensic component with a tactical behavioral engine, and passive auditing to reduce the exposure surface.
- Enhanced security: the entire disk is encrypted, with advanced protection mechanisms such as RBAC in the kernel and anti-0-day protection.
- Adaptability: TEHTRIS NTA can easily work with IT (Internet/LAN) or OT (SCADA/ICS) environments or even with recent IoT environments.
- An integrated solution: Unlike many products, TEHTRIS NTA does not require the use of a SIEM to be useful, as the solution is directly integrated into the TEHTRIS XDR Platform, in order to enrich this ecosystem.
[1] NTA: The other IDS? By Anton Chuvakin | September 20, 2018

