Definition : what is an UES ?
UES, or Unified Endpoint Security in its long version, is a fairly recent concept in the cybersecurity market. It responds to the need for global protection on a complete set of workstations, remote PCs, mobiles, tablets, etc.
Like its predecessor UEM (with M for Management), a UES solution displays the real-time status of this fleet on a unified console. The real value of the UES system lies in its S (for Security), since it represents its ability to detect and actively fight against known and unknown threats. Seeing is good, being protected is better.
UES is therefore the combination (or bundle) of EDR, EPP and MTD tools, thus providing protection on all endpoints.
As the concept is relatively recent, few service providers are ready to provide this complete protection. TEHTRIS is identified as one of them by Gartner (Rob Smith & Dioniso Zumerle, Innovation Insight for Unified Endpoint Security, Nov 2020)
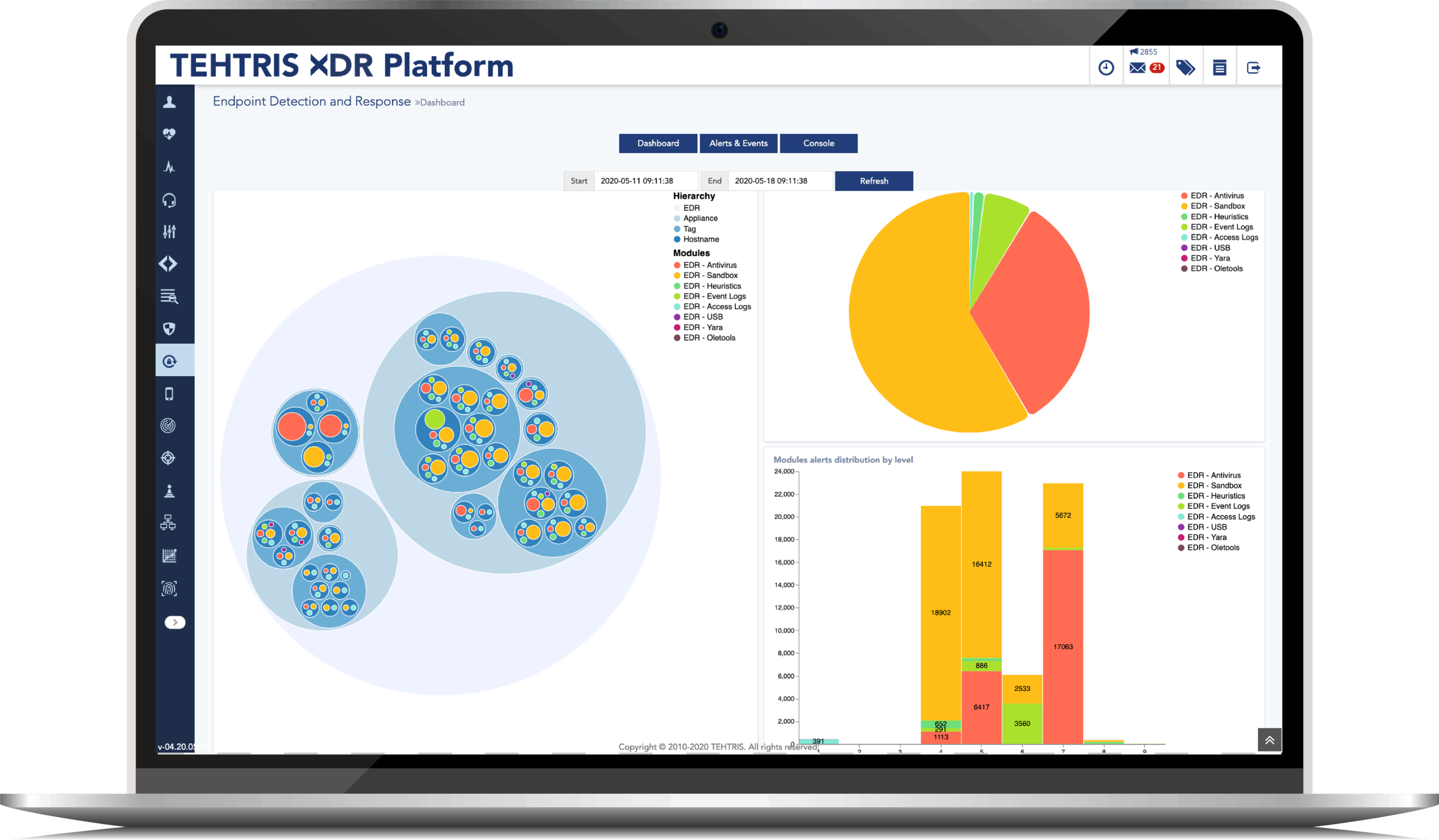
What does it matter at this time ?
