TEHTRIS unveils Qilin: a rising ransomware threat using tailored attacks to quietly cripple targets.
Author: Lefebvre Fabien (CTI)
Review & Input: Antoine Mevel (CTI), Justine Guyot (CTI)
Key points
- Qilin is a ransomware group that has been there for nearly 3 years and has become one of the most active group since the beginning of the year.
- Qilin can target any field, including the healthcare and non-profits organizations.
- USA is by far the most targetted country.
- The group use phishing as a vector of infection.
- Samples are protected by a password, preventing it from successfully running in sandbox environments.
- Each sample is specific to its target.
- The extension used for encrypted files is unique to the target.
The Qilin ransomware group
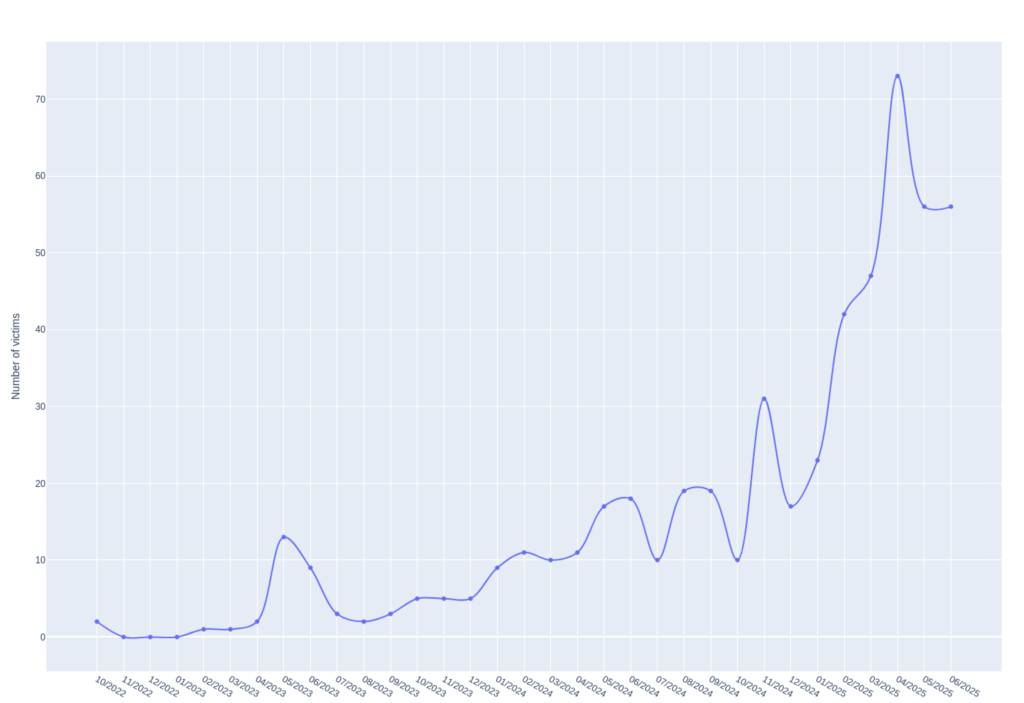
Qilin is a russian-speaking ransomware group which was first spotted in October 2022 and has since steadily risen among the most active ransomware groups, reaching a peak of 73 victims last month and 530 to date.
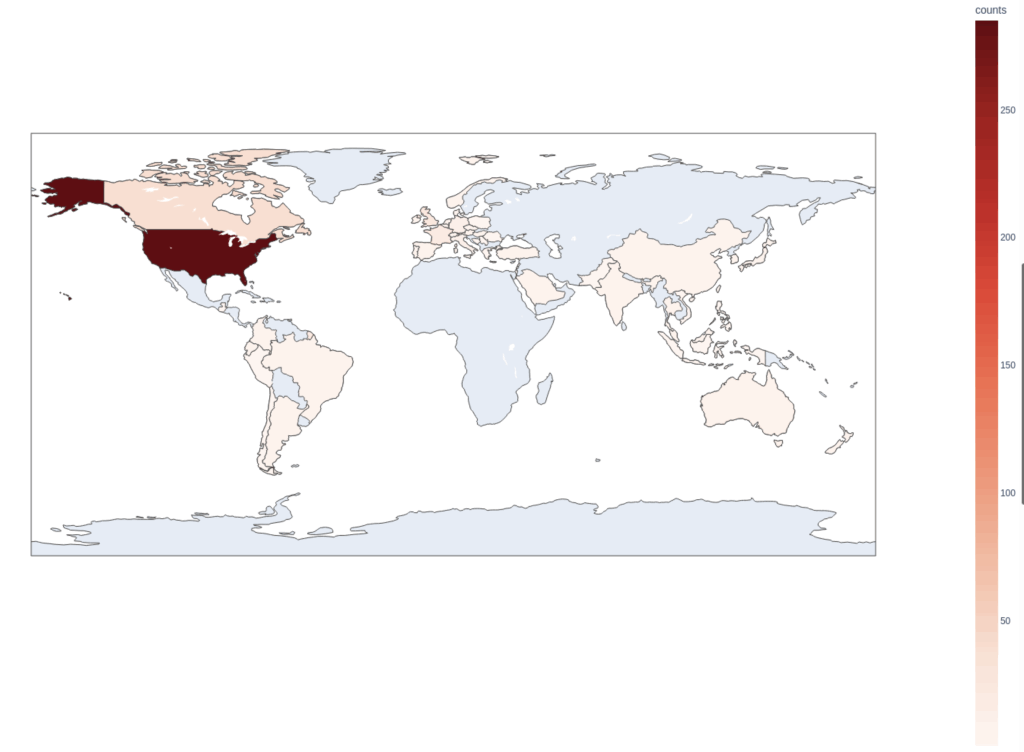
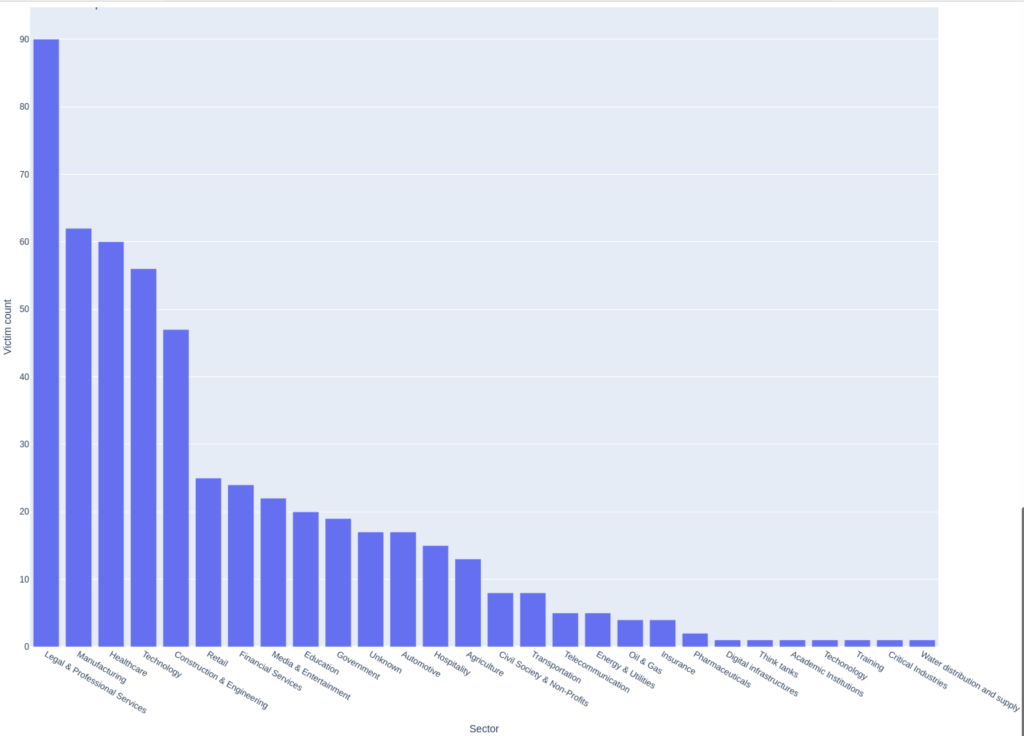
The USA is by far the most targeted country, with over 300 victims from this country, and is particularly dangerous as it is targeting every sector. However, most of its victims are in professional services, manufacturing, healthcare and technology industries with over half of the victims being an actor of these sectors.
