XDR/SIEM
Collects, archives, correlates, and alerts 24/7
Monitor your fleet continuously, qualify your decision-making and save time by automating the processing of information from your infrastructure logs.
Why choose XDR/ SIEM ?
Qualify your logs to strengthen the security of your infrastructure
Centralize the correlation of all your logs, to prioritize your alerts in real time and deal with the large volume of data coming from your systems.
XDR/ SIEM automatically scans them from our library of parsers and connectors (continuously updated) and alerts you in case of incidents. Our interactive and customizable dashboards monitor your infrastructure 24/7 from log volume indicators or active sources. Accelerate your investigations by searching and monitoring IoC and customizable retention of Hot Raw Datas.
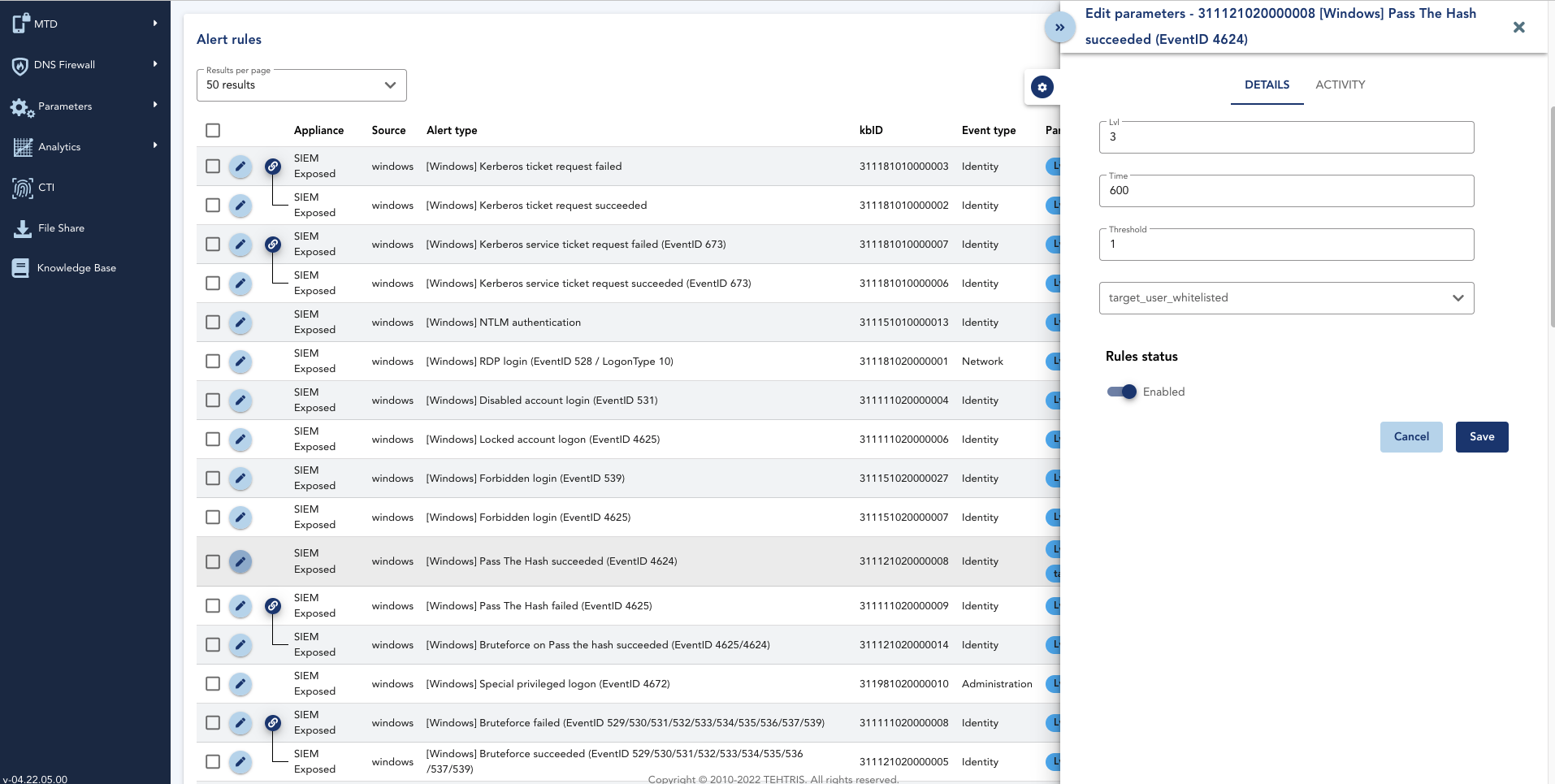
Adapt your SIEM to your business
Each infrastructure is different and has its own cybersecurity needs. Customize XDR/ SIEM to your business, formats and sources:
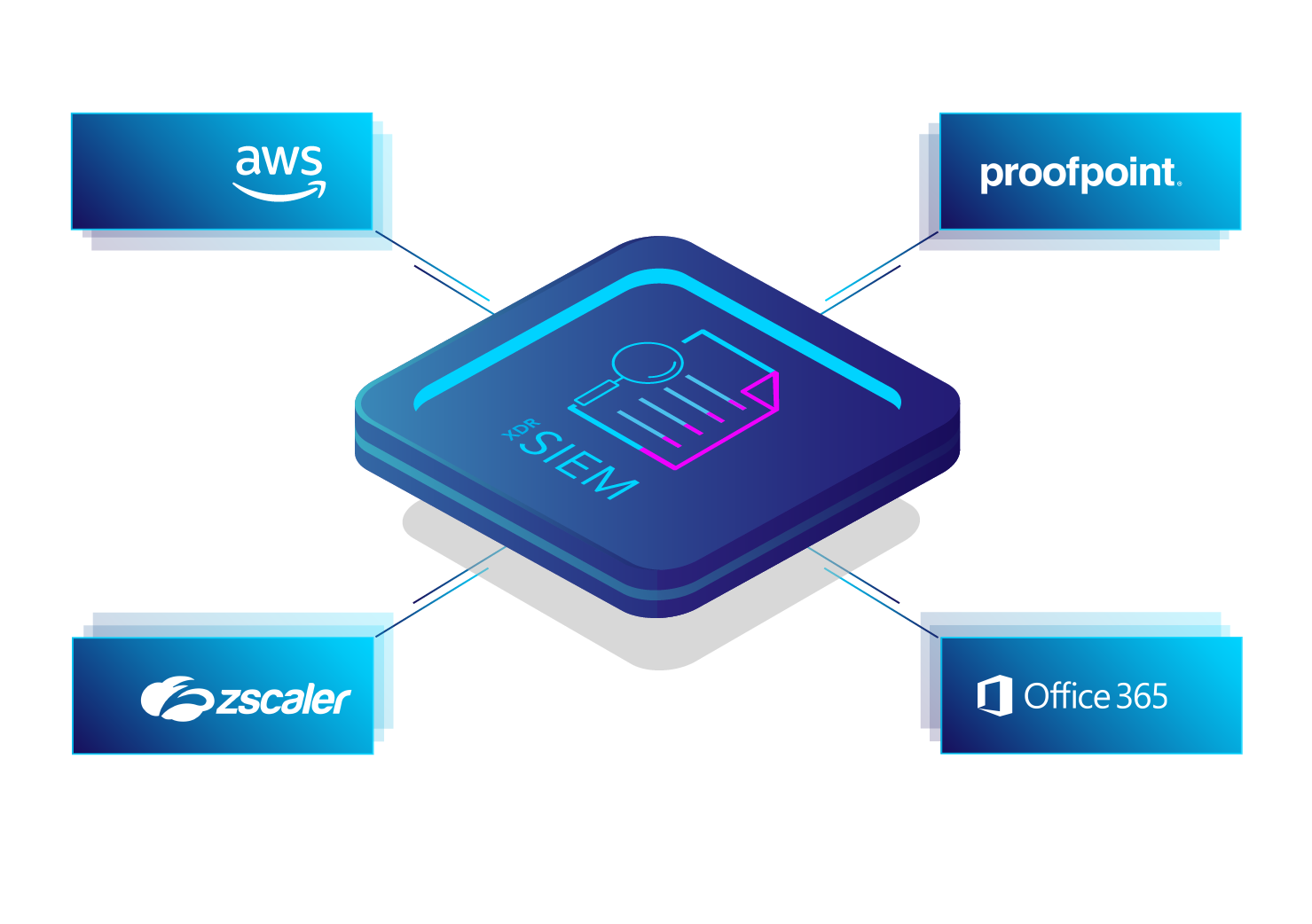
- Supported format types: Syslog, Leef, CEF, JSON, CSV, KVP, XM and others
- Supported sources: AWS, 0365, Proofpoint, Zscaler and others
- Interactive augmented dashboards
- Choose the alerting level and notification mode
- Create and manage the rules (a catalogue of thousands of correlation rules is at your disposal)
- Hot Raw Data configuration
- Blacklisting or whitelisting of IoC and customization IoC databases
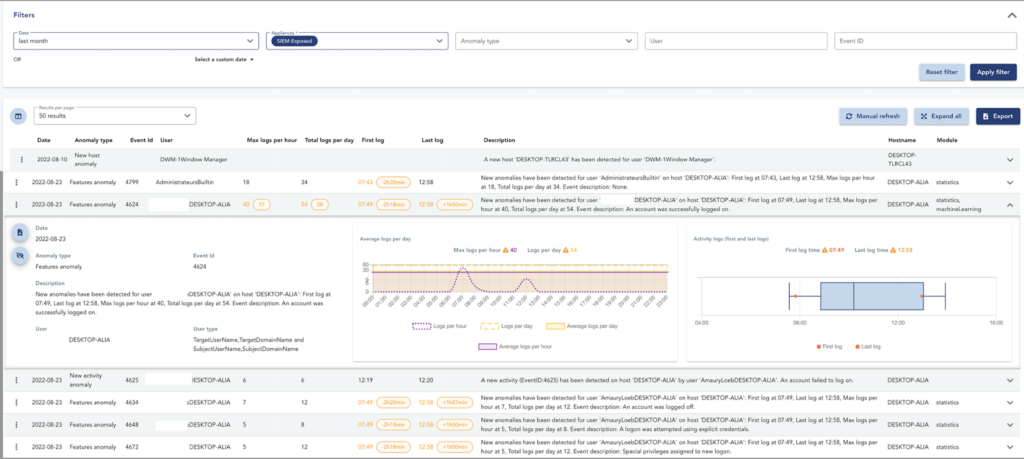
Detect unusual behavior automatically
