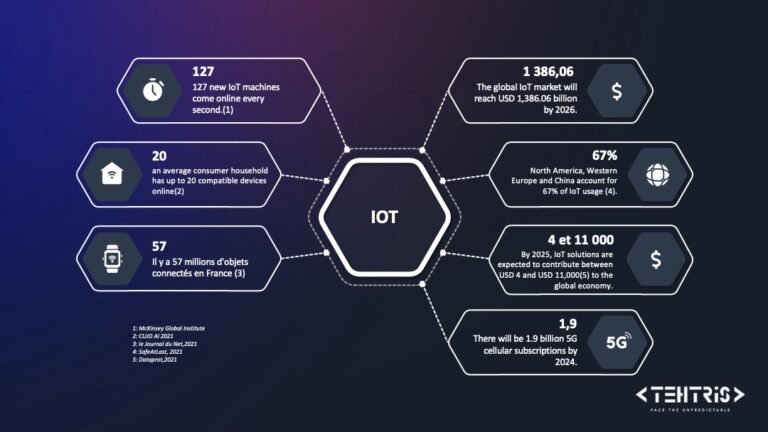
75 billion devices will be online by 2035 and according to the latest GALLUP survey from 2020 “Mobile users, on average, spend about 80% of their time outside the protected corporate network, accessing the Internet from locations other than the office or company.”
These new objects are invading our home, our privacy and becoming not only a threat to the individual but also to the enterprise. The boundaries between home and business are often blurred. After all, who would think that their watch could be an entrance to the corporate network? Yet threats targeting Internet-connected “smart” devices are starting to multiply and remain vulnerable.
In one of our articles, we already mentioned the threats related to smartphones, let’s see here more globally the threats related to IOT which are becoming a target of choice for cybercriminals. The latter have understood very well that in order to access a company’s entire network, all they have to do is to break into one of these unprotected devices.

Definition & Observation
« The apparent uselessness of the object made it doubly attractive ».
G. Orwell, 1984
An IOT: Internet of Things is an object or a set of physical objects with the ability to connect to the Internet or a communication network. These objects communicate via Wi-Fi, Bluetooth, 4G…. and can communicate with each other.
- personal assistants
- smartphones
- tablets
- connected toys for children
- Surveillance cameras
- All home automation such as: sensors, shutters, blinds, gates, switches, connected sockets, smart locks, video doorbells …
- connected scales, connected watches
- dishwashers, ovens, and some refrigerators
- …
We leave more and more digital traces and the particularity of these objects is that they produce large amounts of data, data that can be exploited by cyber attackers. Let’s see how.
What are the cyber threats?
« With the development of television and the technical perfection that made possible, on the same instrument, simultaneous reception and transmission, it was the end of private life. »
G. Orwell, 1984
The primary goal of cyber attacks is to retrieve company information, confidential data, financial data… The rise of connected objects exposes users to risks, but also exposes their company to the same threats. Devices with an IP address, fitness devices, connected watches, PDAs, wireless printers, are a real danger for a company. Most of the time, companies are not even aware of their existence and therefore cannot cover the risk.
Data Exfiltration
Data exfiltration can be explained by several flaws present in IOTs.
Poor device management
The lack of device updates, perhaps the royal road to vulnerabilities and therefore a boon for cyber attackers. An attacker can trick the consumer into making a fake update on their personal device… which they also use to check their work email.
- In 2019, a vulnerability affecting the Avastar wifi firmware, was identified. Many laptops (Microsoft Surface, Samsung Chromebooks, Samsung Galaxy), smartphones, gaming platforms (Sony PlayStation 4, Xbox One), routers and IOTs were affected.
Here are two other cases not directly related to an attack on a company but with real impacts
- It involves a vulnerability in six types of pacemakers manufactured by the company Abbott, which were urgently recalled because they had a serious security flaw that could lead to the death of patients.
- In September 2021, WebsitePlanet revealed a 16.71-gigabyte data exfiltration containing 61 million entries from connected watches. The company GetHealth, a data synchronization tracker, was impacted by this security breach.
Larger physical attack area.
With the multitude of objects, the field of attack is much wider. It is no longer only done on computers but also on objects that accompany us in our daily lives
- In 2019, the Silex malware attacked more than 2000 devices by removing all firewall rules, network configuration and finally the device. The attacker behind this malware was none other than a 14-year-old teenager.
- Criminals have a wild imagination, a casino and its customers in London were victimized. The data was stolen through a thermometer connected in an aquarium! The device in question was connected to the same network as the casino. Who would have thought that a thermometer could be dangerous for a company? The protocols used in IoT systems can have real security issues.
Unsecured data transfer
Finally, the other attack vector for a cybercriminal is to target these devices to access personal or corporate networks through data transfers. By taking control of a smartphone, they can send messages and emails on behalf of the victim to obtain information or cause disruption. Each time data is transferred, the risk of a data breach or compromise increases.
Before connecting any personal devices to business equipment, it is imperative to ensure the company’s security policy. The attacker can take advantage of the mobile device’s access to the company’s Wi-Fi network and can gain access to company data when the victim returns to the office.
By infecting these new objects attackers can also turn IOTs into botnets.
DDOS and Botnet Attacks
Cybercriminals can use botnets to attack IoT devices that are connected to other devices, this was the case with the botnet named This attack took place in 2016. The cyber attackers launched a denial of service attack relying on an army of surveillance cameras (145,000 cameras) and other IOTs, in total 380,000 bots. The Trojan in turn infected hundreds of thousands of connected objects. The attack led to the cutting of access to major sites such as Amazon, Twitter, and Spotify.