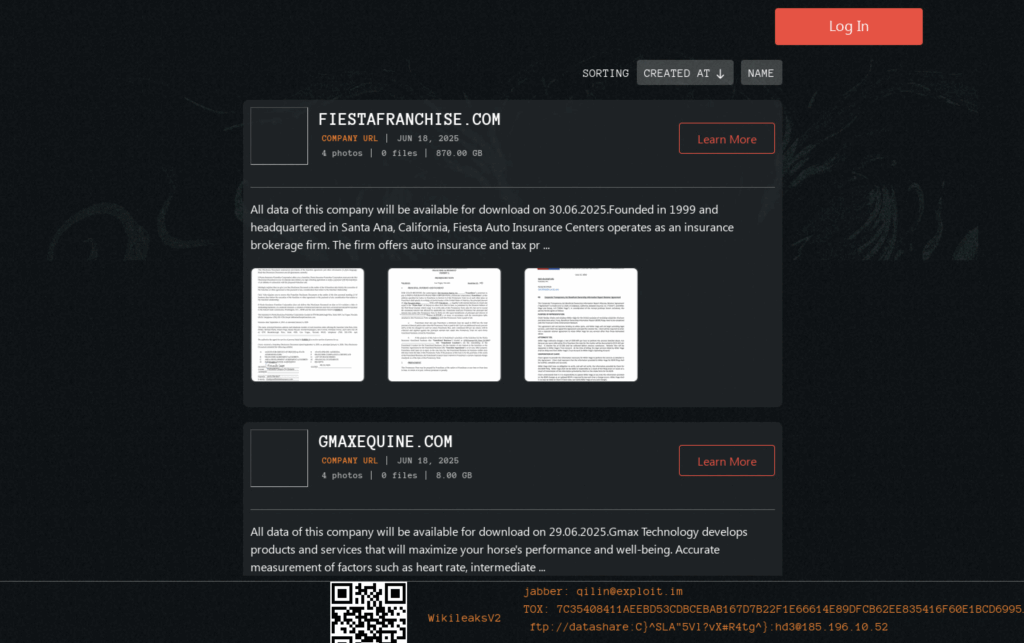
The group has a .onion page to list its victims, and leak data from those who refused to pay the ransom.
Typical infection vectors start with spear-phishing according to Group-IB.
Ransomware analysis
This section will focus on the technical aspect of the ransomware.
Configuration
Qilin handles two configuration sources, the first being embedded in the executable and the second being passed as arguments.
Embedded configuration
The embedded configuration contains the following informations:
public_rsa_pemprivate_rsa_pem: emptydirectory_black_list: a list of directory names which should not be encryptedfile_black_list: a list of file names which should not be encryptedfile_pattern_black_list: a list of keyword for which the file should not be encrypted if it is contained in the name ?process_black_list: ?win_services_black_list: ?company_id: an identificator for the company generated by Qilin. It is used as the extension for encrypted files ?npfastskipstepaccounts: a mapping of leaked accounts and associated cleartext password.note: the ransom note.password_hash: the password used by the operator to run the executable
The malware seems to be able to handle the following configurations that were not used:
white_symlink_dirswhite_symlink_subdirs
The RSA public key has been tested for vulnerabilities with RsaCtfTool, but none were found.
