Abstract
This report provides an overview of recent developments in the cyber threat landscape over the past two weeks. It highlights a critical privilege escalation vulnerability in sudo (CVE-2024-32463), as well as the ongoing Houken campaign targeting French organizations through Ivanti appliance vulnerabilities, with suspected links to Chinese state-sponsored actors. The ransomware ecosystem remains highly active, with Qilin leading in victim count. A detailed focus on SafePay reveals its rapid growth, preferred targets, and operational tactics. This report includes indicators of compromise (IoCs) to support detection and mitigation efforts.
CERT
CVE-2024-32463 (aka “chwoot”)
A vulnerability has been introduced in version 1.9.14 of sudo with the feature -R, allowing the attacker to escalate privilege to root. Version between 1.9.14 (June 2023) and 1.9.17 (except 1.9.17p1) are vulnerable, and exploits using this technique are still mostly undetected.
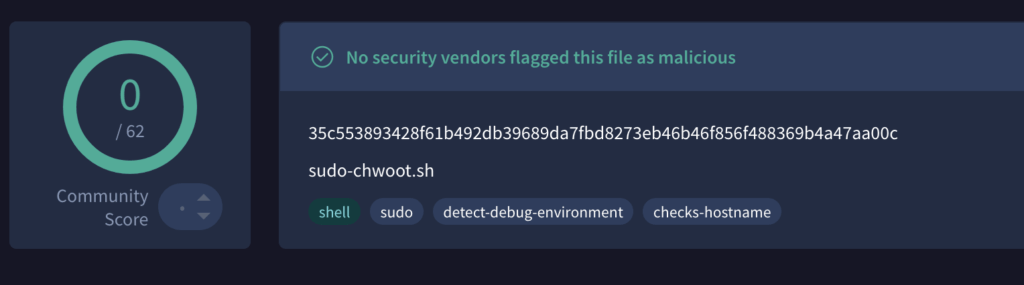
A POC is available here.
SHA256
35c553893428f61b492db39689da7fbd8273eb46b46f856f488369b4a47aa00c
7060cb480aad1973e548a06f5ed82b7378b7a00166d34d8d92610407e7094cab
3ba394c88abc6a45d6757f456707f8ef0ef6e912c4a32ce50dc27f30ad698245
35c553893428f61b492db39689da7fbd8273eb46b46f856f488369b4a47aa00cHouken campaign
Since September 2024, the Houken campaign has been targeting french entities by leveraging multiple vulnerabilities, but most notably the CVE-2024-8190, CVE-2024-8693 and CVE-2024-9380 in Ivanti Cloud Service Appliance.
Targets include governmental, telecommunications, media, finance and transports entities.
Two primary objectives have been identified: the first is establishing initial access via a rootkit for intelligence gathering by suspected Chinese state-sponsored actors; the second is financially motivated, involving cryptomining and data exfiltration.
The ANSSI suspect that the Chinese state-sponsored threat actor UNC5174 is behind the campaign.
The full report is available here.
SHA256
f32d1dbbce880ce57f0635ce3acebff1e2b0005480dde98956ba9eb903d9a393
3bbbef1b4ead98c61fba60dd6291fe1ff08f5eac54d820e47c38d348e4a7b1ecCybercriminality
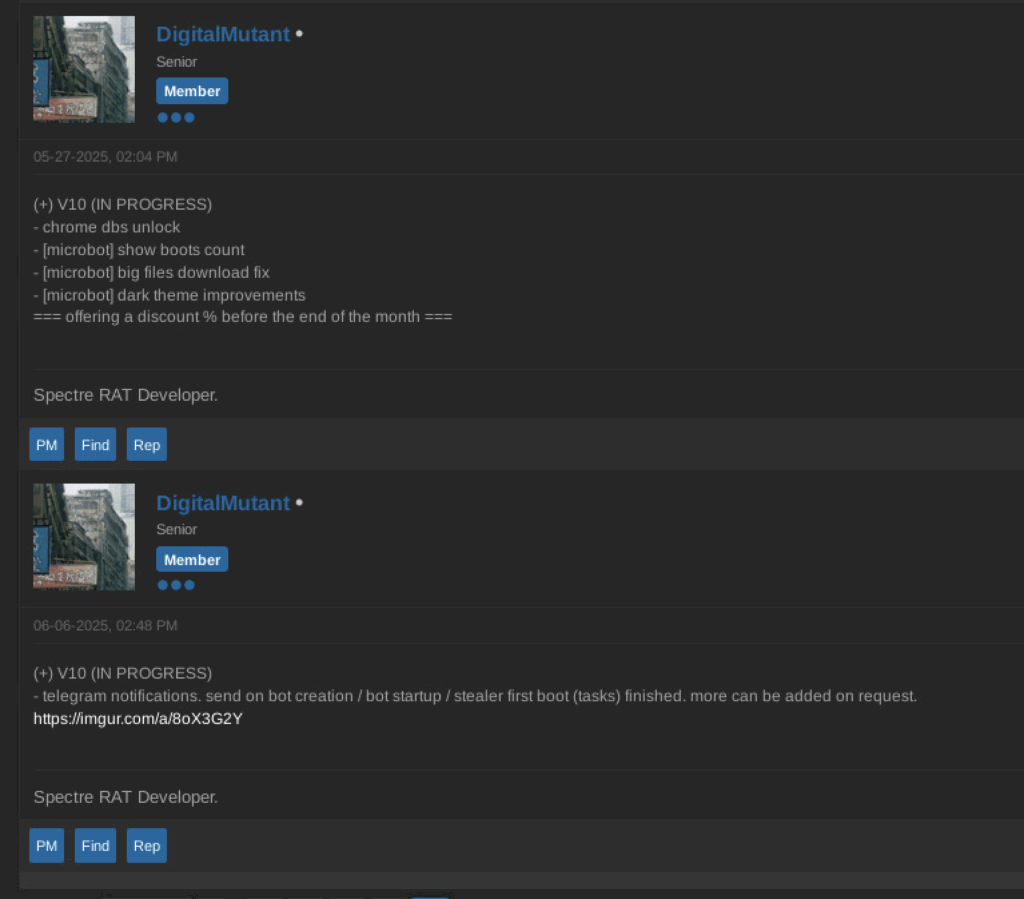
(In progress) SpectreRAT v10
SpectreRAT v10 is in developement and should feature some new or improved capabilities, such as:
- Improved stealth mode
- VirtualBox detection
