In the healthcare sector, cyber attacks are not limited to hospitals, pharmaceutical companies, insurers, medical analysis firms, etc. All other institutions likely to hold sensitive information will be targeted by cybercriminals.
Faced with this situation, many initiatives have been put in place.
What are the protection?
A collaborative approach
« TEAM: Together Everyone Achieves More »
As we have seen, in our first article dedicated to health each hospital manages the security of its organization in a disparate way. More than ever, it seems necessary to increase its resilience and this must be done through collaboration. “There is strength in unity” and many initiatives are emerging, such as in France:
- The France relance program offers cooperation between public and private sectors. This program encourages expert cyber structures to help public organizations in the development of security audits, pentesting, vulnerability reviews, governance… This program plans to dedicate € 6 billion to the health sector as part of the Segur of health.
- The ACSS unit (Accompagnement Cyber sécurité des Structures de Santé) renamed CERT-Santé (since April 2021) aims at structuring the cyber ecosystem, reinforcing the technical means, and promoting sovereign solutions. It will mobilize different cyber actors on topics such as prevention, awareness, monitoring, incident handling…
- The “cybersecurity pathway” offered by ANSSI helps healthcare institutions to better resist cyber attacks.
- The Cyber Campus, which brings together around sixty players from the cyber world, is ready to help hospitals and healthcare facilities.
In Spain, the COVID-19 pandemic has had a considerable effect on the cyber security of healthcare facilities.
In 2021, to strengthen the Spanish capabilities to fight and cybersecurity, the government has announced a plan of 450 million euros over three years.
The «Academia Hacker» program is also part of an initiative to better prepare tomorrow’s talent for cybersecurity.
Awareness
27% of its breaches are due to human error, one of the highest percentages of any sector.[1]
When it comes to healthcare personnel, it is observed that they are not sufficiently trained on cyber attacks, and cybercriminals take advantage of this gap. Training and awareness, remain the first brick to be laid in a security program. All end-users must be made aware that cyber security is everyone’s responsibility, and this requires recurring campaigns to raise awareness of computer security. Each staff member and some employees who have a higher threat profile than others must have the ability to detect a phishing email, a suspicious file, an incoherent call… For this, in addition to the theory, it is important to set up so-called “contextual” training, to really put the user in an attack situation, based on current events. These tests should not be a one-off exercise, on the contrary, there should be a certain regularity to allow everyone to fully understand their role and the danger involved.
In Spain, according to our partners Proofpoint, 90% of attacks against healthcare were business email compromise (BEC) attacks. This is a good reminder of the importance of raising awareness among security operations teams and users.
A robust defense strategy
Once the staff is involved, the second brick to be laid will be to arm them. To do this, these structures must be equipped with an effective cyber security strategy.
Promote the segmentation
The second step is network segmentation. The network is increasingly dense, complex (IOT, IT, OT), changing. This sector must manage both physical elements that are connected, such as a camera, secure physical access, but also IOT such as medical devices, medical records, financial records etc. All these elements, both physical and virtual, must be segmented. All environments, whether routers, firewalls, cloud are impacted. Managing this environment is difficult and cybercriminals will take advantage of this complexity. Segmentation is a solution to mitigate the cyber risk. Indeed, it is by compartmentalizing, by identifying sensitive assets, by dividing systems, by isolating certain environments from others, that we can avoid propagation.
Each asset can be protected by a TEHTRIS solution.
Healthcare organizations can ensure data security with TEHTRIS solutions that will protect each endpoint, but also the network flow with its Deceptive Response and NTA technologies.
Zero Trust Concept
Finally, the healthcare sector favors the concept of zero trust in their security strategy: 79%, compared to an average of 75% for all sectors.[2] Healthcare data can become vulnerable and exposed to theft if employees leave files available, or do not store information in the right place, etc. It is therefore essential that certain staff members have no access to sensitive data.
All access to applications and environments is secured from both inside and outside.
- The value of the information and the frequent turnover in this sector require the implementation of a special “zero trust” type of surveillance to detect suspicious activities on the part of the personnel and thus to guard against any internal threat. This requires the implementation of effective e-mail and authentication controls.
- Every supplier that connects represents a risk, and here again security measures and audits must be put in place and enforced to eliminate any risk of attack from the supply chain.
Globally, in the face of all cyber threats and whatever the sector, anticipation is the watchword. Each organization must plan attack scenarios, be ready in case of crisis, understand the nature of cyber threats, as well as master the specific threats to its sector, know its enemy, what are its motivations, who is the target, who are the most targeted people?
By mastering this context, then we can build a solid defense.
TEHTRIS Offer
The healthcare sector is facing technical peculiarities, a permanent race against time, which require a turnkey security strategy. This is why TEHTRIS chose to take an active role in the France Relance project by providing its leading-edge technology to strategic national entities.
