A good understanding of active threats is necessary to achieve a good security posture. The following report provides actual trends that emerge from the Internet Background Noise. The data are provided using two weeks of our worldwide honeypots’ logs.
Find our previous bi-monthly report here, and subscribe for free to get even more valuable information.
Microsoft patch Tuesday – CVE-2023-21554
For the occasion of Microsoft Patch Tuesday on the 11th of April, CVE-2023-21554 (CVSSv3: 9.8) in Windows Message Queuing (MSMQ) middleware service was disclosed. It was also dubbed QueueJumper. Attack complexity is low and doesn’t require any privileges or user interaction. To exploit this vulnerability, threat actors would send a malicious MSMQ packet to a listening MSMQ service. Microsoft indicates that the service running named Message Queuing is listening on the machine through TCP port 1801.
On our worldwide network of honeypots, we monitored a spike of 1801/TCP calls starting just after the disclosure of the vulnerability on the 12th of April. On Saturday, when most of the organizations were closed for the weekend, the threat actors pick up the pace. We assume this exploit opportunity will continue to grow in the coming days, as organizations will take time to patch all their devices from this threat.
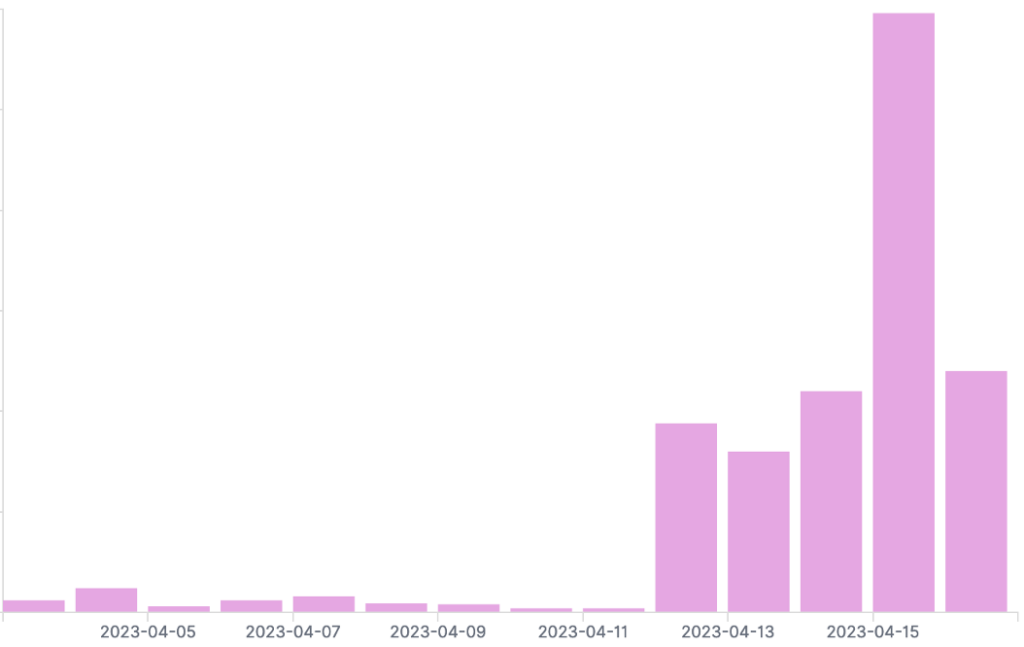
Spike on port 1801 monitored on our worldwide honeypots network
Before the disclosure, we observed that mostly Bulgarian IP addresses were checking this particular port/protocol. After the disclosure, most IP addresses scanning the world to find open port 1801on TCP were hosted in the USA.
