Protect your mobile devices from Jailbreak attacks
Jailbreak – What is it?
Jailbreaking removes Apple’s security restrictions, allowing more freedom in app and tool usage but exposing the device to malware. It grants all apps access to sensitive data and the iOS file system.
An attacker can jailbreak a phone either by connecting it to a computer or remotely via malicious apps, websites, or messages. This can enable data theft – via SSH protocole – such as location tracking, and surveillance through the device’s camera, microphone, and messages—turning the phone into a valuable source of information.
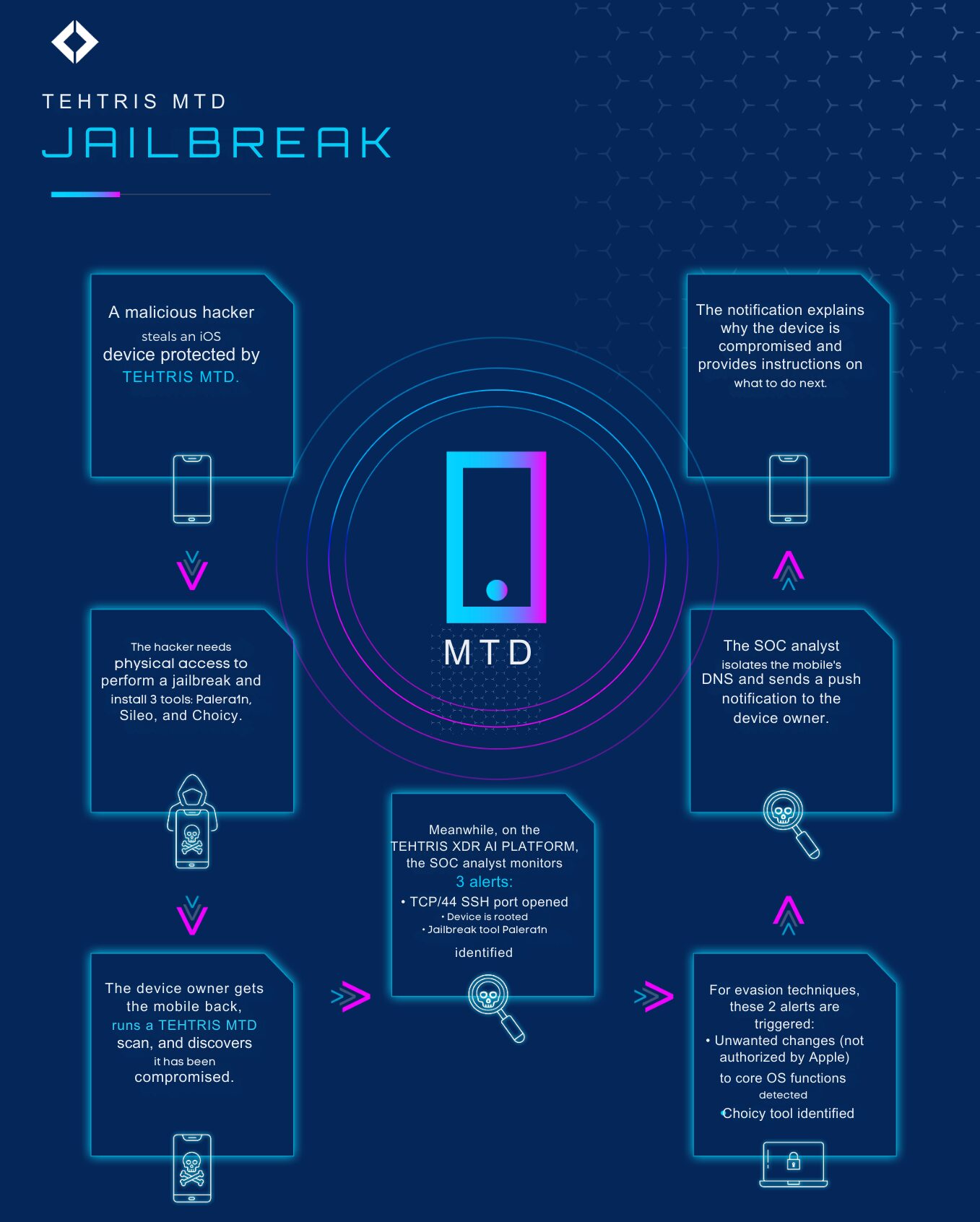
The user briefly loses sight of their iPhone, during which the attacker steals it to jailbreak it before returning it. After memorizing the unlock code, the attacker connects the phone to a computer, performs a jailbreak with Palera1n, and installs Sileo to download Choicy, a tool that conceals the jailbreak. Though the phone is returned, a quick scan by TEHTRIS MTD detects the compromise, alerting the user.
