SIEM
Collecte, archivage, corrélation et alerte 24/7
Surveillez votre parc en continu, qualifiez votre prise de décision et gagnez du temps en automatisant le traitement des informations provenant des logs de votre infrastructure.
Pourquoi choisir SIEM ?
Qualifiez vos logs et renforcez la sécurité de votre parc
Faites face au grand volume de données provenant de vos systèmes en centralisant la corrélation des logs de votre parc, pour prioriser vos alertes essentielles en temps réel.
SIEM les analyse automatiquement à partir de notre bibliothèque de parsers et connecteurs (continuellement mise à jour) et vous alerte en cas d’incidents. Nos tableaux de bords interactifs et personnalisables surveillent votre infrastructure 24/7 à partir d’indicateurs de volumétrie des logs ou encore de sources actives. Accélérez vos investigations par la recherche et mise sous surveillance d’IoC et par la rétention personnalisable des Hot Raw Datas.
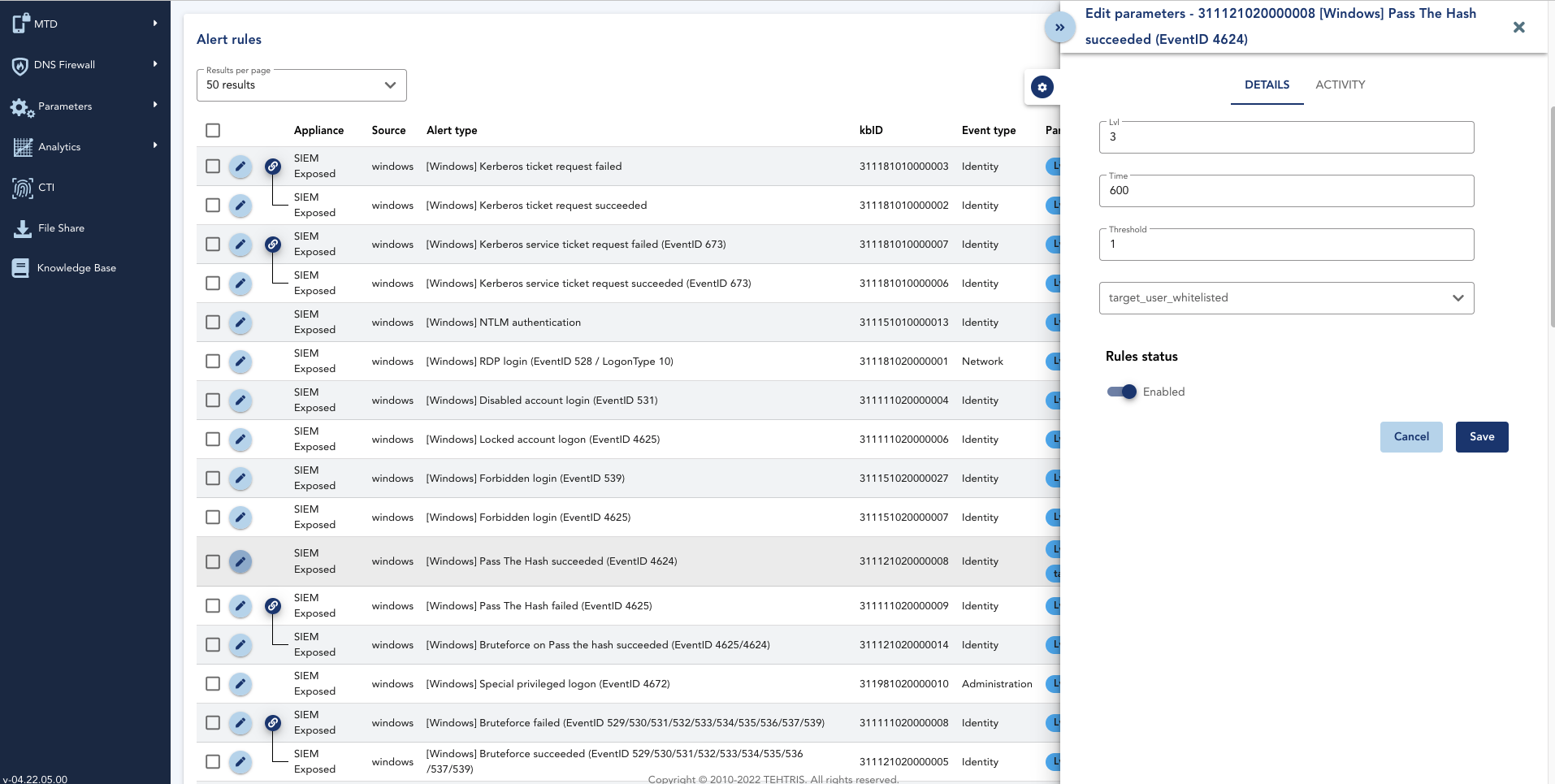
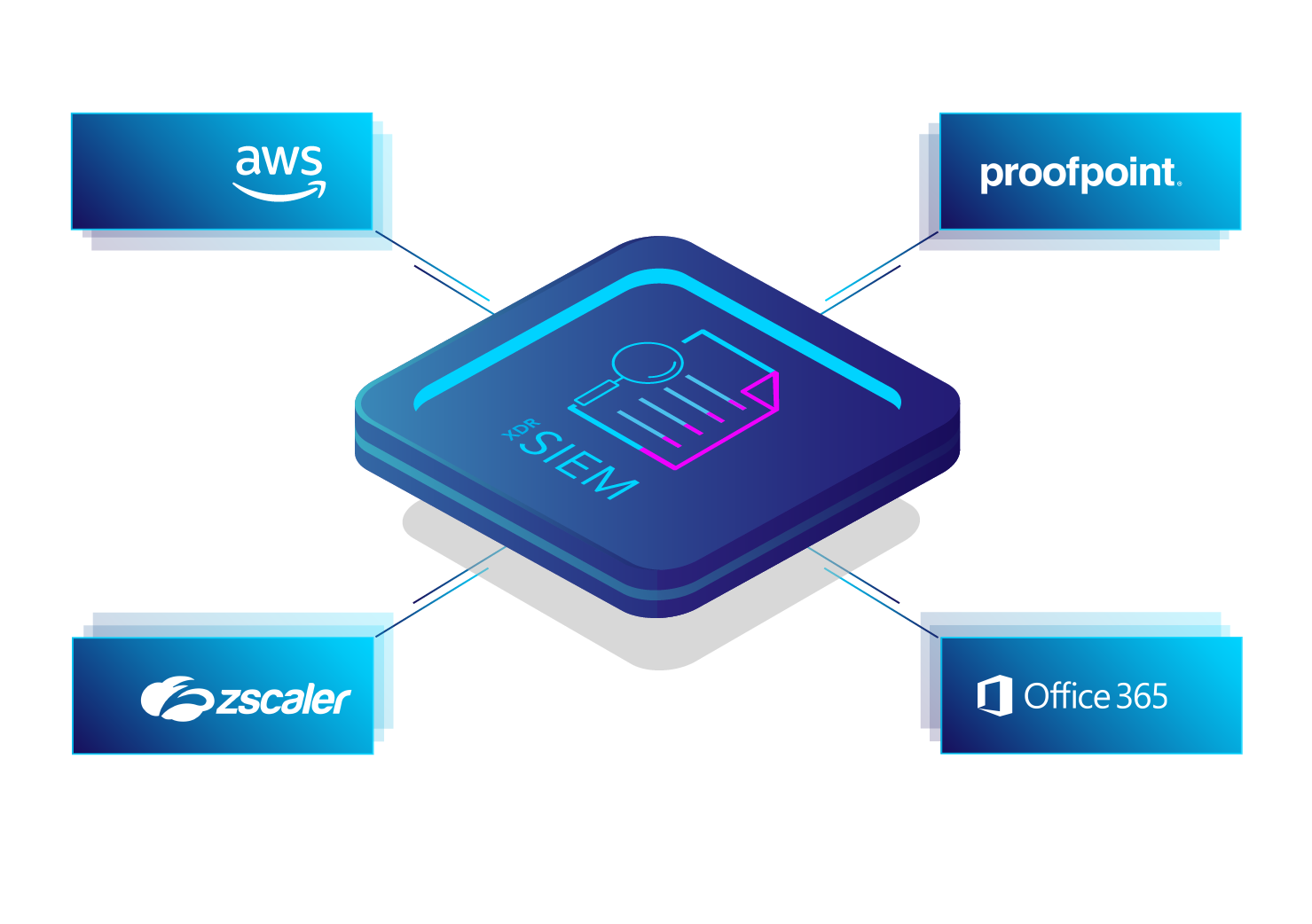
Un SIEM qui s’adapte à votre entreprise
Chaque infrastructure est différente et a ses propres besoins de cybersécurité. Personnalisable, SIEM s’adapte à votre entreprise, aux formats et aux sources que vous utilisez :
- Types de formats supportés : Syslog, Leef, CEF, JSON, CSV, KVP, XM et autres
- Sources supportées : AWS, 0365, Proofpoint, Zscaler et autres
- Tableaux de bords augmentés interactifs
- Choix du niveau d’alerting et du mode de notification
- Création et gestion des règles en autonomie (un catalogue de plusieurs milliers de règles de corrélations à votre disposition)
- Configuration des Hot Raw Data