Arguments
Qilin offers a lot of arguments to customize its execution:
password: password used to execute the ransomware.pathsips: encrypt remote machines.timer: delay encryption (in seconds)no-sandbox: disable sandbox detection.no-escalate: disable privilege escalation throughimpersonate: SID of the user to impersonate.safe: restart computer in safe mode (will change user password and set autologin).no-priority: disables IO/CPU priority increaseno-admin: disables admin token requirement.no-local: disables local computer encryptionno-domain: disables domain computers’ encryption.no-mounted: disables mounted shares encryption.no-network: disables network shares encryption.no-ef: disable extension filter.no-ff: disable file filter.no-df: disable directory filter.no-autostart: don’t add persistence in registry.no-proc: disable process killer.no-services: disable service killer.no-vm: disable VM killer.kill-cluster: enable cluster killer.no-extension: disable extension for encrypted files.no-wallpaper: disable wallpaper changing.no-note: disables ransom note dropping.no-deleteno-destructno-zeroprint-imageprint-delayforcedebug: logs are printed to the consoleno-logsno-deletefdespread: spread to domain computers using PsExecspread-vcenter: spread a payload on ESXi through vCenterdry-runlogsescalatedparent-sidspread-process
Defense mechanisms
Qilin contains multiple ingenious defense mechanism, to avoid detection and to prevent it from being used by an unauthorized person.
Packing (T1027.002, T1055.002)
The main executable is an unpacker for Qilin, looping over its memory and unpacking using XOR and AND operators with hardcodded operands.
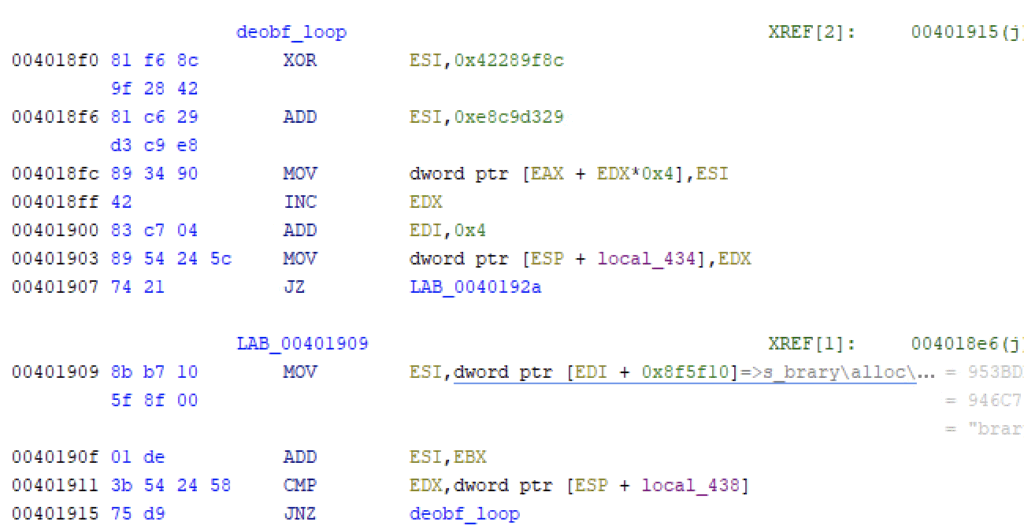
Qilin then copies each section in a memory buffer using memcpy.
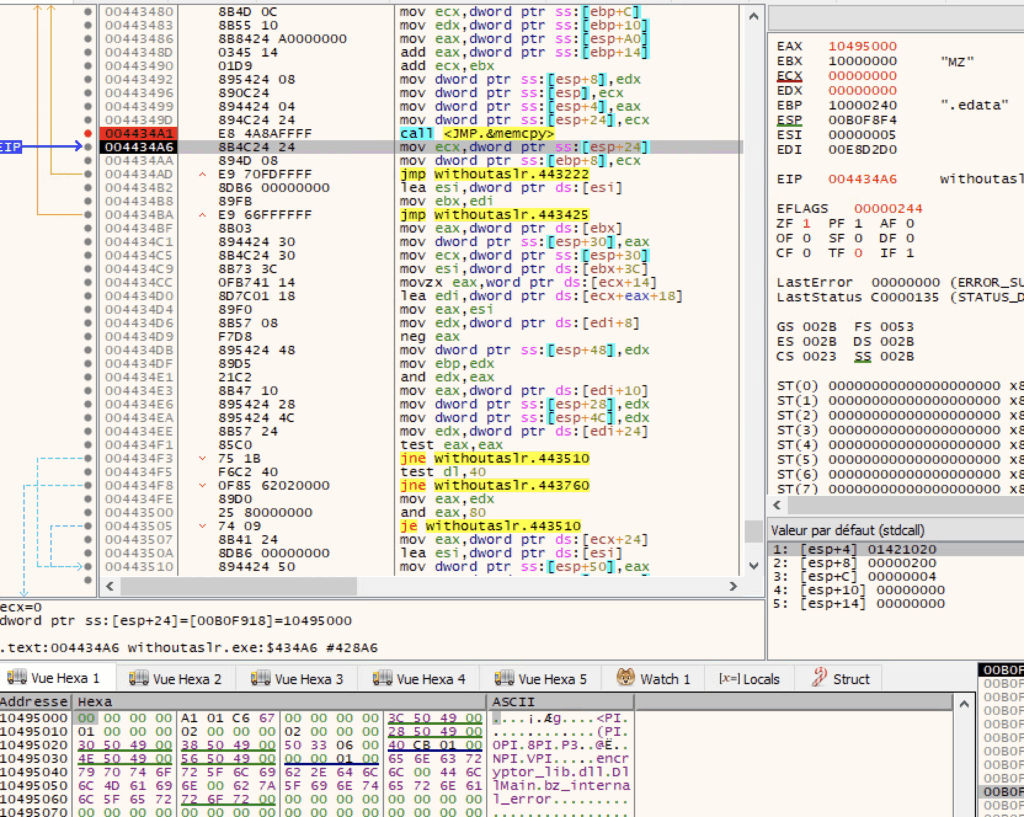
.edata section being copied to buffer at ECX.Afterwards, it makes the code executable and calls the unpacked Qilin’s tls_callback_0, tls_callback_1 and tls_callback_2 and then calls the entrypoint.
