To know the threat for better adjusting defense: that is the wish of every cybersecurity analyst! Cyber Threat Intelligence (CTI) is considered to be the supreme discipline that aggregates, correlates and analyzes all data on cyber threats, from several sources, from a technical, tactical and operational point of view.
At TEHTRIS, CTI is both a knowledge database and a file analysis tool with artificial intelligence along with static and dynamic analysis capabilities. This tool allows to understand, anticipate and respond to the threats, while facilitating decision making.
Therefore, the CTI is:
– the memory, which can be used to determine whether a binary is already known and whether it is considered malicious,
– the brain, which observes the behavior of an unknown executable file and decides on its danger threshold.
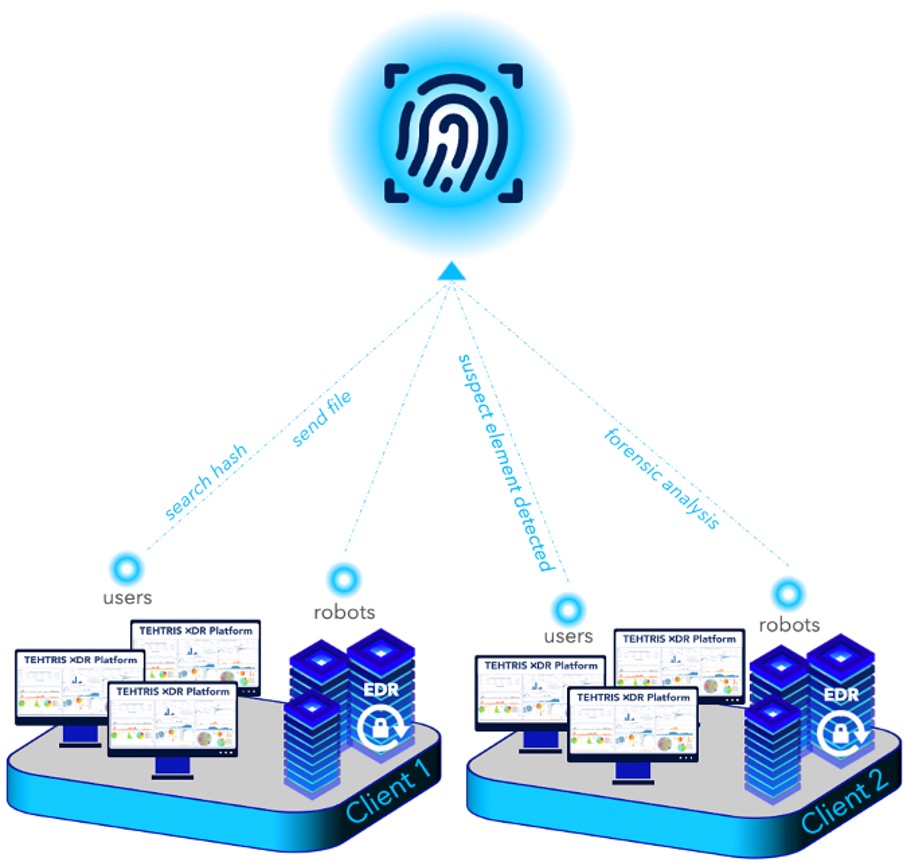
The TEHTRIS CTI tool is natively integrated into the XDR platform and is beneficial to all TEHTRIS technologies (EDR/EPP, MTD, SIEM…). Thus, cybersecurity analysts using our products save time in implementing defensive actions to protect their IT assets by relying on useful information collected and analyzed by TEHTRIS experts and artificial intelligence. This cyber intelligence is automatically updated in the cloud and benefits in real time the experts using TEHTRIS protection software.
How does CTI work at TEHTRIS? How is it used by our cybersecurity experts, whether they are SOC analysts, CISO or threat hunters?
A complementary functioning: between collection and analysis
The CTI allows to obtain information on the qualification of a file and its dangerousness from its fingerprint in SHA256, MD5 and SHA1 format. The CyberIA artificial intelligence module, whose algorithms are based on a deep neural network entirely developed by TEHTRIS, works for the benefit of the CTI. This AI is able to detect all known and unknown malicious binaries with a very fine level of analysis, accurate, fast and efficient.