Businesses around the world are currently facing a chaotic cyber environment. Attackers are attempting to take advantage of the COVID-19 pandemic and the insecure home-based environments in which organizations have been forced to continue operating.
With this unprecedented situation, corporate business continuity plans have sometimes been forced to relax the very strict security rules that were previously enforced inside the walls. Mobile devices, laptops and remote PCs are now accessing data that was once better protected.
Today, these external devices expose organizations to new threats that must be stopped because attackers are very resourceful in launching targeted attacks against both large and small organizations.
Endpoint monitoring and protection – the two most popular methods.
There are two main themes that enable organizations to control and protect their endpoints: management and security.
On the one hand, Unified Endpoint Management offers centralized management of all mobile devices, desktops, laptops and every other type of endpoint you can imagine. It helps organizations manage an ever-increasing range of endpoint and IoT needs, so it’s critical that they have visibility and control over all endpoint environments from a unified console.
On the other hand, Unified Endpoint Security, the subject of this article, which is layered on top of UEM systems, with additional security features offered by Endpoint Detection and Response (EDR), Endpoint Protection (EPP) and Mobile Threat Defense (MTD) technologies.
What is the added value of Unified Endpoint Security systems? And why choose them?
An effective UES solution will work in two stages:
- It detects and responds to risks and threats on all endpoints;
- It provides a global view, and offers correlations and threat management across all endpoints.
Here are the main components of a UES system and what they bring to it:
An [EDR] Endpoint Detection & Response – An EDR solution detects and neutralizes known and unknown threats. Such a system will be able to spot stealthy espionage efforts without malware or weapons, learn the techniques used by hackers and counter them by building solutions upstream. The ideal EDR solution for you will also be equipped with Data Science so you can rely on real data in anomaly detection and decision making, Cyber Threat Intelligence (CTI) to cover millions of endpoints globally, and a clear dashboard to help your SOC team gain visibility into the overall security of your infrastructure.
An [EPP] Endpoint Protection Platform – An EPP solution protects operating systems from known threats with advanced antivirus and scanning capabilities. An effective EPP platform should have a threat knowledge base built into the antivirus engine that is automatically updated and optimized to protect your systems against a wide range of viruses. Advanced features should complement local antivirus protection by fighting vulnerability exploitation. The behavioral analysis capabilities of an EPP system will also allow for real-time detection of advanced and unknown attacks with suspicious process migrations and memory executions.
And finally, the centerpiece for mobile devices, an [MTD] Mobile Threat Defense – An MTD solution strengthens the security of a mobile fleet (smartphones and tablets), for example by analyzing applications as soon as they are installed and during updates. Ideally, the MTD application installed on mobile devices can discover vulnerabilities at the local configuration level. Such a solution can help you equip your mobile devices with anti-malware tools and meet compliance requirements by storing technical information from these devices in a central repository.
The combined effectiveness of these 3 devices provides unified security across all your endpoints. The resulting UES solution has a single console, and allows you to detect and assess previously undiscovered threats through cross-data analysis.
The benefits of Unified Endpoint Security?
The need to consolidate security and operations to achieve significant productivity and gains is driving a strong demand for UES-type solutions.
For example, MTD solutions were adopted by sensitive entities (military environments, governments, and regulated organizations), but are now becoming more mainstream, given the need for large organizations to monitor the mobile and tablet fleets of all their employees.
Ultimately, UES will reduce your costs by reducing the number of consoles you need to monitor and manage. From a single, unified console, you can oversee attack detection and response. This is ideal for neutralizing a variety of threats, such as ransomware on multiple PCs, hacks on multiple tablets, or attacks related to common indicators of compromise (phishing on mobiles and PCs, etc.).
Learn about TEHTRIS UES, a single console solution powered by machine learning and AI.
The three TEHTRIS modules EDR, EPP and MTD integrate and create a UES platform with a unified console that protects your endpoints against known and unknown threats. The great strength of these modules is their hyper-automation: they are programmed to act and interact completely autonomously. In the case of an unknown threat, they stop the suspicious process, analyze it and make the decision to let it run or destroy it.
Today, our solutions are deployed in more than 70 countries, and are used by customers and partners who trust us to deliver uniquely reliable security products, either out-of-the-box or customized.
If you’re looking at UES adoption with two main goals in mind: to extend detection and response from traditional endpoints (laptops and desktops) to mobile devices; and to get a single security component from which you can seamlessly manage the security of all endpoints, then TEHTRIS solutions are ideal for you.
Now that the subject is clear to you, we invite you to read on and learn more about TEHTRIS UES and lead your organization to more mature data protection.