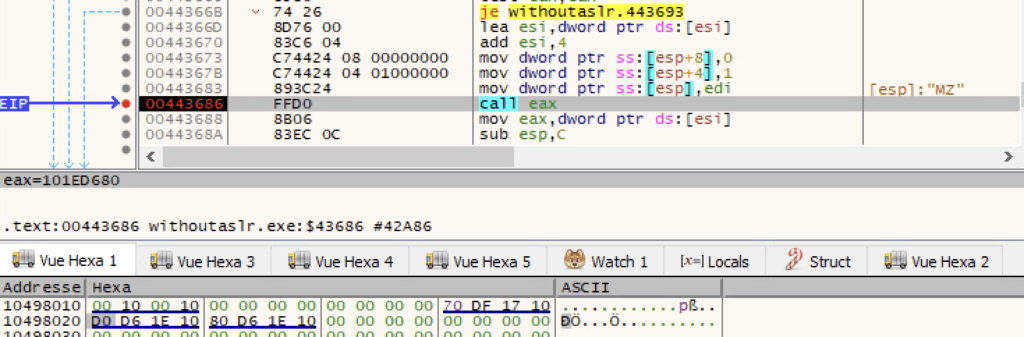
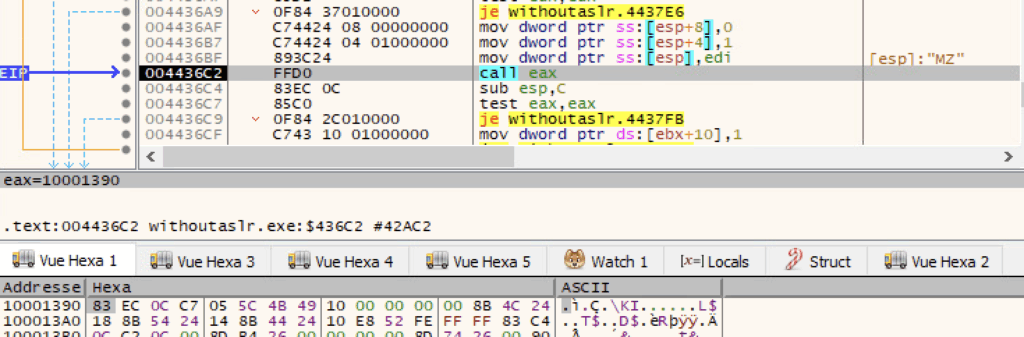
Password (T1497)
The second layer of protection is a password. The operator must provide this password to the executable using --password. The input is then hashed with SHA256 and compared to a password hash stored in the malware configuration. If the hashes don’t match, the executable logs an error and then exits.
Admin check
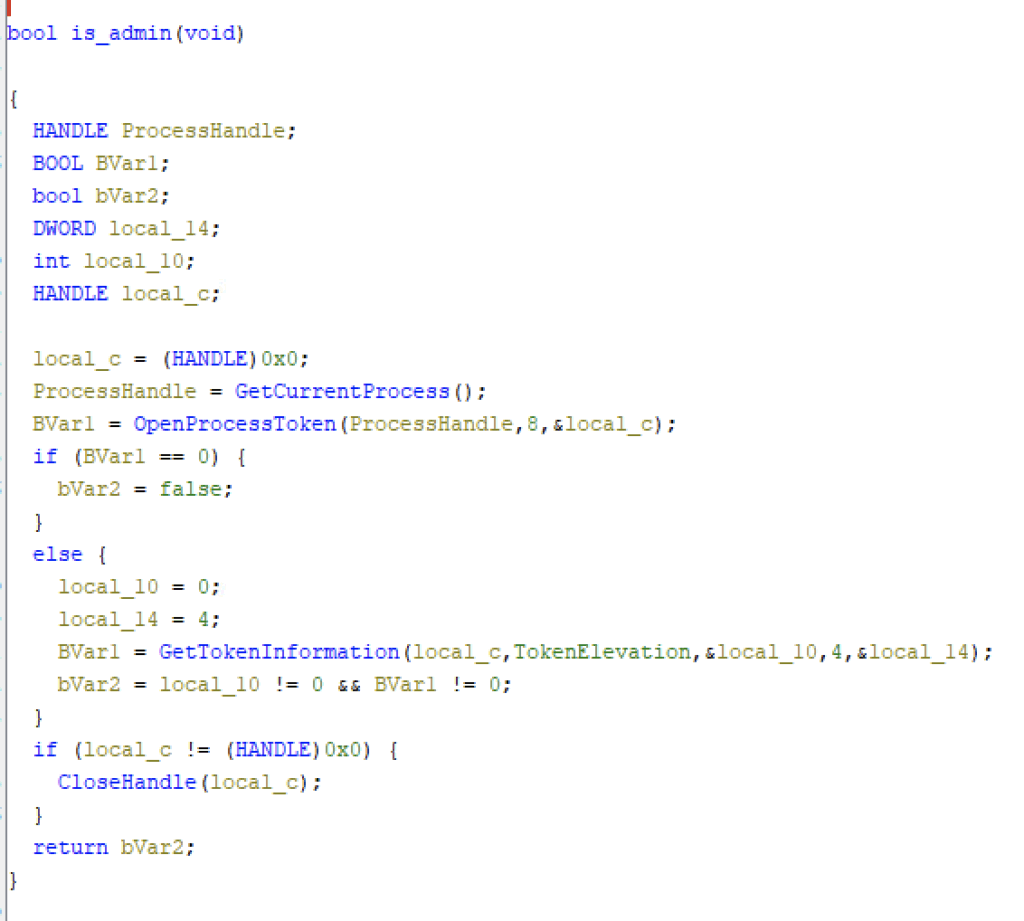
The malware then checks if the process is run with elevated privilege using the GetCurrentProcess, OpenProcessToken and GetTokenInformation APIs.
