A new version of the Ransomware as a Service (RaaS) Redeemer has been launched earlier this summer. This ransomware builder became popular in June 2021 when the creator published the 1.0 programming code version on a forum.
About Redeemer 2.0
Redeemer stands out from other RaaS as it is free and publicly available for all to use. Its author, Cerebrate, conceived the “product” in a way that guarantees that they will benefit from 20% of any successful ransomware operations carried out by affiliates. Indeed, to reverse the encryption process in the event of a victim paying the ransom, the affiliate will need a combination of the master key (provided by the Cerebrate, the author) and their own private key.
Redeemer is accessible on a Dread dark website. After executing itself with admin privileges and encrypting the victims’ files with a .redeem extension, a ransom note asking for a payment in Monero cryptocurrency is generated.
The recent 2.0 version features a new graphical user interface for the affiliate to build the ransomware executable and decryption tool and a campaign tracking system, while all instructions on how to use it are enclosed in a ZIP.
Detecting Redeemer with TEHTRIS XDR Platform
The Redeemer toolkit being freely accessible, anyone – even with low hacking skills – can participate in extortion using encryption. That in itself constitutes a threat for entities that are not sufficiently protected, as is often the case in the vital healthcare sector or for smaller businesses with tight budget to allocate to cybersecurity.
To meet the needs of small and medium-sized organizations to defend themselves against aggressive cyber threats, TEHTRIS OPTIMUS offers a 100% online detection and protection for computers and servers, with simplified and rapid deployment while guaranteeing high-performance security. TEHTRIS OPTIMUS combines EDR (Endpoint Detection and Response) and NGAV (Next Generation AntiVirus) capabilities to detect and neutralize known and unknown threats in real time with no human interaction required. This technology includes a single agent with pre-configurations, can be deployed in a short period of time and offers an optimized user experience.
How does TEHTRIS EDR protect devices from a threat like Redeemer?
TEHTRIS dynamic analysis: Cyber Threat Intelligence
Using a security solution on all endpoints – on top of raising awareness about cybersecurity among the staff and making sure that offline backups are kept up to date – is essential to prevent an attack from a ransomware like Redeemer.
Any file executed on a device protected by TEHTRIS EDR (Endpoint Detection Response) is automatically analyzed in TEHTRIS Cyber Threat Intelligence (CTI) data base. CTI is both a knowledge base and a malware analysis tool powered with artificial intelligence, static and dynamic analysis capabilities, as well as a direct and secure link with external database. If a malware like Redeemer is launched on a machine, it will be identified as highly dangerous and will immediately set off an alert (and instantly kill the process if the EDR is set on remediation mode).
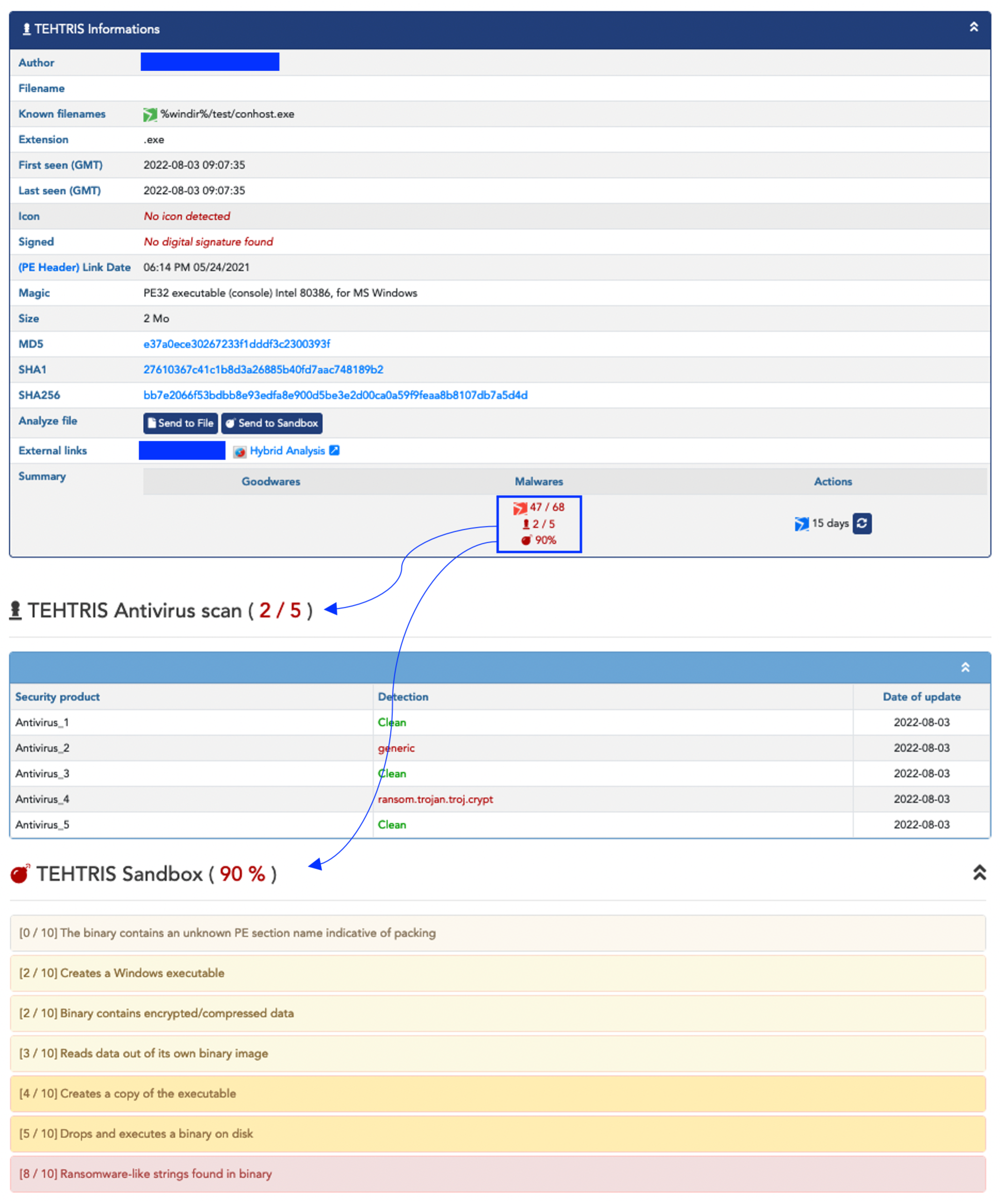
Analysis of Redeemer’s SHA256 in TEHTRIS CTI
The dynamic analysis in TEHTRIS Sandbox has detected several critical behaviors, such as loading shared modules to execute malicious payloads (T1129 on the MITRE ATT&CK framework), evading detection by performing software packing to change the file signature (T1027.002) and then decoding files (T1140), or obfuscating command and control traffic to make it more difficult to detect (T1001).