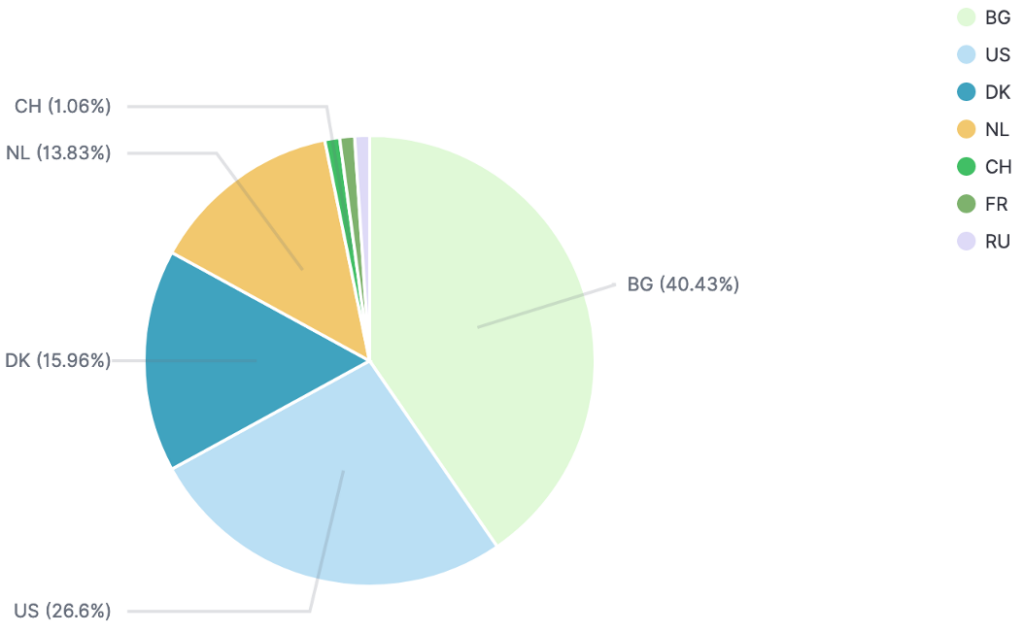
Repartition of malicious IP addresses before the disclosure (1st to 11th of April)
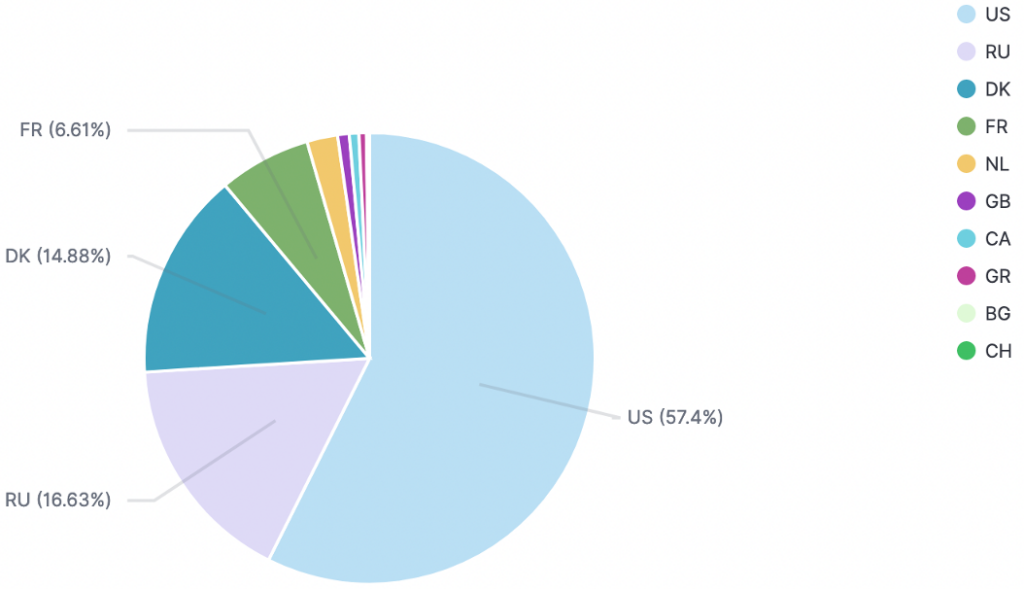
Repartition of malicious IP addresses after the disclosure (12th to 17th of April)
After the disclosure, the most targeted honeypots IPs are localized in the USA and in Western Europe.
TEHTRIS recommends deploying Microsoft’s patch critical MSMQ QueueJumper bug or blocking 1801/TCP connections as workaround.
EXPLOIT Mikrotik Winbox RCE Attempt (CVE-2018-14847)
CVE-2018-14847 (CVSSv3: 9,1) is about MikroTik RouterOS through 6.42 that allows unauthenticated remote attackers to read arbitrary files and remote authenticated attackers to write arbitrary files due to a directory traversal vulnerability in the WinBox interface
On the 7th of April on one of our honeypots located in Northern Pacific Asia, we monitored this particular exploit Mikrotik Winbox RCE attempt on port 22/TCP.
Only one threat actor performed this exploit attempt. The threat actor’s IP address is 104.223.37.118. It is hosted by the US AS 8100 ASN-QUADRANET-GLOBAL, and it is known from public databases identifying malicious IP.
SSH attempts – Huawei login credentials abuse
These past two weeks, around 200 IP addresses tried to login on our honeypots SSH services using “huawei” as credentials.