A constantly enriched database
Each day, more than 2 million entries are analyzed by the TEHTRIS CTI! Our tool is constantly evolving as the database is enriched in two ways.
On the one hand, each binary executed on a machine in a TEHTRIS-protected fleet is sent to CTI to be qualified for its threat score. If the binary is unknown, a static analysis and a dynamic analysis will be launched to understand how it works and determine if its behavior is threatening. The CTI is therefore automatically enriched by the binaries sent by TEHTRIS bots as part of their automatic detection missions. This way, according to Sandbox scores, cyber analysts are able to prioritize alerts to treat on their XDR and save time.
TEHTRIS is contributor of VirusTotal since 2017 making our solution the only French CTI of the platform among 60 other qualified and selected companies in the world.
On the other hand, our cyber threat experts collect data from other sources to feed the database. Our teams improve the general knowledge of the cyber threat through the monitoring of the cyber news, the investigations carried out on the detected threats, the exchanges with our partners…

As an example, TEHTRIS is the only French cybersecurity company member of the Cyber Threat Alliance (CTA). This is a nonprofit organization that strives to improve the cybersecurity of our global digital ecosystem by enabling the sharing of high-quality in real time cyber threat information among businesses and organizations in the cybersecurity field. This collaboration leads to daily exchanges of cyber threat intelligence with other cyber security leaders from around the world with the common goal of protecting the global digital environment.
In addition to hosting intelligence, TEHTRIS CTI also provides static and dynamic binary analysis capability through TEHTRIS Antivirus and Sandboxes.
Static analysis: proven effectiveness for anyone
The TEHTRIS CTI hosts a static analysis farm, composed of antivirus software, but also of tools developed by TEHTRIS. Each of them will give an assessment on the dangerousness of the analyzed binary based on signature studies. A conclusion is rendered by the CTI, resulting in an Antivirus score and displaying several information of interest if the binary has a bad reputation. Depending on the Antivirus score, an alert can be configured to go directly to the XDR platform.
This static analysis is coupled with a dynamic analysis performed in real time if the binary is unknown.
Dynamic analysis (Sandbox): an indispensable cybersecurity tool
The TEHTRIS CTI Sandbox tool allows you to run a binary in a controlled environment to study its behavior in real time. The results are received almost immediately. The binary will first be studied in detail in order to retrieve general information such as its name, logo, type, size and especially the possible signature of the strain editor. The Sandbox analysis report also contains screenshots in order to display the possible commands performed by the analyzed binary.
A technique classification insert from the MITRE ATT&CK matrix (a benchmark in the cyber community) is displayed in the Dynamic Sandbox Analysis reports to provide new contextualization on binary behavior. This provides cyber analysts using TEHTRIS tools with a more comprehensive and efficient computer file analysis capability.
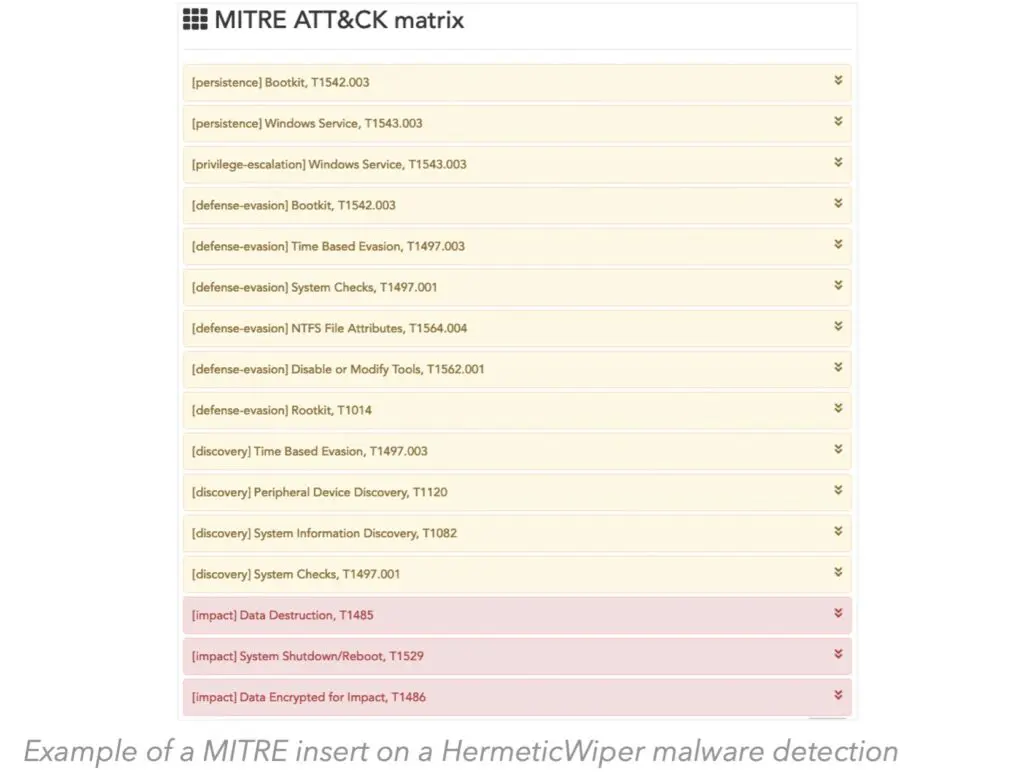
The dynamic analysis offers several studies of the binary’s activity in relation to the existing files on the machine. The objective is to understand what the binary has done: which file it has opened and read, which file it has deleted, which file it has created or modified. The network activity of the binary is also observed according to the TCP, UDP or ICMP connections it requested. Finally, the behaviors of the binary concerning the accessed and consulted registers, the launched processes and the contacted Windows APIs are also studied.