Sandbox evasion (T1497.001)
The malware starts gathering information about the host in an attempt to detect whether it’s running on a virtual machine or not.
First, it checks for processor information using cpuid instruction with EAX=1.
A second check is made with cpuid instruction and EAX=0x40000000, this time looking for the presence of the IDs Microsoft Hv, VMwareVMware, VBoxVboxVbox, KVMKVMKVM, XenVMXenVM, lrpepyv vr, indicating the presence of a hypervisor. If Microsoft Hv is detected, it also checks the presence of the key HKLM\SOFTWARE\Microsoft\Virtual Machine\Guest\Parameters to ensure it’s not a false positive.
A delay can also be specified using the --delay option to delay most capabilities of the ransomware, which can help bypass sandbox detection. By default, the delay is set to 0 seconds.
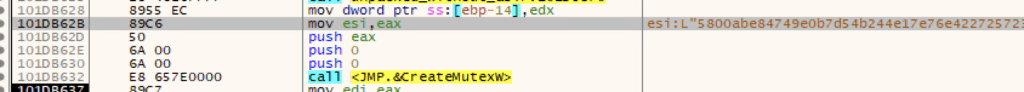
Mutex (T1480.002)
To avoid duplicate execution, Qilin creates a mutex with the executable password as its name.
Privilege escalation
Access token manipulation (T1134)
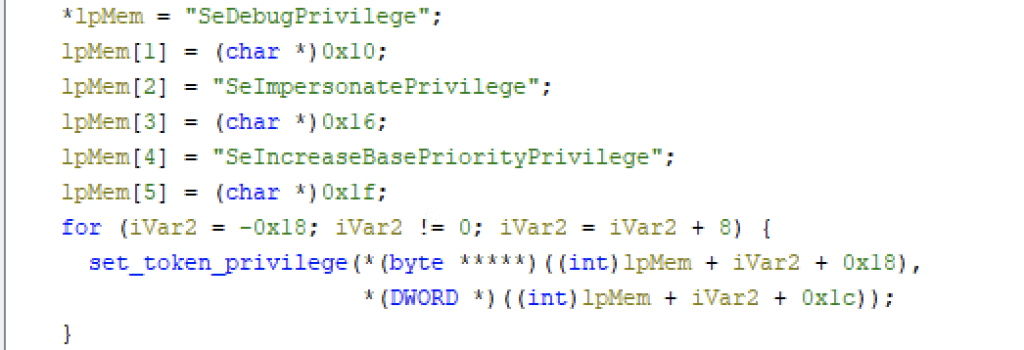
Qilin escalates its privilege using SeDebugPrivilege, SeImpersonatePrivilege and SeIncreaseBasePriorityPrivilege using a loop.
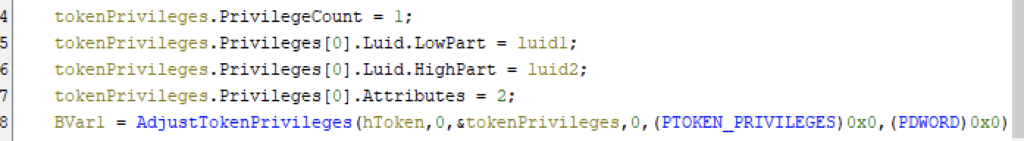
Impersonate
A SID can be given using the --impersonate option to impersonate a user during the encryption.
Impact
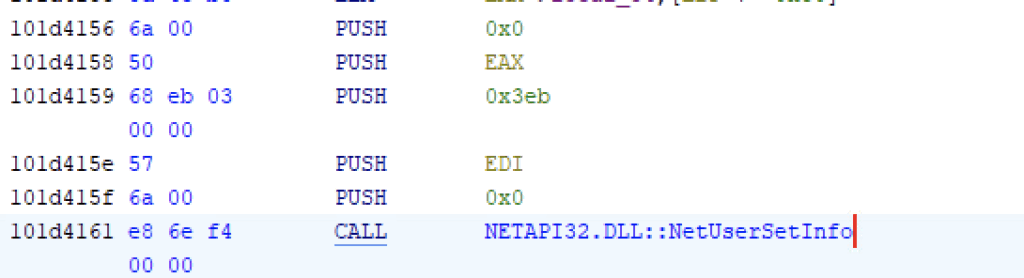
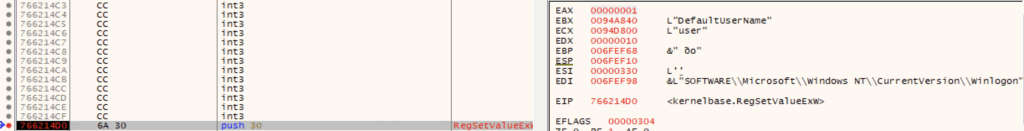
Change user password (T1098)
With --safe mode, Qilin changes the user password to the one passed by the --password argument using NetUserSetInfo with level=1003 (“specifies a user password”), and then enables autologin using HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon (AutoAdminLogon, DefaultUserName, DefaultPassword)
Impair defenses (T1562)
Symbolic links behavior are changed using the commands fsutil behavior set SymlinkEvaluation R2R:1 and fsutil behavior set SymlinkEvaluation R2L:1 which allows encrypting remote network shares by being able to follow the symbolic links to access another remote share.
Disabling VSS (T1490)
The shadows copies are disabled and deleted using the command vssadmin.exe delete shadows /all /quiet and the service is disabled using wmic service where name='vss' call ChangeStartModeDisabled and net stop vssem32.