Use the UEBA feature included in XDR/ SIEM to detect abnormal behavior in your fleet.
Based on a statistical analysis, Machine Learning and on other types of analysis on Windows logs collected by the SIEM, our UEBA compares the daily habits of users with the current activity to remove anomalies in case of suspicious activity.
Unusual actions, activity variations or abnormal user log-in times are automatically detected. All this information is uploaded to the TEHTRIS XDR Platform, where your analysts can access all the details that helped to resolve the anomaly.
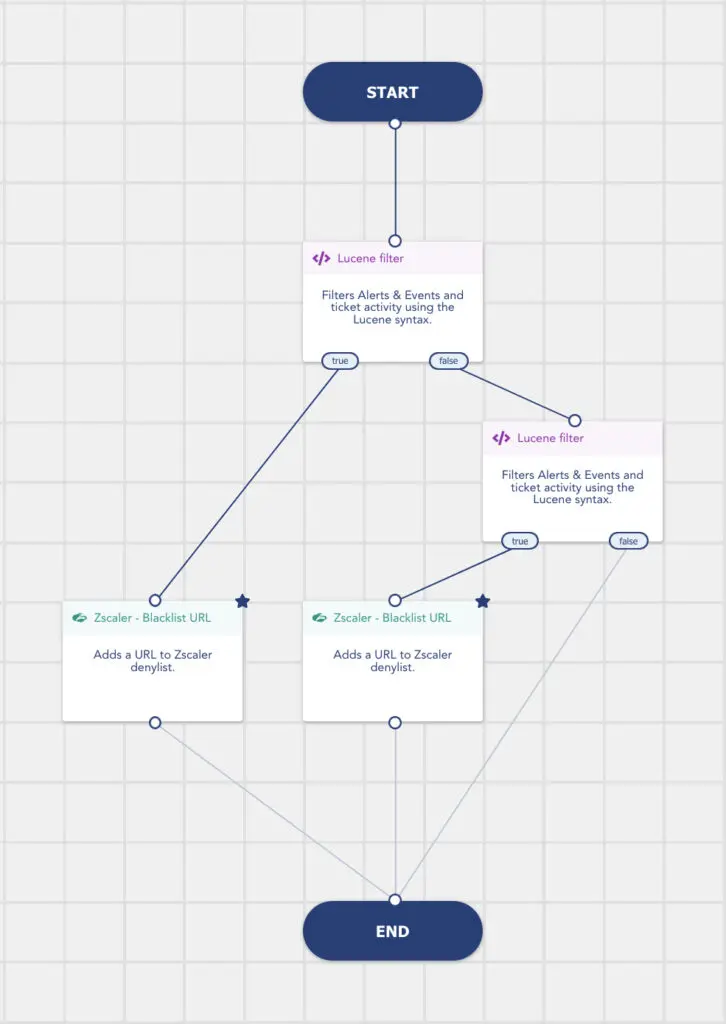
Use case: automatic processing of your SIEM data through our SOAR
Any incident detected by XDR/ SIEM is directly reported to our SOAR to hyperautomate your investigations and responses.
