A complete overview of mobile fleet protection
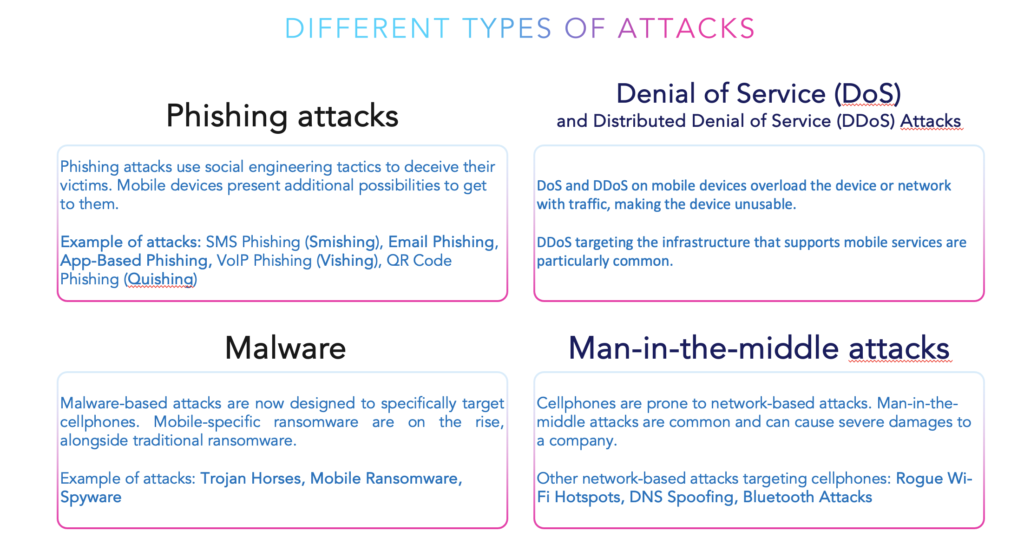
Smishing, man-in-the-middle, jailbreaking/rooting… All these attacks are on the rise and are directly linked to your phones. While companies heavily invest in cybersecurity solutions to protect their IT assets, the security of their mobile fleet often comes in second place or may even be completely overlooked in some cases. Yet smartphones have a lot of security gaps that can easily be exploited by threat actors to gain a direct access to a company.
Man-in-the-middle attacks, for example, can use the lack of security in networks to intercept the communication between a mobile device and a server. This lack of security can simply come from an employee connecting his work cellphone to a public, unsecured, Wi-Fi for a few minutes while waiting for a train. With this connection, a man-in-the-middle attack can happen in seconds or minutes and lead to severe data breaches and financial loss for the company.
An individual with a smartphone might get away with built-in security features, as his data might not be considered as valuable by threats actors (yet, this is very debatable, as ransomware were the biggest threat of 2023). But, as we will see in this article, basic security options available on cellphones or through traditional antiviruses aren’t nearly enough to protect the sensitive data of your company.
To secure your mobile fleet, your company needs to invest in a dedicated security solution. We will give you an overview of these solutions at the end of the article, in order for you to guarantee the cybersecurity of your mobile devices.
Insufficient protection tools
Cellphones keep being forgotten in cybersecurity. A private person will install an antivirus on their personal computer yet installing a similar protection on their smartphone isn’t commonly done.
To face this lack in cybersecurity, cellphones have built-in security features that provide basic protection to all phones. On the other hand, some companies use their traditional antivirus in an attempt to protect their mobile fleet. As we will see, these options both have their limits.
A. The limits of built-in security features
The built-in security features of Android and iOS differ, as their level of protection might not be the same. Yet, globally, it is accepted that these security measures are enough. Be it out of convenience or lack of awareness, people tend to trust the built-in security features of their smartphones.
So, why isn’t it enough?
- Centralized management and compliance
For a company, the lack of centralized management of their entire fleet with built-in security features is a crucial problem, that will quickly be clear for every IT professional. Ensuring compliance without a centralized management will be nearly impossible. Administrators also won’t have the option to quickly make sure that devices are correctly configured or up-to-date, and apps controlled. And to comply with regulations like the GDPR, companies need to enforce specific security measures across all devices, which centralized management will make possible.
