Several researchers have revealed the existence of applications available on the Google Play Store containing a malicious program from the Joker family. Joker is a malware discovered in 2019 that seeks, among other things, to steal SMS messages and make its victims subscribe to premium programs. This type of application is part of the family known as fleeceware.
According to a study conducted by ZScaler researchers, around fifty applications containing Joker have been identified on the Google Store. These applications take out paid subscriptions without the user’s knowledge. To do so, they access the phone’s SMS and phonebook to retrieve the validation code to activate the subscription.
The applications can be grouped by theme:
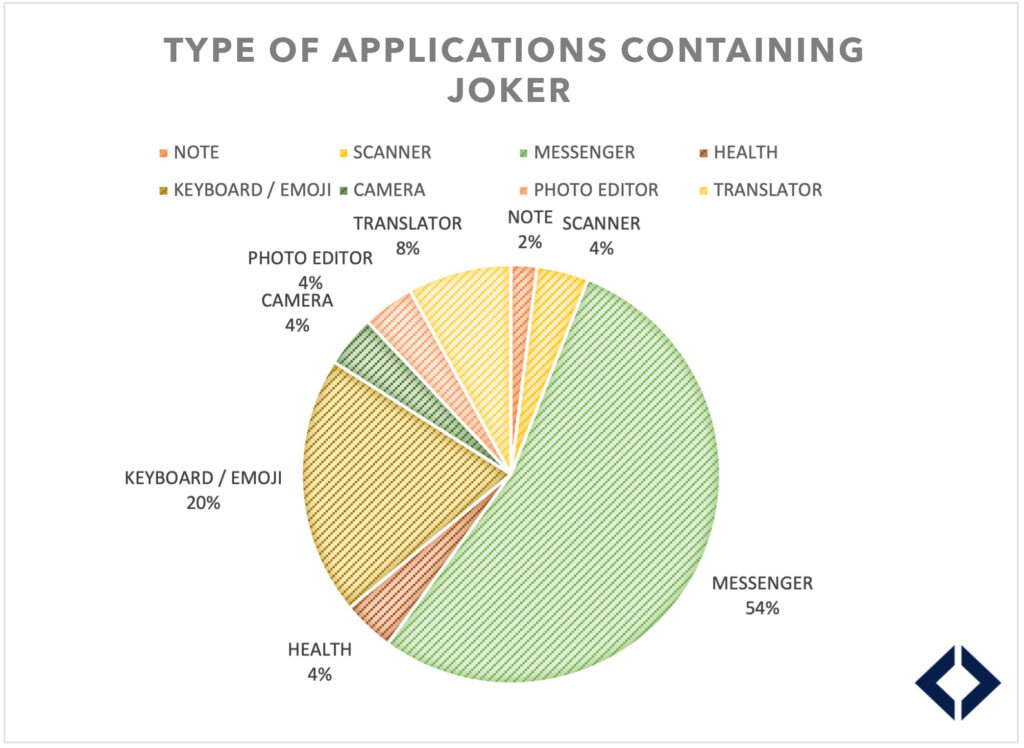
More than half are messaging applications and 1/5th are keyboard/emoji applications, consistent with the accesses that Joker needs to function (i.e. access to SMS). The user can assign high rights to the application if they use it as the default message handling application.
It should be noted that two applications are health applications, which a priori have no legitimacy to access SMS on a phone. According to good digital practice, it is recommended not to give authorisation to an application that is not necessary for its proper functioning. Using a security tool, such as the TEHTRIS MTD agent, it is possible to check the rights and permissions assigned to Android applications at any time to ensure that no abusive permissions have been given.
Also, in a tweet published on 13/07/22, an analyst identified 8 other apps available on the Google Play Store corresponding to over 3 million downloads, which included malware subscribing to paid services. According to Malwarebytes, this is indeed a variant of Joker. Google removed the applications this July 2022.