The most used passwords, associated with “huawei” login, are the following:

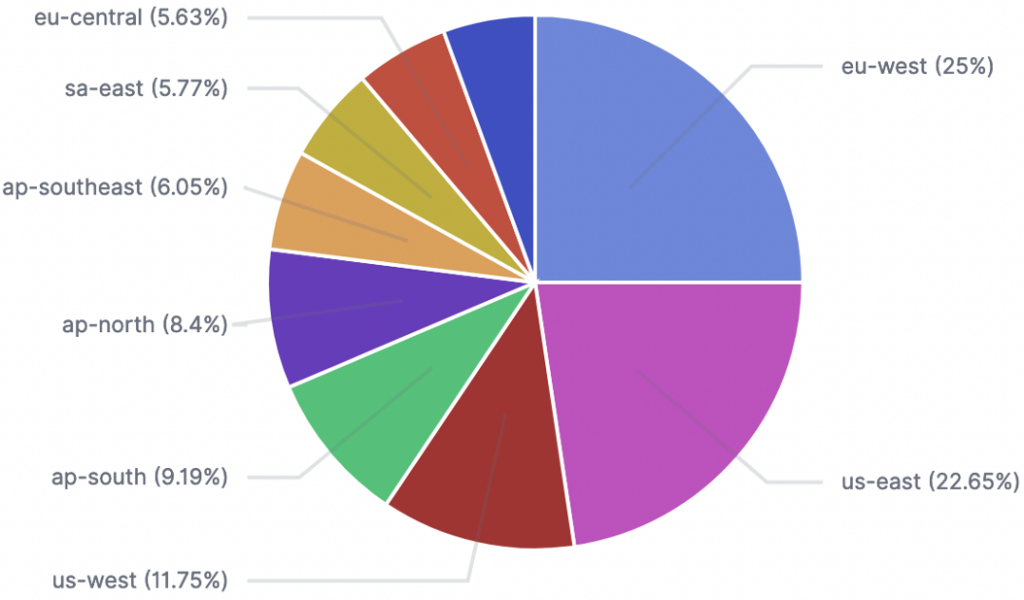
Below, you will find a repartition of our targeted honeypots around the world:
Top 10 IoCs:
92.50.249[.]166
87.219.167[.]66
54.39.96[.]44
43.156.5[.]135
43.156.146[.]134
23.94.0[.]113
96.84.198[.]29
94.70.166[.]88
93.157.174[.]208
92.119.231[.]13
Exploit vRealize Operations Manager API SSRF Attempt (CVE-2021-21975)
Want to learn more on this subject?
More insights on this research issued from the alerts on our worldwide honeypots network.
Subscribe to our bi-monthly threat intelligence newsletter
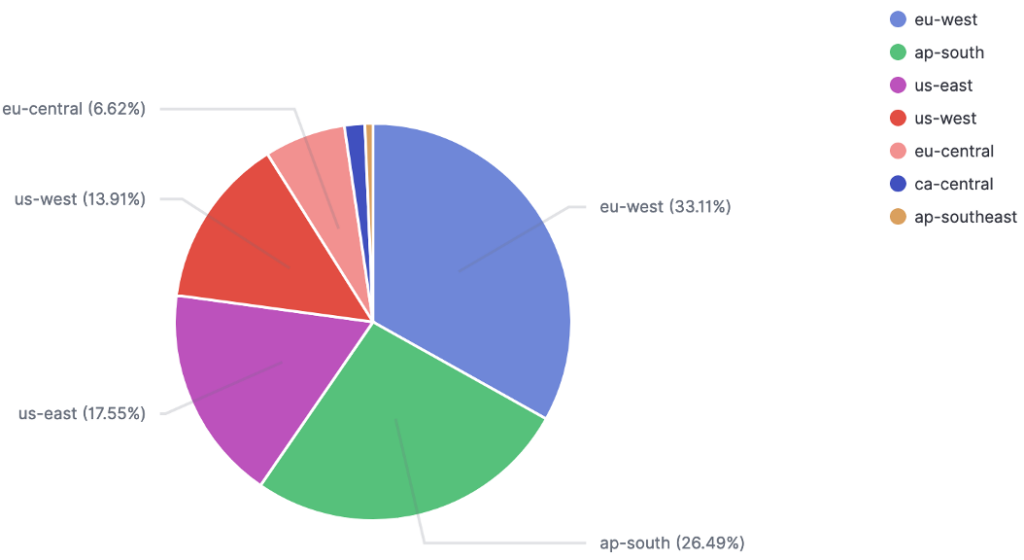
Global network traffic analysis on our honeypots
Want to learn more on this subject?
More insights on this research issued from the alerts on our worldwide honeypots network.
Subscribe to our bi-monthly threat intelligence newsletter
Information remain TEHTRIS sole property and reproduction is forbidden
TEHTRIS is and remains sole property rights owner of the information provided herein. Any copy, modification, derivative work, associated document, as well as every intellectual property right, is and must remain TEHTRIS’ sole and exclusive property. TEHTRIS authorizes the user to access for read use only. Except as expressly provided above, nothing contained herein will be construed as conferring any license or right under any TEHTRIS’ copyright.
No warranty and liability
TEHTRIS will not be held liable for any use, improper or incorrect use of the information described and/or contained herein and assume no responsibility for anyone’s use of the information. Although every effort has been made to provide complete and accurate information, TEHTRIS makes no warranty, expressed or implied regarding accuracy, adequacy, completeness, legality, reliability, or usefulness of any information provided herein. This disclaimer applies to both isolated and aggregated uses of the information.