- Improved cookie stealers for Chrome
- VNC
- Clipper address swapper
- Autorun methods on shutdown
(New) Nemesis RAT
Nemesis is a new RAT being sold on CryptBB claiming to be fully undetectable with no logging and a decentralized C2 using P2P over Tor, I2P or Zeronet.
Ransomware
Victims around the world (25/06 – 09/07)
This interactive world map highlights the distribution of ransomware victims. Hovering over each country reveals a list of known victims for these last two weeks.
Unsurprisingly, the United States remains the most heavily targeted.
(Data from Ransomfeed)
Most targeted sectors (25-06 – 09/07)
This graph displays the distribution of ransomware victims by industry sector.
Professional services and manufacturing are by far the most targeted.
(Data from Ransomfeed)
Group ranking based on activity (25/06 – 09/07)
This table shows a ranking of ransomware groups activity based on victims count the last two weeks.
Qilin* is currently the most active ransomware group, with 41 victims these past two weeks.
| rank | name | victims | change |
|---|---|---|---|
| 1 | qilin* | 41 | ➖ |
| 2 | play | 21 | 🔺 (+4) |
| 3 | akira | 19 | 🔺 (+5) |
| 4 | safepay | 18 | 🔻 (-1) |
| 5 | dragonforce | 13 | 🔻 (-1) |
| 5 | payoutsking | 13 | ⭐️ |
| 7 | handala | 10 | 🔻 (-1) |
| 8 | kawa4096 | 9 | ⭐️ |
| 8 | worldleaks | 9 | ➖ |
| 8 | incransom | 9 | 🔻 (-3) |
(Data from Ransomfeed)
*A report on the group, a technical analysis and IoC on Qilin is available here.
Focus on SafePay
With 18 victims over the last two weeks and 247 victims all time, SafePay is among the most active ransomware groups. Below is a breakdown of SafePay activity, victim profile and IoCs.
The SafePay ransomware group was first reported in November 2024 by Huntress and has started to become one of the biggest cybercriminal actors over the last 4 months.
The following graph illustrates the number of SafePay victims reported each month. An upward trend can be noticed, highlighting the group’s rapid growth.
(Data from Ransomfeed)
SafePay appears to heavily target organizations in North America and Europe, as illustrated in the map below.
(Data from Ransomfeed)
The sectors that are the most hit by SafePay are the legal and professional services, construction and engineering, but SafePay can target any field, including healthcare (63 victims) and non profits (10 victims).