- Blacklisting ou whitelisting des IoC et personnalisation des bases d’IoC
Détectez automatiquement les comportements déviants
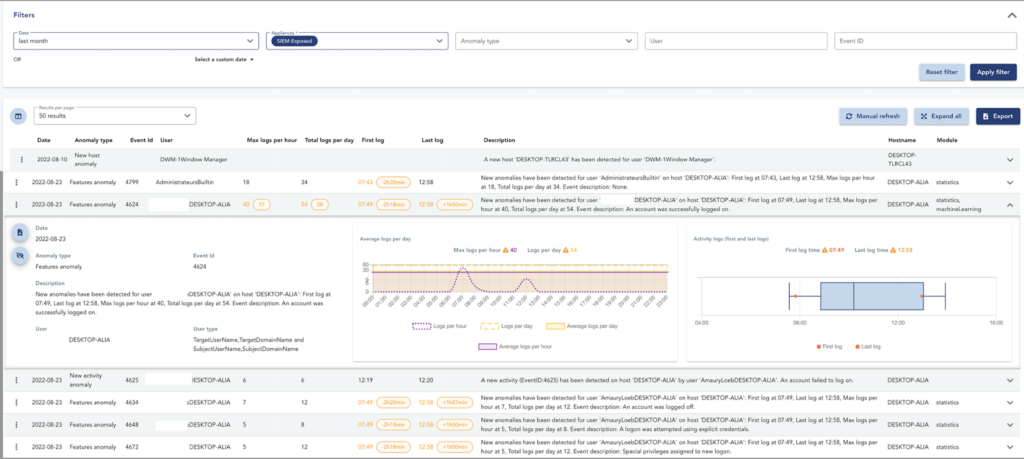
Utilisez la fonctionnalité UEBA incluse dans SIEM pour détecter les comportements anormaux dans votre parc.
Basé sur une analyse statistique, du Machine Learning et des analyses d’autre type sur les logs Windows collectés par le SIEM, notre UEBA compare les habitudes quotidiennes des utilisateurs avec l’activité courante pour lever des anomalies en cas d’activité suspecte.
Actions anormales, variation d’activité ou heures inhabituelles de connexion des utilisateurs sont par exemple automatiquement détectées. Ces informations sont remontées sur la TEHTRIS XDR AI Platform, où vos analyses accèdent à tous les détails qui ont permis de lever l’anomalie.
