MITRE ATT&CK EVALUATIONS 2024: Changement de perspective
L’importance de l’anticipation par rapport aux évaluations post-attaque
Pour la deuxième année consécutive, TEHTRIS a démontré sa volonté de se remettre constamment en question et son engagement à atteindre l’excellence en participant à l’évaluation prestigieuse « MITRE ATT&CK Evaluations: Enterprise », une évaluation exclusive réalisée aux côtés d’acteurs majeurs de la cybersécurité.

Renforcer les équipes SOC : la puissance de l’IA proactive
Cette année, l’évaluation a davantage mis l’accent sur l’analyse post-attaque et s’est éloignée de l’anticipation et de la détection. La TEHTRIS XDR AI PLATFORM a démontré une résilience significative en identifiant, avec précision, les étapes de détection critiques et en neutralisant de manière autonome un complexe scénario de PROTECTION, impliquant trois vecteurs d’attaque distincts.
Cette évaluation a réaffirmé notre philosophie selon laquelle l’anticipation des menaces avec détection automatique et neutralisation en temps réel, et sans action humaine, doit primer sur l’analyse post-attaque. En dotant les équipes de sécurité de son IA propriétaire CYBERIA, basée sur l’Automatisation des Processus Neuronaux (APN), la TEHTRIS XDR AI PLATFORM simplifie le passage des événements en alertes, avec pour objectif principal d’améliorer l’efficacité globale de la détection et d’éliminer la cyber-fatigue des équipes SOC.
Cette évaluation valide l’approche innovante deTEHTRIS en matière de détection, de réponse et de stratégies de supervision.
A propos de l’évaluation MITRE ATT&CK :
L’évaluation MITRE ATT&CK est un exercice de test indépendant des fournisseurs de cybersécurité, mondialement reconnu. Cette année, elle a simulé les tactiques d’acteurs notoires de la menace, tels que les groupes de ransomware Cl0p et LockBit, ainsi que des comportements attribués à des adversaires tels que la République populaire démocratique de Corée (RPDC). L’objectif ? Évaluer les capacités de détection et de réponse dans des scénarios d’attaque réalistes.
L’innovation clé : « La méthode Chokepoint de TEHTRIS »
L’approche TEHTRIS Chokepoint, centrée sur les points de contact, garantit une stratégie qui combine une télémétrie complète à une détection précise, minimisant les faux positifs et réduisant les risques de passer à côté de menaces critiques. Lorsqu’une détection est faite via un point de contact, la TEHTRIS XDR AI PLATFORM permet d’y répondre de façon automatique ou manuelle, en ciblant une liste prédéfinie d’actifs, améliorant ainsi l’agilité opérationnelle.
En s’appuyant sur l’approche TEHTRIS Chokepoint, le scénario MITRE ER6 de détection et de protection met en évidence l’efficacité de la TEHTRIS XDR AI PLATFORM, en atteignant une pertinence de 100 % pour 12 tactiques MITRE ATT&CK®.