Leverage detections from your solutions, including from external tools such as Zscaler, with the combined action of SIEM and SOAR.
When someone connects to IP addresses or domains that are identified as suspicious by XDR/ CTI, our SIEM generates an alert and the information is send to the SOAR. In the Playbook Zscaler – Blacklist URL for example, XDR/ SOAR automatically enriches the Zscaler denylist with these new domains, based on SIEM alerts. Your teams have no additional processing tasks to do.
XDR/ SIEM is natively integrated
into the TEHTRIS XDR Platform.

The SOAR built into the TEHTRIS XDR Platform connects directly to the SIEM, simplifying the cost, maintenance and integration of these technologies. Access TEHTRIS’ hyperautomation directly from your SIEM.
Certified and recognized by
many actors of the cyber world
Leading cybersecurity authorities, analysts and associations recommend TEHTRIS solutions








MITRE ATT&CK compliance
MITRE ATT&CK is a knowledge base with a model of the behavior of a cyber attacker, reflecting the different phases of the attack life cycle according to the targeted platforms: Windows, Mac, Linux, mobile, etc.
Discover the compatibility of TEHTRIS XDR AI PLATFORM
with
< 1
day to deploy
XDR/ SIEM
6
months of log retention
100
countries where our technologies are deployed
FAQ
Is it a SIM or a SEM or a SIEM?
XDR/ SIEM combines security information management (SIM) and security event management (SEM). This is a perfect SIEM.
How do you collect the logs?
XDR/ SIEM includes an enhanced SIM sub-system, in charge of the collection of all the events from your infrastructure, the normalization of complex heterogeneous data, and the retention of your data inside a hardened storage.
How do you interpret the logs?
XDR/ SIEM comes with an advanced SEM subsystem that acts as its brain. The latter has an intelligence layer to sort out data, select what is relevant and aggregate events in order to detect very complex attacks. Thanks to its internal correlation engine, XDR/ SIEM delivers scenario-based analyses.
Can we use your SIEM to carry out forensic investigations?
XDR/ SIEM can smartly gather and keep your data for months, allowing your company to conduct Digital Forensic or Incident Response operations. Exporting your logs to a XDR/ SIEM appliance limits the risk associated with the loss of activity evidence from the system, application and infrastructure layers. In the event of an intrusion, attackers would no longer be able to erase their fingerprints from the logs, enabling you to follow the progress of the attack thanks to TEHTRIS XDR Platform. In addition, post-incident analysis of archived raw logs can simplify forensic operations against complex attacks like identity theft, internal bounces and malicious elements.
Does XDR/ SIEM come with correlation rules and can it be used from day one?
When XDR/ SIEM is delivered, it comes with more than 500 built-in rules, linked to IT environment standards. For example, you already have everything for your operating systems (Windows, Linux, etc.). XDR/ SIEM is thus closely intertwined with the TEHTRIS XDR Platform, making it a plug-and-play, intuitive and efficient tool to boost your threat hunting campaigns.
When it comes to logs and events, what can actually be collected?
XDR/ SIEM centralizes and organizes the management of all security logs: events and logs of systems, applications and network or security equipment. Once collected, archived and encrypted, these elements are analyzed through the correlation engine to detect suspicious activities and report alerts in all traditional business environments such as Windows, Unix, cloud, firewalls, proxies, etc.
Does XDR/ SIEM give you a more local or global view?
Not only does XDR/ SIEM take into account what is happening on a single machine, but it can also monitor your entire system environment, complete with its complexities and all its interactions. This allows you to keep control of your assets by getting a clear view of the inside of your network. With the XDR/ SIEM and thanks to the cyber threat intelligence provided by the TEHTRIS XDR Platform, you can also keep an eye on what’s happening outside your network and know where threats are coming from.
Can abnormal behaviors and anomalies be detected?
XDR/ SIEM can detect abnormal behaviors and trigger qualified alerts in real time to your SOC response team. It makes sense of an unlimited stream of heterogeneous event logs from various source devices, products and sensors, to present your analysts with only relevant and actionable information.
We already have a SIEM solution and we would like use TEHTRIS SIEM to upgrade our cybersurveillance, but can it be integrated into our current setup?
XDR/ SIEM can easily replace your current SIEM solution. All you have to do is share your current diagrams with us, and we will come up with several easy options to look into. To facilitate your migration, there can be a transition phase with two co-existing SIEM solutions.