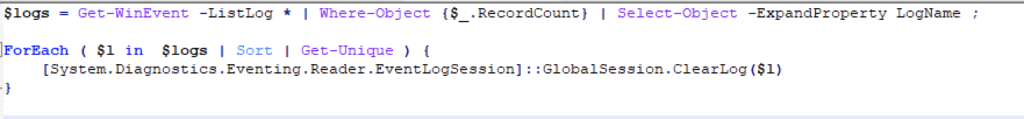
Logs removal (T1562.002)
Logs are continuously removed with a powershell script using the Get-WinEvent module.
Encryption (T1486, T1491.001)
Before the encryption, the malware collects information such as storing devices (such as device type, and if it is DASD capable) and volumes (mount points, whether it’s a system volume), shares and shortcuts on desktop and in shares.
To improve its performance, Qilin set the CPU priority to Realtime which is allowed by the SeIncreaseBasePriorityPrivilege privilege.
Qilin makes two passes on the encryption, the first with Chacha20 and the second with AES256.
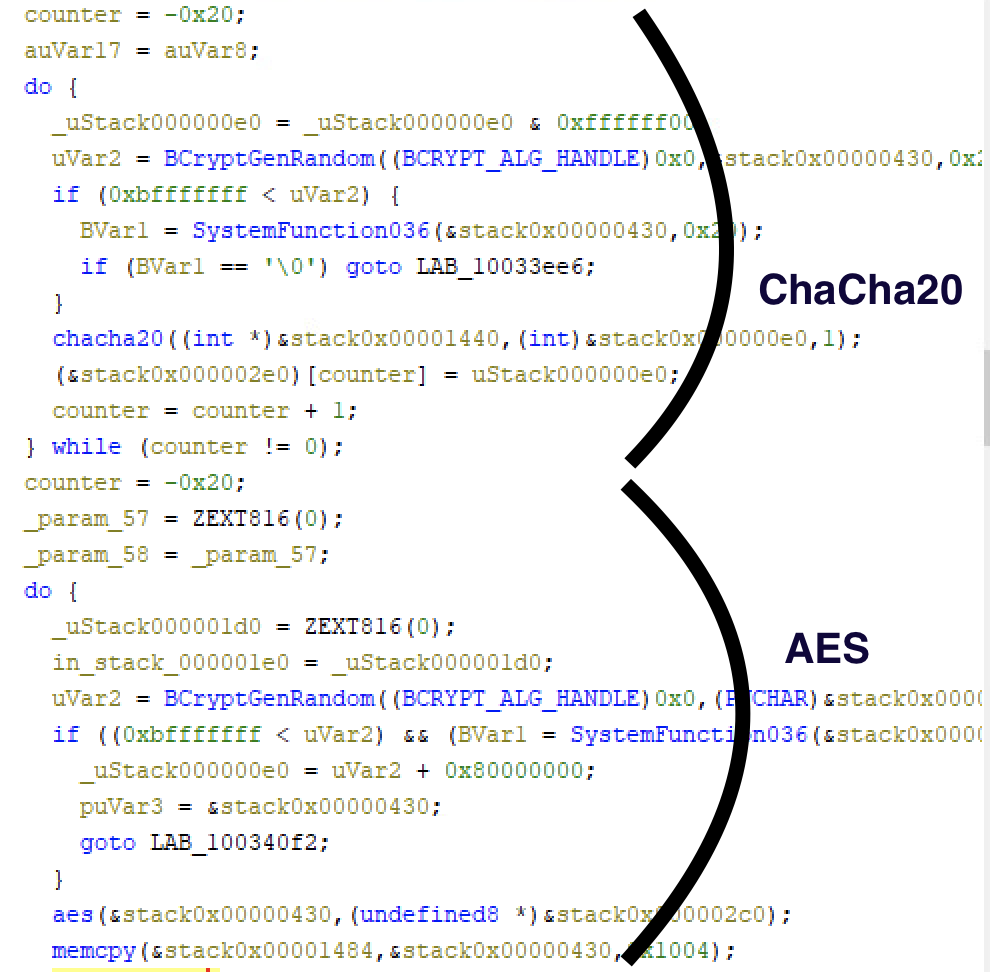
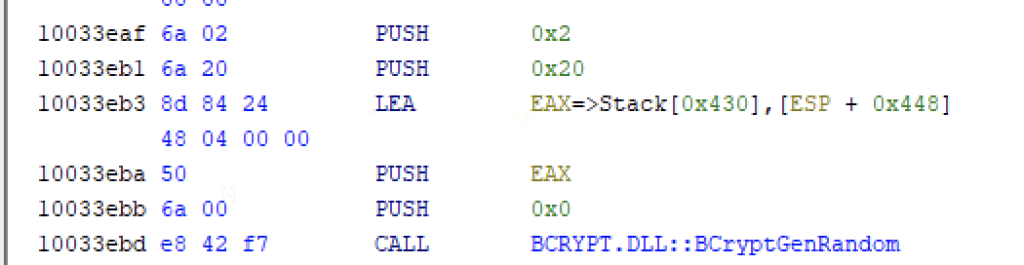
BcrypGenRandom is used to generate the random number used for both keys, the algorithm is chosen by the system (BCRYPT_USE_SYSTEM_PREFERRED_RNG). If it fails, it falls back to RtlGenRandom.