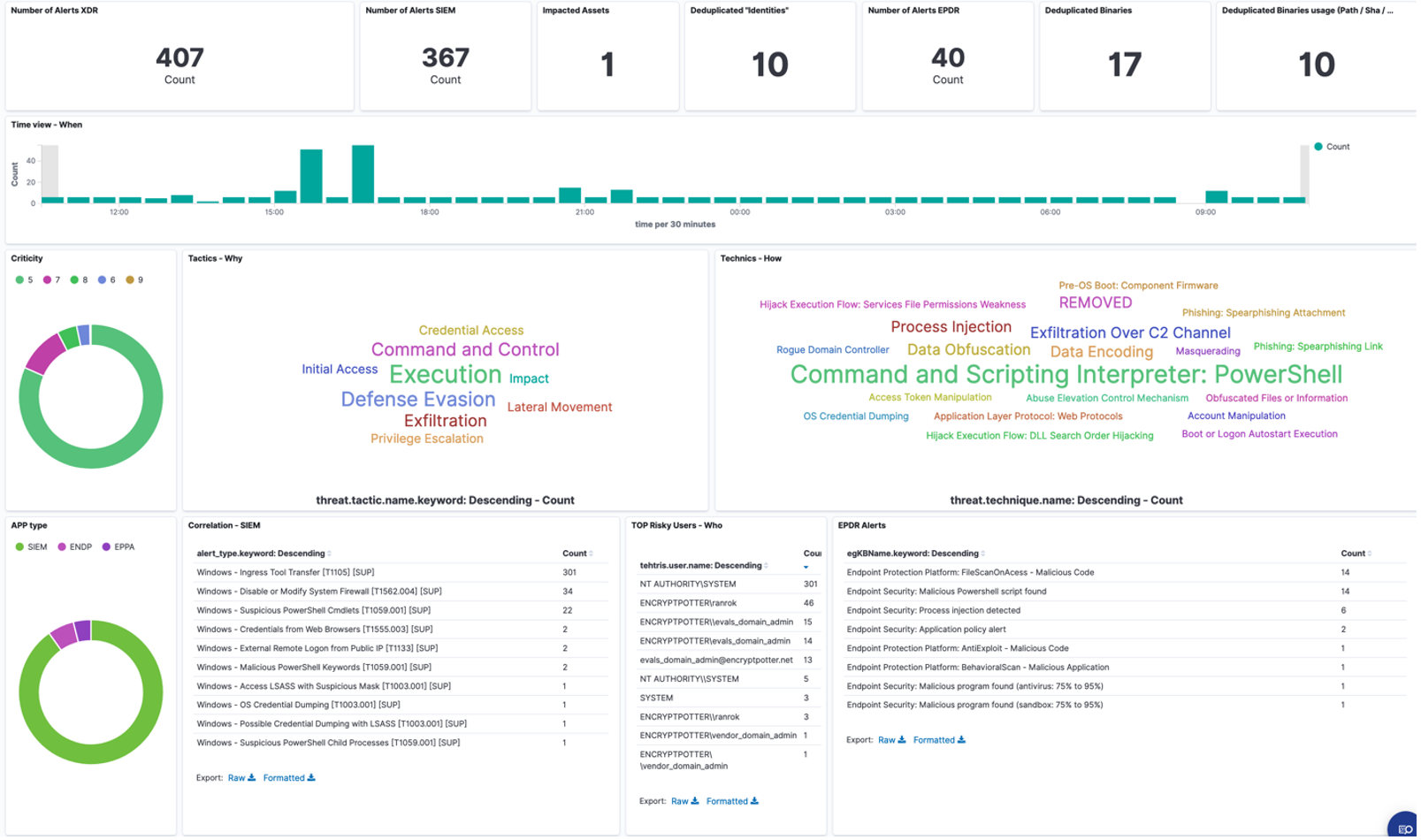
La TEHTRIS XDR AI PLATFORM offre des vues spécifiques pour chaque rôle, conçues pour rationaliser les flux de travail des analystes :
- Une vue pour des supervisions ciblées : dédiée aux analystes de niveau 1, elle permet une surveillance rapide et efficace de l’infrastructure.
- Une vue d’investigation : structurée autour des tactiques de MITRE, elle est adaptée aux analystes de niveau 2 pour leur permettre d’effectuer des analyses plus approfondies.
Les deux vues sont alimentées par l’IA propriétaire de TEHTRIS, CYBERIA. Grâce à elle, les analystes se concentrent exclusivement sur les alertes les plus pertinentes et les plus critiques, optimisant ainsi l’efficacité et la précision de la réponse.
Cette approche identifie les actions nécessitant une intervention automatisée ou humaine, tout en alignant les investigations sur les tactiques MITRE ATT&CK®. Les responsables SOC bénéficient de nouveaux tableaux de bord qui donnent des informations directement exploitables et améliorent la supervision du parc.
Conformément au modèle « Summiting the Pyramid » de MITRE, TEHTRIS se concentre sur les étapes critiques de l’attaque afin de minimiser les faux positifs, de maximiser la Threat Intelligence et de permettre des réponses décisives.
Points clés de l’évaluation 2024
L’évaluation de cette année comprenait :
- Des scénarios de menaces plus étendus : élargis pour inclure des menaces macOS, des activités bénignes testant leurs taux de faux positifs, ainsi que des attaques dans les environnements Windows et Linux.
- Un focus sur les ransomwares : analyse détaillée des méthodes d’attaque dans les campagnes Cl0p, LockBit et celles inspirées par la RPDC.
- Des ajustements du scope concerné : les étapes de l’Initial Access ont été exclues du scénario de protection évalué.
Télémétrie et configuration : Le scénario de protection de cette année s’est concentré sur les environnements déjà compromis
Télémétrie et configuration : Le scénario de protection de cette année s’est concentré sur les environnements déjà compromis
Selon les Règles d’Engagement (ROE) de MITRE ATT&CK, le blocage générique et général des services – comme le blocage de PowerShell, le blocage de tous les flux depuis Internet… – n’était pas autorisé pendant l’évaluation.
Pour respecter ces directives, TEHTRIS a dû effectuer des ajustements spécifiques à la configuration de sa TEHTRIS XDR AI PLATFORM et autoriser un comportement particulier. Une autorisation temporaire a été accordée pour l’accès RDP à distance, permettant à un compte privilégié de se connecter depuis un réseau non-administratif à un Contrôleur de Domaine Windows exposé à Internet.