About the attack
This use case explores widely used jailbreak tools that are easily accessible and simple to operate, but require the attacker to connect the iPhone to a computer.
Jailbreak tool: Palera1n
(https://palera.in/)
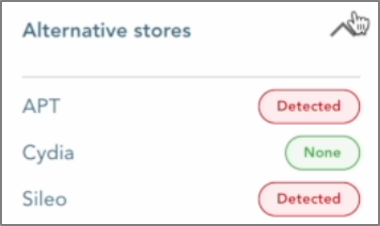
Store alternatif: Sileo
(https://getsileo.app/)
Tweak: Choicy
REAL-TIME ALERTS ON TEHTRIS XDR AI PLATFORM – MTD
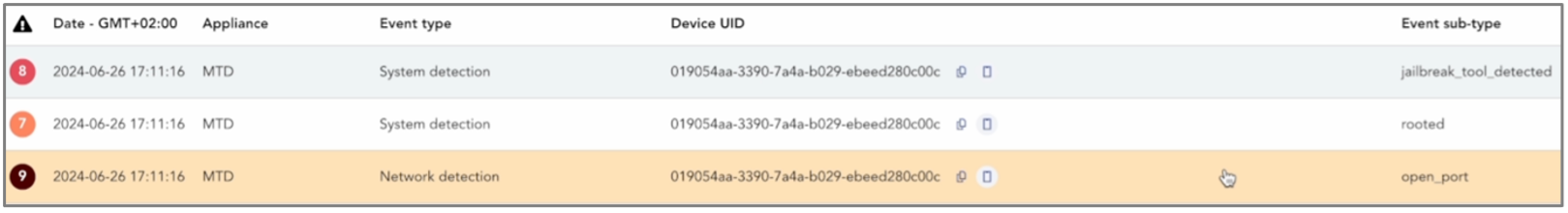
Console, MTD Alerts & Events Tab
While the attack unfolds between the attacker and the phone owner, the SOC analyst monitoring the organization’s iPhone fleet with TEHTRIS MTD will notice new alerts appearing in the “Alerts & Events” tab on the console.
First, the jailbreak triggered the following alert:
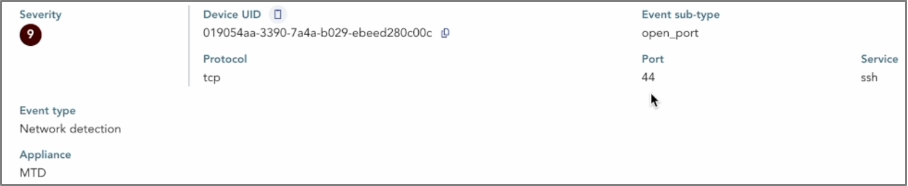
SSH port TCP/44 was opened.
In this case, Palera1n opened a port with an SSH server for debugging purposes, useful for jailbreak developers.
However, it only allows SSH connections via USB cable, not over the network.
