Lefebvre Fabien (CTI) Vincent Fournier (CTI)
WhatsApp zero-click exploits, phishing in India, and the rise of Akira ransomware: the cyber threats you need to know.
Cyber threats aren’t just an issue for security experts — they affect businesses, governments, and even everyday users. This September report highlights recent cyber threats including a malware campaign targeting India, an actively exploited WhatsApp vulnerability, and ransomware trends with a focus on Akira. Indicators of compromise and detection rules are provided to assist defenders.
CERT
CVE 2025-55177 & CVE-2025-43300
Two vulnerabilities targeting WhatsApp on iOS, iPadOS and Mac are being chained in a sophisticated 0-click attack to execute code remotely. CVE-2025-55177 is a vulnerability in the linked device synchronization feature in WhatsApp, allowing the processing of arbitrary URLs on a victim’s device. CVE-2025-43300 is a vulnerability in the implementation of Adobe’s DNG file format by Apple, allowing to execute code remotely.
WhatsApp vulnerable versions are:
- WhatsApp for iOS < v2.25.21.73
- WhatsApp Business for iOS < v2.25.21.78
- WhatsApp for Mac < v2.25.21.78
Apple’s product vulnerable versions are:
- macOS Sonoma < 14.7.8
- macOS Ventura < 13.7.8
- macOS Sequoia < 15.6.1
- iPadOS < 17.7.10
- iPadOS < 18.6.2
- iOS < 18.6.2
Sindoor
Sindoor is a phishing campaign uncovered by Nextron Systems targeting organization in India. According to Nextron Systems, the techniques used have been linked to APT36, a Pakistan based threat group targeting diplomatic, defense and research organizations in India and Afghanistan.
Sindoor is used to download MeshAgent to provide control over the system to the attacker.
Yara rules and IOCs are available on the Nextron Systems page to help with Sindoor detection.
Ransomware
Victims around the world (07/08 – 03/09)
This interactive world map highlights the distribution of ransomware victims. Hover over each country to reveal the list of known victims for these last four weeks
(Data from Ransomfeed)
Most targeted sectors (07/08 – 03/09)
This graph displays the distribution of ransomware victims by industry sector.
Legal & professional services remain the most targeted sector, but the manufacturing sector is seeing an increase in ransomware attack.
(Data from Ransomfeed)
Group ranking based on activity (07/08 – 03/09)
Qilin remains as the most active ransomware group. A slow comeback from Dragonforce – which was previously known as Ransomhub – can be noticed. A detailed report on this group is available below.
| rank | name | victims |
|---|---|---|
| 1 | qilin | 82 |
| 2 | akira | 55 |
| 3 | safepay | 36 |
| 4 | warlock | 33 |
| 5 | play | 26 |
| 6 | dragonforce | 24 |
| 7 | incransom | 23 |
| 8 | sinobi | 22 |
| 9 | cephalus | 19 |
| 10 | blacknevas | 14 |
| 10 | beast | 14 |
(Data from Ransomfeed)
Focus on Akira
Akira is a ransomware group that is behind close to a thousand attacks since april 2023.
Akira acquires initial access to companies network via dark web marketplace. Once inside, they deliver their ransomware to encrypt files and demand a ransom, ranging from 100,000$ to 10,000,000$, in exchange for a decryptor. The ransom amount is decided after analysis of gathered files to match the financial capabilities of the company.
The group targeting profile is standard, with victims mostly from the US and in legal & professional services and manufacturing sectors.
(Data from Ransomfeed)
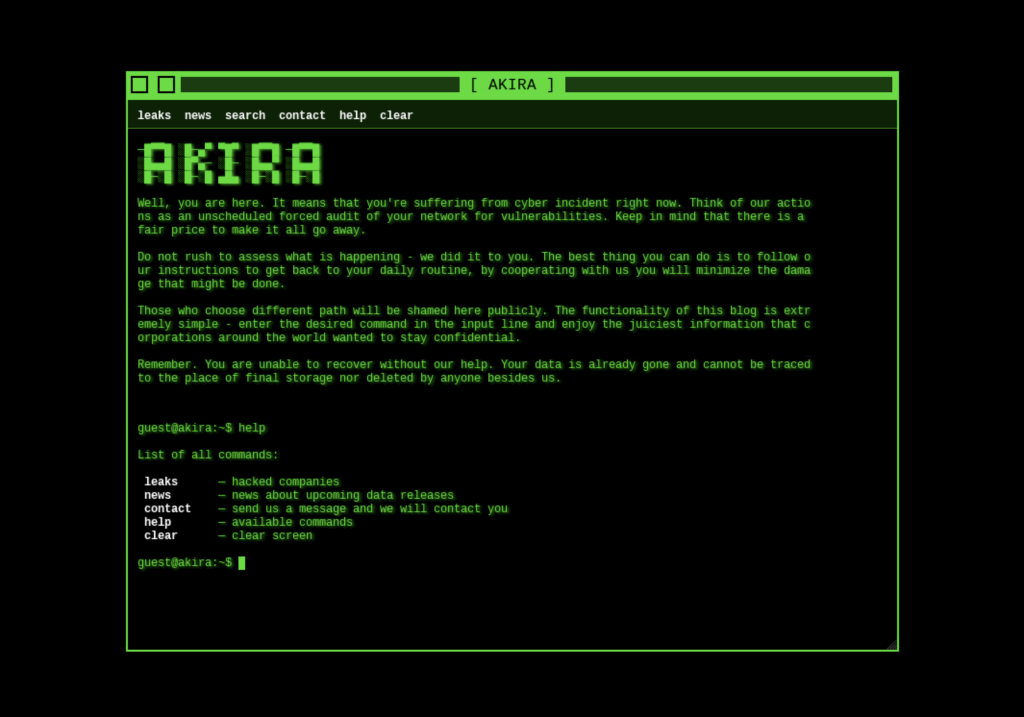
The blog features a CLI-like interface to navigate the website.