Cet ajustement, qui ne se produirait pas dans un environnement de production réel, était nécessaire pour permettre aux évaluations Enterprise de MITRE ATT&CK de poursuivre le scénario d’évaluation.
Dans un environnement réel, la configuration de TEHTRIS XDR AI PLATFORM aurait immédiatement stoppé une telle menace. Ces ajustements soulignent la flexibilité et la précision de notre solution lorsqu’elle opère sous des paramètres d’évaluation contrôlés.
Bien que la télémétrie des attaques n’ait pas été évaluée cette année, elle reste essentielle dans les environnements de production, permettant les playbooks SOAR, les réponses automatisées et l’analyse forensique. TEHTRIS a démontré sa capacité à détecter et arrêter les activités malveillantes à chaque étape critique, validant ainsi sa stratégie de points de contrôle.
Des résultats qui comptent : arrêter les attaques avant leur escalade
Alors que beaucoup considèrent une couverture de détection à 100 % comme l’objectif ultime, TEHTRIS choisit une perspective plus large.
Chez TEHTRIS, nous donnons la priorité à ce qui compte vraiment : équiper les équipes SOC et les fournisseurs de services de sécurité managés (MSSP) avec des solutions qui permettent des détections et neutralisations automatiques des menaces, en temps réel. En anticipant les risques et en prévenant les brèches dans votre sécurité avant qu’elles ne puissent s’aggraver, notre approche garantit l’efficacité opérationnelle tout en minimisant le bruit inutile et la fatigue liée aux alertes.
La TEHTRIS XDR AI PLATFORM excelle dans la détection et la neutralisation des menaces. Dans des conditions réelles, notre technologie aurait arrêté les attaquants dès le départ.
Cette évaluation a réaffirmé notre engagement à fournir des outils pratiques et opérationnels qui apportent une valeur immédiate, en aidant les professionnels de la cybersécurité à se concentrer sur la prévention et la protection, plutôt que sur l’analyse post-attaque.
En optimisant les configurations à chaque étape, nous nous assurons que notre technologie anticipe et arrête les attaques à des points critiques.
Forrester souligne que « les évaluations MITRE ne sont pas un classement, c’est pour cela qu’elles ont de la valeur » et met en garde contre le fait qu’une focalisation excessive sur des détections complètes peut générer du bruit inutile, des faux positifs et un volume d’alertes écrasant, dont beaucoup peuvent ne pas être exploitables, ce qui finit par alourdir la tâche des équipes de sécurité.
Regarder vers l’avenir : renforcer le rôle des spécialistes de la configuration
La participation de TEHTRIS à l’évaluation MITRE ATT&CK Evaluations réaffirme notre engagement à doter les équipes de cybersécurité d’outils pratiques et opérationnels qui apportent une valeur immédiate et significative. En donnant la priorité à la prévention proactive et à la gestion rationalisée, nous permettons aux professionnels de se concentrer sur la protection de leurs systèmes et l’anticipation des menaces, plutôt que de se contenter de réagir aux incidents après coup.
À mesure que les défis en cybersécurité deviennent plus complexes, le rôle des spécialistes de la configuration devient essentiel. Ces experts jouent un rôle vital dans l’optimisation et la gestion des configurations des outils de sécurité, en veillant à ce que les solutions fonctionnent avec une efficacité maximale. En minimisant les erreurs de configuration et en améliorant l’efficacité des tests de pénétration et la détection des menaces, ils renforcent le dispositif de sécurité global d’une organisation.
Pour répondre à ce besoin émergent, le concept de Configuration-as-a-Service (CaaS) gagne du terrain. Ce modèle centralise et simplifie la gestion des configurations, ce qui permet aux analystes SOC de se concentrer sur leur mission principale, à savoir la prévention des brèches et le maintien de l’efficacité opérationnelle. En adoptant ces pratiques avant-gardistes, les organisations peuvent gagner en agilité, réduire les risques opérationnels et améliorer la résilience de leurs opérations de sécurité.
Alors que le paysage de la cybersécurité continue d’évoluer, l’intégration de spécialistes de la configuration et de pratiques de gestion rationalisées sera indispensable pour construire des stratégies de sécurité robustes et modernes. TEHTRIS se consacre à cette évolution en fournissant les outils et les connaissances qui permettent aux organisations de garder une longueur d’avance sur les menaces émergentes.
Pour en savoir plus sur les évaluations MITRE ATT&CK® Evaluations, cliquez ici : https://attackevals.MITRE-engenuity.org/