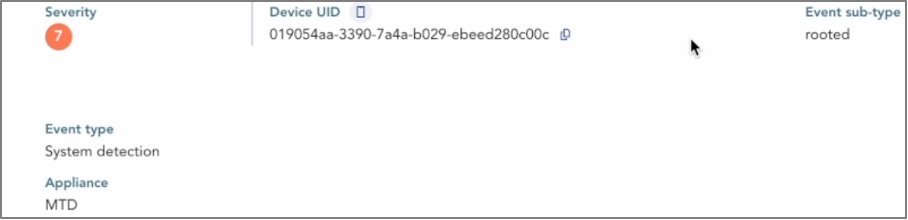
The phone is detected as jailbroken (or “rooted”).
As a reminder, this implies that any application has
user admin rights on the phone.
The Palera1n jailbreak tool has been identified..
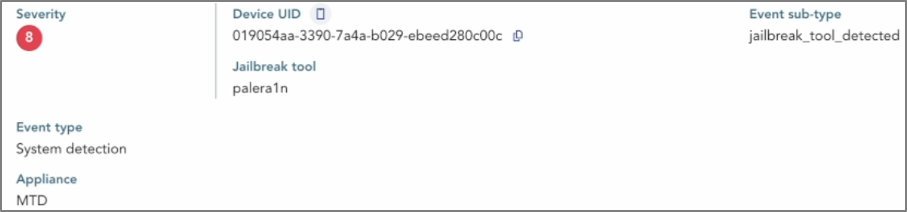
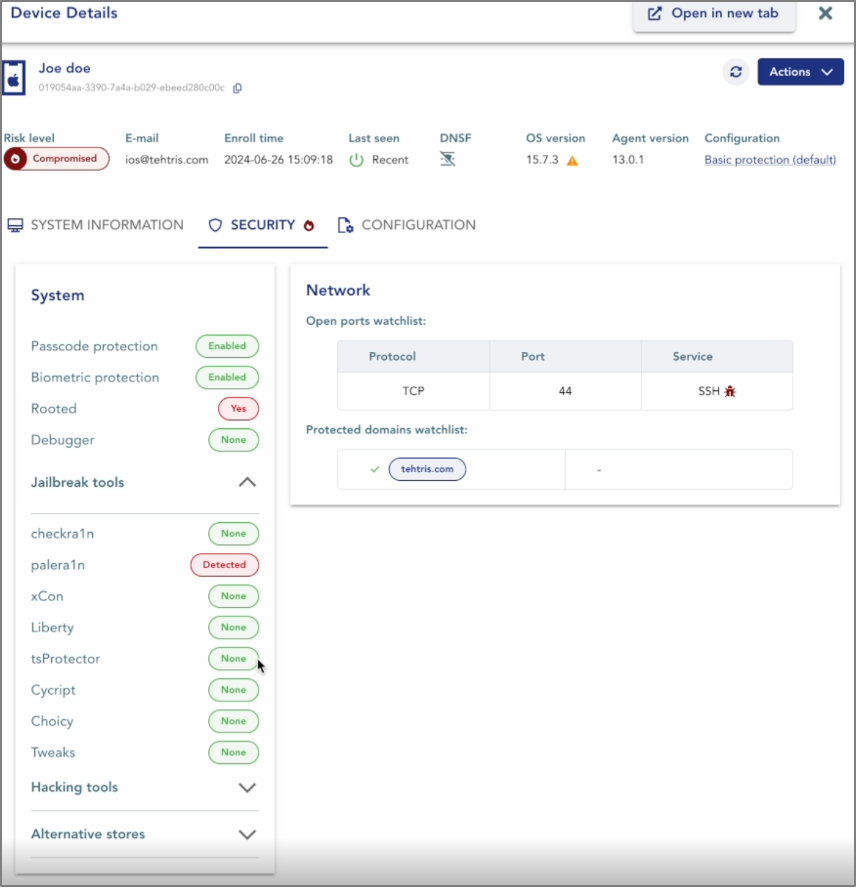
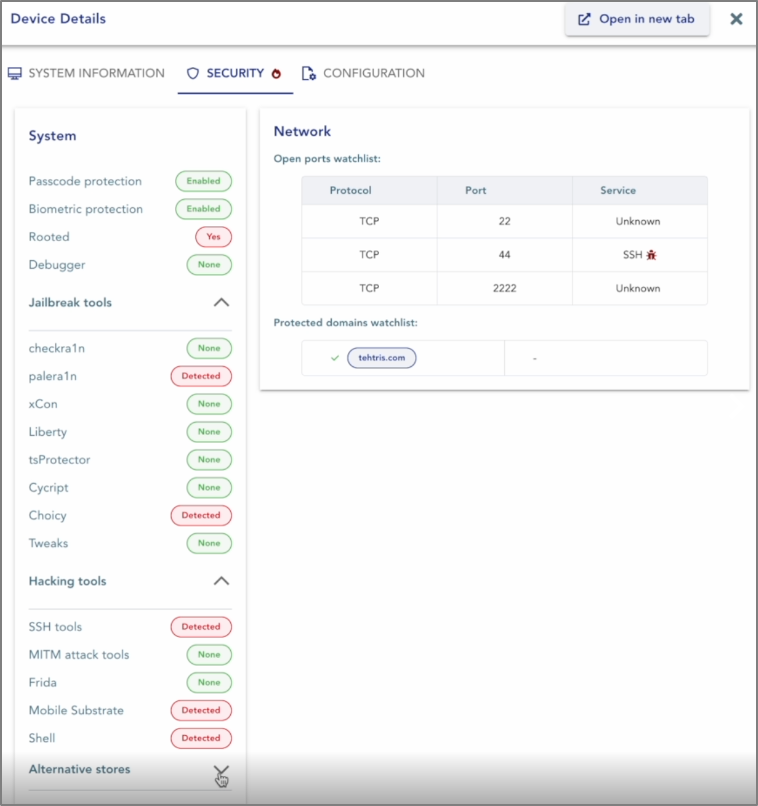
For further investigation, the SOC analyst can review detailed logs of the affected mobile device in the “Device Details” tab. The