IOCs
SHA256
2b8b37175c09c75394bfbd5a2cf1eff28a4956fb3e7c6f24ea53c1b966d77153
43b0ac119ff957bb209d86ec206ea1ec3c51dd87bebf7b4a649c7e6c7f3756e7
21eace9e1cdf8c8c63e36f8f5c03da3966dee4869a3af2a8f4b1b9425261515a
ffed1a30d2cf18fe9278ab9feedcc65e7ff3e07de4208c253c854c3b3e0f4ed0
4e6d1b629282a9bc1ffde3aad6112e5842c7d757fec721ea9e0ba1efc190bf75
8a0b72f61455ac9132514b7feb4f1bb4eca7b83956b1d175529554db984e977a
86406792ba40039102772d1aa2f2d650a15cf115a75eb339035d0f8d22399e56
1ec34305e593c27bb95d538d45b6a17433e71fa1c1877ce78bf2dbda6839f218
637e28b38086ff9efd1606805ff57aaf6cdec4537378f019d6070a5efdc9c983
86b421d47957716217c6aa646402f2a85fb7b1cc2eb988e22102d5a2b2af38d4
86708db0f4c405c96b5ed10e7eb844528e0e0ec0a673d728b4ca46a3be306a52
77f13e2887ccd042e4303ed6dcc4c435097e14d2072025a9c089189850d91308
eb9cb0bc3488096f786c4081e6fe333132644593d9965d0b56c6eebfe9e18022
45bd312829efc1028cdf0777871ddd69dd4ef18b2ee2b1f08a94b71d8a667626
82e4eec824567f08778d343f156cbce57ac11d4e7a695ce26db40daafdbb90a9
86517343326a99a6c89ee5a1895b43b338214ef945de817c22a2cf37f127c4b4
a3410e5e4003361ccd1f4417ab7b36e1faed98abd248f85a21f4f74007c8ba0e
dd6ff9119440ce8f91c15946c52faf7fb62494cb5fd9b1736bd03b8f55f15118
d131cb0aa9ff7a152b506d53fbc066743e97aa7c6592b5de534f0b174fc819fc
aaa7799edfd86b52438a9e0d71f8069cbcbe1988036b95888fcdc553e729b7b9
ac7cc61ce28e9cfd9d942dbbf0459d5575164f0f858a608634e7107d56dbd0c8
4f16317dba9b983bf494892dcd227c0795f3809303e3b2787bf0a2193a318e0c
78d75669390e4177597faf9271ce3ad3a16a3652e145913dbfa9a5951972fcb0
ae455890e2123a9d011e47065828b0a03c08fd66570fab9d0340d2f5d5eb40c3
b8ed237d1cfef4f1cefaeb06219be94b8fbb8cf404369b4f3734deeccb3e1079Ransom note
Hi friends,
Whatever who you are and what your title is, if you're reading this it means the internal infrastructure of your company is fully or partially dead, all your backups - virtual, physical - everything that we managed to reach - are completely removed. Moreover, we have taken a great amount of your corporate data prior to encryption.
ATTENTION! Strictly prohibited:
- Deleting files with .arika extension;
- Replacing or renaming .arika and .akira files;
- Using third party software to recover your systems.
If you violate these rules, we cannot guarantee a successful recovery.
Well, for now let's keep all the tears and resentment to ourselves and try to build a constructive dialogue. We're fully aware of what damage we caused by locking your internal sources. At the moment, you have to know:
1. Dealing with us you will save A LOT due to we are not interested in ruining you financially. We will study in depth your finance, bank & income statements, your savings, investments etc. and present our reasonable demand to you. If you have an active cyber insurance, let us know and we will guide you how to properly use it. Also, dragging out the negotiation process will lead to failing of the deal.
2. Paying us you save your TIME, MONEY, EFFORTS and be back on track within 24 hours approximately. Our decryptor works properly on any files or systems, so you will be able to check it by requesting a test decryption service from the beginning of our conversation. If you decide to recover on your own, keep in mind that you can permanently lose access to some files or accidentally corrupt them - in this case we won't be able to help.
3. The security report or the exclusive first-hand information that you will receive upon reaching an agreement is of great value, since NO full audit of your network will show you the vulnerabilities that we've managed to detect and use in order to get into, identify backup solutions and download your data.
4. As for your data, if we fail to agree, we will try to sell personal information/trade secrets/databases/source codes - generally speaking, everything that has a value on the darkmarket - to multiple threat actors at once. Then all of this will be published in our blog - akiral2iz6a7qgd3ayp3l6yub7xx2uep76idk3u2kollpj5z3z636bad[.]onion.
5. We're more than negotiable and will definitely find a way to settle this quickly and reach an agreement which will satisfy both of us.
If you're indeed interested in our assistance and the services we provide you can reach out to us following simple instructions:
1. Install TOR Browser to get access to our chat room - torproject[.]org/download/.
2. Paste this link - <CENSORED>.
3. Use this code - <CENSORED> - to log into our chat.
Keep in mind that the faster you will get in touch, the less damage we cause.Ransom file
akira_readme.txtEncrypted file extension
.arikaDetection rules
YARA
import "pe"
rule Akira: ransomware akira {
meta:
author = "TEHTRIS - Lefebvre Fabien"
description = "Detects Akira ransomware"
sha256 = "['def3fe8d07d5370ac6e105b1a7872c77e193b4b39a6e1cc9cfc815a36e909904']"
strings:
$ = ".akira" ascii fullword
$ = ".arika" ascii fullword
$ = "akira_readme.txt" ascii fullword
condition:
pe.is_pe and any of them
}