Isolated an infected machine with TEHTRIS SOAR
Another layer of protection offered by the TEHTRIS XDR Platform is the implementation of a playbook on the SOAR (Security Orchestration Automation and Response). Since a ransomware will use lateral movement to access high-value data in a penetrated network, the SOAR allows to automatically isolate a device to prevent the threat from spreading to the whole network, while still keeping an eye on the events happening on the infected machine through TEHTRIS XDR. In the case of Redeemer, a tailored-made playbook could be implemented with the following characteristics – after a testing phase to make sure that it does not trigger false positives:
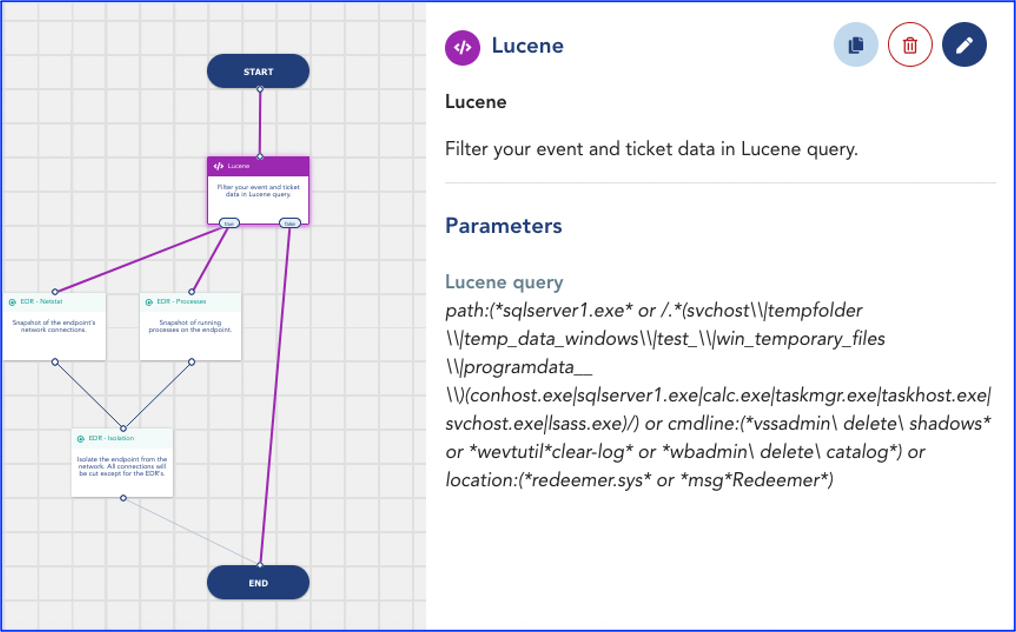
The scenario starts with a Lucene query that takes into account the specificities of Redeemer (such as names of the files and folders in which the malware copies itself into the victim’s machine, command lines that Redeemer uses to delete the shadow copies, backup catalog and system state backups before encryption to prevent restoration for the victim.). If the query conditions are met, an automatic action will isolate the device from the network after taking a snapshot of the endpoint’s network connections and running processes. Results will then be available in the Alerts & Events tab. These indicators will help gather information for the incident investigation.
As for Redeemer 1.0, the author announced that version 2.0 “will go opensource” if they were to “lose interest”, which would create further opportunities for low-skilled cybercriminals. Anticipating those types of attacks is crucial: carrying out regular offline backups, updating systems and using a cybersecurity protection are imperative measures to protect from RaaS operations. TEHTRIS protects your company from known and unknown threats as we automatically neutralize ransomware and 0-days attack in real-time. Our solutions are modular and can be deployed individually or in a suite within the TEHTRIS XDR Platform.
https://www.bleepingcomputer.com/news/security/new-redeemer-ransomware-version-promoted-on-hacker-forums/ (21/07/22)
https://blog.cyble.com/2022/07/20/redeemer-ransomware-back-action/ (20/07/22)
TEHTRIS Threat Research weekly feed for customers (05/08/22)