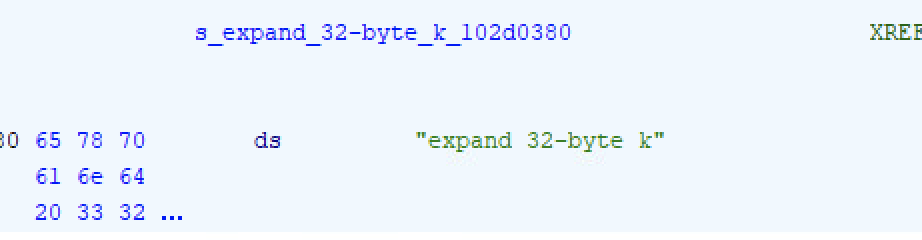
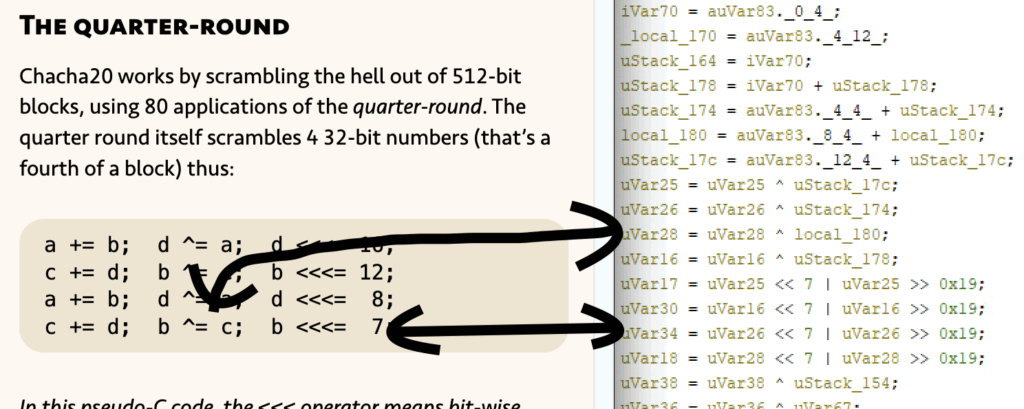
ChaCha20 is used to encrypt the data, this can be seen by the presence of the Brotli-compression constant, operations specific to ChaCha20 and a 32 bits counter.
AES is used for the second round, with the operations corresponding to AES implementation by OpenSSL.
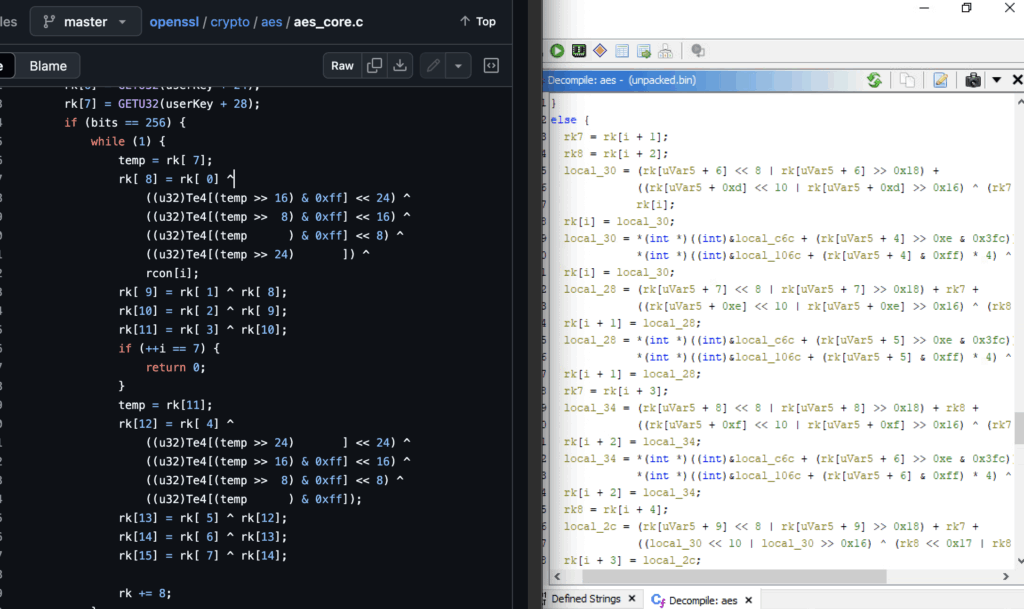
Files are renamed using the MoveFileExW API, by adding the company ID embedded in the configuration to the file name and a ransom note is dropped in each directory.
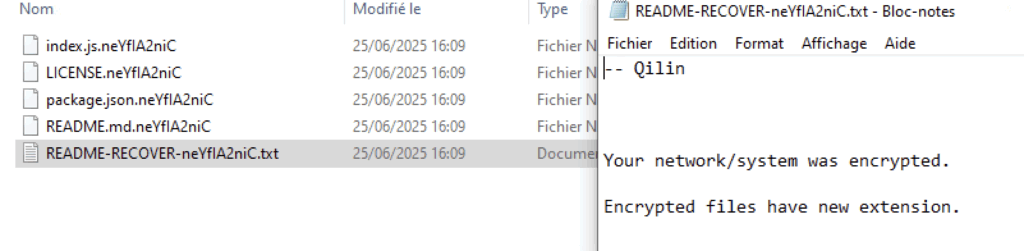
Once the encryption process is over, Qilin changes all users’ wallpaper and the lock screen with instructions for the user.
Self delete (T1070.004)
Qilin self delete itself once all encryption operations are over and logs cleared to impair recovery capabilities.
Persistence
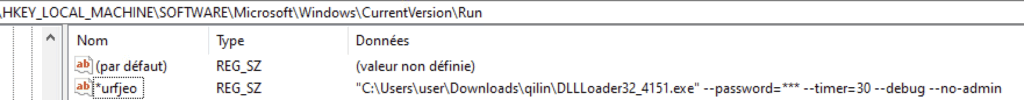
Registry (T1547.001)
A key in SOFTWARE\Microsoft\windows\CurrentVersion\Run is added to automatically run the ransomware on machine startup with the same arguments.
Lateral movement
ESXi (T1098, T1021.004; T1210, T1623)
With option spread-vcenter enabled, Qilin is capable of spreading a payload to ESXi using vCenter credentials. It then disables HA and Drs on all clusters, changes the user’s password and enables SSH on all hosts. Finally, it uploads and runs the payload on these hosts The path to the payload and credentials are given by the operator through the command line.
A comment in the Powershell script shows a developer’s frustration with Powershell.
Domain computers (T1588.002, T1021.002)
Qilin is also capable of spreading to other computers via PsExec with the --spread option, prompting the operator for user credentials.