According to Gartner, “from the perspective of security and risk practitioners, SRM (security and risk management) managers must deal with intelligent buildings, remotely piloted aircraft or connected medical devices, for example, in a completely different way”. Gartner adds that “security for critical information systems must focus on safety, reliability, resiliency, adaptability and privacy.” [3] Gartner Research lists TEHTRIS as a Representative Vendor Offering XDR in the Market Guide 2021 for Extended Detection and Response.
They trusted us
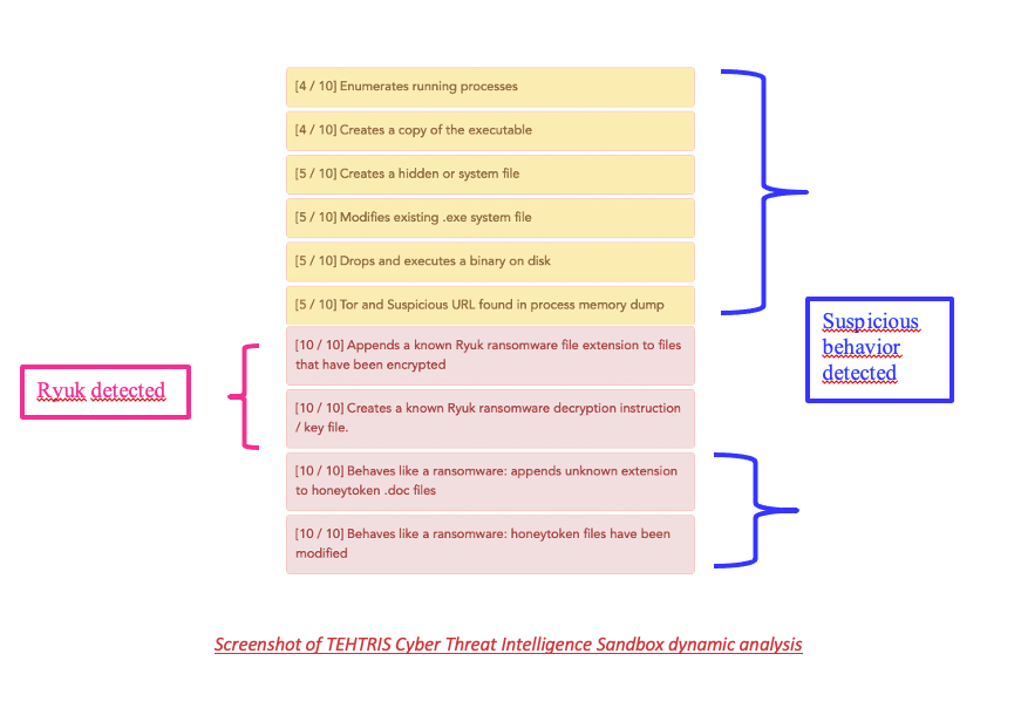
At the beginning of 2021, several French hospitals were targeted by Ryuk ransomware. However, even as the attack is being perpetrated, TEHTRIS can deploy a DFIR (Digital Forensics Incident Response) technology in merely a few hours to contain and remediate the attack.
As part of the France Relance program, TEHTRIS has experience in monitoring and protecting hospitals IT systems, and is constantly improving its detection capabilities based on artificial intelligence, on behavioral analysis of binaries and on its cyber threat database. Thanks to the Cyber Threat Intelligence (CTI) tool, which is natively and systematically integrated to all TEHTRIS tools (EDR, EPP, SIEM, etc), the suspicious programs are directly sent to a Sandbox in order to check their behavior. The CTI Sandbox tool is capable of recognizing plenty of known threats and ransomwares, such as Ryuk, but can also alert on suspicious behavior performed by unknown threats. TEHTRIS goes further than other solutions since active defense systems can be configured to respond autonomously, 24/7 to an attack – even unknow – following predetermined criteria and policies, from the lifting of the alert to the immediate and automatic neutralization, without losing time and energy – thus helping the health sector.
Why choose TEHTRIS?
Choosing TEHTRIS is the assurance of having:
- A sovereign solution that can protect employee and patient data easily deployed.
- Coverage of all endpoints to detect and neutralize ransomware in real time. 360-degree endpoint protection against the most advanced threats through hyper-automation and artificial intelligence.
- Compatibility with the ecosystem and client environment.
- Rapid deployment and support in monitoring the cybersecurity roadmap.
[1] The Cost of a Data Breach report 2020 released by IBM and the Ponemon Institute.
[2] Rapport Efficient IP et International Data Corporation (IDC). July 2021.
[3] Source Gartner. 3 first steps to deal with insecure cyber-physical systems. Katell Thielemann. November 4, 2021

