The crisis between Russia and Ukraine is not new. Its origin is historical but accelerated with the events of 2014, which correspond to the annexation of Crimea by Russia. Tension is particularly high in the Donbass region. A tendency to thaw had been felt with the arrival of Volodymyr Oleksandrovytch Zelensky to power in 2019, including the signing of ceasefire agreements in 2020, but the hope was short-lived.
These factors added to a more global context, such as the arrival of Joe BIDEN to power, who is pro-Ukrainian and wants Ukraine to join NATO (which strongly displeases Russia) explain the mobilization of Russian military troops and the escalation of violence in recent months.
Despite an attempt at dialogue between the United States, Europe and Russia, the tension remains. Ukraine is indeed subject to large-scale cyberattacks, paralyzing government agencies (70 government sites), national education sites … no data leakage is to be deplored for the moment.
Ukraine accuses Russia, which denies any involvement in these cyberattacks.
The attack mentioned in this article is based on a Microsoft publication [1].
It takes the form of a disguised ransomware, which, instead of reversibly encrypting with a ransom demand, renders computers inoperable.
What are we talking about?
This attack is composed of several steps (“stage”):
Stage 1
The first stage aims at trapping the MBR of the machine, and, at the next reboot, destroys the data on the disk.
Stage 2
Before starting its action, this binary launches a obfuscated powershell command in order to delay the malicious action by a few seconds, probably to evade security products.
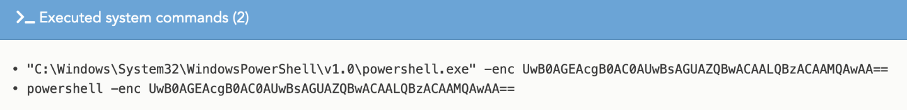
Then, it will try to download a third stage via the Discord CDN (free written/voice messaging software for the public) in the form of a JPG, whose URL is hardcoded in the binary of the second stage:
https[:]//cdn.discordapp[.]com/attachments/928503440139771947/930108637681184768/Tbopbh.jpg
Stage 3
This JPG, which is not a JPG, is in fact the obfuscated stage3. Indeed, the deobfuscated stage3 seems to be a dll with two functions:
- disable Windows Defender
- corrupt files of some extensions by overwriting part of their content:
.3DM .3DS .7Z .ACCDB .AI .ARC .ASC .ASM .ASP .ASPX .BACKUP .BAK .BAT .BMP .BRD .BZ .BZ2 .CGM .CLASS .CMD .CONFIG .CPP .CRT .CS .CSR .CSV .DB .DBF .DCH .DER .DIF .DIP .DJVU.SH .DOC .DOCB .DOCM .DOCX .DOT .DOTM .DOTX .DWG .EDB .EML .FRM .GIF .GO .GZ .HDD .HTM .HTML .HWP .IBD .INC .INI .ISO .JAR .JAVA .JPEG .JPG .JS .JSP .KDBX .KEY .LAY .LAY6 .LDF .LOG .MAX .MDB .MDF .MML .MSG .MYD .MYI .NEF .NVRAM .ODB .ODG .ODP .ODS .ODT .OGG .ONETOC2 .OST .OTG .OTP .OTS .OTT .P12 .PAQ .PAS .PDF .PEM .PFX .PHP .PHP3 .PHP4 .PHP5 .PHP6 .PHP7 .PHPS .PHTML .PL .PNG .POT .POTM .POTX .PPAM .PPK .PPS .PPSM .PPSX .PPT .PPTM .PPTX .PS1 .PSD .PST .PY .RAR .RAW .RB .RTF .SAV .SCH .SHTML .SLDM .SLDX .SLK .SLN .SNT .SQ3 .SQL .SQLITE3 .SQLITEDB .STC .STD .STI .STW .SUO .SVG .SXC .SXD .SXI .SXM .SXW .TAR .TBK .TGZ .TIF .TIFF .TXT .UOP .UOT .VB .VBS .VCD .VDI .VHD .VMDK .VMEM .VMSD .VMSN .VMSS .VMTM .VMTX .VMX .VMXF .VSD .VSDX .VSWP .WAR .WB2 .WK1 .WKS .XHTML .XLC .XLM .XLS .XLSB .XLSM .XLSX .XLT .XLTM .XLTX .XLW .YML .ZIP
There are still doubts about the precise intentions of this malware.
TEHTRIS recommendations
Against these threats, TEHTRIS recommends to all its customers and all readers of this article, as advised by Microsoft to:
- Check in its EDR/EPP logs all the executions in the directories C:PerfLogs, C:ProgramData, C:, and C:temp, that have been seen to carry this threat. Unless there is a park-related exception, these path should contain very few legitimate executions.
Also, you can check the following filenames: stage1.exe, stage2.exe, Tbopbh.* .
In general, thanks to the different modules of the TEHTRIS EDR (powershell detection, Sandbox, …), even if the threat was not known, it would have been detected and even remedied depending on the configuration applied.
- Check in the SIEM logs, for example proxy, the URL of the Discord CDN:
https://cdn.discordapp[.]com/attachments/928503440139771947/930108637681184768/Tbopbh.jpgSince the Discord CDN can be used as an intermediary to download malicious content[2],, if it is not useful in your company, you may consider simply blocking this URL from certain networks (e.g. from the servers’ network if they have Internet access).
If you have an instance of TEHTRIS DNS Firewall, it can be used for both investigation and blocking if desired.
TEHTRIS is monitoring the threat closely and will update the article if new developments become known.
Bibliography :
[1] https://www.microsoft.com/security/blog/2022/01/15/destructive-malware-targeting-ukrainian-organizations/
[2] https://www.proofpoint.com/us/blog/threat-insight/ta575-uses-squid-game-lures-distribute-dridex-malware
IOC
|
Type |
Description |
Objet |
|
SHA256 |
stage 1 |
a196c6b8ffcb97ffb276d04f354696e2391311db3841ae16c8c9f56f36a38e92 |
|
SHA256 |
Stage 2 |
dcbbae5a1c61dbbbb7dcd6dc5dd1eb1169f5329958d38b58c3fd9384081c9b78 |
|
SHA256 |
Tbopbh.jpg (stage3, obfusqué) |
923eb77b3c9e11d6c56052318c119c1a22d11ab71675e6b95d05eeb73d1accd6 |
|
SHA256 |
frkmlkdkdubkznbkmcf.dll (stage3, decodé) |
9ef7dbd3da51332a78eff19146d21c82957821e464e8133e9594a07d716d892d |
|
URL |
https[:]//cdn.discordapp[.]com/attachments/928503440139771947/930108637681184768/Tbopbh.jpg | |
|
Chemin |
C:PerfLogs | |
|
Chemin |
C: | |
|
Chemin |
C:ProgramData | |
|
Chemin |
C:temp | |
|
Nom de fichier |
Tbopbh.* | |
|
Nom de fichier |
Stage1.exe | |
|
Nom de fichier |
Stage2.exe | |
|
Nom de fichier |
frkmlkdkdubkznbkmcf.dll | |
|
Ligne de commande |
powershell -enc UwB0AGEAcgB0AC0AUwBsAGUAZQBwACAALQBzACAAMQAwAA== |