IOC
SHA256
d628914c72a4294d6b67126eb8b5a08fa4974d05469852cb7ef872721b207498
5b358f7cb6c2f16badbb476f7fa7515d4c142a1c1c47e22ab058155aa3120ba1
5acd1ff8da9958a032cf63fb27d5e4b71c201612461e039f44eb07b2cc6735c0
381c3ed7a3b3d3017faaacb917c911aa266c2fb3e648f0e659222ec38148ee3c
1e52d9f04f99be66d5bc13db767c6acb5f0515906633f76e5c713681af9454df
1455a215def8fe3c7053a21e748d20bcef586014b3d000b9f8e64be6ed99addd
033b4d28791b318fee5017e79c87c974ee621bae3b137d78ff11e2623ecf78a5
02835451193c2232094b591b7ef52a18786bae3232330839e63631f077f4946b
f52567ef22018ee7ef696ec1b28b99f019552827445425dd08e98195f6ac56fe
f17c9c6b1f1e4434e2688fc0d25d0bca1efb89582c03028f787fa2b9f765c17a
db7b88dfbc16f4798b30c135a1e305d11b201ca3d9b600f2b2f3306f0ad32b18
c3fec6dd70f15fdf0683473539f1bde4c24e1aa25d97555c3d330f77b1edc3f1
a58adc18c13c4c357039ee5cf5fa5e886a7efc6026350cb7087466d667b87263
9983e9559790c6df67dc78157f65ee42320a9914c0b2cb7eb4b210e50266268c
96de53f71a914113dd1e0ab030b3e0707101af10bd6de3c894ee328d6f175e94
90bf9700d267b34aef7963ca51623daab9f4725253735a66e0a56c532f6b32c4
906f88817e3bf1bd4e800cf798650f3a309c81ee9b78c2a37d9118ce2567ae3d
8410f85c1710bfefccf0517cbbc91c0019073ced28d66539eeb596a9de8be1a9
78b6552fe4e7afbd21d8494dd19c056e16316b7aabdbaf746f5511a2dc2c542c
76dfbf622b6846653eff769e047efedc7a9fdbb00c939965d555da7aef460a5d
690d584bb489f5de42077147b13d5431ef3cd36e429a90fcdfe02bc97fdbec85
57e93d498dd91aebb7473950c12d8dc414aec39f6e3baa2a0b249649adf2ddc9
340351639863a1c01eb0f8e34aafa2a5f36a7ee378c3cb112827ce3e9bfd7a87
147ad250400bb8c5ec2f7542afc82491fd23d665b070db03c17022ec969024a6
6316417fcd979c39a4da672ba3521f62081ff4dfebb868ef65a1f2dff9a738ea
Written files
%TEMP%/QLOG/ThreadId(1).LOGRansom note
-- Qilin
Your network/system was encrypted.
Encrypted files have new extension.
-- Compromising and sensitive data
We have downloaded compromising and sensitive data from your system/network.
Our group cooperates with the mass media.
If you refuse to communicate with us and we do not come to an agreement, your data will be reviewed and published on our blog and on the media page (https://31.41.244.100)
Blog links:
http://kbsqoivihgdmwczmxkbovk7ss2dcynitwhhfu5yw725dboqo5kthfaad.onion
http://ijzn3sicrcy7guixkzjkib4ukbiilwc3xhnmby4mcbccnsd7j2rekvqd.onion
Data includes:
- Employees personal data, CVs, DL , SSN.
- Complete network map including credentials for local and remote services.
- Financial information including clients data, bills, budgets, annual reports, bank statements.
- Complete datagrams/schemas/drawings for manufacturing in solidworks format
- And more...
-- Warning
1) If you modify files - our decrypt software won't able to recover data
2) If you use third party software - you can damage/modify files (see item 1)
3) You need cipher key / our decrypt software to restore you files.
4) The police or authorities will not be able to help you get the cipher key. We encourage you to consider your decisions.
-- Recovery
1) Download tor browser: https://www.torproject.org/download/
2) Go to domain
3) Enter credentials
Please note that communication with us is only possible via the website in the Tor browser, which is specified in this note.
All other means of communication are not real and may be created by third parties, if such were not provided in this note or on the website specified in this note.
-- Credentials
Extension: neYfIA2niC
Domain: <CENSORED>
login: <CENSORED>ESXCLI command
esxcli system settings advanced set -o /User/execInstalledOnly -i 0Windows commands
fsutil behavior set SymlinkEvaluation R2R:1
fsutil behavior set SymlinkEvaluation R2L:1
net use
wmic service where name='vss' call ChangeStartMode Manual
net start vss
vssadmin.exe delete shadows /all /quiet
net stop vss
wmic service where name='vss' call ChangeStartMode DisabledQilin blog
http://kbsqoivihgdmwczmxkbovk7ss2dcynitwhhfu5yw725dboqo5kthfaad.onion
http://ijzn3sicrcy7guixkzjkib4ukbiilwc3xhnmby4mcbccnsd7j2rekvqd.onionDetection rules
Yara rule
import "pe"
rule QilinRansomware : ransomware qilin {
meta:
author = "TEHTRIS - Lefebvre Fabien"
description = "Detects Qilin ransomware"
sha256 = "['d628914c72a4294d6b67126eb8b5a08fa4974d05469852cb7ef872721b207498']"
strings:
$sections = {
// @loop
8b 72 10 // mov esi, [edx + 0x10]
8b 42 0c // mov eax, [edx + 0xc]
8d 7c 05 00 // lea edi, [ebp + eax]
01 f0 // add eax, esi
85 f6 // test esi, esi
0f 44 c7 // cmovz eax, edi
39 c3 // cmp ebx, eax
0f 42 d8 // cmovc ebx, eax
83 c1 01 // add ecx, 1
83 c2 28 // add edx, 0x28
39 4c 24 24 // cmp [esp + 0x24], ecx
75 de // JNZ @loop
}
condition:
pe.is_pe and all of them
}