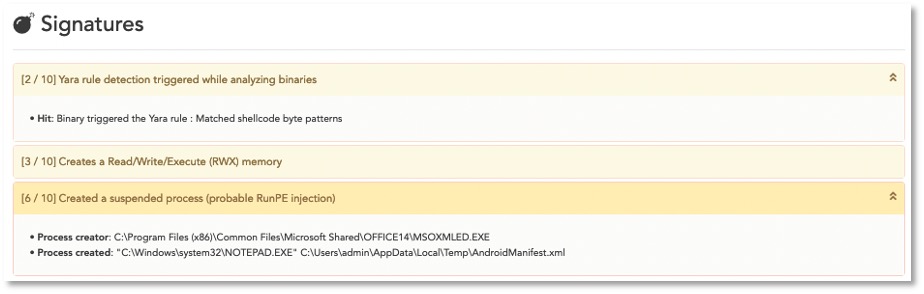
A malicious Joker application will be detected by the TEHTRIS Mobile Threat Defense (MTD) agent, which will raise alerts in the TEHTRIS XDR platform notifying of the installation of a malicious APK, as well as a DNS request to a domain name deemed dangerous. Indeed, MTD scans all applications as soon as they are installed and each time they are updated and automatically analyses them in the Cyber Threat Intelligence (CTI) database. In addition, coupled with the DNS Firewall module, it blocks requests to sites that are known to be unfavourable in the TEHTRIS database.

In addition, due to the seriousness of these security events, it is possible to alert in real time of the triggering of one of these alerts (by sending an email or an SMS directly to the supervisor, for example) via the TEHTRIS SOAR automation tool.
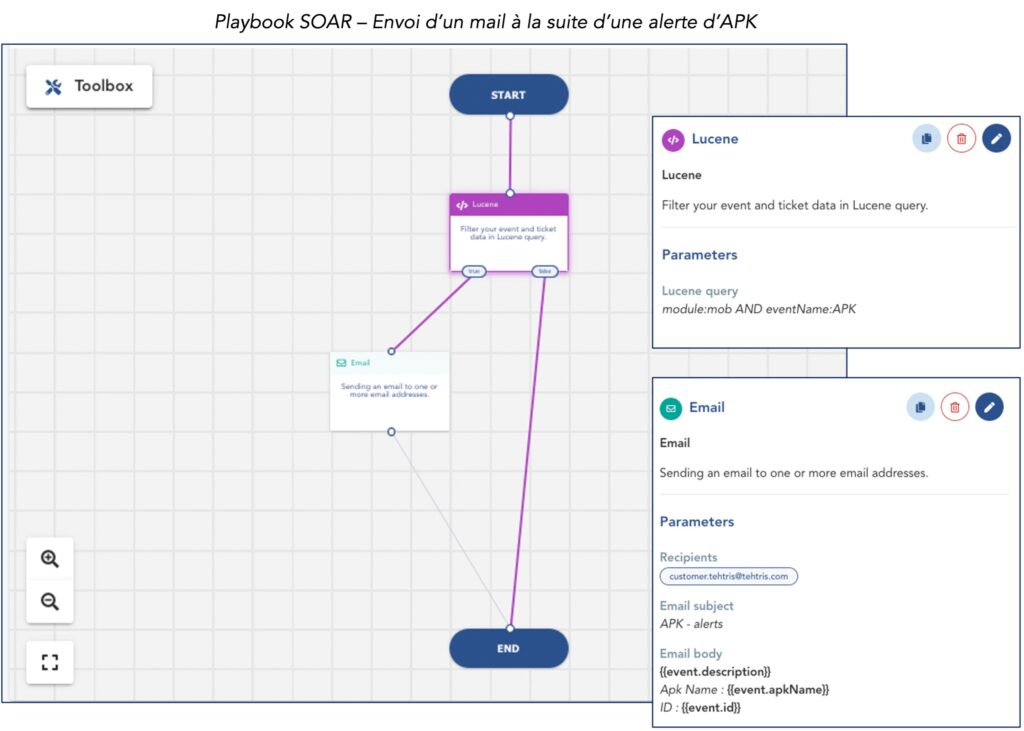
The TEHTRIS MTD module provides in-depth defence of mobile devices. In addition to being alerted to the installation of a malicious application, regular security scans can be scheduled to ensure that no device is compromised.
Adhering to digital best practices as well as using security software will help protect against fleeceware malware.
Sources:
Feed Threat Research TEHTRIS

