When reviewing logs from a company, TEHTRIS CERT found multiple instances where an IP address had been trying to contact sensitive servers. Since these servers were unknown to open source databases, an investigation was conducted to understand how a potential attacker could identify the IP addresses of the company’s sensitive servers.
Approach
In order to determine the potential impact as soon as possible, we made assumptions based on:
- the nature of the systems concerned (web servers, email, etc.);
- the technologies employed;
- the size of the attack surface (a single web server or a hundred servers of a different nature?);
- the level potentially required for an attacker to succeed in intruding;
- the intrusion techniques known by TEHTRIS on the exposed technologies.
Among the hypotheses that we formulated, the most risky one revealed the possibility of a computer attack attempt to compromise the information systems of the company or one of its customers.
The most likely hypothesis suggested that a robot could have managed to scan all the IP addresses used by the company in order to discover the exposed services.
In this case, how would it work?
Identification
In order to verify our hypotheses and answer our questions, we had to start by collecting all the elements in our possession. To do this, a search was conducted to establish an exhaustive list of servers that had received network connections from the malicious IP address.
This was followed by an open source analysis of the malicious IP address to determine:
- the country of origin;
- the number of the AS BGP that this IP address belongs to;
- its reputation;
- current and previously hosted services.
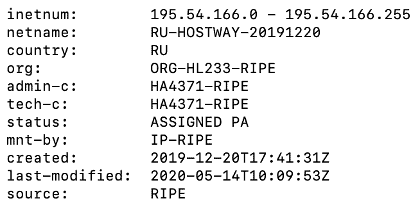
The public information accessible via a “whois” search allowed us to affirm that the malicious IP address was part of the address range 195.54.166.0/24, corresponding to servers based in Russia, near St Petersburg.
We then verified, through open source intelligence, whether the addresses of the targeted company could be discovered by recognition techniques based on certificate transparency, by querying public search engines and crawlers or via passive DNS. This was not the case here.
Knowledge of the threat
At the instigation of TEHTRIS CERT and in order to build up an intelligence base of cyber-oriented network interest not dependent on foreign companies or technologies, TEHTRIS implemented a sensor network covering most European countries that has collected more than 25 million records over the last two months.

The information collected by these sensors is stored in a knowledge base using big data technologies, allowing us to quickly query them and search for the presence of particular events.
Thanks to this knowledge base, in the case of our malicious IP address having solicited a large number of sensitive servers, we were able to determine that it was in fact the source of scans destined for many European countries. From May 20, 2020 to June 9, 2020, eleven of the countries covered by our sensors were actively scanned.
On the basis of these elements, we were able to conclude that the attempted attack was not targeted and that it was the result of a massive scanning campaign aimed at the countries of the European Union, at the very least.
LIST OF COUNTRIES TARGETED BY THE MALICIOUS RUSSIAN IP ADDRESS:
| Germany | Belgium | Spain | Finland | France |
| Italy | Ireland | Lithuania | Portugal | Czech Republic |
The IP address associated with this incident does not belong to any known Internet monitoring projects (such as Shodan, ZoomEye, etc.) and does not have an associated DNS record.
Thus, everything suggests that it was a server that was leased for a limited amount of time, to scan ports and vulnerabilities across a wide area for malicious purposes.
Conclusion
The deployment of a network of sensors at the European level allows TEHTRIS to have a knowledge of past, current and future events, making it easier to remove any doubts.
The analysis of the collected elements and their evolution allows us to identify changes in the behavior of the attackers. For example, when the exploit of the SMBghost vulnerability was made public, we noticed an increase in scans targeting the TCP/445 port, allowing for remote code execution.
In a future article, we will see that only the observation of targeted ports and protocols can sometimes allow us to identify vulnerabilities sought by attackers before they are exploited.