first displayed information confirms the phone is compromised.
By exploring the security section, the analyst will see that the phone has been jailbroken, with Palera1n identified as the jailbreak tool used. Additionally, an open ports list on the right reveals that the device’s SSH protocol is at risk.
However, the attack goes even further.
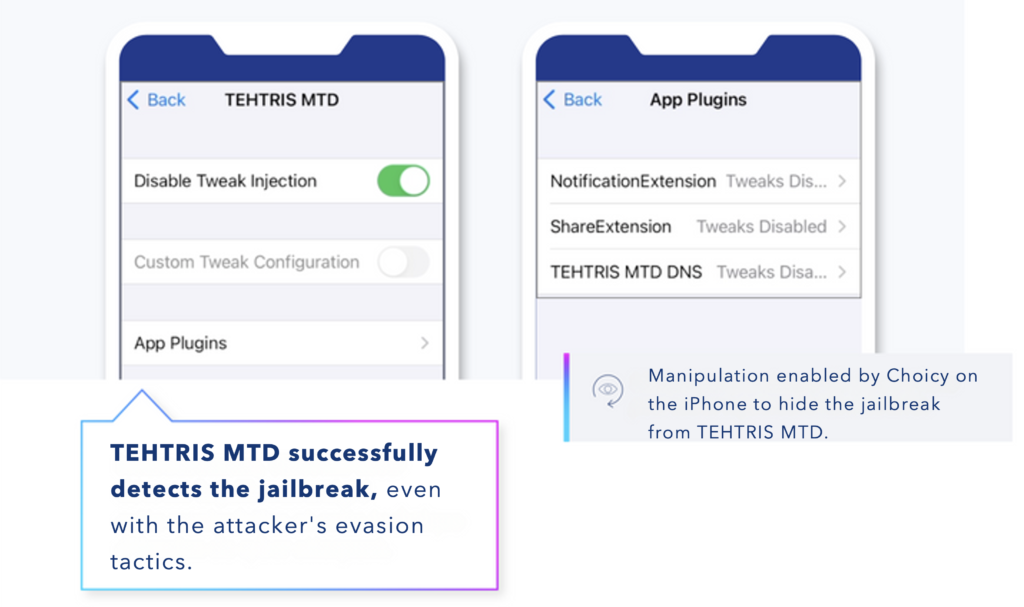
After jailbreaking the device with Palera1n, the attacker also deployed Choicy.
