Overview of current threats facing businesses in July 2025
This report outlines two major cybersecurity threats and the growing danger of ransomware attacks, all of which could have serious consequences for organizations across sectors.
The first threat involves a serious flaw in Microsoft Windows, which could allow hackers to gain access remotely without needing a password. This vulnerability (CVE‑2025‑47981) is especially concerning because it affects authentication systems that are built into Windows and are usually turned on by default. The second flaw (CVE‑2025‑47812) targets a popular file-sharing software called Wing FTP Server. Unlike the first, this one is already being exploited by attackers, meaning organizations using it are at immediate risk.
In addition to these technical issues, cybercriminal groups are becoming more aggressive. Two gangs, known as Qilin and Incransom, are especially active. They break into company systems, lock up critical data, and demand payment to unlock it. Their attacks have recently focused on legal services, retail businesses, and healthcare providers—industries that rely heavily on sensitive information and constant access to systems.
This report aims to help decision-makers understand the nature of these threats in clear terms, so they can take timely action to secure their systems, protect customer data, and reduce operational risk.
This report highlights two critical remote code execution vulnerabilities: CVE-2025-47981 in Windows SPNEGO NEGOEX (CVSS 9.8) and CVE-2025-47812 in Wing FTP Server (CVSS 10.0), with active exploitation confirmed for the latter. It also provides insights into recent ransomware activity, identifying Qilin and Incransom as the most active groups, with legal, retail, and healthcare sectors being heavily targeted.
CERT
CVE-2025-47981 (RCE in Windows SPNEGO NEGOEX)
Windows SPNEGO NEGOEX are security protocols extensions used in Windows environments to help negotiate which authentication protocol to use (Kerberos, PKU2U, NTLM) when a client connects to a Windows Server. It is enabled by default starting Windows 10 version 1607. This can be checked with the Group Policy setting Network security: Allow PKU2U authentication requests to this computer to use online identities. Protocols such as SMB, RDP and LDAP uses SPNEGO and potentially NEGOEX for authentication.
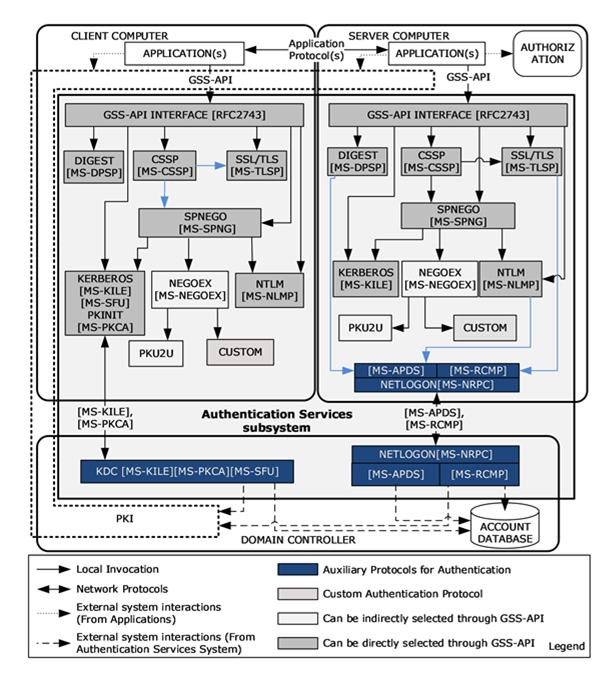
A remote code execution vulnerability in SPNEGO NEGOEX has been published on 08/07/2025, allowing an unauthenticated attacker to execute code on a remote server. The CVSS 3.1 score is 9.8.
Exploitation of this vulnerability could be exploited according to Microsoft, but has not yet been spotted in the wild. The vulnerability was patched on 08/07/2025.
CVE-2025-47812 (RCE in Wing FTP Server)
Wing FTP is a free FTP server software used in thousands of public facing servers worldwide.
A vulnerability has been made public on 10/07/2025 in Wing FTP Server < 7.4.4 (14/05/2025) allowing attacker to execute remote code on the server. The CVSS 3.1 score for CVE-2025-47812 is 10.0 (critical) and In-The-Wild exploitation has been spotted.
The exploit requires credentials, either through anonymous login or with known credentials.
A Sigma rule has been released by Huntress to help the detection, based on the creation of cmd.exe from the Wing FTP process.
Ransomware
Victims around the world (08/07 – 22/07)
This interactive world map highlights the distribution of ransomware victims. Hovering over each country reveals a list of known victims for these last two weeks.
(Data from Ransomfeed)
Most targeted sectors (08-07 – 22/07)
This graph displays the distribution of ransomware victims by industry sector.
Legal & professional services remains the most targetted sector, followed by retail and technology.
(Data from Ransomfeed)
Group ranking based on activity (08/07 – 22/07)
Qilin remains the most active group, with Incransom being very close. Payoutsking is a new ransomware group with very little information about it, but already has 18 victims to its name. A detailed report on Incransom is available in this report.
| rank | name | victims |
|---|---|---|
| 1 | qilin* | 29 |
| 2 | incransom | 28 |
| 3 | akira | 22 |
| 4 | worldleaks | 20 |
| 4 | safepay** | 20 |
| 6 | payoutsking | 18 |
| 7 | play | 15 |
| 8 | dragonforce | 12 |
| 9 | lynx | 10 |
| 10 | direwolf | 9 |
(Data from Ransomfeed)
*A report on the group, a technical analysis and IoC on Qilin is available here.
**A short analysis of the group and IOCs are available in a previous edition of this report.
Focus on IncRansom
Incransom has been in the industry for a while now and has remained a constant threat for a few years.
(Data from Ransomfeed)
As with most ransomware groups, the west is their primary target, especially the US with a total of 218 victims.
(Data from Ransomfeed)
Companies in the healthcare sector are the most targeted by Incransom.
(Data from Ransomfeed)
According to SOC Radar, the group uses spear phishing and vulnerabilities exploitation to gain initial access.
IncRansom’s blog feature details about victims and a countdown for some of them to indicate when they plan on leaking stolen data.
IOC
SHA256
73237b5c37b9625b0b26d6f4d476a619dfa78d9bc3959b48c7a77302d40093c1Ransom note
Inc. Ransomware
We have hacked you and downloaded all confidential data of your company and its clients.
It can be spread out to people and media. Your reputation will be ruined.
Do not hesitate and save your business.
Please, contact us via:
http://incpaysp74dphcbjyvg2eepxnl3tkgt5mq5vd4tnjusoissz342bdnad.onion/
Your personal ID:
<CENSORED>
We're the ones who can quickly recover your systems with no losses. Do not try to devalue our tool - nothing will come of it.
Starting from now, you have 72 hours to contact us if you don't want your sensitive data being published in our blog:
http://incblog7vmuq7rktic73r4ha4j757m3ptym37tyvifzp2roedyyzzxid.onion/
You should be informed, in our business reputation - is a basic condition of the success.
Inc provides a deal. After successfull negotiations you will be provided:
1. Decryption assistance;
2. Initial access;
3. How to secure your network;
4. Evidence of deletion of internal documents;
5. Guarantees not to attack you in the future.Extension
.INCDetection rules
Yara
import "pe"
rule IncRansom : ransomware incransom {
meta:
author = "TEHTRIS - Lefebvre Fabien"
description = "Detects IncRansom ransomware"
sha256 = "['73237b5c37b9625b0b26d6f4d476a619dfa78d9bc3959b48c7a77302d40093c1']"
strings:
$pdb = "C:\source\INC Encryptor\Release\INC Encryptor.pdb" ascii
condition:
pe.is_pe and all of them
}