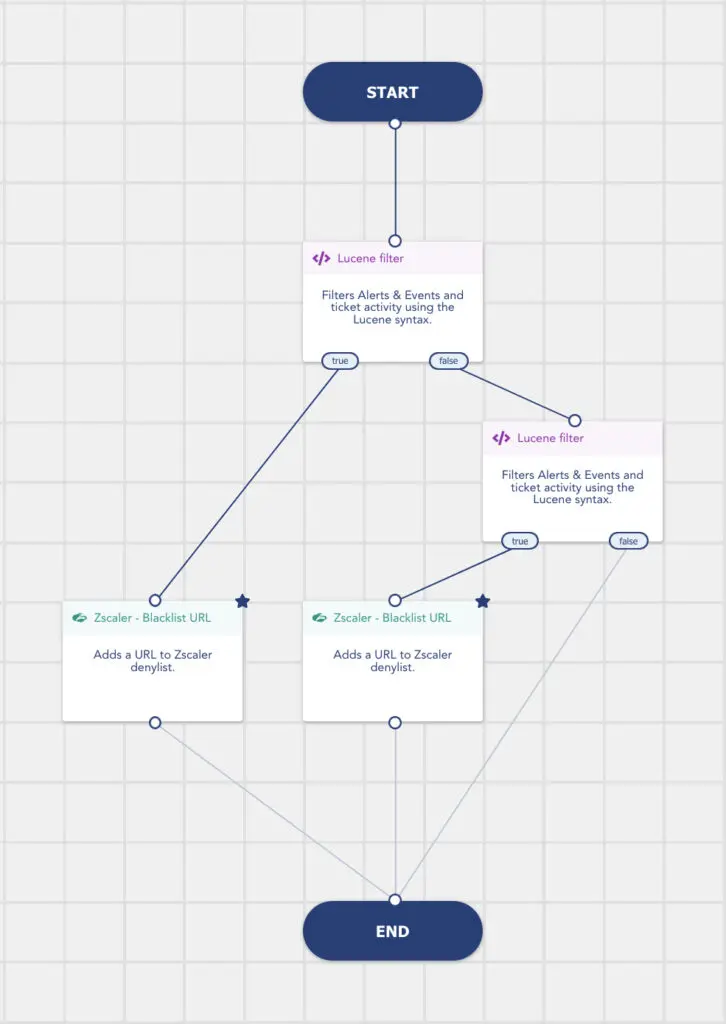
Cas d’usage : traitement automatique des données du SIEM grâce au SOAR
Tout incident détecté par le SIEM est directement remonté au SOAR pour hyperautomatiser vos investigations et réponses.
Exploitez les détections provenant de vos outils, y compris de vos solutions externes telles que Zscaler, avec l’action combinée du SIEM et du SOAR.
Notre SIEM génère des alertes lors de connexions à des addresses IP ou à des domaines identifiés comme suspicieux par CTI. Dans le Playbook Zscaler – Blacklist URL par exemple, XDR/ SOAR enrichit automatiquement la denylist de Zscaler avec ces nouveaux domaines, en se basant sur les alertes du SIEM. Vos équipes n’ont aucun traitement supplémentaire à effectuer.
Interfaçable
à la XDR Platform

SIEM est nativement intégré à la TEHTRIS XDR AI Platform.
Le SOAR intégré à TEHTRIS XDR AI Platform se connecte directement au SIEM, en simplifiant ainsi les coûts, la maintenance et l’intégration de ces technologies. Accédez à l’hyper automatisation TEHTRIS directement depuis votre SIEM.
Certifié et plébiscité
par de nombreux acteurs du monde cyber
Les autorités, analystes et associations majeurs du secteur de la cybersécurité recommandent les solutions TEHTRIS








TEHTRIS est conforme MITRE ATT&CK
MITRE ATT&CK* est une base de connaissances proposant une modélisation du comportement d’un cyber agresseur, reflétant les différentes phases du cycle de vie des attaques en fonction des plateformes ciblées : Windows, Mac, Linux, mobiles, etc.
Découvrir la compatibilité TEHTRIS XDR AI PLATFORM
avec
< 1
journée pour déployer
SIEM
6
mois de rétention des logs
100
pays où nos technologies sont déployées
Foire aux questions
Est-ce un outil de type SIM ou de type SEM ou un SIEM ?
SIEM combine la gestion des informations de sécurité (SIM) et la gestion des évènements de sécurité (SEM). C’est un SIEM complet.
Comment recueillez-vous les journaux de logs ?