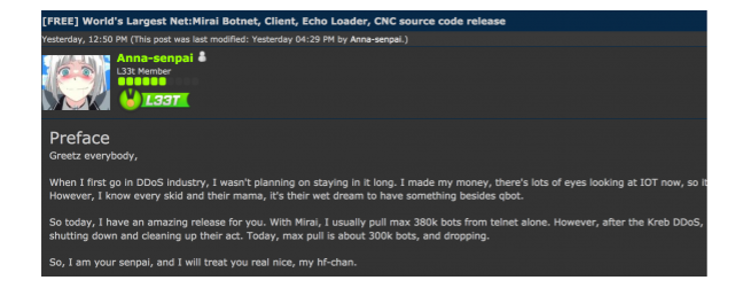
Other botnets followed this attack, such as Gafgyt in 2019 (which relied on Wifi routers), IoT Reaper: the “Great Reaper” in 2019 which targeted vulnerabilities in routers, IP cameras, affecting a million companies worldwide, Hajime, Omni Botnet, etc. examples abound.
The reason for such attacks is due to the weak security of these objects, open ports, unmodified credentials, outdated IOT, without updates, as we have seen above.
Identity theft
What if tomorrow, the cybercriminal attacked your connected watch? Why would they do that? Simply to obtain data on users and organizations that will be used for future identity theft. Since your watch is also connected to your smartphone, which in turn is used to connect to the office, the cocktail becomes explosive. The attacker will thus exploit the vulnerability of an object to infiltrate the company’s system.
- In 2019, the login credentials of thousands of Ring camera owners were published online, 3,672 sets of emails, passwords, phone number were stolen.
- In 2021, startup Verkada Inc. was hacked. 150,000 surveillance cameras in hospitals, businesses, police departments, prisons and schools were affected. The data breach was committed by an international group of hackers.
Social Ingeneering
Social engineering attacks are made easier with the arrival of IOT. Your watch, your personal assistant, your smartphone, are a knowledge base for the attacker. The sensors integrated in the connected objects collect very detailed data on their environment and their users, allowing the attackers to obtain confidential information, bank details, purchase history, your address, your name and surname, your pseudonym, your date of birth, your weight, your height, your gender, etc. All this information will allow him to refine his future attacks.
The data from your connected watch, for example, can give your GPS location, your agenda and once combined, this information can create a map of you. This compiled data is sent by your service provider and can even be resold.
One of the simplest vulnerabilities that a cybercriminal will exploit is to find the login credentials. He will use the “brute force” technique or simply retrieve your credentials (defined by the manufacturer) by default during the first use. Because many of us do not change them! The criminal will then have access to the entire network and will be able to extract your information
Your cell phone could be used for industrial espionage.
Espionnage
- Spyware applications are also a significant threat, as we have seen with the Pegasus case, since they allow to retrieve phone conversations, access cameras and steal information…
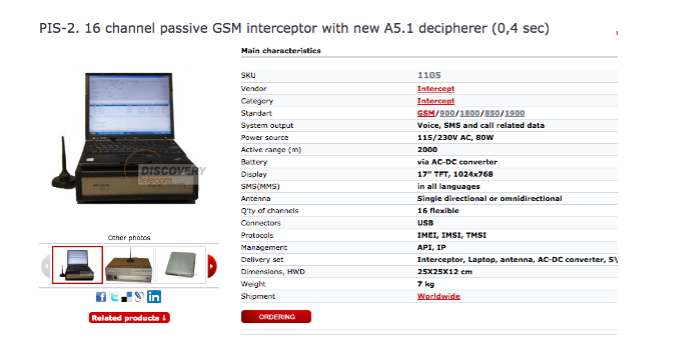
- Stingray / GSM interceptor / IMSI catcher, are interceptors that can be found on the black market and are capable of hacking cell phones and collecting data.
A cyber criminal can also attack via a smart camera in an organization or in the private sphere and record video, or audio footage (eavesdropping) and thus recover confidential information, production secrets, etc.
- In 2018, an exploit against Alexa and Google Home had been discovered and had made a lot of noise, damaging the reputation of the products. The exploit made it possible to spy on victims and retrieve confidential information.
- Other cases reported cameras sold by Amazon, produced in China, have escaped the vigilance of security protocols. More than 50,000 connected cameras had critical security flaws.
- Internet-connected baby monitors suffered the same fate. This is what happened to an American couple (the Beirnes) in 2021. Of course, that was not in the business world, but a camera monitoring the security of an industrial site or offices, could be used in the same way.
- The Danish intelligence services revealed the “Dunhammer operation” which dates from 2015. Members of parliament and members of the French, Norwegian and Swedish administrations were spied on between 2012 and 2014. Angela Merkel would also have been a victim of phone tapping.
What future for IOT?
Internet of Things devices are an integral part of your lives and still remain the least secure.
As we have just seen through multiple examples, new attacks are imagined every day, and security systems must therefore be tested and updated. The use of machine learning algorithms may bypass defensive systems, creating new attack vectors.
Even if governments are finally reinforcing their requirements to industry (the European Telecommunications Standards Institute (ETSI) has launched cyber security standards to protect users of smart devices) and regulation is a necessary step, it remains insufficient.
One of the most effective the protections is to be careful about what we connect to our networks, and to respect the basic protections.
We will see in a next article how.
[1] IBM Data