(Data from Ransomfeed)
The group’s blog gives a listing of victims, which includes the name of the victim, their revenue, the size of the zip containing stolen data and a download link to the zip itself.

The group’s page gives a listing of victims, which includes the name of the victim, their revenue, the size of the zip containing stolen data and a download link to the zip itself.

IoC
Ransom files
readme_safepay.txtRansom note
Greetings! Your corporate network was attacked by SafePay team.
Your IT specialists made a number of mistakes in setting up the security of your corporate network, so we were able to spend quite a long period of time in it and compromise you.
It was the misconfiguration of your network that allowed our experts to attack you, so treat this situation as simply as a paid training session for your system administrators.
We’ve spent the time analyzing your data, including all the sensitive and confidential information. As a result, all files of importance have been encrypted and the ones of most interest to us have been stolen and are now stored on a secure server for further exploitation and publication on the Web with an open access.
Now we are in possession of your files such as: financial statements, intellectual property, accounting records, lawsuits and complaints, personnel and customer files, as well as files containing information on bank details, transactions and other internal documentation.
Furthermore we successfully blocked most of the servers that are of vital importance to you, however upon reaching an agreement, we will unlock them as soon as possible and your employees will be able to resume their daily duties.
We are suggesting a mutually beneficial solution to that issue. You submit a payment to us and we keep the fact that your network has been compromised a secret, delete all your data and provide you with the key to decrypt all your data. WE ARE THE ONES WHO CAN CORRECTLY DECRYPT YOUR DATA AND RESTORE YOUR INFRASTRUCTURE IN A SHORT TIME. DO NOT TRY TO DECRYPT YOUR FILES YOURSELF, YOU WILL NOT BE ABLE TO DO THIS, YOU WILL ONLY DAMAGE THEM AND WE WILL NOT BE ABLE TO RESTORE THEM.
In the event of an agreement, our reputation is a guarantee that all conditions will be fulfilled. No one will ever negotiate with us later on if we don't fulfill our part and we recognise that clearly! We are not a politically motivated group and want nothing more than money. Provided you pay, we will honour all the terms we agreed to during the negotiation process.
In order to contact us, please use chat below, you have 10 days to contact us, after this time a blog post will be made with a timer for 3 days before the data is published and you will no longer be able to contact us.
To contact us follow the instructions:
Install and run “Tor Browser” from https://www.torproject.org/download/
2) Go to http://safepayinzkjqijq6qyker2kmq7pri5hy65tzisslkhiei47kltx2iad.onion/
Log in with ID: <<CENSORED>>
When you first login, you need to set a password.
IMPORTANT if you are not a decision maker in your company, do not login to the chat.
Contact and wait for a reply, we guarantee that we will reply as soon as possible, and we will explain everything to you once again in more detail.
Our blog:
http://j3dp6okmaklajrsk6zljl5sfa2vpui7j2w6cwmhmmqhab6frdfbphhid.onion
http://nz4z6ruzcekriti5cjjiiylzvrmysyqwibxztk6voem4trtx7gstpjid.onion
Our TON blog:
tonsite://safepay.tonEncrypted file extension
.safepayURLs
nz4z6ruzcekriti5cjjiiylzvrmysyqwibxztk6voem4trtx7gstpjid.onion
j3dp6okmaklajrsk6zljl5sfa2vpui7j2w6cwmhmmqhab6frdfbphhid.onion
safepayinzkjqijq6qyker2kmq7pri5hy65tzisslkhiei47kltx2iad.onionHashes
0f23a313f79d54ae2102f193d3de1a6a98791c27921f28a4fab1092bcb43e5ee
327b8b61eb446cc4f710771e44484f62b804ae3d262b57a56575053e2df67917
f0127e786c9fb7bf2c8c999202d95c977af4c26cc27302a6ee352cfd62869e7b
94244ec2480addeaebb43aebbe48cee94f7f429231aa054f4c26f671653163b0
b3045308a07e46c9f7dd98d352e964f242307ce30df8087dc751488118b5b959
ba1b89023581a0bc7a75f8ede9ec6115d5dda98c0145634f1b98978fbc79c956
7f33c939f7aaf46945d58ed7fd0d1f5c7e3de1ff6a1a591ecc1992dab2a65078
fa74ac0e05b6209b7691511572386f97464ff5728732de99ddd6b5449ffae386
2f49bff45cc091a7bf52dcd061d24f9a7f2cf0ca9b3c12123bd3cf2fac56b481
a0dc80a37eb7e2716c02a94adc8df9baedec192a77bde31669faed228d9ff526
