A good understanding of active threats is necessary to achieve a good security posture. The following report provides actual trends that emerge from the Internet Background Noise. The data are provided using two weeks of our worldwide honeypots’ logs.
SSH connection attempts: focus on 2 French IP addresses
These past two weeks, 10% of the SSH connection attempts on our European honeypots originated from just 2 French IP addresses :
The first one is 54.36.126[.]205, testing over 23,000 credentials in just 4 hours in the mornings of the 30th and 31st of March. The table below shows the top 10 credentials that were used:
| Login | Password |
| developer | mar20lt |
| nagios | 555555 |
| test | 333333 |
| wso2 | 123qwe |
| plex | abcd1234 |
| webdev | 54321 |
| mattermost | usr |
| matrix | 1qaz@WSX |
| start | start |
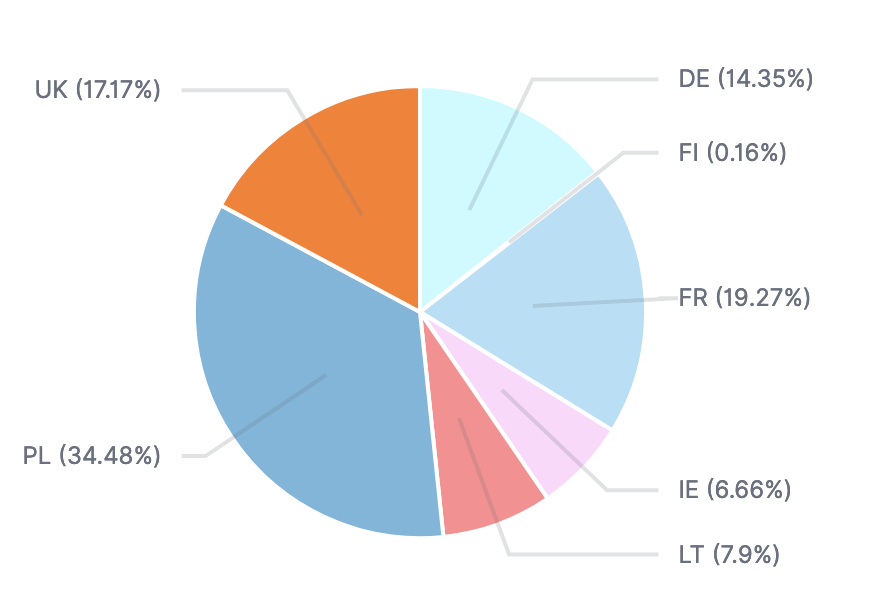
The targeted countries are distributed as follows:
The second IP address is 51.91.136[.]234, which – following the same pattern – tested over 13,000 credentials in a few hours on the Monday of March 30th. The table below shows the top 10 credentials that were used:
| Login | Password |
| steam | 0 |
| centos | 123456789 |
| deployer | 123456 |
| remote2 | remote2 |
| root2 | root2 |
| user1 | user1 |
| oracle | 1111 |
| oracle | 111111 |
| oracle | 123 |
| oracle | 123123 |
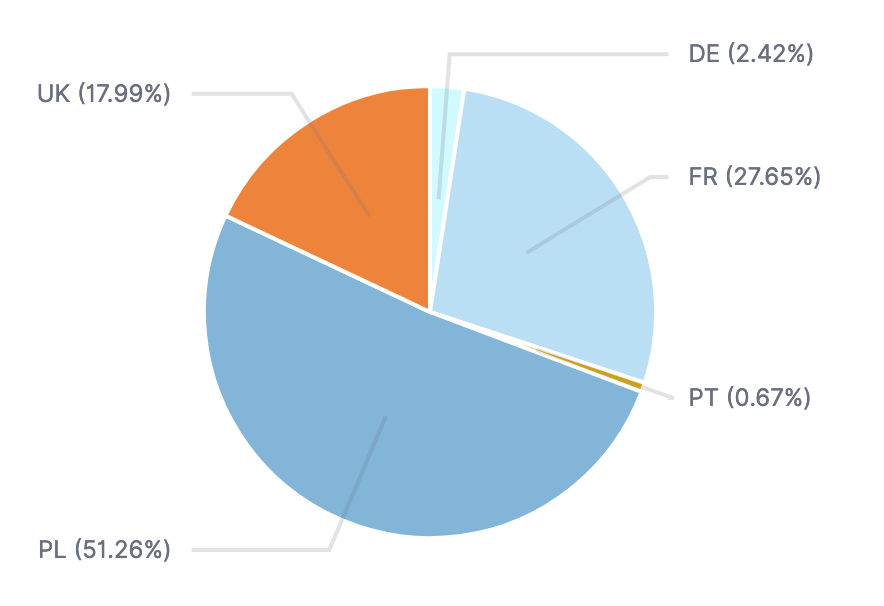
The targeted honeypots are distributed as follows:
AndroxGh0st scanning for Laravel debug mode information
AndroxGh0st is a python script available in open sources which is used to scan for and parse Laravel applications to find exposed .env files, revealing configuration data including and private keys. Laravel is an open-source platform used to create web application. When the Debug mode is enabled, it can disclose sensitive information such as database, passwords, application keys… This information is of interest for threat actors to pursue further attacks.
AndroxGh0st was discovered by the cybersecurity community at the end of 2022 and has been mentioned recently because it is included in a new toolset called AlienFox sold on Telegram channels. AlienFox is used to harvest API keys and secrets from popular services including AWS SES.
Packets containing “androxgh0st” have been increasingly detected on our honeypots over the course of March, almost doubling the amount over the course of the month.
4 IP addresses amount for almost 80% of the total requests:
| Ip address | Country | AS |
| 135.125.246[.]110 135.125.217[.]54 135.125.244[.]48 135.125.246[.]189 | FR | AS 16276 (OVH SAS) |
Most used usernames over SMB protocol
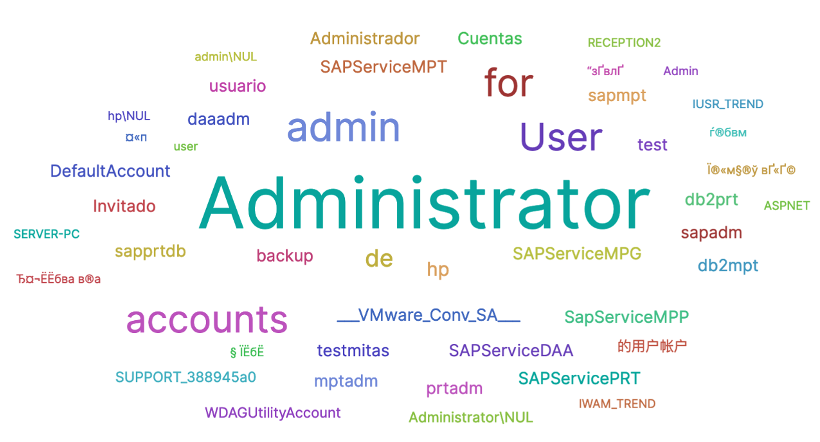
Over 2 million SMB connection attempts were registered over the past couple of weeks on our honeypots. The usernames most used by threat actors are the following:
Turkish IP address 88.255.215[.]2 (AS 9121 – Turk Telekom) that we mentioned in our February bi-monthly is still extremely active since its relentless requests amount for almost 50% of the total events.