SIEM comprend un sous-système SIM amélioré, en charge de la collecte de tous vos évènements à partir de votre infrastructure, de la normalisation des données hétérogènes complexes, et de la conservation de vos données à l’intérieur d’un stockage sécurisé.
Comment interprétez-vous les logs ?
SIEM comprend un sous-système SEM pointu, qui est son cerveau. Ce dernier possède une couche d’intelligence qui trie les données, sélectionne ce qui est pertinent et agrège les évènements afin de détecter des attaques très complexes. Grâce à son moteur de corrélations interne, SIEM fournit des analyses sur la base de scénarios.
Pouvons-nous utiliser ce SIEM pour faire des autopsies numériques ?
SIEM peut recueillir et conserver intelligemment vos données pendant des mois, ce qui permet à votre entreprise de mener des opérations de type Digital Forensic ou Incident Response. En exportant vos logs vers SIEM, vous limitez le risque associé à la perte de preuves issues des activités des couches système, des applications et des infrastructures. En cas d’intrusion, les attaquants ne pourront plus effacer leurs empreintes digitales dans les journaux, ces derniers étant déjà sur SIEM. Vous serez alors en mesure de suivre la progression d’un piratage grâce à la TEHTRIS XDR AI Platform. En outre, l’analyse rétrospective dans les journaux bruts archivés peut simplifier les opérations de Forensics contre des attaques complexes comme les vols d’identité, les rebonds internes et certains éléments malveillants.
Nous avons déjà un SIEM et nous souhaitons moderniser notre cybersurveillance avec SIEM, mais peut-on l’intégrer à l’existant ?
SIEM peut facilement remplacer votre infrastructure SIEM. Il vous suffit de nous transmettre vos schémas actuels, afin que nous puissions vous proposer plusieurs options simples. Nous pouvons avoir une phase avec deux SIEM en même temps, pendant la fin de votre projet pour une migration souple. Nous pouvons aussi remplacer les équipements en place. Enfin nous pouvons revoir totalement le design de votre infrastructure, par exemple si vous changez pour une offre SIEM SaaS en mode cloud.
En ce qui concerne les journaux et les évènements, que pouvons-nous réellement collecter ?
SIEM centralise et organise la gestion de tous les journaux de sécurité : évènements et journaux des systèmes, applications et équipements de réseau ou de sécurité. Une fois collectés, archivés et chiffrés, ces éléments sont analysés par le moteur de corrélations pour détecter les activités suspectes et déclencher les alertes dans tous les environnements professionnels traditionnels. Les sources sont extensibles à volonté, qu’elles soient de type équipement réseau, systèmes d’informations, applicatifs ou IoT.
SIEM permet-il une vue locale ou une vue globale ?
SIEM ne prend pas seulement en compte ce qui se passe sur une seule machine, il peut également superviser l’ensemble de votre environnement système, avec vos complexités et toutes vos interactions. Cela permet de garder le contrôle de vos actifs en ayant une vue claire de l’intérieur de votre réseau. Avec SIEM et grâce à la connaissance des cyberattaques apportée par la TEHTRIS XDR AI Platform, vous avez également un œil ouvert sur l’extérieur de votre réseau afin de savoir d’où viennent les menaces.
Est-ce que l’on peut détecter les comportements anormaux et les anomalies ?
SIEM est capable de détecter les comportements anormaux et de déclencher des alertes qualifiées en temps réel à votre équipe d’intervention SOC. Il donne un sens à des flux illimités de journaux d’évènements hétérogènes provenant de divers dispositifs, produits et capteurs sources, pour ne présenter à vos analystes que les informations pertinentes.
Avez-vous des règles de corrélation par défaut ou est-ce un SIEM non utilisable dès le premier jour ?
Lorsque SIEM est livré, il comporte déjà plus de 500 règles intégrées, liées à la norme des environnements informatiques. Par exemple, vous avez déjà tout pour vos systèmes d’exploitation (Windows, Linux, etc.). SIEM est donc étroitement lié à la plateforme TEHTRIS XDR AI platform afin d’être un outil intuitif et efficace “prêt à l’emploi” pour votre chasse aux menaces.