Searching for cyber threats: manual use of the TEHTRIS CTI tool

Cybersecurity analysts using TEHTRIS tools, can consult the database and manually send their binaries or hashes of scripts to query the CTI tool. This allows them to:
- Search for analyses already performed by the tool;
- Download a binary in the TEHTRIS CTI and analyze it by Antivirus and static analysis tools;

In addition, the TEHTRIS CTI tool provides an automated collection and analysis agent, the TEHTRIS Offline Forensic (TOF), which performs live forensic analysis, which consists of performing tests on a computer to determine its health. It consists of downloading a file and running it on the machine to be analyzed, then sending the results to the CTI tool. TOF is very useful when investigating a machine after an incident has occurred to find out what happened and what the consequences were.
These tools enable cybersecurity analysts to detect a threat because they are a valuable source of information in the initial investigation phase of a security incident.
Thanks to these technologies, TEHTRIS experts have, for example, contributed to the analysis of the Raspberry Robin malware, initiated by Red Canary, in order to better protect you by sharing knowledge of this threat with other experts in the cyber world. First detected by artificial intelligence, analysts were able to deepen the study by relying on the dynamic analysis of the CTI tool. Indeed, the Sandbox execution of this malicious binary revealed the following activities:
- number of IP addresses contacted,
- number of files created, accessed and read
- number of Windows APIs contacted
Our experts then proceeded to reverse engineer this script in order to study in depth this malware that spreads like a worm and that seems to occur following the insertion of an infected USB key containing a .lnk file.
To go further and get the IoCs: analysis of Raspberry Robin
The TEHTRIS CTI is a toolbox for investigating any type of cybersecurity incident that occurs on your IT estate. This tool provides you with a broad threat view that constantly updates to establish persistant and relevant cybersecurity. The TEHTRIS CTI tool feeds automatically detections and remediations of TEHTRIS XDR platform solutions, as well as feeding detailed forensic investigations in the event of an Incident Response (DFIR). From the Cloud to Endpoints, as well as your OT, TEHTRIS technologies neutralize ransomware and 0-days attacks in real time.