- No threat detection and responses in real-time
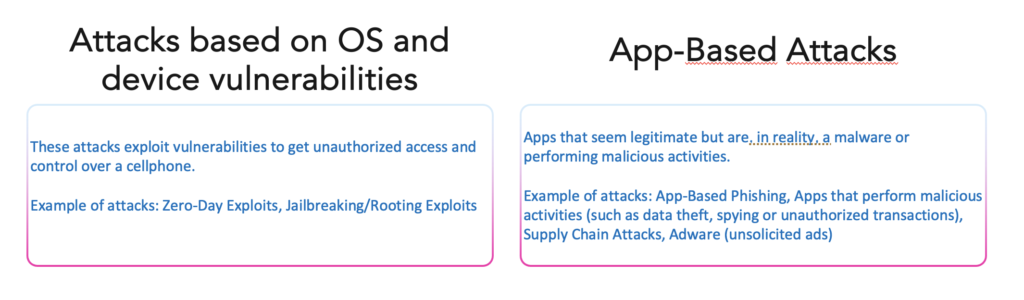
As we have seen in this article, a lot of attacks are created to target smartphones. These threats are becoming more and more sophisticated and are developed to bypass built-in security features. Some phishing attacks, zero-day exploits or malware (amongst others) will even be programmed to exploit the vulnerabilities of built-in security features.
To face the lack of protection provided by smartphones, your company needs to rely on security tools that can detect threats and respond to them in real-time. Built-in security features usually rely on signature-based detection or rules that have been defined in advance and won’t be able to respond to attacks that aren’t known to them. They also don’t have the ability to detect unusual behavior. This can result in big losses for companies in case of fast-paced attacks like ransomware, for example.
- Lack of network security
Network security is one of the crucial points when it comes to protecting your smartphones. While on-the-go, users are very likely to connect to new networks, or even unsecured (public) Wi-Fi. Having a tool that controls the networks the smartphones are connected to is essential, and built-in features won’t protect you against threats linked to networks.
B. The limits of traditional antiviruses
Some companies still rely on their traditional antivirus to protect their mobile fleet. There can be many reasons to this: the remaining misconception that smartphones are “smaller computers”, a fear of higher costs, relying on a legacy security structure… If this is your case, we highly recommend you reconsider your perspective, in order for you to ensure the security of your fleet, and, by extension, of your company.
So, why isn’t it enough?
- Attacks that are specific to mobile devices
As we have previously seen, threat actors are continuously developing attacks that are specifically targeting the vulnerabilities of cellphones. There are numerous attacks that traditional antiviruses won’t be able to detect and neutralize. For example, phishing and smishing attacks easily bypass traditional antiviruses nowadays by focusing on social engineering.
- Lack of centralized management, threat detection and responses
Traditional antiviruses rely on signature-based detection. A signature-based detection will identify threats only if they match the threats that are currently available in a database of known malware signatures. Threats are constantly evolving, and your antivirus needs to be capable of recognizing the newest, or even unknown, threats. In addition to that, attacks on smartphones very often exploit vulnerabilities through non-malware threats, which won’t be covered by a traditional, signature-based, antivirus. Behavioral analysis and network security will also be lacking in your fleet’s security. Yet they are easy opportunities for threat actors to get to your company.
In case of theft or loss of a phone of your fleet, a traditional antivirus won’t allow you to remotely lock or wipe the phone. And, unless your antivirus provides you with a way to manage all your mobile fleet at once, compliance won’t be enforced, and basic security policies will be hard to supervise.
- Cybersecurity solutions to protect your mobile fleet
Cybersecurity solutions that can give a full coverage of your mobile fleet exist. These solutions will be able to provide you with protection against mobile-specific attacks, which traditional and built-in features will have trouble doing.
If you are on the search for a cybersecurity solution to protect your mobile fleet, it can be difficult to distinguish between all the available tools. MDM, MTD, EMM, IAM, MAM… To keep up with the ever-rising threats, a lot of options have flooded the market, making it hard to get a clear image of which ones will actually provide the best protection of your mobile fleet. We selected the go-to cellphone cybersecurity solutions for you to get an overview.
MDM
MDMs are used to centralize the management of all the phones of a company’s mobile fleet. Having a centralized management of all mobile devices will give IT administrators the option to enforce all security policies on all phones. Usual security policies enforced with MDMs are password requirements, security configurations, control of installed apps…
Unfortunately, MDMs alone might not be enough to secure your mobile fleet anymore. They do provide the basic security necessary to protect your mobile fleet but will lack in detection and responses to threats.
MTD
MTD are focused on protecting your fleet against mobile-specific threats. Phishing, malware, network attacks… they won’t only help you to enforce security policies on your entire fleet but will also protect you against the ever-growing cyberattacks against phones.
MTDs are a direct response to the rise of new cyberthreats against mobile fleets. They provide proactive threat detection and responses, similar to what you would use to secure your premises against cyberattacks.
VPN
As mentioned above in this article, a common cyberthreat for phones is the use of public or unsecured Wi-Fi accesses. While getting around, your teams might connect to new Wi-Fi networks.
VPNs will provide you with secure access to new networks by encrypting the communications of your fleet and thus protect the data of your company.
EMM
EMM offer similar options as MDMs but go further than them in the protection of your phones.
While still being restricted to centralized management and security policies enforcement, they provide more than the basic security of MDMs: application management, content management and identity management, amongst others, will provide you with advanced cybersecurity option for your mobile fleet.