By downloading the alternative app store Sileo, the attacker gained access to Choicy, a tool specifically designed to conceal the jailbreak from other apps on the device.
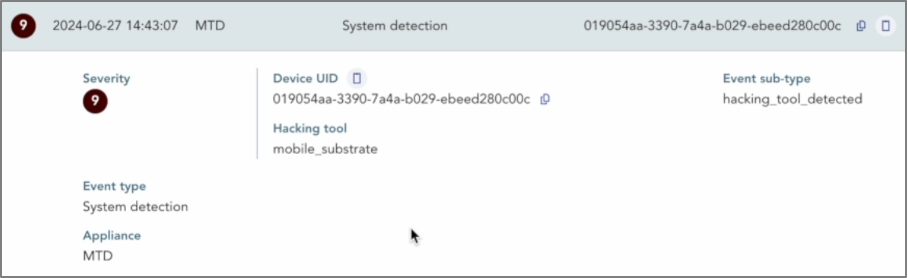
On the XDR AI PLATFORM console, under the “MTD Alerts & Events” tab, the SOC analyst notices two new alerts:
Detection of unauthorized changes to core operating system functions (not approved by Apple).
Identification of the Choicy tool
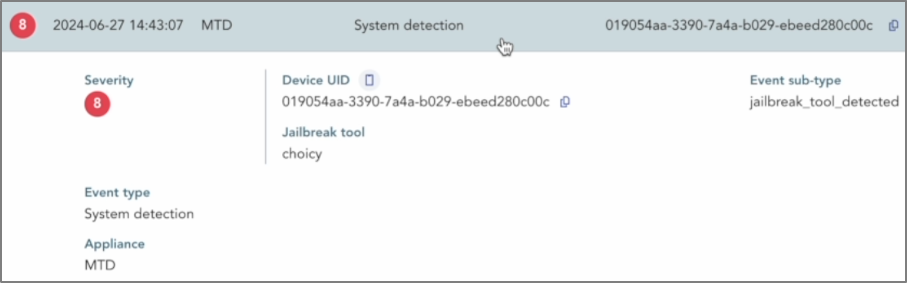
In the “Device” tab, the SOC analyst gains a clear, detailed view of all security issues on the mobile device. This concise overview highlights system vulnerabilities and identifies the tools used by the attacker.
Open ports, along with associated protocols and services, are also displayed, simplifying decision-making for the analyst with quick access to this summary.
Expanding the “Alternative Stores” section reveals the presence of Sileo. Additionally, APT is flagged as detected, as Sileo relies on APT to function.
At this stage, with all the necessary information, the SOC analyst can isolate the mobile device from DNS and send a push notification to the user, alerting them of the compromise and providing security guidelines to follow.
Key Takeaways
Steps Taken by the Attacker: The attacker conducted a jailbreak on the iPhone by installing and using the Palera1n tool.
Impact on the user’s device:
< none >
The attacker hid the icons of the malicious tools on the iPhone’s home screen, preventing detection of the cyberattack.
They also used the Choicy tweak, downloaded from the Sileo store, to hide the jailbreak from security apps.
This tool can further conceal the jailbreak from banking apps with protections against compromised devices.
TEHTRIS MTD’s Detection:
Both the app and the XDR AI PLATFORM console successfully detected all actions taken by the attacker. The mobile device is confirmed compromised, with each alert providing specific details.
In this case, it is critical to immediately STOP using the device.
The TEHTRIS MTD solution is designed to detect and identify low-level system threats, which pose the greatest danger.
These threats risk the user’s loss of control over the mobile device and exposure of sensitive data.
The administrator or SOC analyst is provided with the necessary information to assess the incident and take swift remediation actions.
