These past few days, a ransomware attack campaign has taken place, affecting thousands of VMware ESXi servers in several countries, especially in Europe. It was massively and publicly discovered during the first weekend of February.
This campaign appears to be exploiting the vulnerability CVE-2021-21974 (CVSS V3 : 8,8) for which a patch has been available since the 23rd of February 2021. OpenSLP as used in ESXi has a heap-overflow vulnerability. A malicious actor residing within the same network segment as ESXi who has access to port 427 may be able to trigger the heap-overflow issue in OpenSLP service resulting in remote code execution.
CVE-2021-21974 affects the following systems:
- ESXi versions 7.x prior to ESXi70U1c-17325551
- ESXi versions 6.7.x prior to ESXi670-202102401-SG
- ESXi versions 6.5.x prior to ESXi650-202102101-SG
The campaign is dubbed ESXiArgs ransomware as it creates a .args file for each encrypted document.
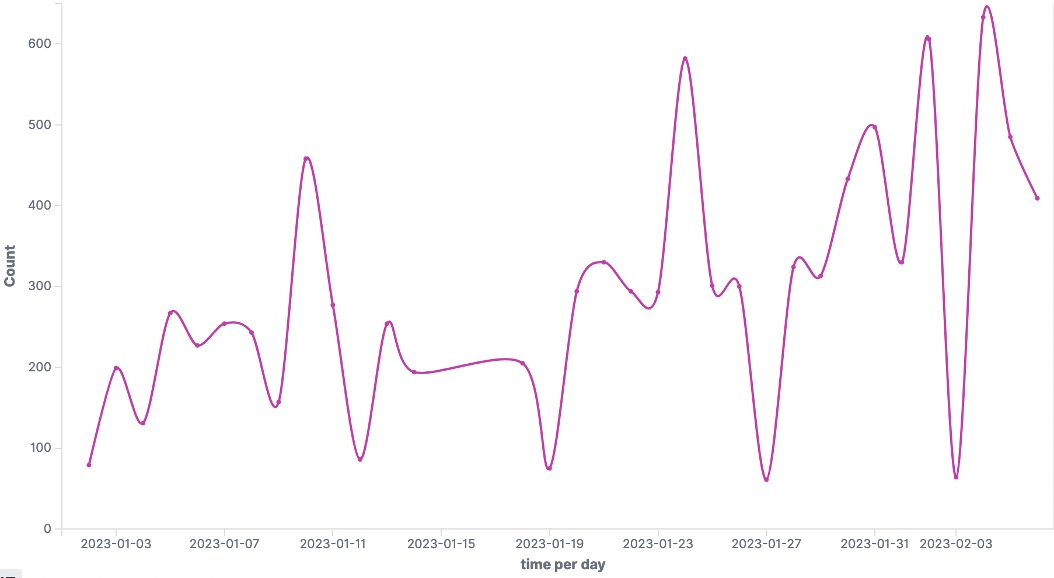
Thanks to our worldwide network of TEHTRIS honeypots equipped with our XDR Platform, we observed that the attack did not happen this weekend for the first time ever. The timeline hereunder based on our data since 1st of January 2023 shows that there were already spikes in attacks targeting port 427 on the 10th and the 24th of January before it rose up again in the beginning of February.
The top 10 most aggressive IPs for the first month of 2023 were the following. They are all flagged as malicious in public databases.
| IP | AS | Country |
| 176.58.124[.]251 | AS 63949 Akamai Technologies, Inc. | GB |
| 89.248.163[.]200 | AS 202425 IP Volume inc | NL |
| 152.89.196[.]211 | AS 57523 Chang Way Technologies Co. Limited | RU |
| 45.79.82[.]183 | AS 63949 Akamai Technologies, Inc. | US |
| 103.75.201[.]219 | AS 133496 CDN PLUS CO., LTD. | TH |
| 106.75.169[.]43 | AS 58466 CHINANET Guangdong province network | CN |
| 107.170.238[.]11 | AS 14061 DIGITALOCEAN-ASN | US |
| 162.243.136[.]10 | AS 14061 DIGITALOCEAN-ASN | US |
| 192.241.238[.]16 | AS 14061 ( DIGITALOCEAN-ASN ) | US |
| 162.243.146[.]10 | AS 14061 ( DIGITALOCEAN-ASN ) | US |
Interesting to notice, that the first 3 IPs that hit port 427 have started after the French official alert on the 3rd of February.
On the other side and before the 3rd of February, some of the malicious IPs, that we have monitored on our honeypots network, tried to keep under the radar. Indeed, it remained very discrete by making only one call, but it reached a big amount of our honeypots. This low signal performed by more discrete threat actors might be the most dangerous.
More broadly, here is the top 10 source countries where the threat targeting our honeypots on port 427 is coming from :
- US – 80%
- NL – 5%
- GB – 3%
- FR – 3%
- BG – 2%
- DK – 2%
- JP – 2%
- CN – 1%
- CA – 0,6%
- PH – 0,3%
Considering our honeypots panel worldwide, we saw most of incoming attacks by port 427 targeting the Eastern part of the USA, the Northeast part of Asia Pacific region and Western Europe practically at the same level.
To sum up, this is one of the many services that we can see being currently targeted, thanks to our honeypots network. Keeping your systems safe is a matter of having relevant information: highlighting suspicious activity is key. As we have done for the past months, we will keep informing you, via our blog, on the attacks targeting our worldwide honeypots network.
TEHTRIS recommends applying the available patch on your infrastructure and following up VMware workarounds instructions for disabling the SLP service on ESXi : https://kb.vmware.com/s/article/76372

